As technology progresses at a rapid pace, businesses are becoming increasingly dependent on digital and online components. Consequently, cybersecurity is gaining an ever greater importance. This blog will explore the most recent developments in terms of cybersecurity and provide strategies for protection from security risks, digital threats and data breaches. Moreover, it shall also discuss approaches to secure data and guarantee that customers’ and employees’ safety when using the internet is guaranteed so readers can remain up to date regarding novel cyber trends!
What is Cybersecurity?

Cybersecurity consists of technologies, processes, and practices intended to protect digital information as well as guarantee its integrity, confidentiality and accessibility; it also helps prevent breaches and maintains the stability of both individual’s digital ecosystems or organizations. Firewalls, encryption software, and security training are just some examples that defend from malicious programs like malware or phishing attempts since more businesses rely upon technology daily enhancing cybersecurity safeguards becomes increasingly important when protecting confidential info.
What is the need for Cybersecurity in IT?
Cybersecurity is essential when it comes to IT, safeguarding sensitive data, systems & networks from numerous security threats which become more sophisticated as technology advances; making cyber protection indispensable in protecting businesses from potential financial losses due to ransomware attacks or other malicious activities that could damage reputation along with legal liabilities involved too! In addition, robust cybersecurity measures ensure continuous operations alongside trustworthiness among customers & partners – thus being an integral part of today’s digital infrastructure & management process.
What are the top Cybersecurity trends in IT?
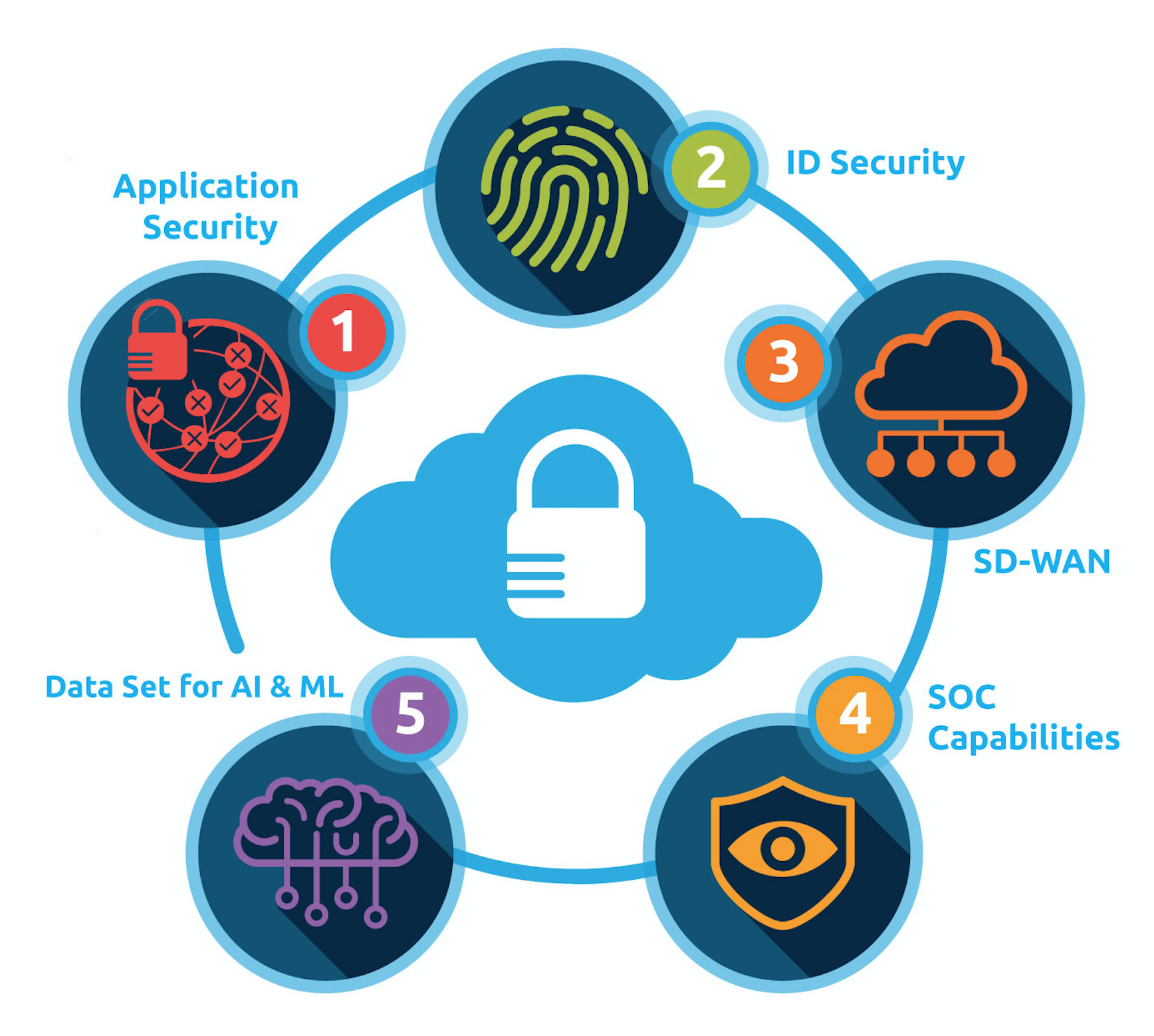
The top cybersecurity trends in IT are as follows-
- Zero Trust Architecture
Relying on strict identity verification for all users and devices, regardless of location.
