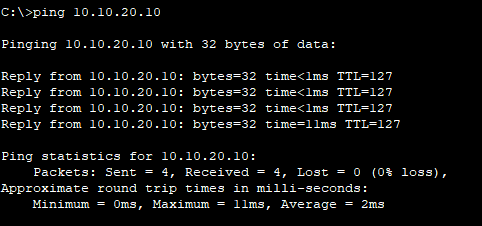
Are you curious to know about what is IT networking and how it can benefit your business? You are in luck! IT networking is vital for modern businesses; it enables information sharing, data exchange as well and remote connectivity solutions. It’s also a fundamental element when building network infrastructure – allowing multiple devices to communicate with each other.
In this blog post we will be taking an in-depth look into what exactly networking consists of, and explain why it is so essential for companies trying to reach their targets.
What is IT Networking? Explain

IT Networking is an idea that is becoming more and more significant in today’s tech landscape which never remains the same. It involves connecting different computers, devices or any other networking components so they can swap data between them. This could include using cables like ethernet cable for a wired network as well as Wi-Fi connection to build a wireless one – both types of networks ultimately allow all connected nodes within the interconnected system to exchange information with each other seamlessly. How cool is that?
Gaining a grasp of IT Networking requires gaining an awareness of the fundamentals related to establishing and maintaining networks. This includes being knowledgeable about local area networks (LANs), wide area networks (WANs), virtual private networks (VPNs), routers, switches, firewalls as well as other various elements that are used in constructing a network.
Furthermore, there are lots of kinds networking topologies which direct the shape from the network itself e.g. star topology or bus layout; ensuring these particular frameworks match your requirements is essential for setting up and taking advantage of your IT Networking system effectively. What sort of model would be effective for my setup?
Having an appreciation of the fundamental components involved in an IT Networking system – including such physical equipment as routers and switches – it is also important to think about software requirements. To initiate efficiency, special programs need to be employed that regulate traffic within your network from external sources competently; not having these programs can lead you into security troubles when trying to retrieve data from outside the local area network.
Firewalls are other kinds of safety protocols which are vital for keeping unwanted users away from secure information inside your internal system; make sure you come across one suited exactly to what you require.
Lastly, sustaining a consistent agenda for supervising and modernizing software will keep your IT Networking functioning optimally at all times with no risk of burglaries or malfunctions due to being behind on security measures. Also, it is wise to advise that you consult professionals who specialize in IT Networking if any strange problems occur with regards.
The Importance of IT Networking in Today's Digital Age
IT Networking is a vital part of life in this digital age. Its purpose is to create links between people, systems and data for the betterment of communication over the Internet. This IT strategy lets businesses build up their internal and external networks which can lead them towards making more money – not bad!
Also, through networking with other companies or individuals, companies can expand their customer base and get access to new markets which could result in increased sales opportunities. Sounds like an opportunity worth taking advantage of?
IT Networking is a key element of staying abreast with the latest trends such as cloud computing, virtualization, security measures and many more. It helps ensure that organizations are up-to-date with cutting-edge technologies which can assist them to work efficiently and effectively. Moreover, IT Networking enables data transfer between departments within an organisation without needing any third-party systems or external professionals – this could help cut costs whilst bettering business procedures.
In today’s digitalised world, maintaining good networks has become ever more relevant for corporations who depend on technology for their functioning processes; from connecting divisions inside or corresponding externally with customers/partnerships – having a secure network system facilitates all those involved to complete tasks speedily yet skillfully while keeping it safe.
And of course, there’s also the matter of securely storing important information safeguarded against malicious activity; plus allowing organisations to make decisions quickly based upon corky insights into accurate data sets. Surely one cannot underestimate how crucial IT networking is these days!
Diving into the Elements of Network Infrastructure

When it comes to IT Networking, one of the essential areas to understand is network infrastructure. This refers to hardware components that enable communication between devices connected to the same system. It involves switches and routers which process data before sending it over the Internet – plus software packages such as operating systems and anti-virus programs for secure communications.
What’s more, these all need to work together with equipment to make sure your network remains sound from any malicious activity online! So you might be asking yourself how can I ensure my data is protected?
