Are you looking for a step-by-step guide on How to get a job in Cyber security? In today’s digital age, cyber security has become a critical aspect of our lives. With the increasing reliance on technology and the rise of cyber threats, protecting our personal information and digital assets has never been more important.
This blog post aims to provide a comprehensive guide to pursuing a career in cyber security. Whether you are a recent graduate looking to enter the field or a professional seeking a career change, this post will provide valuable insights into the job market, essential skills and qualifications, resume building, networking, interview preparation, job search process, career advancement, and available resources and tools.
What is Cyber Security?
Cyber security refers to the practice of protecting computer systems, networks, and data from unauthorized access, theft, or damage. It encompasses various measures and technologies designed to prevent cyber attacks and ensure the confidentiality, integrity, and availability of information. Cyber security professionals play a crucial role in safeguarding organizations and individuals from cyber threats.
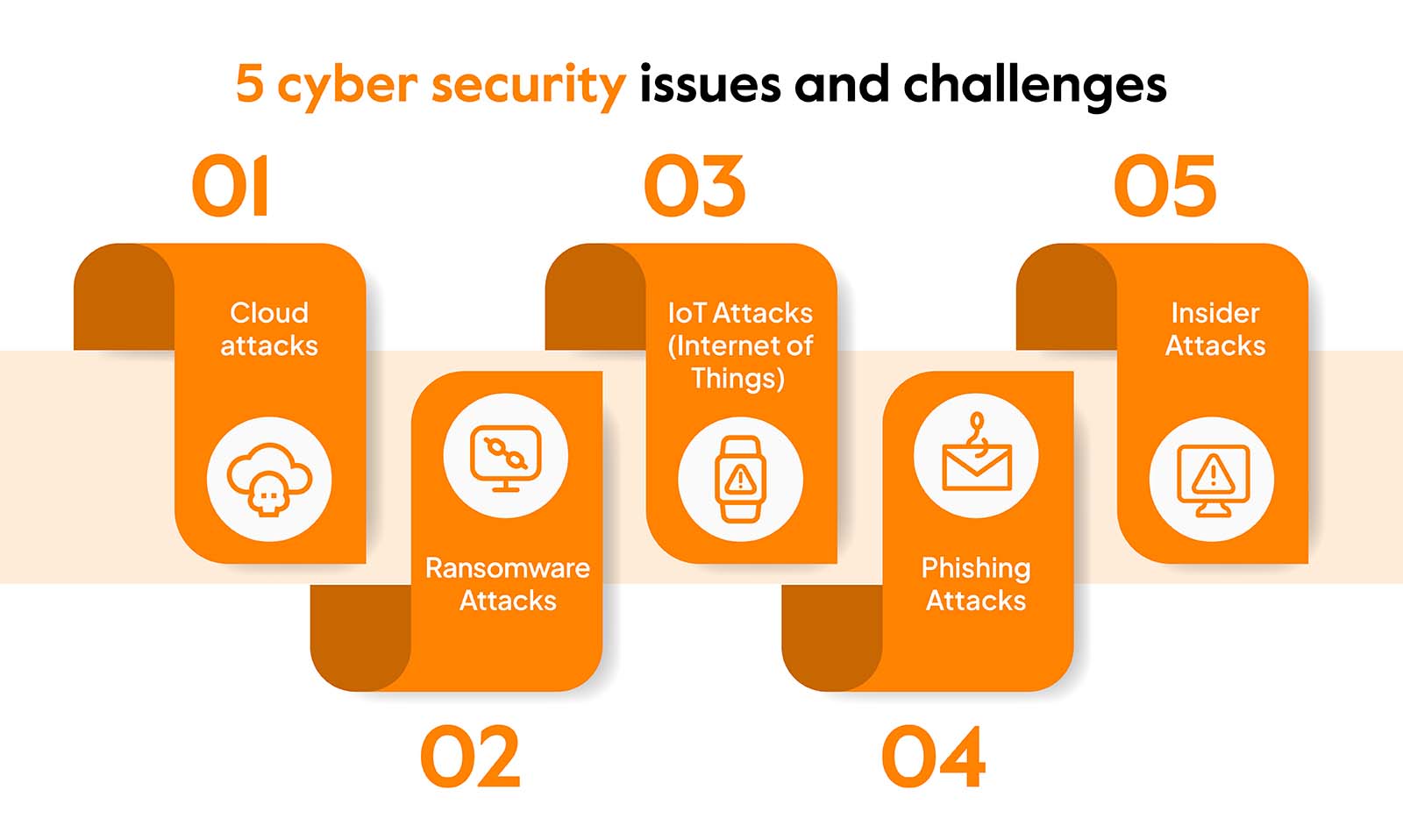
There are different types of cyber security jobs, each with its own set of responsibilities and requirements. Some common roles include:
- Security Analyst: Security analysts are responsible for monitoring and analyzing security systems to identify potential vulnerabilities and threats. They develop and implement security measures to protect against attacks and respond to incidents.
- Ethical Hacker: Ethical hackers, also known as penetration testers, are responsible for identifying vulnerabilities in computer systems and networks. They use their skills to simulate cyber attacks and help organizations strengthen their security defenses.
