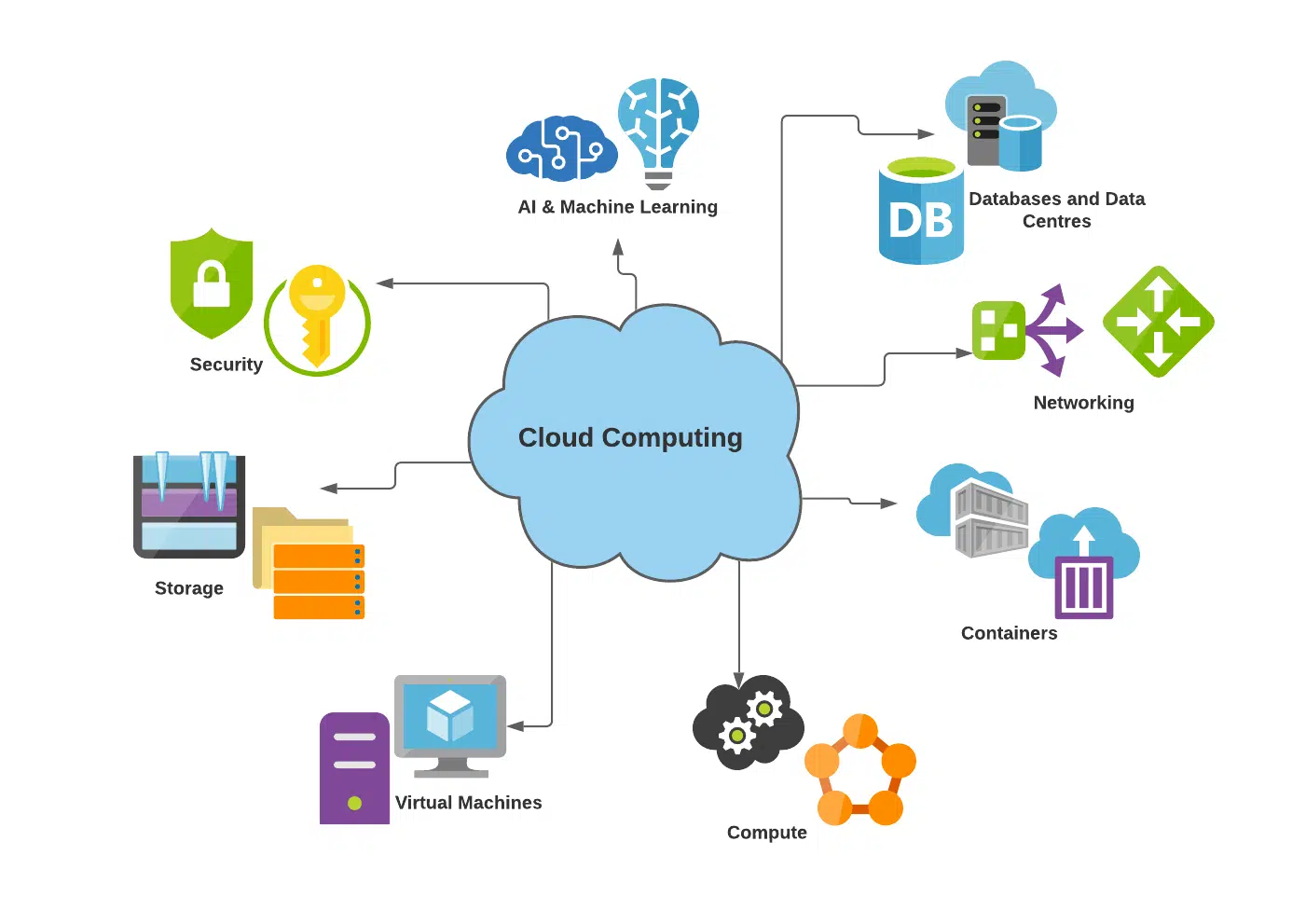
(Identity and Access Management) IAM in Cloud Computing is integral to cloud computing these days. It is essential to make sure only authorised users can access sensitive information, while also keeping their accounts secure from malicious attacks. Cloud IAM plays an important role in this; it provides organisations with more control when it comes to who can access data or enter systems through authentication procedures, authorisation processes and federations.
