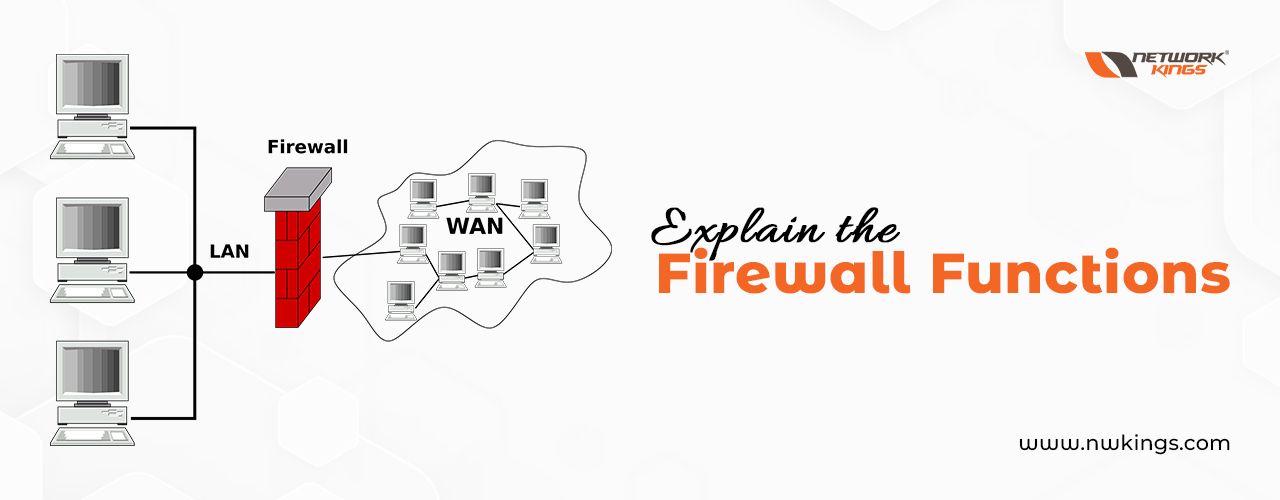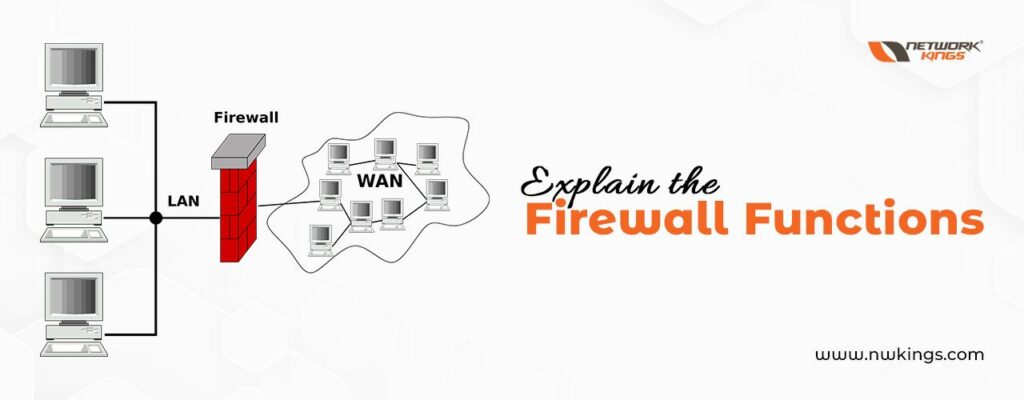
A firewall is a device or software application that is used for network security. It helps to monitor and control the incoming and outgoing network traffic based on some pre-defined security policies Its purpose is to establish a barrier between a trusted internal network and an untrusted external network such as the internet and to prevent unauthorized access while allowing the authorized communication to pass through. So it functions by creating a trusted and untrusted zone. Most firewalls allow traffic from the trusted zone (authorized zone) to the untrusted zone but traffic from the untrusted zone to the trusted zone is denied.
Firewalls also have a less trusted zone which is called a Demilitarized zone.
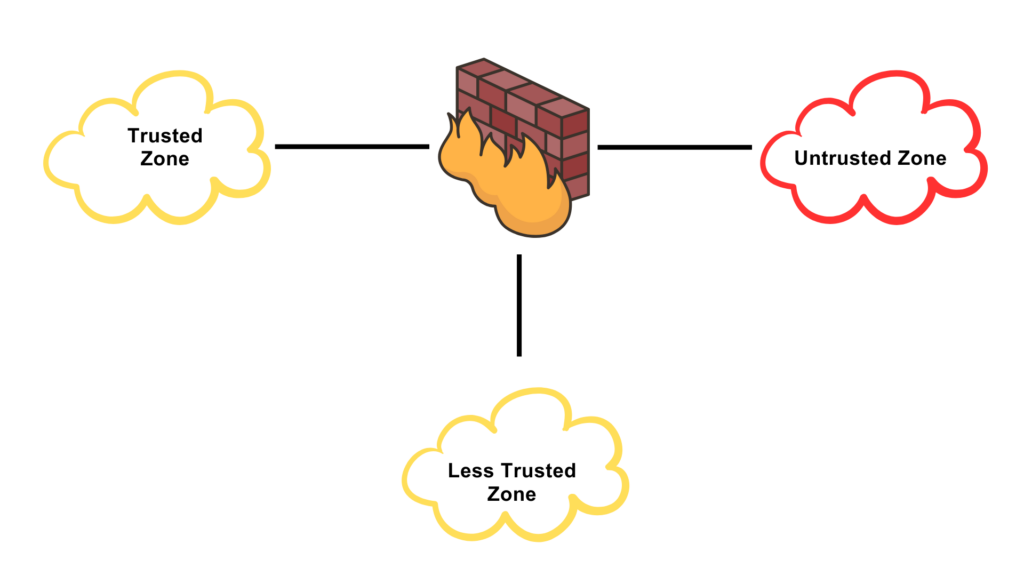
Some value is assigned to the interface of these zones and the traffic from lower security value is not allowed to the higher security value by default and requires some permission. But the traffic from a higher security zone is allowed to the lower security zone. The flow of traffic can be manipulated as per the need.
