
Despite a recession this year, Cybersecurity has been booming like no other industry. Thanks to the increased number of cyberattacks thus, calling in for the need for more cybersecurity professionals. In fact, the cybersecurity industry is set to face over 2.5 million unfilled job positions up until 2025. This is a clear sign that cybersecurity engineers are in so much demand. It is very important to prepare yourself for an interview if you are planning to enter the cybersecurity industry. In this blog, we are going to discuss cyber security interview questions and answers for both beginners and experienced candidates. We will also discuss some frequently asked questions at the end of the blog.
Without any further ado, let us start with the cybersecurity interview questions.
Cyber Security Interview Questions for Beginners
1. What is meant by cryptography?
Cryptography is a method that is used to protect confidential information from third parties. Therefore, it is a method to transfer confidential data without revealing the information to third parties that are not authorized to access the information.
It sends the data in an encoded manner so that no third party can decrypt it. Only the sender and the receiver can see the data.
2. What is meant by firewall? Why is it used?
A firewall is a network security system that acts as a barrier used to control, monitor, and filter incoming network traffic. It is used to block any harmful traffic such as hackers, malware, viruses, worms, etc. from entering the network system.
The uses of the firewall are as follows:
- It is used to maintain data privacy.
- It keeps a check over the incoming and outgoing packets of data (traffic). It only allows the information packets that follow the network protocols.
- It acts as a protection gate between the network and the incoming traffic from external sources like the Internet.
- It keeps malicious attacks away from the network system.
3. What is meant by VPN?
- If we elaborate the term VPN, it stands for Virtual Private Network.
- Its function is to connect the VPN client to the VPN server.
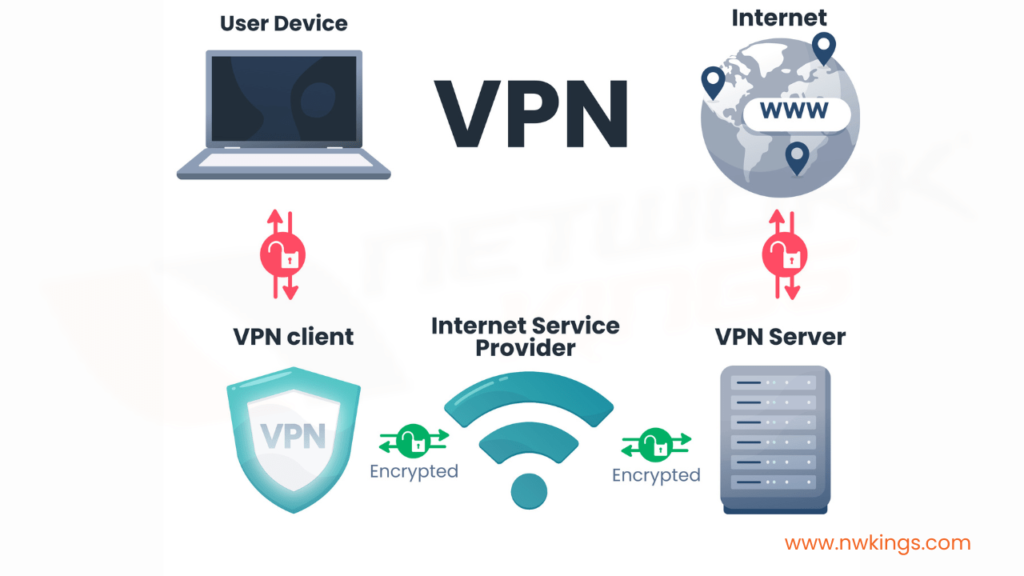
- The user device or the VPN client gets connected to the VPN server via an encrypted tunnel.
- This is how the information is sent and received by the Internet in a secure manner.
- VPN technology is mostly used in the corporate environment to protect sensitive data from being exposed.