- AI and Machine Learning in Threat Detection
Using AI algorithms to detect and respond to threats in real-time.
- Multi-Factor Authentication (MFA)
Expanding the use of MFA for added security.
- IoT Security
Addressing vulnerabilities in the rapidly growing Internet of Things.
- Cloud Security
Strengthening cloud-based security solutions as more data migrates to the cloud.
- Ransomware Defense
Developing robust strategies to protect against and recover from ransomware attacks.
- Endpoint Security
Enhanced security measures for devices like laptops, smartphones, and IoT endpoints.
- Container Security
Protecting applications running in containers and microservices.
- Supply Chain Security
Ensuring the security of the entire supply chain to prevent attacks like the SolarWinds incident.
- Quantum Computing Threats
Preparing for future cryptographic vulnerabilities posed by quantum computers.
- Cybersecurity Skills Shortage
Addressing the shortage of skilled cybersecurity professionals.
- Regulatory Compliance
Navigating and adhering to evolving data protection and privacy regulations.
- Threat Intelligence Sharing
Collaborating with industry peers to share threat intelligence and best practices.
- Deepfake Detection
Developing tools to identify and combat deepfake content.
- 5G Security
Securing the expanding 5G network infrastructure.
- Incident Response Automation
Automating incident response processes for faster threat mitigation.
- Blockchain Security
Protecting blockchain networks and cryptocurrencies from attacks.
- Biometric Authentication
Increasing use of biometrics for authentication and identity verification.
- Data Privacy Focus
Addressing user concerns and regulations regarding data privacy.
- Security Awareness Training
Educating employees and users to reduce human-related vulnerabilities.
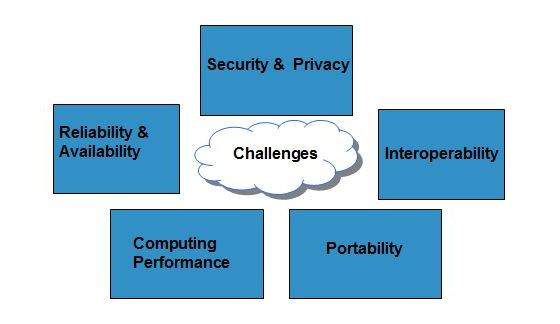
What are the Cybersecurity challenges one can face in IT?
