Routing is a process of selecting the best possible paths for data packets to travel from a source to a destination in a network. Routing is performed by layer 3 devices like routers and multi-layer switches.
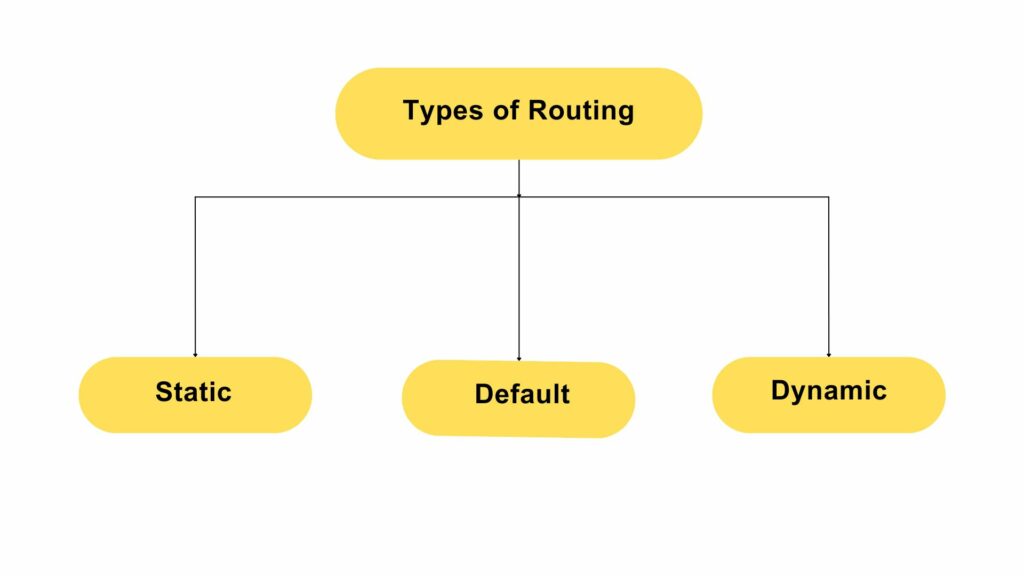
What are the different types of Routing?
Routing protocols can be broadly categorized into three types:-
- Static Routing
- Default Routing
- Dynamic Routing
Let us try to understand each type in brief.
What is Static Routing Protocol?
Static Routing is a process in which the network administrator will determine the path to reach unknown networks. So, in the case of static routing, the network administrator will configure the router’s routing table manually.
In case any change occurs in a network, the administrator has to reconfigure the route, and changes do not take place automatically. Static routing is simple to configure and suitable for small-scale enterprises.
How to configure Static Routing?
Static Routing can be configured in two ways, namely-
Static Routing with the Next Hop
In this type of static routing, the network administrator will tell the router about the next hop address, i.e., the neighboring router interface IP to reach a particular network.
Syntax for static routing with the next hop:
Enter Global configuration mode.
Device# configure terminal
Device (config)# ip route <Destination N/W IP> <Destination subnet mask> <Next hop IP address>
Static Routing with an Exit Interface
In this case, the network administrator will configure the router about the interface from which a packet will exit for an unknown network. Most commonly, this protocol is used when routers are connected with a serial cable. The serial cable does not use the Mac address.
NOTE: If Mac addresses are not used, then proxy ARP will not be generated.
Syntax for static routing with an exit interface:
Enter Global configuration mode.