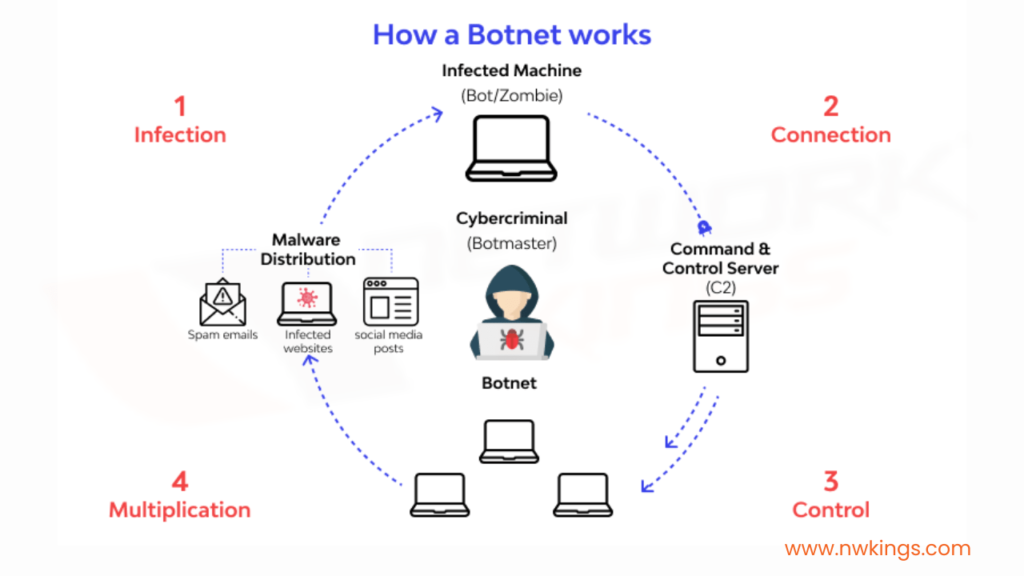
4. What do you understand by a botnet? How does it work?
A botnet refers to a group of Internet-connected devices such as laptops, PCs, servers, mobile phones, etc. These devices are often infected and controlled by malware.
Botnets can be used to attack a large number of devices if used to their full capacity by hackers.
A botnet works in the following way:
- An infected system or a device which is called a bot or a zombie computer is used to create a botnet.
- These devices work on the orders of bot herder’s commands.
- The bad actor finds out the vulnerability of the device that is to be infected.
- It then infects the user with the help of a malware.
- It then gains control over all the infected devices.
5. What are the different types of cybersecurity attacks?
Here are some of the most important cybersecurity attacks:
- SQL injection attack
- Malware
- Denial-of-Service (DoS)
- Cross-Site Scripting (XSS)
- Credential Reuse
- Phishing
- Session Hijacking
- Man-in-the-Middle Attacks
- Brute Force
- Domain Name System Attack
6. What is meant by the three-way handshake process?
A three-way handshake process is a data transmission process used in the Transmission Control Protocol (TCP/IP) network. It is a process that happens when a connection is built between a local host and the server.
It is a three-step process that occurs before communication starts to discuss acknowledgment and synchronization.