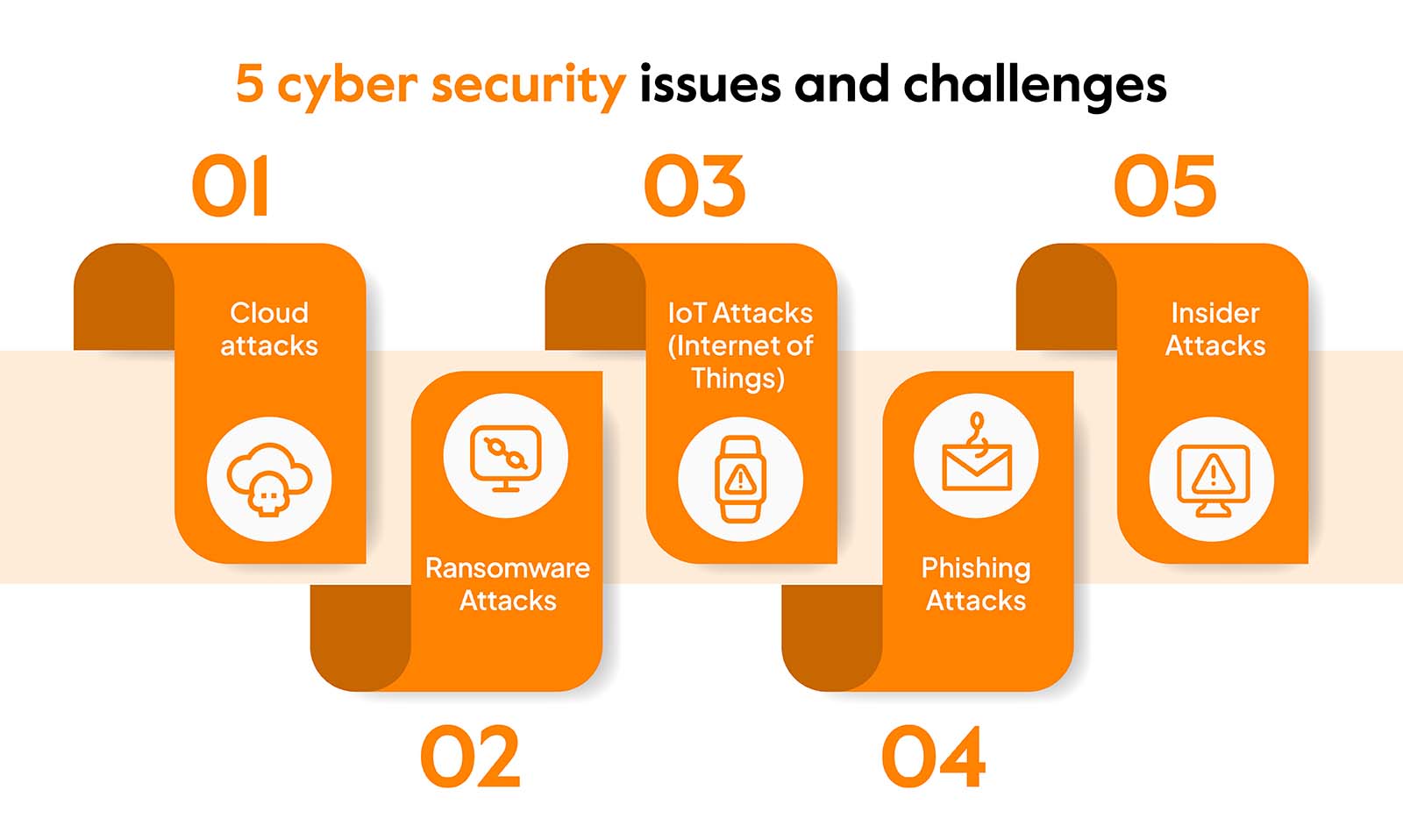
The cybersecurity challenges one can face in IT are as follows-
- Advanced Persistent Threats (APTs)
Sophisticated, long-term attacks by skilled adversaries that are hard to detect and mitigate.
- Ransomware
Growing prevalence of ransomware attacks that encrypt data and demand payments for decryption keys.
- Zero-Day Vulnerabilities
Attacks exploit undisclosed vulnerabilities before patches are available.
- Insider Threats
Malicious or negligent actions by employees or insiders who compromise security.
- IoT Vulnerabilities
Insecure Internet of Things devices that can be exploited for cyberattacks.
- Supply Chain Attacks
Attackers target third-party vendors or software suppliers to compromise organizations downstream.
- Cloud Security
Ensuring the security of data and services in cloud environments.
- Regulatory Compliance
Meeting increasingly complex data protection and privacy regulations.
- Cybersecurity Skills Gap
Shortage of qualified cybersecurity professionals to defend against threats.
- User Awareness
Educating users about cybersecurity best practices to reduce human-related vulnerabilities.
How to overcome cybersecurity challenges?
A few ways to overcome cybersecurity challenges are as follows-
- Advanced Threat Detection
Invest in cutting-edge threat detection technologies, including AI and machine learning, to identify and respond to advanced threats like APTs and zero-day vulnerabilities.