To work optimally though, IAM needs proper integration with other cloud security methods such as encryption, and multi-factor authentication techniques like tokenization or micro-segmentation. For example, as the number of cloud applications constantly grows so does the requirement for strong IAM solutions which offer a safe option when controlling identities and granting permission rights throughout an organisation – making compliance easier while improving user experience at all times plus ensuring organizational policies are met securely!
Understanding the Concept of Identity and Access Management
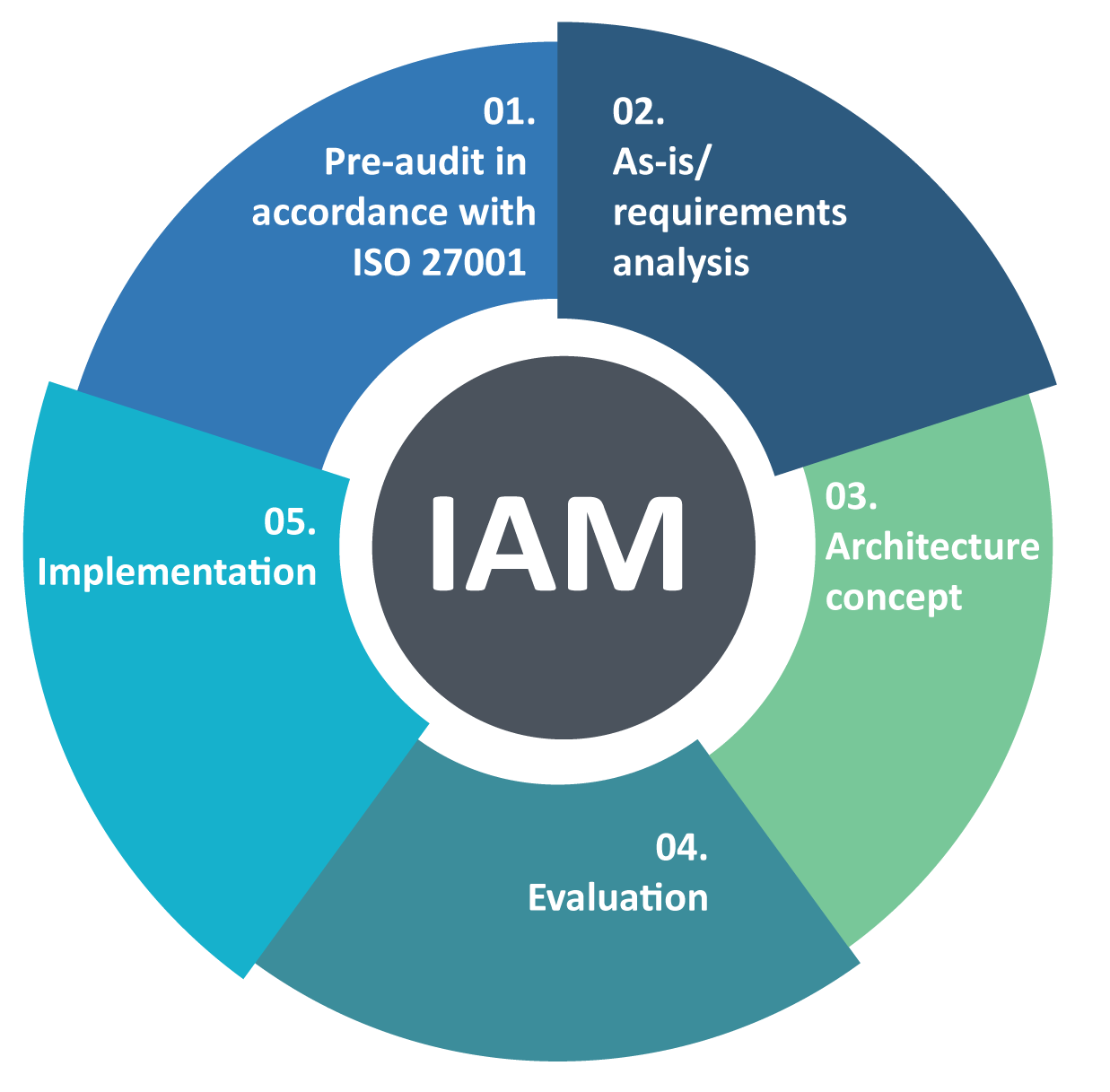
Identity and Access Management (IAM) is a necessary part of cloud computing. IAM deals with creating, managing and maintaining the identity of users for safe access to network assets. It allows diverse users to have admittance to a certain system depending upon their functions and permissions – it also grants administrators power over what these people can do or view in that particular system.