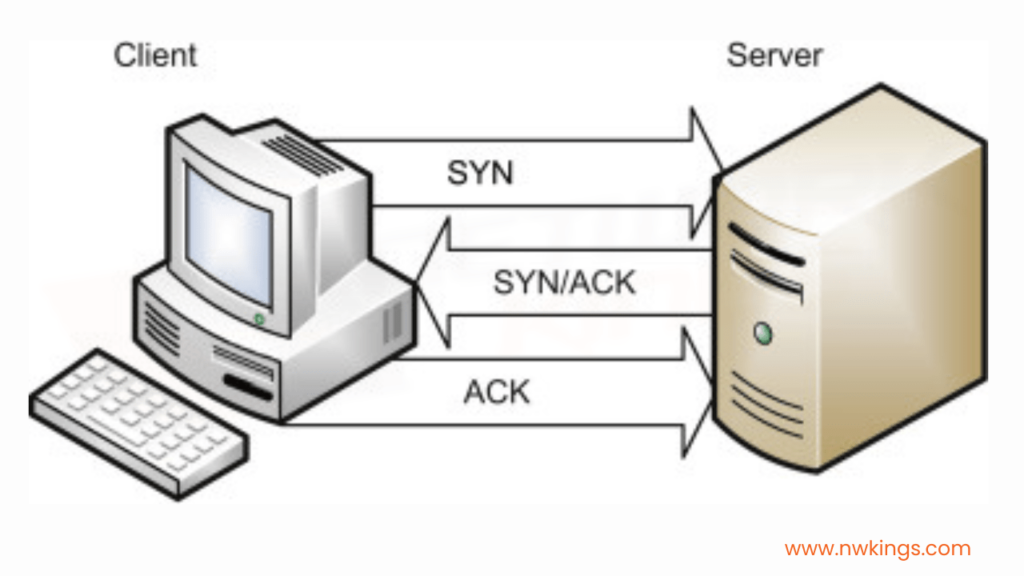
Step 1:
Using SYN, the client makes a connection with the server.
Step 2:
The server then responds to the request of the client with SYN+ACK.
Step 3:
The server’s response is acknowledged by the client with ACK. the actual data transmission then starts to occur.
7. What is meant by CIA Triad?
CIA Triad refers to a security model. It is a sustainable model designed to that handle policy for information security in an organization.
The CIA triad stands for the following three terms:
Confidentiality:
It is a group of rules that limits access to information. It is used to protect sensitive information from any third-party access which is not authorized to access it.
Integrity:
It makes sure that the information is reliable and true. It protects the data from getting modified by an unknown person who should not have access to it.
Availability:
It enables access to the authorized people of the data. It makes sure that the data availability to the client user.
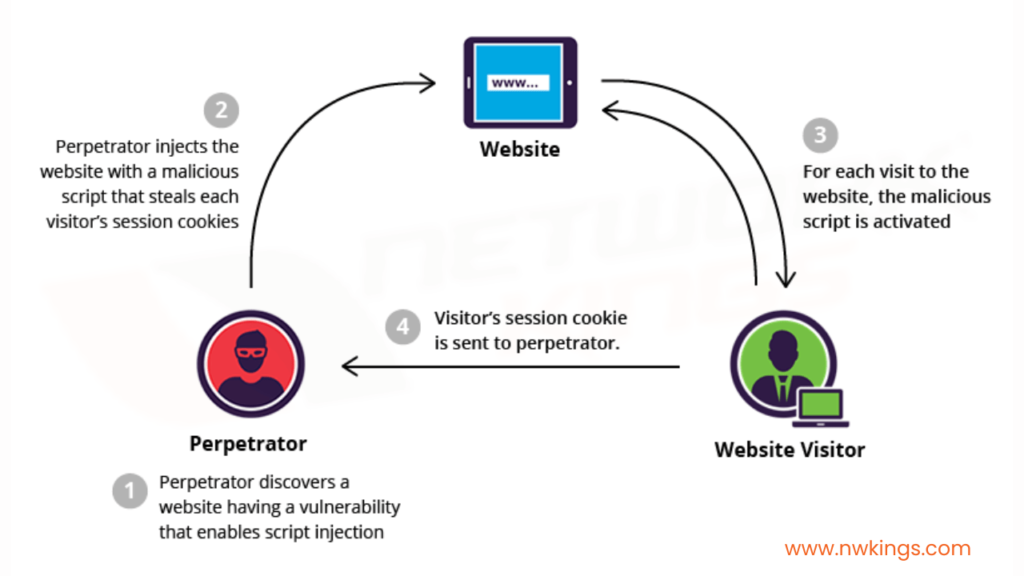
8. What is meant by XXS? How to prevent it?
Cross-Site Scripting also known as XXS is a web security shortcoming that can allow client-side injection attacks. It allows an attacker to modify how a user interacts with a particular web browser. The modifier does so by injecting malicious code into the user’s web browser.
