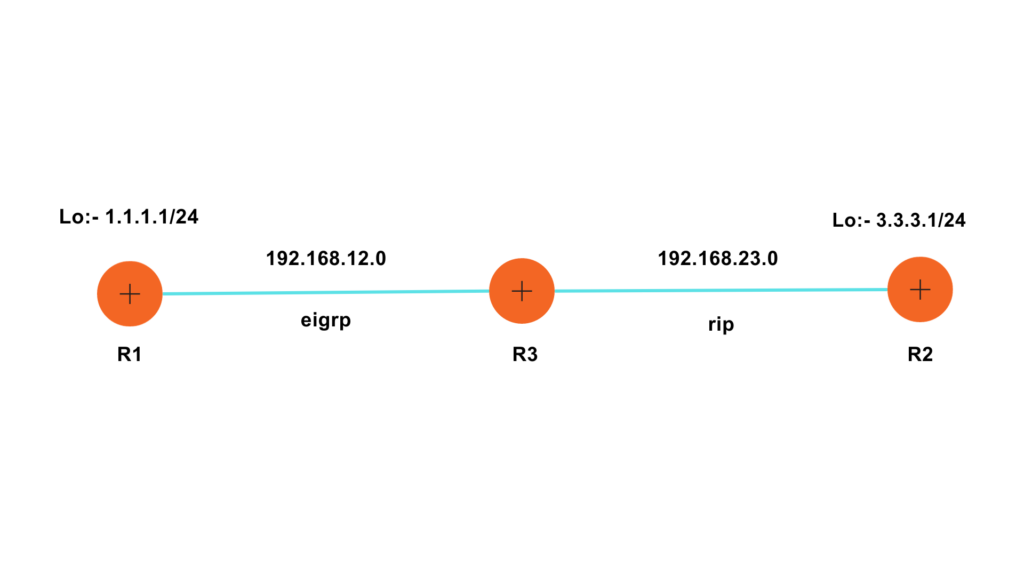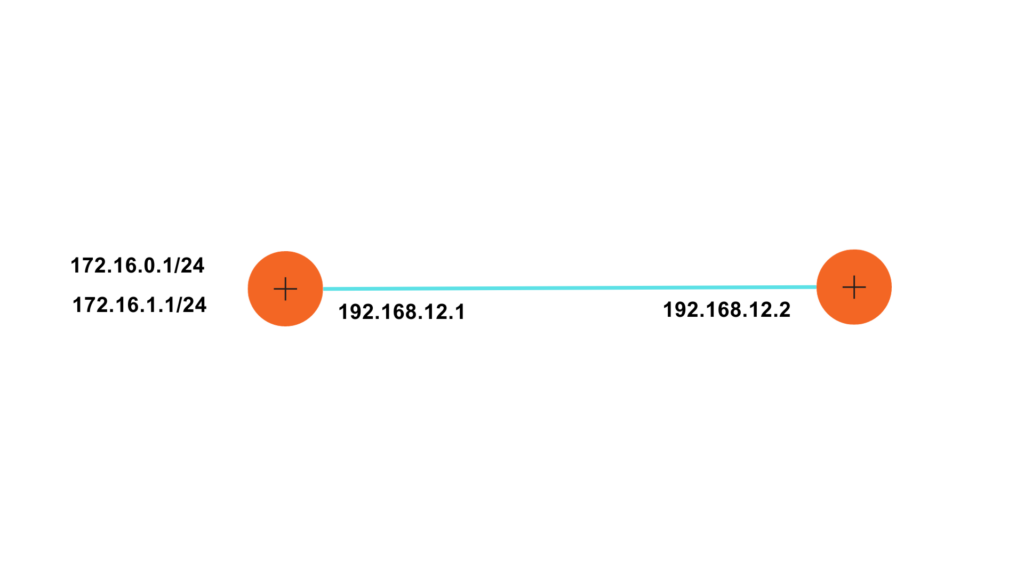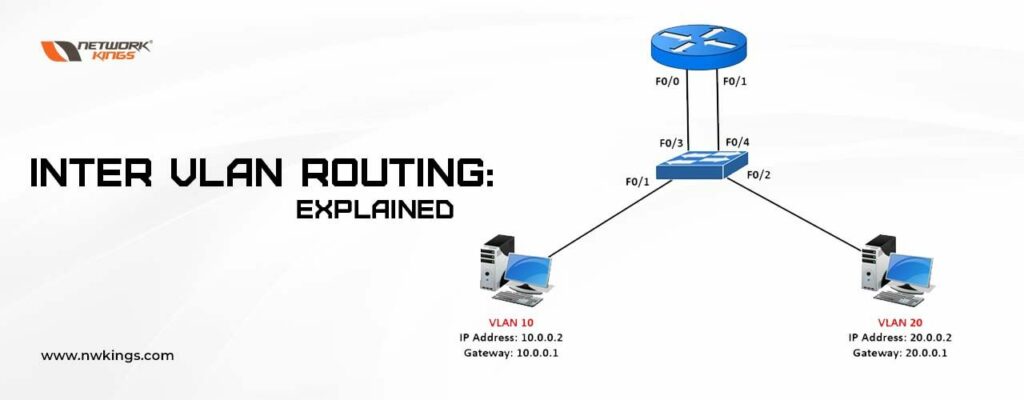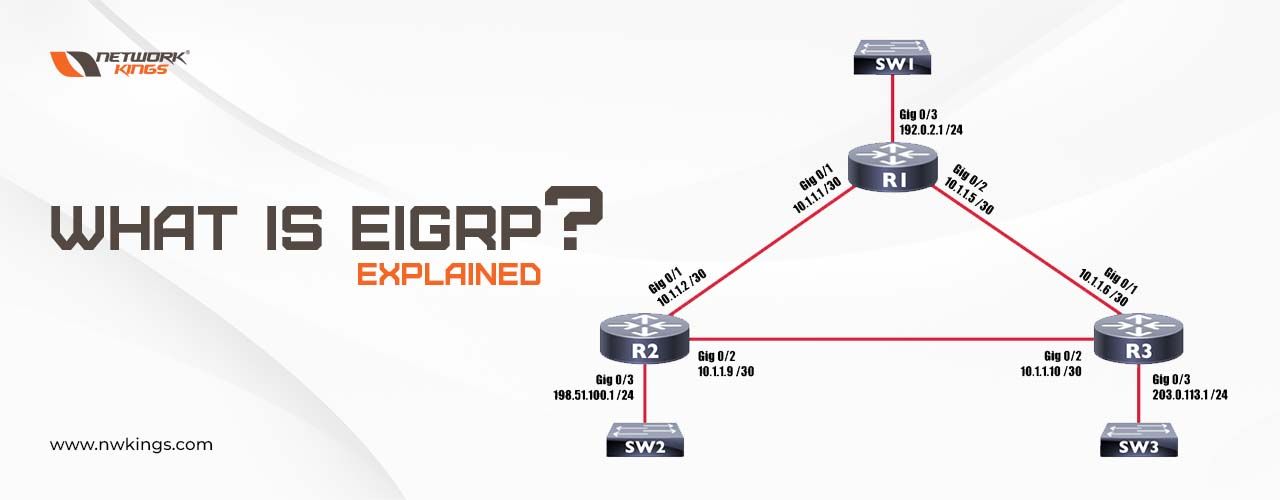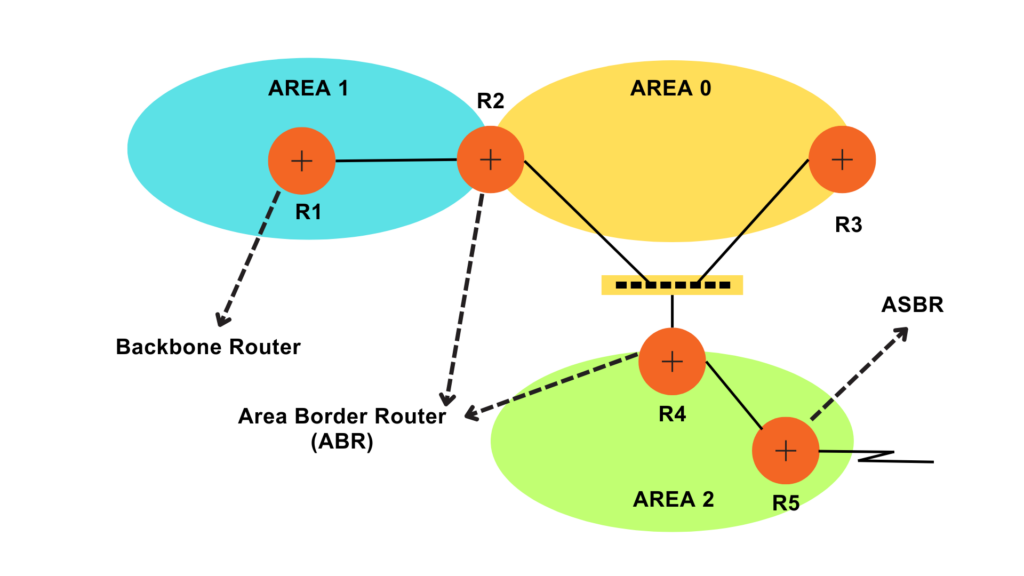
Until now, we have also learned about the network components such as routers and Wireless LANs. When you grant Internet access, your LAN is connected to the Internet via the router.
Therefore, a router plays a very important role in forwarding the data packets in a computer network. It is the one responsible for sending your packets from source to destination.