When it comes to networking, cables are the fundamental building block of any connection. They provide a conduit for data travelling between different parts of your network and can be either wired or wireless depending on what technology is being used in the system. Networking devices come in two varieties – active gear such as routers and switches that send out information; and passive components like bridges which enable connections but don’t actively transmit anything themselves.
Routers take care of forwarding data packets from one network to another while switches create links among computers within local area networks (LANs). It’s worth mentioning that without these various elements working together harmoniously, communication across our digital networks would become an impossibility!
Knowing the fundamentals of servers, LANs, endpoints and other network components can be helpful when setting up a network infrastructure. For instance, if you need to boost your bandwidth or storage space on the system, you could easily add in some extra servers without having to redo all of the wiring as well! You could also switch out clunky old routers with ones that have faster speeds – this is only possible once you know how every bit fits together. Knowing these elements comes into play while troubleshooting too; it helps pinpoint any problems within its structure so they can get sorted quickly.
An Insight into the Role of Network Infrastructure in IT Networking

IT Networking is a subject that involves putting together, configuring and keeping up numerous types of networks. Usual sorts of systems incorporate Local Area Networks (LANs) and Wide Area Networks (WANs). Comprehending the different parts of IT Networking can make it simpler for people to both comprehend and advance their network infrastructure.
A major component of any IT Networking setup is the basic framework. This implies the physical wiring, equipment, programming and gadgets which are utilized to set up LANs or WANs. It’s essential to get this right as this structure will be fundamental in making sure about your system against unapproved access and guaranteeing you have fast transfer speeds while sharing data over various areas or customers inside a similar area.
Network Infrastructure includes routers, switches, firewalls, modems and other apparatus which help transfer data between computers or servers on the same network or through the internet. What’s more, IT professionals can use management software to control how these devices interact with each other on the network. Security is another vital element of any infrastructure too. This involves setting up regulations for who can access different parts of the network as well as firewall settings; being a significant barrier between internal and external networks by blocking off unwelcome links from malevolent attackers..
By configuring security correctly, IT professionals can make sure that only permitted users have access to particular areas of a network while stopping unauthorized people from getting in too. What’s more, there are instruments available for tracking network use such as bandwidth utilisation or traffic patterns over numerous sites. These types of tools let IT experts observe how their networks are being employed so they can enhance their performance better and identify any possible issues before they become serious ones.
To sum up, networking infrastructure has an indispensable role when it comes to linking devices together and exchanging data and resources through vast distances between businesses or departments. Though understanding everything related to this field might be demanding at first glance, having an excellent grasp of its fundamentals will prove invaluable when constructing or keeping a secure yet efficient network environment is required.
Unravelling the Process of Data Exchange in IT Networking

IT Networking is a hugely intricate area. It concentrates on how computers are linked together, share resources and interact with one another over the same network. Data transfer holds an essential place in IT Networking as it permits computers to swap info and data between them. But what exactly happens during this process?
To begin with, exchanging data requires some kind of system that’s composed of different components such as hardware for computer systems, networking tools, applications and protocols. All these pieces must be set up correctly so that machines can communicate across the connected network effectively. How do you make sure all those elements align properly though?
Take, for instance, a computer network. For each device to be identified by the others on there it needs its IP address. What’s more, these components need compatibility with data formats which will be sent between them so successful communication and information exchange can happen. In addition to this protocols like TCP/IP (Transmission Control Protocol/Internet Protocol) or UDP (User Datagram Protocol) govern how messages are packaged up and despatched across the web from one machine to another.
When it comes to exchanging data over a network, there are various measures in place to ensure security. This includes authentication which verifies that the user is who they claim to be before allowing them any access and encryption which ensures secure transmission of messages so as not to get intercepted by malicious entities or exploited. Not only this but protocols also specify how errors should be managed such that the message can still reach its intended destination properly even when issues occur during the transfer process.
Altogether these aspects add up to what we call IT Networking – offering users trustworthy connection points between different networks and systems, enabling us to securely move information from one location to another without worrying about contamination from external sources.