To truly grasp how IAM operates in cloud computing there are three principal components: authentication, authorization as well and accounting which make sure everything runs smoothly on the platform’s side too! Authentication verifies who you are; Authorization defines your level of access according to various roles and regulations while Accounting logs track all user actions within take place inside a given environment – this ensures accountability if something goes wrong at any point during operations so that parties responsible could be identified quickly without causing much hassle.
Authentication sets out who you are, granting you the right that whatever action is taken inside a system is really from yourself. Authorization explains what explicit activities can be done by each user in an online scheme as per their privileges level, while accounting observes customer doings so it can be exploited for examination or adherence aims.
When it comes to working IAM systems within your business organisation, there’s loads of potential available. You may pick existing IAM solutions or construct your answer which satisfies with company’s requirements. It is significant to make sure that all functions attached to identity control happen under hardened security measures since any kind of break-in could bring about pricey data loss and reputational spoilage too; not forgetting recurrent tracking of users’ activity helps organisations sense looming hazards ahead they become serious problems?
The Importance of IAM in Cloud Computing
Identity and Access Management (IAM) is a hugely important part of cloud computing. It has an immense role to play when it comes to securing the environment based on the cloud, as it controls who can access which resources in that space. Through IAM, organisations can create user policies that will apply across lots of different people and applications – this helps make sure only valid users get permission into certain sections or areas where they have pertinent information stored up.
In addition to preventing unauthorised infiltration, using IAM also double-checks any credentials given by prospective customers before allowing them their desired entryway; making sure no malicious intent exists behind someone’s request for access.
Strong authentication methods like multi-factor authentication can help organisations minimise the probability of somebody gaining unauthorised access to data stored in the cloud. IAM (Identity and Access Management) is a useful tool for organisations as it keeps an eye on user activity, guaranteeing that all activities are following company policies and regulations. But its value doesn’t just end there – it has also been known to bolster compliance with stringent security standards such as GDPR or HIPAA by putting necessary protections into place for sensitive info held in the cloud.
Have you ever thought about how important these measures are? Having an audit log that tracks user activity makes it simpler for organizations to confirm they’re adhering to all regulations related to data protection and privacy. But this isn’t the only benefit IAM has when it comes to cloud-computing environments. It also creates secure barriers between different parts of a system, allowing only authorised users to access them whilst abiding by varied security standards at the same time – plus keeping tabs on each user’s activity is made easy too!
In other words, having an efficient IAM setup in place can help make sure your organisation meets every requirement needed as far as cyber safety goes; providing you with invaluable peace of mind in today’s digital world.