The cross-site scripting allows the attacker to behave like the victim user and make undesirable changes.
The following steps can be taken to prevent cross-site scripting:
- Filter the user input on arrival.
- Encode special characters on the output.
- Use headers such as content-type and X-Content-Type-Options headers to make sure that the browser reads the required HTTP responses.
- Use anti-XSS tools or services.
- Use a Content Security Policy (CSP) to reduce the effects of remaining XSS issues.
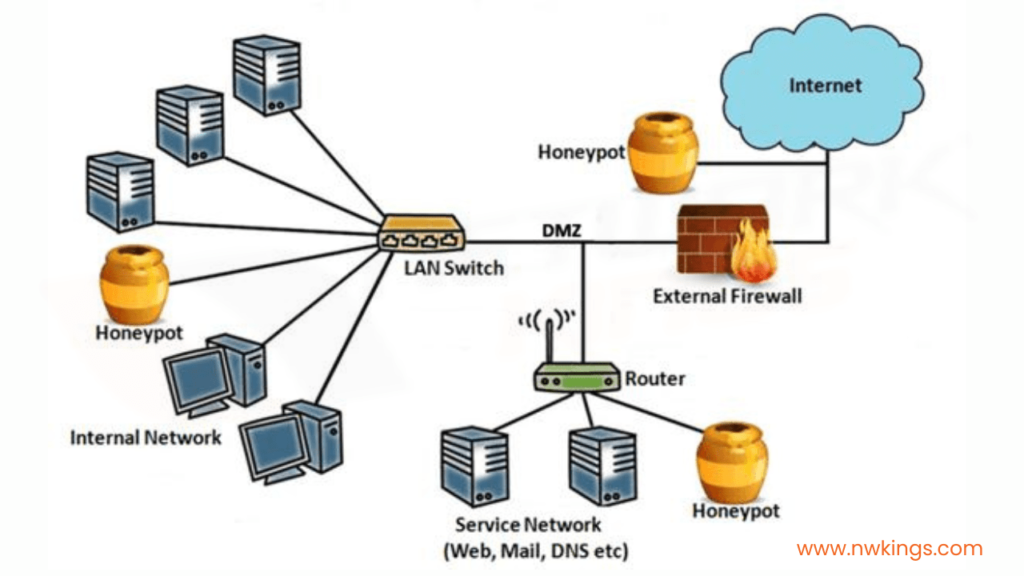
9. What is meant by a honeypot?
It is a bait to know how different attackers attempt exploits. It is used as an attack target. Most government and private firms can also use this concept to find the weaknesses in their security systems. This is also often used in educational setups.
10. What is Phishing? How to prevent it?
Phishing is categorized as a cyber attack in which the attacker appears to be a normal user such as a business personnel, co-worker, trusted website, etc., and attempts to steal private/unauthorized information through fake pop-up messages, calls and emails, etc.
They also often send some foreign link to the user to set it as a trap for the legit user. When the user taps on the link, the attacker gets access to the user’s device and can control it remotely.
Phishing can be prevented by taking the following measures:
- Always verify a website’s security. Do not surf on untrusted websites.
- Always use VPN when surfing online.
- Make use of good firewalls such as Palo Alto, CheckPoint, etc.
- Make sure that you use anti-phishing tools such as McAfee, Sophos, etc.