Device# configure terminal
Device(config)# ip route <Destination N/W IP> <Destination Subnet Mask> <Exit interface>
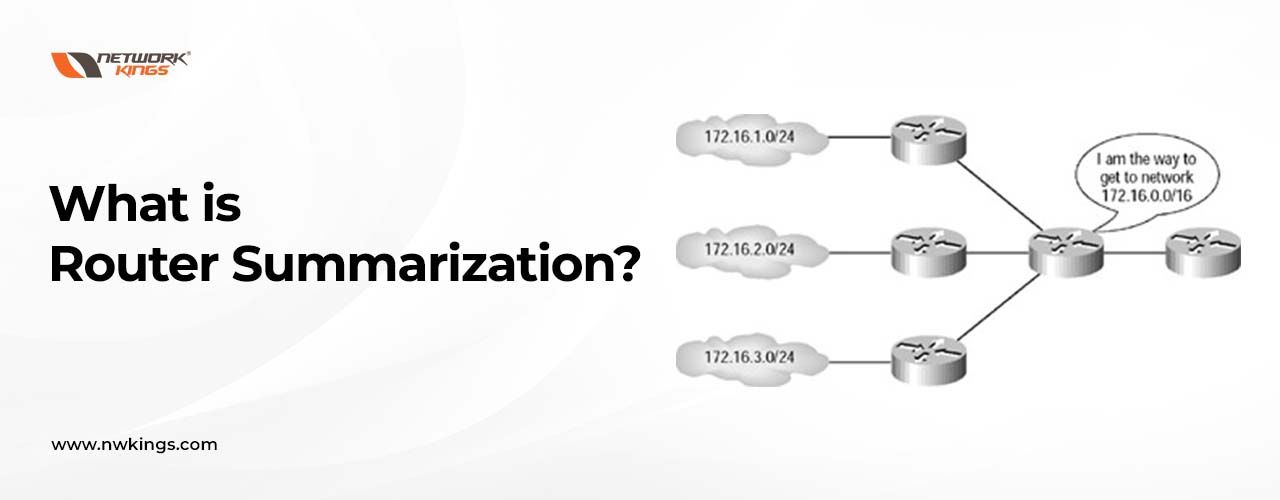
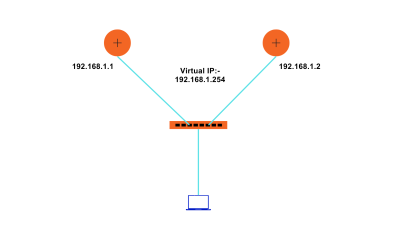
Configuration:- Let us take an example of a small topology given in the figure.
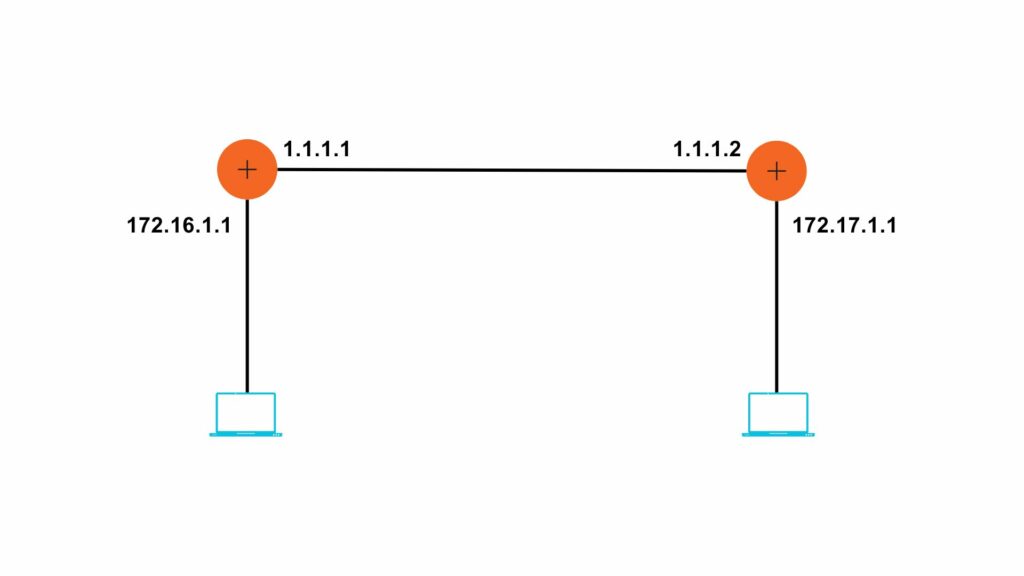
R1
R1#config t
R1(config)#ip route 172.17.0.0 255.255.0.0 1.1.1.2
R2
R2#config t
R2(config)#ip route 172.16.0.0 255.255.0.0 1.1.1.1
Verification: –
R1#show ip route
Codes:
L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2, E – EGP
i – IS-IS, L1 – IS-IS level-1, L2 – IS-IS level-2, ia – IS-IS inter area
* – candidate default, U – per-user static route, o – ODR
P – periodic downloaded static route
The Gateway of last resort is not set.