Role of Data Exchange in Ensuring Effective Communication
Grasping how IT Networking functions is indispensable for any enterprise. It facilitates the sharing of data and intelligence, constructing a proficient working atmosphere where colleagues can work together without struggles. Data transfer stands as one of the most pivotal elements of IT networking, providing effective communication between people.
In layman’s terms, data exchange is switching info from one device to another through a network – like the internet – maybe forwarding documents or archives within an organisation or exchanging messages amongst individuals; in short making it easier than ever before to collaborate with others!
Data Exchange guarantees that every participant in an organisational network can access information swiftly, helping them to remain on top of any changes within the company or contact other businesses outside their circle. By using Data Exchange, organisations are providing staff with the latest technologies and systems which ultimately allow for improved efficiency at work – plus it saves money; no need to spend a fortune on manual processes or hardware improvements!
Data exchange is vital for securely sharing sensitive information and financial transactions. Companies can set up secure networks that only authorised personnel have access to, thus preventing unauthorised use or tampering of confidential info. Encryption methods and other security measures mean data stays safe during transfers across different network systems. Plus, organisations gain a useful understanding of how their network is being used if they look at usage stats like which users are accessing what files and when.
All in all, data exchange is essential for effective communication between members of a company’s system – it offers an easy way for people to share data fast while cutting expenses related to manual techniques and hardware updates; by using safety features such as encryption methods plus user monitoring tools companies will be assured their private details remain protected throughout transfer over public networks — providing them greater assurance about their operations long-term! What more could you want?
Introduction to Connectivity Solutions in IT Networking

IT networking is the idea of hooking up various computers and other gadgets in one network, permitting them to swap resources and data. It eliminates the need for separate computers to be linked physically and allows them to communicate with each other as if they were a single unit. Connectivity solutions in IT networking refer to all sorts of systems used for setting up this kind of communication among different machines.
One example of such a connectivity solution can be seen in Ethernet; it’s employed for connecting multiple computer systems over networks – which does away with having physical connections between individual devices!
Ethernet is a great way to quickly transfer files and other types of data between computers that are connected to the same network. Not only this but it can also be utilised for virtual private networks (VPNs), connecting remote systems or locations securely.
Another popular option these days is Wi-Fi – ideal for laptops, tablets and smartphones as they don’t need cables or wires to connect to the internet! Instead, radio signals are used which makes setup simple and maintenance hassle-free. It’s no wonder why so many people rely on WiFi nowadays; within seconds you have access to an array of possibilities at your disposal!
Whilst not as quick as Ethernet, it still provides a dependable connection which can be accessed from anywhere in the network’s coverage area. Another preferred connectivity resolution among IT networking is Bluetooth technology. By connecting two devices within proximity of each other without wires or cables, Bluetooth works its magic – quite frequently used for wireless headsets while making phone calls and also streaming audio from music players directly into headphones or speakers minus having to plug them into any device.
When we look at recent years’ developments, cloud computing has become incredibly popular when it comes to discovering the right connectivity solution for IT networking; how do businesses benefit most from using this type of service? Rather than storing data on local hard drives, cloud computing entails utilizing remote servers to store data which then allows users with an internet connection to access their information from anywhere.
This also facilitates the ability for multiple individuals working on shared projects from disparate locations all across the world by permitting them to upload documents and make changes at once without having any apprehensions over file compatibility predicaments or geographical locale-based bans. In other words, right at your fingertips you have all these possibilities – who would’ve thought?
You can see that there are lots of different connection options for IT networks today, from which people all over the world can stay connected. This includes means like file sharing, video conferencing and online collaboration tools – no matter where they’re located in the globe. By utilizing these various connections effectively we make sure everyone has access to similar material regardless of their physical separation; this will cause us to get better outcomes overall when it comes to successful collaborations in any field!
Exploring the Significance and Function of Connectivity Solutions
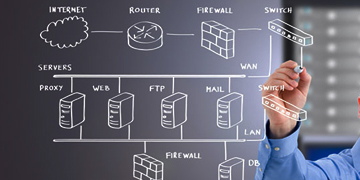
Staying connected and making sure data keeps flowing between devices is vital, so IT Networking provides a range of connectivity solutions. These ensure efficient communication happens with computers, networks, apps and any other relevant devices.