Note: If you haven’t read the previous blog of our CCNA 200-301 series, I highly recommend you do so.
In this blog, we will learn how a router uses a ‘routing table’ , the interface to which the data must be sent. We will also learn about all the information that a routing table stores inside it. Last but not the least, we will also learn the difference between static and dynamic routing.
Let us start learning about the routing table!
Devices such as routers and switches that are IP-enabled use routing tables. A routing table is updated dynamically via network routing protocols.
What is a routing table?
When a data packet has to be sent to a destination via the source, the router delivers the packet by following a set of rules. These sets of rules viewed in a tabular format determine where these data packets will be delivered. These are called a routing table.
You can view a routing table by using the “show IP route” command. When you use this command, you will be presented by something like the following:
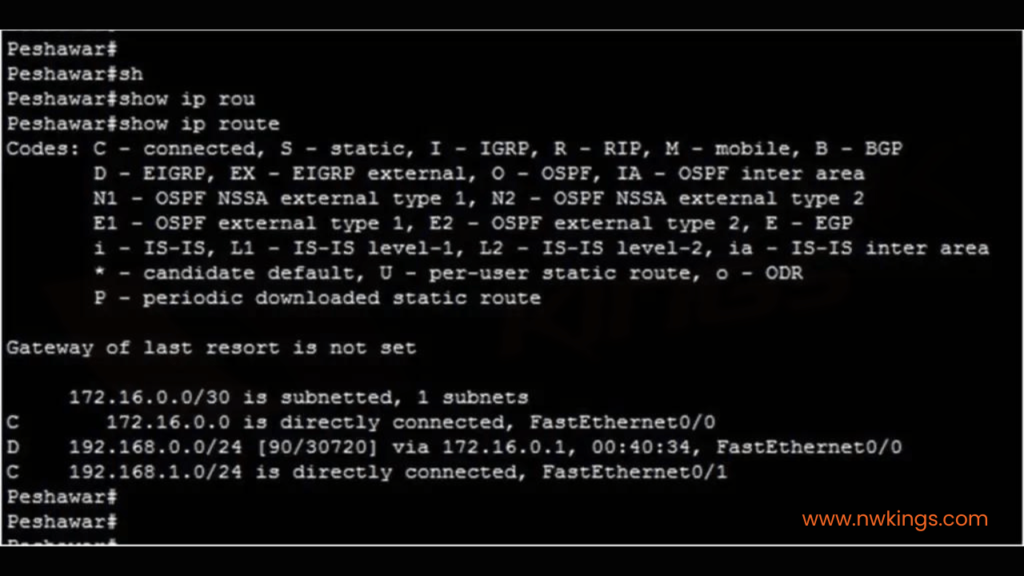
Devices such as routers and switches that are IP-enabled use routing tables. A routing table is updated dynamically via network routing protocols.