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.0.0.0/8 is directly connected, GigabitEthernet0/0/0
L 1.1.1.1/32 is directly connected, GigabitEthernet0/0/0 172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.0.0/16 is directly connected, GigabitEthernet0/0/1
L 172.16.1.1/32 is directly connected, GigabitEthernet0/0/1
S 172.17.0.0/16 [1/0] via 1.1.1.2
R2#show ip route
Codes:
L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2, E – EGP
i – IS-IS, L1 – IS-IS level-1, L2 – IS-IS level-2, ia – IS-IS inter area
* – candidate default, U – per-user static route, o – ODR
P – periodic downloaded static route
The Gateway of last resort is not set.
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.0.0.0/8 is directly connected, GigabitEthernet0/0/0
L 1.1.1.2/32 is directly connected, GigabitEthernet0/0/0
S 172.16.0.0/16 [1/0] via 1.1.1.1
172.17.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.17.0.0/16 is directly connected, GigabitEthernet0/0/1
L 172.17.1.1/32 is directly connected, GigabitEthernet0/0/1
What are the advantages of Static Routing Protocol?
The advantages of the Static Routing Protocol are as follows:-
- Easy to implement as compared to dynamic routing
- Less overhead on the router means minimizing the utilization of the device.
What are the disadvantages of Static Routing Protocol?
The disadvantages of the Static Routing Protocol are as follows:-
- It is not suitable to configure on a large network because the administration has to configure it manually.
- If there are changes in the network, like a new router being added or a network being removed, then the static entry must be added or removed accordingly.
- Recursive Lookup: When a routing table is checked more than once for a packet, this is known as a recursive lookup. This is a disadvantage with static routing with the next hop.
What is Default Routing Protocol?
When a router does not have the specific route entry for the destination network, default routing is used to forward packets to a default gateway or next-hop router. In other words, a router will send a packet to a preconfigured default gateway if the packet’s destination IP address doesn’t match any of the routes it has configured.
NOTE: Default routing is the type of static routing in which all the packets will be forwarded by matching the default entry in the routing table.
This routing protocol is mainly used at the edge router of the enterprise
There is a high chance of creating a loop in the network by default routing so we have to use default routing carefully.
Syntax:
Enter Global configuration mode.
Device# configure terminal
Device(config)# ip route 0.0.0.0 0.0.0.0 <Next Hop IP Address>
Configuration: – Let us configure the default route on the same topology
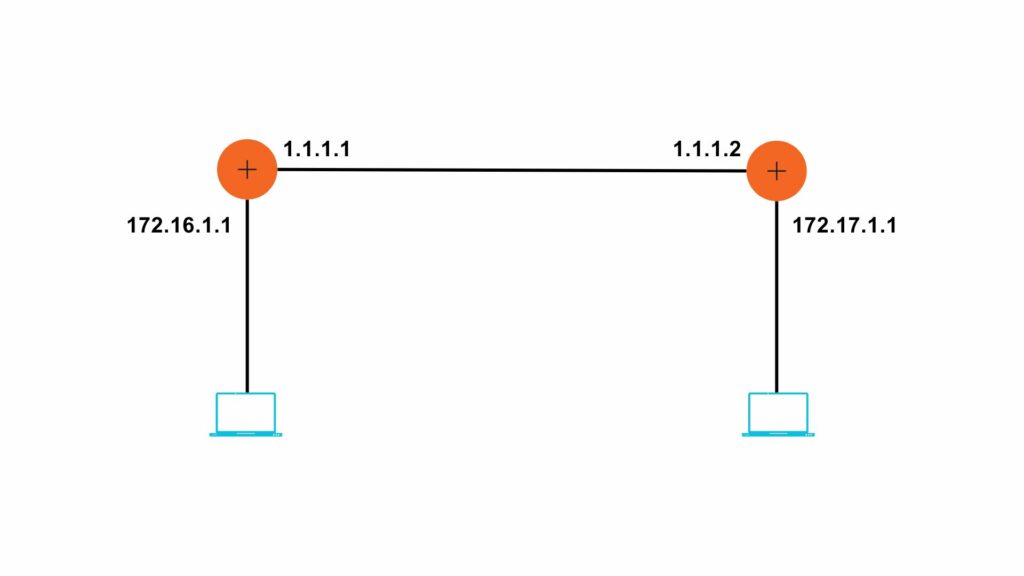
R1#config t
R1(config)#ip route 0.0.0.0 0.0.0.0 1.1.1.2
Verification:
R1#show ip route
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2, E – EGP
i – IS-IS, L1 – IS-IS level-1, L2 – IS-IS level-2, ia – IS-IS inter area
* – candidate default, U – per-user static route, o – ODR
P – periodic downloaded static route
Gateway of last resort is 1.1.1.2 to network 0.0.0.0
1.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 1.0.0.0/8 is directly connected, GigabitEthernet0/0/0