- Security Engineer: Security engineers design and implement security systems and protocols to protect computer networks and data. They work closely with other IT professionals to ensure the security of an organization’s infrastructure.
To pursue a career in cyber security, it is essential to have a strong foundation in computer science or a related field. A bachelor’s degree in computer science, information technology, or a similar discipline is often required. Additionally, certifications courses such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH) can enhance job prospects.
How to Get a Job in Cyber Security: Pathway for Success
Here, are the Pathway to get a highly-paying job in Cyber Security.
Understanding the Job Market in Cyber Security
The job market in cyber security is highly competitive, with a growing demand for skilled professionals. Organizations across various industries, including government agencies, financial institutions, healthcare providers, and technology companies, are actively seeking cybersecurity experts to protect their sensitive information.
The types of companies that hire cybersecurity professionals vary widely. Large corporations often have dedicated cyber security teams, while smaller organizations may outsource their security needs to specialized firms. Government agencies and defense contractors also offer numerous opportunities in the field.
In terms of roles, the cyber security job market offers a wide range of options. From entry-level positions to senior management roles, there are opportunities for professionals at every stage of their careers. Some common roles include:
- Security Analyst: As mentioned earlier, security analysts play a crucial role in monitoring and analyzing security systems. They are in high demand due to the increasing number of cyber threats.
- Incident Responder: Incident responders are responsible for investigating and responding to cyber security incidents. They analyze the nature and scope of an incident, contain the damage, and implement measures to prevent future incidents.
- Security Consultant: Security consultants provide expert advice and guidance to organizations on how to improve their cyber security roles. They assess vulnerabilities, develop security strategies, and recommend appropriate solutions.
Essential Skills and Qualifications for a Career in Cyber Security
To succeed in a career in cyber security, certain skills and qualifications are essential. These include technical skills, soft skills, and industry certifications.
Technical skills: A strong foundation in computer science and information technology is crucial for a career in cyber security. Proficiency in programming languages such as Python, Java, or C++ is highly desirable. Additionally, knowledge of networking protocols, operating systems, and database management is important.
Soft skills: In addition to technical skills, cyber security professionals need strong communication, problem-solving, and analytical skills. They must effectively communicate complex technical concepts to non-technical stakeholders and work collaboratively with cross-functional teams.
Industry certifications: Obtaining industry certifications can significantly enhance job prospects in cyber security. Some popular certifications include Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and Certified Information Security Manager (CISM). These certifications validate an individual’s knowledge and expertise in specific areas of cyber security.
Continuing education is also crucial in the field of cyber security. Technology is constantly evolving, and new threats and vulnerabilities emerge regularly. Staying up-to-date with the latest trends, tools, and techniques is essential to remain competitive in the job market.
Building a Strong Cyber Security Resume
A strong resume is essential for standing out in the competitive cybersecurity job market. It should highlight relevant skills, experience, and qualifications that make you a strong candidate for the position.
Key components of a strong cyber security resume include
- Summary statement: A concise summary at the beginning of your resume that highlights your key qualifications and career goals.
- Technical skills: A section that lists your technical skills, including programming languages, operating systems, networking protocols, and security tools.
- Professional experience: A detailed description of your previous work experience, highlighting your accomplishments and responsibilities in previous cyber security roles.
- Education and certifications: A section that lists your educational background, including degrees earned and relevant certifications obtained.
When tailoring your resume to a specific cybersecurity job, it is important to carefully review the job description and identify the key skills and qualifications required. Customize your resume to highlight those specific skills and experiences that align with the job requirements.
It is also important to highlight any relevant experience or projects outside of formal employment. This could include internships, volunteer work, or personal projects that demonstrate your passion for cyber security and your ability to apply your skills in real-world scenarios.
Networking and Building Professional Relationships in Cyber Security
Networking is a crucial aspect of building a successful career in cybersecurity. It allows you to connect with industry professionals, learn about job opportunities, and gain valuable insights into the field.
To build professional relationships in the cyber security industry, consider the following strategies:
- Attend industry events: Attend conferences, seminars, and workshops related to cyber security. These events provide opportunities to meet professionals in the field, learn about the latest trends and technologies, and expand your professional network.
- Join professional organizations: Joining professional organizations such as the Information Systems Security Association (ISSA) or the International Information System Security Certification Consortium (ISC)² can provide access to networking events, educational resources, and job boards.
- Utilize online platforms: Join online communities and forums dedicated to cyber security. Platforms such as LinkedIn, Reddit, and specialized cybersecurity forums allow you to connect with professionals, ask questions, and share knowledge.
Building relationships in the cyber security industry is not just about networking events and online platforms. It is also important to actively engage with professionals in the field. Reach out to individuals for informational interviews, seek mentorship opportunities, and participate in industry discussions.
Preparing for Cyber Security Interviews
Preparing for a cyber security interview is crucial to increase your chances of success. It is important to research the company and the role you are applying for, understand the specific requirements of the position and be prepared to demonstrate your knowledge and skills.