- Ransomware Mitigation
Implement robust backup and recovery solutions, educate employees on phishing awareness, and maintain up-to-date software to minimize the impact of ransomware attacks.
- Patch Management
Prioritize timely software and system updates to patch vulnerabilities and minimize exposure to zero days.
- Insider Threat Prevention
Implement user access controls, monitor user activities, and conduct regular security training to mitigate insider threats.
- IoT Security
Establish strict IoT device management protocols, including firmware updates and network segmentation.
- Supply Chain Security
Vet third-party vendors, conduct security audits, and establish a secure supply chain ecosystem.
- Cloud Security
Implement strong access controls, encryption, and continuous monitoring in cloud environments.
- Regulatory Compliance
Develop comprehensive compliance strategies and appoint compliance officers to ensure adherence to data protection laws.
- Cybersecurity Workforce Development
Invest in training, recruitment, and retention of skilled cybersecurity professionals to bridge the skills gap.
- User Education
Promote a culture of cybersecurity awareness through regular training and communication to reduce human-related vulnerabilities.
What skills should I learn to cope with the cybersecurity trends?

The skills you need to learn to cope with cybersecurity trends are as follows-
- Network Security
Understanding network protocols, firewalls, and intrusion detection/prevention systems.
- Security Architecture
Designing and implementing secure system and network architectures.
- Cryptography
Knowledge of encryption, decryption, and cryptographic algorithms.
- Penetration Testing
Ethical hacking skills to identify and exploit vulnerabilities.
- Incident Response
Developing and executing incident response plans effectively.
- Threat Intelligence Analysis
Gathering and analyzing threat intelligence data to predict and prevent attacks.
- Security Auditing
Conducting security audits and assessments of systems and networks.
- Security Policies and Compliance
Understanding and implementing security policies and ensuring regulatory compliance.
- Secure Coding
Writing and reviewing secure code to prevent software vulnerabilities.
- Endpoint Security
Securing endpoints like laptops, smartphones, and IoT devices.
- Cloud Security
Protecting data and resources in cloud environments.
- Identity and Access Management (IAM)
Managing user identities and controlling access to systems and data.
- Security Information and Event Management (SIEM)
Monitoring and analyzing security events and incidents.
- Machine Learning and AI for Security
Applying AI and ML techniques for threat detection and analysis.
- Forensics and Investigation
Conducting digital forensics to trace and attribute cyber incidents.
- Mobile Security
Securing mobile applications and devices.
- Secure DevOps
Integrating security practices into the DevOps pipeline for continuous security.
- Risk Management
Evaluating and managing cybersecurity risks within an organization.
- Security Awareness Training
Educating employees and users on security best practices.
- Blockchain Security
Understanding the security implications of blockchain technology.
What cybersecurity courses are available in IT?
The top available cyber security courses in IT are as follows-
CEH (v12)
CEH is a certification that teaches ethical hacking skills. It equips professionals with knowledge to identify and counteract vulnerabilities and threats, enabling them to think like hackers and protect systems and networks from cyberattacks.
The exam details for the CEH (v12) course are as follows-
Exam Name | Certified Ethical Hacker (312-50) |
Exam Cost | USD 550 |
Exam Format | Multiple Choice |
Total Questions | 125 Questions |
Passing Score | 60% to 85% |
Exam Duration | 4 Hours |
Languages | English |
Testing Center | Pearson Vue |
CISSP Training
CISSP is a globally recognized certification for information security professionals. It covers a wide range of security topics, including access control, cryptography, and risk management, and validates expertise in designing, implementing, and managing security programs.
The exam details for the CISSP training course are as follows-
Exam Name | ISC2 Certified Information Systems Security Professional |
Exam Code | CISSP |
Exam Cost | USD 749 |
Exam Duration | 4 hours |
Number of Questions | 125-175 |
Exam Format | Multiple choice and advanced innovative questions |
Passing Marks | 700/1000 points |
Exam Language | English |
Testing Center | (ISC)^2 authorized PPC, PVTC Select Pearson VUE tests |
CompTIA PenTest+
CompTIA PenTest+ certifies skills in penetration testing and vulnerability assessment. It focuses on hands-on techniques for identifying and addressing security vulnerabilities, making it suitable for professionals who want to specialize in offensive security.