L 1.1.1.1/32 is directly connected, GigabitEthernet0/0/0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.0.0/16 is directly connected, GigabitEthernet0/0/1
L 172.16.1.1/32 is directly connected, GigabitEthernet0/0/1
S* 0.0.0.0/0 [1/0] via 1.1.1.2
Similarly, for R2:
R2(config)#ip route 0.0.0.0 0.0.0.0 1.1.1.1
Verification: –
R2#show ip route
S* 0.0.0.0/0 [1/0] via 1.1.1.1
What are the advantages of Default Routing Protocol?
The advantages of Default Routing Protocol are as follows:-
- Default routing simplifies the routing configuration by providing a single route for the network.
- Reduction in routing table size
- Easy to configure
What are the disadvantages of Default Routing Protocol?
The disadvantages of the Default Routing Protocol are as follows:-
- If an unauthorized device or attacker gains control of the default route, they could potentially divert traffic inappropriately.
- If a default route is misconfigured or points to an incorrect next hop, it can lead to traffic being misrouted or dropped.
- In complex networks with diverse destinations and traffic patterns, default routing might not effectively accommodate all routing requirements.
What is Dynamic Routing Protocol?
Configuring Static Routing and Default Routing is hectic, and when it comes to a large number of routes, it is not easy to configure each route manually. Dynamic Routing can automate this process.
Dynamic Routing protocols allow routers to dynamically learn and adapt to changes in the network topology. These protocols use algorithms to calculate the best path for packet forwarding based on various factors such as network congestion, link availability, and cost metrics.
Examples of dynamic routing protocols include RIP, OSPF, EIGRP, and BGP.
What are the kinds of Dynamic Routing Protocols?
Dynamic Routing can be divided into two types, namely-
Interior Gateway Protocol (IGP)
IGP is designed and intended for use inside a single autonomous system.
IGP is further divided into multiple types-
- Distance vector routing protocol (DVRP): – Routing Internet protocol (RIP), Interior gateway routing protocol (IGRP)
- Advanced distance vector routing protocol (ADVRP): – Enhance interior gateway routing protocol (EIGRP)
- Link state routing protocol (LSRP): – Open shortest path first (OSPF), IS-IS (Intermediate system-intermediate system).
Exterior Gateway Protocol (EGP)
EGP is designed to be used between the same as well as different autonomous systems over the internet.
NOTE: Path vector routing protocol (PVRP) i.e. Border gateway protocol comes under this category.
What are the advantages of Dynamic Routing Protocol?
The advantages of Dynamic Routing Protocol are as follows:-
- Dynamic routing protocol can automatically update the routing table in response to changes in the network. Hence, manual work is reduced.
- This protocol can easily adapt to network changes by recalculating routes which makes it suitable for networks with dynamic traffic patterns.
- It provides fast convergence.
What are the disadvantages of Dynamic Routing Protocol?
The disadvantages of the Dynamic Routing Protocol are as follows:-
- Configuring dynamic routing protocol is very complex.
- Dynamic protocol generates routing updates which leads to the utilization of bandwidth, processing power, etc.
- Security risk is high.