How Does a Routing Table Work?
A router has to make decisions on which interface it has to deliver the packets. A routing table helps the router to take these decisions effectively.
The routing table helps a router with the following most important piece of information:
- It tells the destination IP address to the router.
- It tells the best path to the router to reach the destination.
- It also helps the router to manage the network traffic every second.
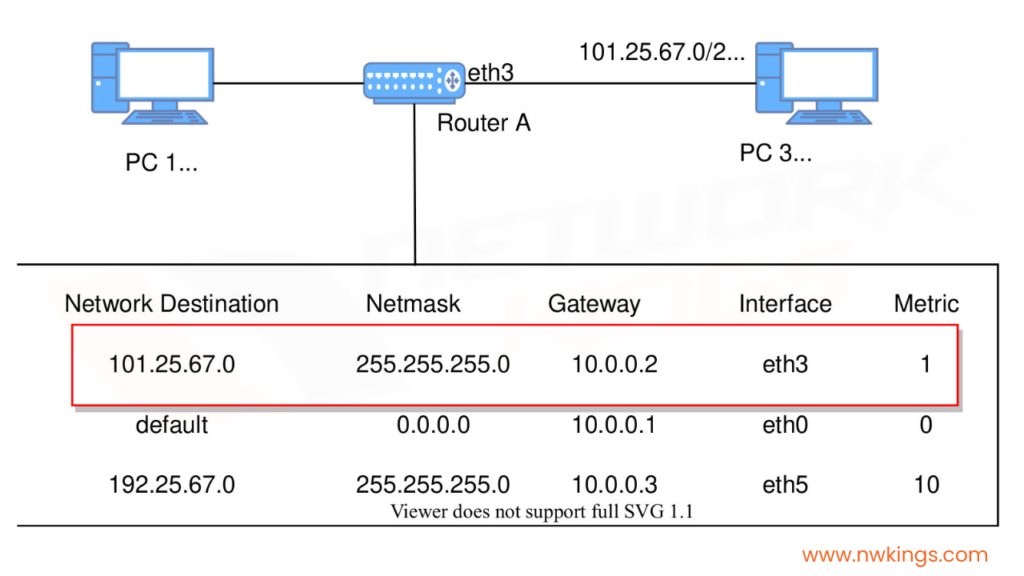
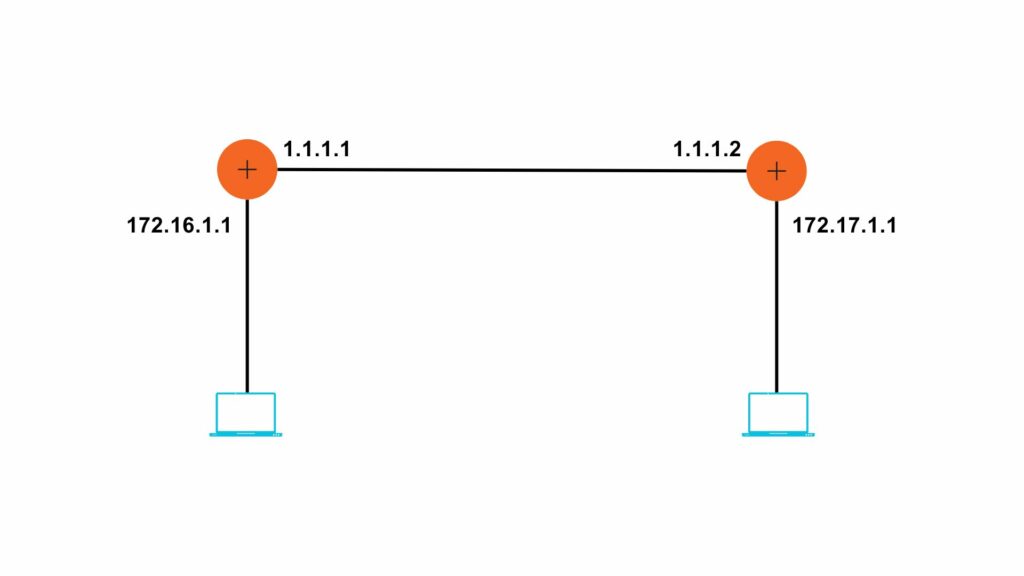
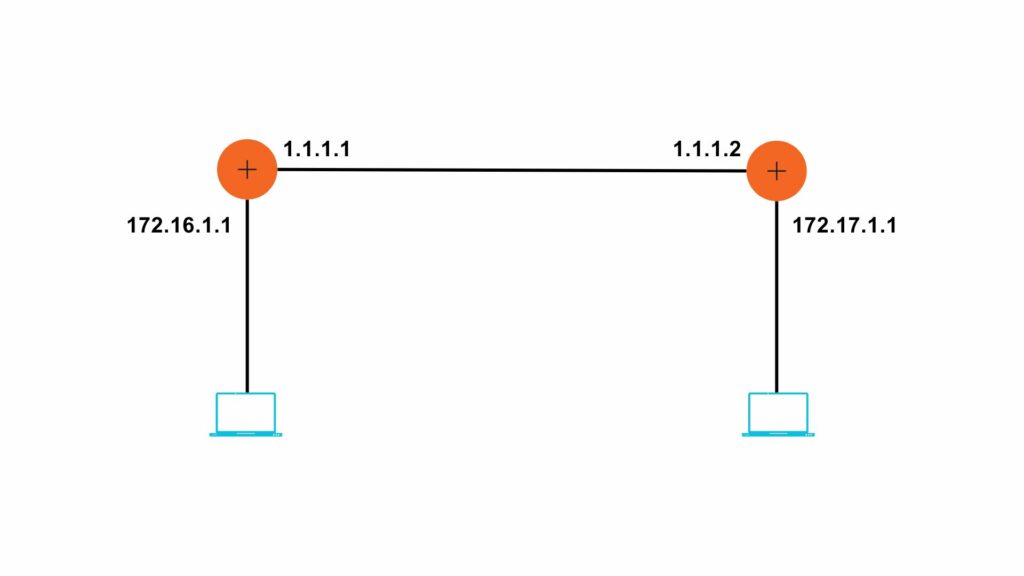
In the routing table as shown in the image above, the 3 metrics are the most important:
- Network destination:
It consists of the network ID of the destination.
- Net mask:
It consists of the subnet mask of the destination IP address.
- Interface:
It refers to the port at which the router is connected to the network.
Let’s understand all of these in detail!
What are the Routing Table Entries?
Routing table entries refer to the information that is contained in a routing table. It contains important information such as IPv4 and IPv6 address classes.
Note: The primary fields such as Network ID, next hop and cost or metric of a routing table do not change.
Let us learn about the various routing table entries:
- Network ID:
The Network ID is the ID of the destination that belongs to a route.
- Destination:
It is the IP address of the final destination that a data packet has to reach.
- Subnet Mask:
It is a 32-bit network address, also referred to as the netmask. It functions to match the destination IP Address to the Network ID. it tells whether the host is the local or remote network.