Exploring the Role of Cloud IAM in Businesses
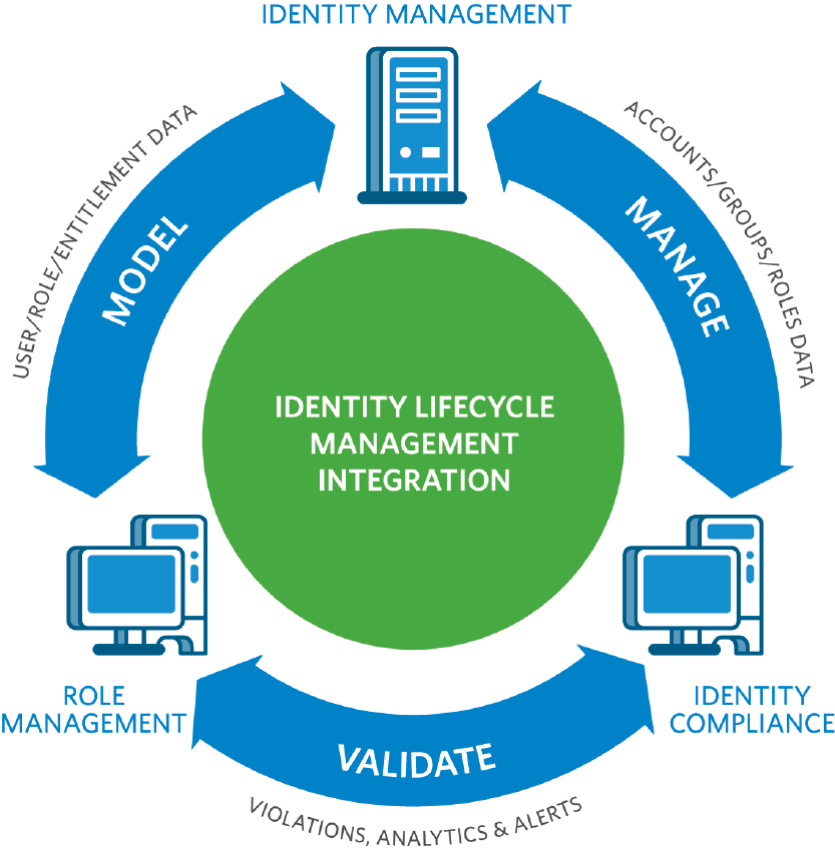
No matter how large or small your business is, cloud Identity and Access Management (IAM) should be a key tool in maximising efficiency and security. Cloud IAM focuses on offering users secure access to both digital and physical equipment. It gives control over who can view which data plus who has permission to edit or modify it. Ultimately, the role of Cloud IAM in businesses boils down to protecting them from possible malicious actors while guaranteeing a safe atmosphere for their vital apps, facts and systems – surely that’s something we all want?
Having an effective Cloud IAM system in place is a great way for businesses to better manage their users’ identities and access levels. It is all about granting employees access to specific resources based on their roles within the organisation, as well as applying multi-factor authentication – only those with designated credentials get through this kind of security checkpoint. Leveraging these elements is how organisations can provide tailored authorization policies without compromising safety, whilst also avoiding having multiple accounts or needing manual administration of user rights – no hassle!
When you take into account the huge number of customer profiles businesses are dealing with these days, cloud IAM helps firms to stay organised by permitting them to save user information in one centralised place alongside their profiles’ accompanying privileges and limits. All user data is kept securely within a lone platform, meaning companies can effortlessly monitor employee activity like logins from multiple gadgets and promptly identify any questionable behaviour.
Finally, utilising Cloud IAM services gives you complete assurance that your company’s delicate files and info remain safe while only being accessible by approved personnel. Depending on which service package you select it might even be possible for you to establish automated commands so particular members of staff have access to certain resources at specified times – offering yet another layer of security against potential breaches; diminishing the chance of internal or external threats making it through your enterprise defences if they were not maintained appropriately enough or left unprotected altogether.
Securing Data with IAM Security Measures
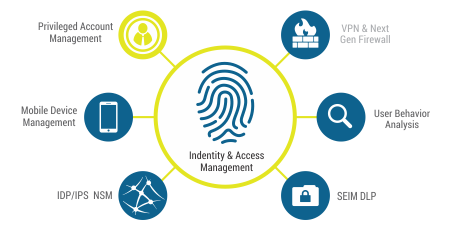
(Identity and Access Management) IAM in cloud computing gives organisations the power to regulate access securely to data stored on cloud servers. One of the most efficient methods for achieving this is using IAM security measures – such as user authentication, single sign-on abilities, authorization systems, control policies and monitoring. User authentication allows identifying a user who is attempting to gain entry into resources or data on a cloud server – often through passwords but may also include other approaches like biometric identification or security questions.