The exam details for the CompTIA PenTest+ course are as follows-
Exam Code | PT0-002 |
Number of Questions | Maximum of 85 questions |
Exam Cost | USD 392 |
Type of Questions | Performance-based and multiple choice |
Length of Test | 165 minutes |
Passing Score | 750 (on a scale of 100-900) |
Languages | English, Japanese, Portuguese and Thai |
Testing Provider | Pearson VUE |
CompTIA Security+
CompTIA Security+ is an entry-level certification covering essential security concepts and practices. It validates knowledge of network security, cryptography, and threat detection, making it a good choice for beginners and those pursuing IT security careers.
The exam details for the CompTIA Security+ course are as follows-
Exam Code | SY0-601 |
Number of Questions | Maximum of 90 questions |
Type of Questions | MCQs and performance-based |
Length of Test | 90 minutes |
Passing Score | 750 |
Exam Cost | USD 392 |
Testing Provider | Pearson VUE |
Languages | English, Japanese, Vietnamese, Thai, Portuguese |
CompTIA CySA+
CompTIA CySA+ is a mid-level certification emphasizing threat detection and analysis. It equips professionals with skills to monitor, analyze, and respond to security incidents effectively, making it valuable for security analysts and related roles.
The exam details for the CompTIA CySA+ course are as follows-
Exam Name | CompTIA CySA+ |
Exam Code | CS0-003 |
Exam Cost | USD 392 |
Exam Format | MCQs and performance-based questions |
Total Questions | 85 questions |
Passing Score | 750/900 |
Exam Duration | 165 minutes |
Languages | English, Japanese, Portuguese, and Spanish |
Testing Center | Pearson VUE |
Where can I learn these cybersecurity courses?
To learn the top cybersecurity skills in IT, you can choose Network Kings. Being one of the best ed-tech platforms you will get to enjoy the following perks-
- Learn directly from expert engineers
- 24*7 lab access
- Pre-recorded sessions
- Live doubt-clearance sessions
- Completion certificate
- Flexible learning hours
- And much more.
What are the available job opportunities after the cybersecurity training?
The top available job opportunities after the cybersecurity training are as follows-
- Security Analyst
- Cybersecurity Engineer
- Penetration Tester (Ethical Hacker)
- Security Engineer
- Incident Responder
- Security Architect
- Information Security Manager
- Security Administrator
- Network Security Engineer
- Cloud Security Engineer
- Application Security Engineer
- Identity and Access Management (IAM) Specialist
- Security Auditor
- Security Compliance Analyst
- Security Operations Center (SOC) Analyst
- Security Awareness Trainer
- Threat Intelligence Analyst
- Digital Forensic Analyst
- Security Sales Engineer
- Chief Information Security Officer (CISO)
What are the salary aspects for a cybersecurity-certified in IT?
The salary aspects for a cybersecurity expert are as follows-
- United States: USD 90,000 to USD 180,000 per year
- United Kingdom: GBP 45,000 to GBP 120,000 per year
- Canada: CAD 80,000 to CAD 150,000 per year
- Australia: AUD 80,000 and AUD 150,000 per year
- Germany: EUR 60,000 to EUR 120,000 per year
- France: EUR 45,000 to EUR 100,000 per year
- Singapore: SGD 60,000 and SGD 150,000 per year
- India: INR 600,000 to INR 2,500,000per year
- China: CNY 150,000 to CNY 400,000 per year
- Japan: JPY 5,000,000 to JPY 12,000,000 per year
- Brazil: BRL 80,000 to BRL 200,000 per year
- South Africa: ZAR 300,000 to ZAR 800,000 per year
- UAE (Dubai): AED 180,000 and AED 400,000 per year
- Saudi Arabia: SAR 120,000 to SAR 300,000 per year
- Russia: RUB 1,000,000 to RUB 2,500,000 per year
Wrapping Up!
The evolving landscape of cybersecurity in 2023 demands our utmost attention and adaptation. As technology continues to advance, the need to protect digital information, systems, and networks has become paramount. In this digital age, cybersecurity is not merely an option; it is an imperative. By staying informed, proactive, and well-equipped, we can navigate the ever-evolving cybersecurity landscape and safeguard our digital future. The secrets of cybersecurity in 2023 are out, and it’s time to act upon them to ensure a secure and resilient digital world for all.