What are the key functions of a firewall?
Network Security: A firewall acts as the first line of defense against cyber threats, malicious attacks, and unauthorized access attempts from the internet or untrusted zone/network. A firewall helps in monitoring incoming and outgoing traffic, filtering and blocking potentially harmful or suspicious data packets based on predefined security rules.
Access Control:- Firewalls implement access control policies allowing administrators to define and manage rules that determine which network traffic is permitted or denied. This control helps in regulating who and what can access the network, safeguarding against unauthorized users and potential threats.
Protection of sensitive data: A firewall helps in protecting the sensitive data and resources within a network by preventing unauthorized access to confidential information, proprietary data, personal details, or financial records. By controlling access to resources, firewalls help maintain data confidentiality and integrity.
Prevention of malware and cyber attacks:- Firewalls help prevent malware viruses worms, ransomware, and other malicious software from infiltrating the network by blocking known malicious traffic patterns or infected files from entering the system.
Network Segmentation:- They Facilitate network segmentation by dividing the network into separate zones or segments each with its security policies. This isolation helps contain potential threats and limit the impact of security breaches.
Compliance and regulatory requirements:- Many industries have specific security standards and compliance regulations that require the implementation of firewalls as part of their security measures. Compliance with these standards ensures adherence to security best practices.
Protection of Endpoint:- In addition to network-level protection firewalls on individual devices or endpoint firewalls offer an additional layer of security by monitoring traffic specific to that device and preventing unauthorized access or attacks targeting the endpoint.
What are the types of firewalls?
- Packet filtering firewall: – This type of firewall operates at the OSI model’s network layer (Layer 3). As the name suggests, it uses the packet filtering technique to provide network security, and some predefined rule is configured on the firewall. When a packet arrives at the firewall, it examines the packet header including information on the source and destination IP Address, source port, destination port, protocol type, etc. Firewalls then look at the predefined policy, compare the information, and make the decision whether to allow or deny the packet.
Also, packet filtering firewalls operate in a stateless manner which means that they evaluate each packet individually without considering the packet’s relationship to previous or subsequent packets. They do not maintain a state table or keep track of the state of connections like in the case of stateful inspection firewalls do.
Based on the rules, the firewall decides to permit the packet to pass through (allow) drop the packet (deny), or possibly log information about the packet for auditing purposes.
One thing to remember is the order of the rule list. The list is always viewed from top to bottom. Thus, more important rules must always be placed at the top.
For example: –
Rule 1:- Allow Destination Address 172.16.1.5
Rule 2:- Deny Destination Address 172.16.1.5
since the rule list is viewed from top to bottom, the packet with destination address 172.16.1.5 will be allowed even though you have denied it in rule 2.
Hence the order of rule is of utmost importance.
- Stateful inspection firewall: – These firewalls operate at the network layer (Layer 3) and the transport layer (layer 4) of the OSI model. It is an advanced form of firewall that keeps track of the state and context of an active connection. This allows firewalls to make more informed decisions about network traffic enhancing security and providing better protection against threats. When a packet arrives at the firewall it examines the packet headers like a packet filtering firewall (checks for destination and source IP Address) ports and protocol types but unlike traditional packet filtering firewalls, stateful inspection firewalls maintain a state table or stateful connection table. When a packet matches the predefined rules and is permitted the firewalls add an entry to its state table to keep track of the connection, This entry includes detailed information about the connection’s state such as source IP Address, destination IP Address, port numbers, and the current state of the connection (e.g. established, initiated or closed)
As more packets were, the firewall compared them with the context provided by the state table and not only to the predefined set of rules. Firewall performs stateful analysis which ensures that incoming packets are part of an established connection. It verifies that it belongs to an active session initiated by an internal host and maintains the state of the connection.
- Proxy Firewall: – It operates at the application layer (Layer 7) of the OSI model. They act as intermediaries between the client and the server and handle communication requests on behalf of the originating user. These firewalls provide deep packet inspection by examining the contents of packets and filtering based on application content. They offer a higher level of security. Due to their method of working, they can introduce additional latency.
Next-Generation Firewalls:- NGFW integrates traditional firewall features with advanced capabilities such as intrusion prevention systems, application awareness, deep packet inspection user and application level controls SSL inspection, and integration with threat intelligence to provide more comprehensive security