Single sign-on (SSO) makes it easier to log into numerous accounts with a single set of details. This helps streamline the login process, as well as providing improved security since there’s less risk that someone could guess an individual’s password from one account and get access to another. Of course, who gets permission to access what data on organisational cloud servers is determined by the organisation’s control policies; but having easy-to-use SSO can help make sure everyone knows where they stand in terms of accessing whatever information they need – without any potential hassle or danger!
If someone needs to get their hands on confidential information or edit certain files, they need permission first. Authorization mechanisms then make sure that only those given the go-ahead can do specific tasks like viewing and editing the data in question. On top of this, monitoring keeps an eye out for all activity going down on cloud servers and records it so any suspicious behaviour is quickly identified and acted upon accordingly.
All of this also allows businesses to identify weak points in their systems before they become issues – allowing them to prompt action that should be taken. By setting up IAM security measures companies are more able to shield important business info from unwanted access while at the same time granting necessary users safe passage when needed – a win-win!
Impact of Identity Access on Cloud Computing
Identity Access Management (IAM) has become an increasingly essential part of cloud computing. In this day and age, businesses must securely manage their customers’ data and access control to protect the enterprise from potential risks and threats. IAM is a collection of technologies, policies, and procedures created to monitor user access, recognise people using it, verify requests for entry as well as other activities associated with managing users’ identities. Without safe IAM measures in place, companies can suffer serious security breaches which could have devastating consequences on their standing or operations – what’s more, they may even incur financial losses!
The significance of IAM in cloud computing is intensified as it involves storing top secret data on the cloud which requires strict authentication protocols to make sure only those who are authorised can gain access. Companies need thorough safety for their information stored on the cloud against malicious attacks or unlawful admittance. To acquire this degree of defence, organisations must deploy solid IAM measures together with best practices such as two-factor verification and password complexity regulations.
IAM also gives augmented scalability for managing user identities correctly when companies switch from traditional systems to cloud systems – how do you guarantee that all these new accounts correspond with existing ones? What processes have been put in place to maintain security consistently across a growing number of environments within an increasingly complex digital landscape?
With the help of IAM solutions like Single Sign-On (SSO), IT departments can easily deal with large quantities of passwords without placing a load on users trying to remember them all. SSO eliminates feeble passcodes, and multiple logins for disparate applications or resources and cuts down IT operational expenses as well as makes life simpler by simplifying the login process.
It is worth mentioning that while IAM solutions make it more straightforward for companies to manage user credentials in big-scale environments, they come along with certain risks such as insider threat attack surface where an organisation’s personnel may compromise the system through malicious acts or negligence. To stop these threats from emerging companies should take into account risk assessments which include privileged access management (PAM) practices and appropriate oversight regulations over who can gain admittance to what data or service within their system environment.
Rhetorically speaking – do you know who has access rights across your systems? Could any staff be doing something nefarious right now?
Cloud Security Benefits Through Effective IAM

Cloud computing has become a huge part of many businesses today. A crucial element in such systems is Identity and Access Management (IAM). It is the set procedures and tools used by companies to control access to their data or services. Regarding cloud security, IAM plays an influential role; it provides strong authentication methods as well as authorization for users which stops confidential information from being accessed without permission. So how do we make sure our sensitive data is secure?
Multi-factor authentication is the most common form of IAM, requiring users to input two or more pieces of information to be granted access. This could include something as simple as a password and verification code sent via text message or email, plus biometric scans like fingerprints for extra safety measures. By enforcing this double (or triple) check procedure organisations can make sure only those with rightful credentials get into their cloud services – all helping them reduce the chances of security breaches significantly.