These connections exist to help transmit information over long distances – by cables or fibre optics; wireless transmission; satellite tech etc., allowing organisations to share info and resources quickly but securely too.
An example of connectivity solutions is when multiple users can access a network printer from their workstations at the same time, or everyone on your network can get documents that are stored on one shared computer. Connecting different physical locations helps bring people in those places closer together – making it so folk don’t have to be physically present for them all to communicate and collaborate as if they were. This comes with a bonus too: increased security!
So not only does this make working collaboratively easier but it also safeguards against malicious actors getting into your systems. It’s quite remarkable what these solutions allow us to do really – there’s nothing we can’t achieve even if folks aren’t side-by-side in person!
As the growth of handheld devices such as laptops, tablets and smartphones continues on an upward trajectory, many companies are embracing secure connectivity solutions so that they can have data accessible remotely without any risks to its security or integrity. The implementation of encryption technologies like Secure Socket Layer (SSL) or Transport Layer Security (TLS), means that even when using public networks – including Wi-Fi hotspots – invaluable protection is granted against any unauthorised access.
Moreover, cloud-based services also bring both scalability and reliability to the table – customers gain control of their IT systems via one service provider alone; reducing costs associated with managing various relationships with different vendors whilst simplifying everyday business operations through uninterrupted backups eliminating the majority of hassle.
To conclude modern-day networking has long since stepped up a notch thanks to improvements in regards to bettering connectivity solutions which help organisations stay connected more efficiently than ever before allowing them to deliver quality products quicker than before!
The Relevance of Remote Access in IT Networking
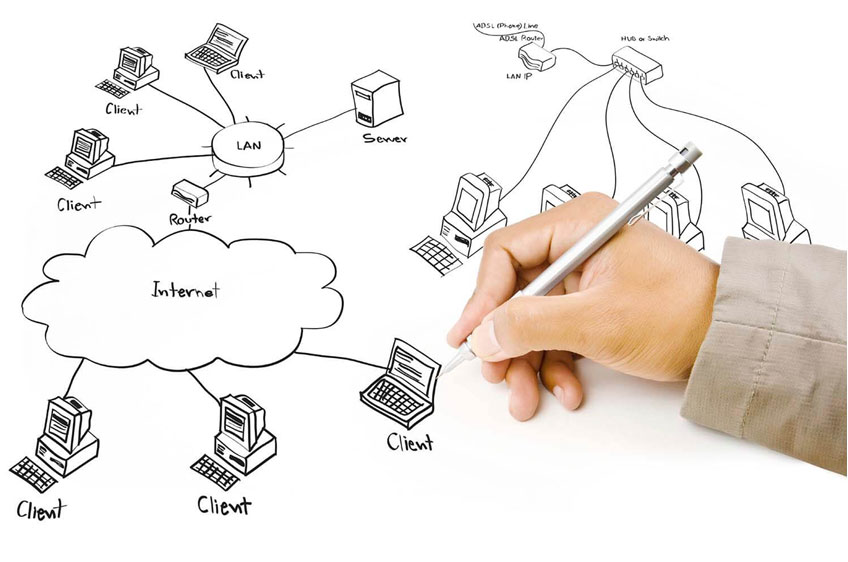
IT Networking is an ever-changing business and one of the key components of IT Networking which has developed significantly as of late is Remote Access. This allows people and organisations to securely link up with a corporate organisation or its resources using the internet, giving users access to data and applications like they were actually inside their office environment. So what makes it that important for IT networking?
To begin with, Remote Access enables organisations to get around physical restrictions; you no longer need everyone present in your workplace if you wish them all to have access to confidential files – now workers can set themselves up at home! Not only this but instead of needing extra hardware such as multiple servers or cables running through walls connecting computers (which are both costly investments) staff members from different sites can communicate more efficiently with each other without having any actual face time needed.
What’s even better about remote connections is that there isn’t anything preventing team collaboration across distant locations either: setting up video conferencing calls takes seconds rather than hours when done remotely.