- Gateway:
It is the IP address to which the packet is forwarded to and is commonly known as the next hop.
- Interface:
A router could either be connected to the devices in the same network or outside a Wide Area Network (WAN). They mostly use Ethernet interfaces to connect to these devices.
- Metric:
It shows the minimum number of networks crosses or hops to the Network ID. it provides a value to each available route through which the packet can be sent. Then, it helps in selecting the best path.
The path with the lowest metric is chosen when there are multiple paths to the same destination network.
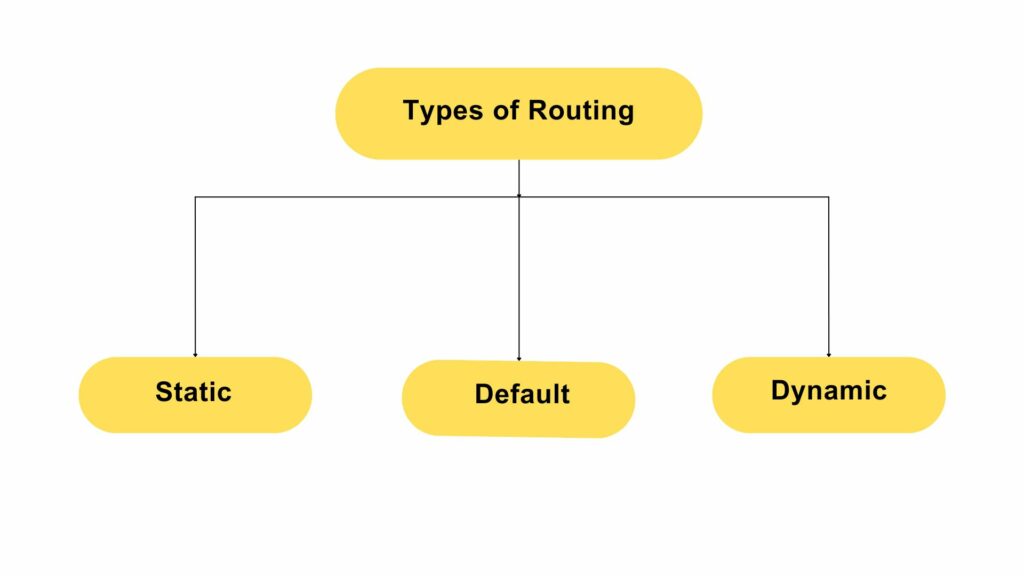
How are the Routing Tables Maintained?
A routing table can be maintained by:
- Using Dynamic routing
- Using Static routing
Let’s learn the difference between these two routing modes with the help of a table!
Dynamic Routing | Static Routing |
1. Routing protocols are used to build and maintain the routing tables automatically without any manual help. | 1. The routing tables are not changed until a Network Administrator manually changes them. |
2. They have multiple paths available to the destination. | 2. They have a single pre-configured path to the destination. |
3. The algorithms automatically update the routing tables. | 3. There is no automation update. |
4. It needs more computation time and bandwidth. | 4. It does not need more computation time or bandwidth. |
5. It is less secure. | 5. It is more secure. |
6. It uses distance vector algorithms such as RIP/IGRP as well as link state algorithms such as OSPF to adjust the routes. | 6. There is no use of algorithms. |
7. Entire routing table is used to identify the available paths. | 7. Only one entry in the routing table is used to identify the available path. |
8. It is used in large networks in big organizations. | 8. It is used in small networks in small-sized organizations. |
The above are all the important points that you need to know about static and dynamic routing.
Conclusion:
This marks the end of our introductory blog to the routing table. We have learned about what routing tables are and how they function.
This helps us understand and dissect how routers work. We also learned about how routing tables can be maintained. Further, we will learn more about networks in the upcoming blogs.
Stay tuned for the upcoming blog of our CCNA 200-301 series.
Happy Learning.