Besides aiding security measures, another great benefit provided by using IAM on cloud computing platforms is that it gives you quite precise control over data access levels.
Identity and Access Management (IAM) is a vital tool for organisations looking to protect their data. By setting up varied permission levels based on user roles, administrators can ensure only certain individuals have access to sensitive information – even if someone were able to get past authentication measures. If there was an unauthorized entry into the organisation’s account then it would be limited by its privileges so no changes could be made without prior authorization.
What this means effectively is that attackers won’t have the ability to do anything they shouldn’t unless, of course, they have all the necessary approvals!
Ultimately, IAM solutions enable frequent reviews and monitoring of user behaviour to swiftly spot any risks that may arise and take action before it becomes a serious issue. This guarantees no one is taking advantage of weaknesses within the system or accessing data without authorisation – while still ensuring proper users can quickly get hold of their accounts or resources with minimal interference.
In conclusion, having effective IAM solutions in place is fundamental for organisations using cloud services – enabling a greater understanding of what users are doing as well as providing extra protection against dubious threats. By making sure these measures feature prominently in cybersecurity plans, companies have peace of mind knowing that confidential information stays secure but remains accessible when necessary.
The Challenges of Access Management in Cloud Computing
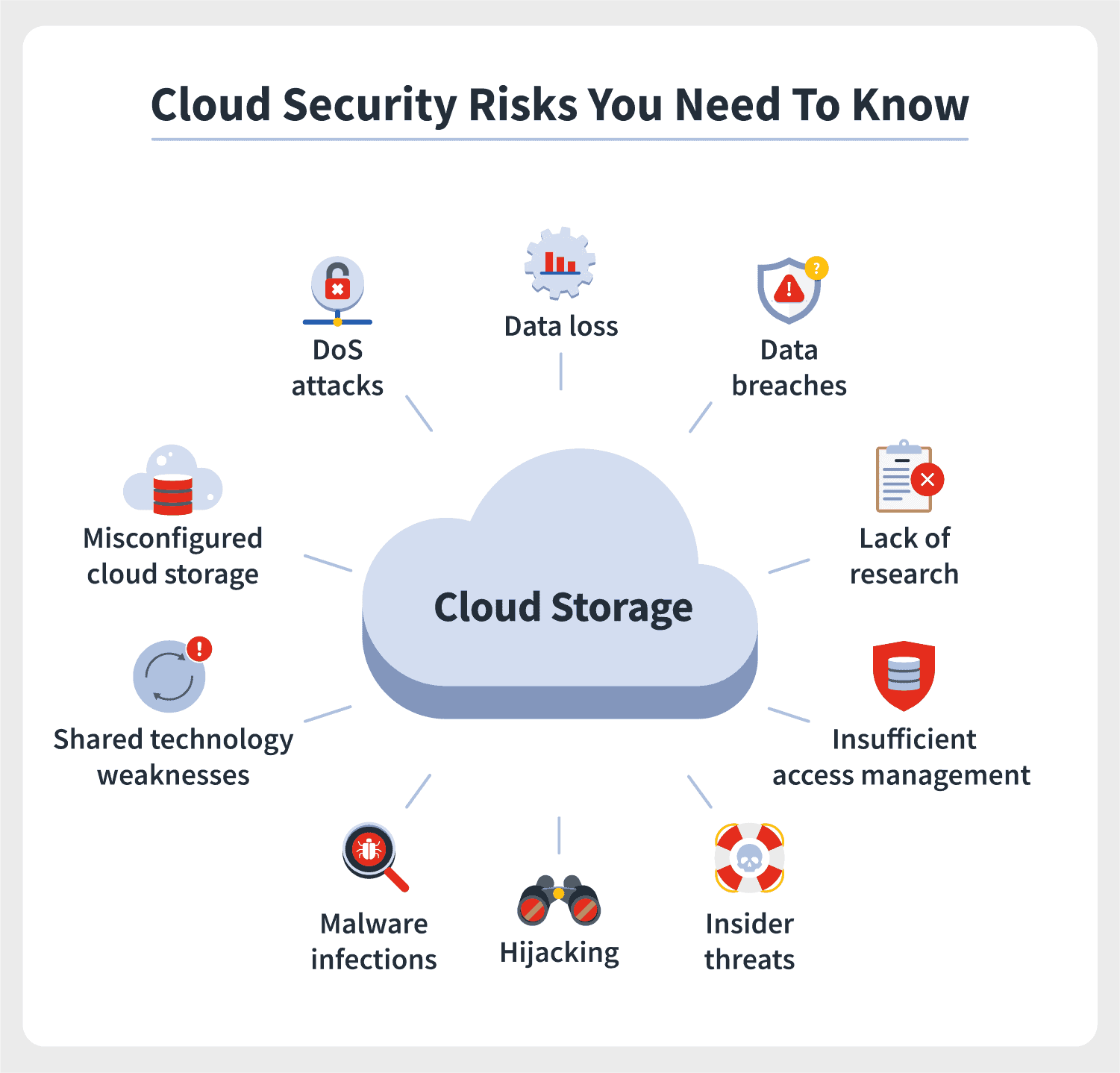
The challenges of access management in cloud computing are no joke – they are multiple and complex. Cloud computing has the potential to completely transform the way companies handle their identities and access control systems, but unfortunately, it poses some serious security risks too. If these issues are not managed effectively, then all sorts of problems might arise; data breaches, malware attacks or worse – cybercrime! To make sure nothing untoward happens on your networks businesses need to understand the associated threats with cloud-based IAM and take steps to preempt any possible danger.
A major hurdle when it comes to controlling access in the cloud is managing users who don’t have an adequate grasp of tech or security guidelines. Without providing them with helpful instructions on how they should properly oversee user data, companies are endangering their precious possessions by leaving them open for potential malicious activities.
Moreover, if there is no proper idea of roles and rights linked with each system account, then sneaky individuals may get into areas that should not be accessible to them; this could result in private info going missing or unauthorised exploitation of sensitive systems resources – something which nobody wants!