Having the ability to access resources remotely can enable innovation across departments, no matter where they’re based or what time zone – potential for assigning project tasks and sharing information with colleagues who are further away. It also means costs don’t have to be pumped into physical hardware such as servers, which is a real headache when it comes to setting up and maintaining them. Are there other cost-saving strategies that could benefit businesses? How about creating efficient processes or taking advantage of cloud technology?
Organisations could instead choose cloud-based solutions and access their data remotely without having to be concerned about the expense of physically hosting a server. Remote Access also provides greater security by allowing organisations to manage their IT systems securely from any place, at any time. Moreover, with remote access services monitoring usage and recognising suspicious activity, organisations can take quick action to safeguard their data against potential cyber threats or malicious attacks which might damage networks.
All things considered, Remote Access is an essential part of IT Networking and its value cannot be overstated: not only does it enable businesses to run more effectively but it safeguards them as well whilst decreasing operational costs – what’s there not to love?
The Future of IT Networking: How Remote Access is Changing the Game

IT networking is at the heart of modern life. Whether it’s linking networks together or establishing data conduits, businesses rely heavily on successful IT networks to operate. As technology progresses, so too does the area of IT networking – and one of its most significant advances is remote access.
Essentially speaking, remote access grants users secure network capability from any position they choose. This gives personnel a chance to work away from their offices if needed – eradicating geographical barriers and traditional working hours alike!
Cloud-based systems becoming more commonplace has made this type of connection almost essential in certain business areas, and it is only going to become increasingly important. This brings a few key benefits when it comes to the maintenance and security of networks. Because connections can be formed between different places without having to physically wire everything together, IT teams save loads of time and effort keeping things running smoothly – one less headache for them! What’s more, even over long-distance links encryption measures can be implemented – thus adding an extra layer of safety regarding crucial data and networks.
Remote access also makes it easier for companies to provide support services without worrying about where customers may be located. Not all businesses can afford a big customer service team – but with the right setup, they might not even need one! By using remote access, these firms can keep their customer service running 24/7 and save costs in the process too.
The future of IT networking is looking very positive indeed! As more tools designed specifically for remote access solutions such as Virtual Private Networks (VPNs) are released constantly; this means that businesses now have an opportunity to cut down on expenses while still having secure connection between offices and workers; giving them extra freedom when managing operations at hand. It’s clear how much of an influence remote access has had on today’s IT industry – those who understand its potential will reap great savings from minimizing overheads along with improved business productivity overall going forward. Is your organisation making full use of this technology?
Wrapping Up!
In conclusion, IT Networking is a vital component of any organisation. It facilitates the safe and secure exchange of data within organisations as well as allowing for remote access to systems, applications and services if necessary. A good network infrastructure provides businesses with improved communication between their team members in both internal offices or remotely – something which can be massively beneficial when it comes to collaboration on projects etc. Knowing what networking is about and how it works means that users can make full use of this technology without risking security issues either way.
Are you considering taking your career in the rapidly flourishing and profitable world of network engineering to new heights? If so, why not enrol on our online Network Engineer Master Program? This advanced course will provide you with all the know-how and abilities necessary to become a success in this field. You will be granted access to an array of seasoned professionals who can dispense invaluable advice as part of your journey.
Also, learn about cutting-edge technologies, put newer solutions into practice – and get some essential hands-on experience – from any place that suits you best: whether it’s at home or work! Therefore don’t dally any longer – sign up straight away to start crafting a bright future for yourself today!
Are you looking to become a Network Engineer Master? Look no further than our exclusive Network Engineer Master Program! Our program gives the perfect chance for you to improve your skills in this field and get up to speed with the newest technologies. Our course comes equipped with top-notch training from experienced professionals who are devoted to aiding you in becoming an expert engineer. We have an exhaustive syllabus that covers all basic principles of networking plus its practical applications.
You will learn about network architecture, routing protocols, and systems management amongst other topics. Enrol today and begin your journey towards being a professional Network Engineer Master – we guarantee it won’t be something regretful! With our programme, there’s potential for you to become one of the leading network engineers around town. Thus don’t delay – enrol now and start making strides toward success!
Happy Learning!