To prepare for a cyber security interview, consider the following tips:
- Research the company: Familiarize yourself with the company’s mission, values, and recent projects. Understand their cyber security needs and how your skills and experience align with them.
- Understand the role: Review the job description in detail and identify the key responsibilities and requirements of the role. Be prepared to discuss how your skills and experience make you a strong fit for the position.
- Brush up on technical knowledge: Review key concepts and technologies related to cyber security, such as network security, encryption, vulnerability assessment, and incident response. Be prepared to answer technical questions related to these areas.
- Prepare for behavioral questions: In addition to technical questions, be prepared to answer behavioral questions that assess your problem-solving skills, communication abilities, and ability to work in a team.
Common Cyber Security Interview Questions and How to Answer Them
During a cyber security interview, you may encounter a variety of questions that assess your technical knowledge, problem-solving abilities, and communication skills. Here are some common cyber security interview questions and tips on how to answer them effectively:
- “Tell me about a time when you faced a cyber security incident and how you resolved it.”
When answering this question, provide a specific example from your experience. Describe the incident, the steps you took to investigate and resolve it, and the lessons you learned from the experience. Emphasize your ability to think quickly, work under pressure, and effectively communicate with stakeholders.
- “How do you stay up-to-date with the latest cyber security trends and technologies?”
When answering this question, highlight your commitment to continuous learning and professional development. Discuss specific resources you utilize, such as industry publications, online forums, or professional organizations. Emphasize your ability to adapt to new technologies and stay ahead of emerging threats.
- “How would you handle a situation where a colleague violated a security policy?”
When answering this question, demonstrate your ability to handle sensitive situations diplomatically. Discuss the importance of open communication and collaboration in addressing policy violations. Emphasize your commitment to educating colleagues about the importance of security policies and the potential consequences of non-compliance.
Navigating the Cyber Security Job Search Process
The cyber security job search process can be overwhelming, but with the right strategies, it can be manageable and successful. Here are some steps to effectively navigate the job search process:
- Define your career goals: Determine the specific area of cyber security you are interested in and the type of role you want to pursue. This will help you focus your job search and tailor your application materials accordingly.
- Research job opportunities: Utilize online job boards, company websites, and professional networking platforms to identify job opportunities in your desired field. Take note of the specific requirements and qualifications for each position.
- Tailor your application materials: Customize your resume and cover letter to highlight the skills and experiences that align with the job requirements. Use keywords from the job description to demonstrate your suitability for the role.
- Follow up after submitting applications: After submitting your application, follow up with a thank-you email or phone call to express your continued interest in the position. This demonstrates your professionalism and enthusiasm for the role.
Advancing Your Career in Cyber Security
Advancing your career in cyber security requires a combination of continuous learning, professional development, and strategic career planning. Here are some ways to advance your career in the field:
- Pursue advanced education: Consider pursuing a master’s degree or specialized certifications in areas such as digital forensics, network security, or cloud security. Advanced education can enhance your knowledge and skills and open up new career opportunities.
- Seek leadership roles: As you gain experience in the field, look for opportunities to take on leadership roles. This could involve managing a team, leading projects, or mentoring junior professionals. Leadership experience demonstrates your ability to take on greater responsibilities and can lead to career advancement.
- Stay up-to-date with industry trends: Continuously educate yourself on the latest trends, technologies, and best practices in cyber security. Attend conferences, participate in webinars, and read industry publications to stay informed and maintain a competitive edge.
- Network and build professional relationships: Continue to network and build relationships with professionals in the field. Attend industry events, join professional organizations, and engage with online communities to expand your network and gain valuable insights.
Resources and Tools for Cyber Security Job Seekers
There are numerous resources and tools available to help cyber security job seekers in their career journey. Here are some valuable resources to consider:
- Job boards: Utilize online job boards dedicated to cyber security, such as CyberSecJobs, Indeed, or LinkedIn Jobs. These platforms allow you to search for job opportunities, filter by location or specific roles, and apply directly through the platform.
- Professional organizations: Join professional organizations such as the Information Systems Security Association (ISSA), the International Information System Security Certification Consortium (ISC)², or the Cybersecurity and Infrastructure Security Agency (CISA). These organizations provide access to job boards, networking events, educational resources, and industry news.
- Online learning platforms: Platforms such as Coursera, Udemy, and LinkedIn Learning offer a wide range of online courses and certifications in cyber security. These courses can help you acquire new skills, enhance your knowledge, and demonstrate your commitment to professional development.
- Industry publications: Stay up-to-date with the latest news and trends in cyber security by reading industry publications such as Dark Reading, SC Magazine, or SecurityWeek. These publications provide insights into emerging threats, best practices, and industry developments.
Conclusion
Pursuing a career in cyber security offers numerous opportunities for growth and advancement. The field is in high demand, with organizations across various industries seeking skilled professionals to protect their digital assets. By acquiring the necessary skills and qualifications, building a strong resume, networking with industry professionals, preparing for interviews, and utilizing available resources and tools, you can position yourself for success in the cyber security job market.
Remember to stay up-to-date with industry trends, continuously learn and develop your skills, and actively engage with professionals in the field. With dedication and perseverance, you can build a rewarding career in cyber security.