Cyber Security Interview Questions for Experienced
11. How to know the difference between Black Hat, White Hat and Grey Hat Hackers?
Black Hat Hacker | White Hat Hacker | Grey Hat Hacker |
Also referred to as a cracker, a black hat hacker accesses an unauthorized system to steal important data. | He is also known as an ethical hacker. His aim is only to strategically protect a computer network system by breaking into the system with the organization’s permission. | His responsibilities include both of white and black hat hacker. They hack the system without an organization’s permission. |
He performs activities such as injecting viruses, malware and worms. | His purpose is to find loopholes in the computer network system. They perform penetration testing and vulnerability assessment. | They figure out the flaw in the security system in order to get it acknowledged by the owner for a small reward. |
12. What is meant by port scanning?
It is an application designed to look out for open ports and all the other services available on a host network. It is mostly used by security administrators for exploiting vulnerabilities and by hackers for targeting online users.
The following are the most popular scanning techniques are as follows:
- TCP connect
- UDP
- TCP half-open
- Ping scan
- stealth half-open – NULL, FIN, X-MAS
13. What is SQL injection? How to prevent it?
SQL injection or SQLi is categorized as a code injection attack. It manages to implement malicious SQL statements to control a database server present behind a web application. It is used by the cyber attackers to access, delete and modify unauthorized data.
You can prevent SQL injection attacks by following ways:
- Make use of stored procedures
- To include prepared statements
- To update your system
- To store database credentials encrypted and classified
14. What is meant by man-in-the-middle attack?
The man-in-the-middle attack is a type of eavesdropping attack which tries to make independent connections with the victim and mimics messages between them as if they are having a private conversation.
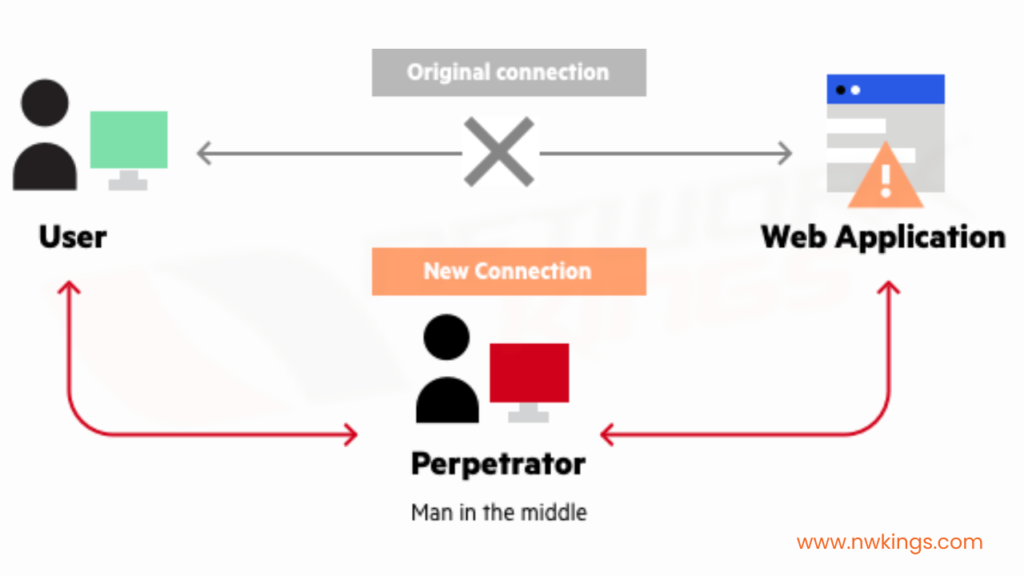
The main objective of this attack is to gain access to any company’s private information. For example, Lenovo computers were installed with pre-installed adware that made users vulnerable to MiTM attacks. This happened in 2015.
15. What is a salted hash?
Sometimes, when two users use the same password, it causes the formation of same password hashes. That password can easily be cracked using a dictionary or brute-force attack. A salted hash is implemented in such a case in order to avoid such attack.
It is therefore, used to join a random string called salt to the password before hashing.
Bottom Line:
This blog is the perfect free guide for anyone who is appearing for an interview for a cybersecurity role. This guide consists of Cyber Security interview questions and answers for beginners as well as Cyber Security interview questions for advanced candidates.
You can go through these important questions to ace in your next cybersecurity interview.
Happy studying!