To tackle this issue, administrators need to put in place strong training programmes for all those who would have access to any cloud-based services or systems. Another problem associated with controlling entry into the cloud is guaranteeing that user authentication is robust enough so that only authorised individuals can gain admittance into applications and systems.
Password policies must be continually enforced to stop attackers from easily working out passwords and gaining unauthorised admission. For added security, two-factor authentication should be adopted wherever feasible as an extra line of defence against prospective invaders.
Finally, organisations must reflect on who else might get access outside their organisation to their cloud-based services or structures. When using a third party’s Cloud infrastructure such as Amazon Web Services (AWS) or Microsoft Azure, companies ought to understand what level of vision they will have about which external accounts will be allowed log-in rights involving their system databases together with moving data around inside them – if not given the ability track these activities then businesses could bring vulnerabilities into existence within their processes allowing outsiders perhaps without detection to enter valuable corporate resources illegitimately!
Role of IAM in Enhancing Cloud Security Protocols
IAM is essential for cloud security. It grants users one spot of control over the resources they need to get their job done right – no more, no less. IAM also allows organisations to tailor user privileges within their IT environment which keeps potential issues caused by human errors away from your data and any other places it should not be in danger!
At its core, IAM helps companies securely store user credentials and authentication processes so that IT teams have better reign on who has access where and when – providing a peace of mind about what’s going on behind closed doors. Who do you trust?
Extending the use of IAM further, it can be used to make sure that users abide by specific policies when they are using applications or systems, for example, multi-factor authentication in highly sensitive activities and other security risk prevention elements. Moreover, this type of management tool assists organisations in upholding internal regulations as well as external ones – making certain that all personnel have fitting levels of access irrespective if they are working remotely with multiple tasks simultaneously.
Offering a structured process for granting and revoking user access additionally helps reduce any chance of human fault causing data leakage or breach; thereby aiding teams to stay compliant with industry standards such as GDPR while concurrently allowing staff members to attain the appropriate level of gain entry needed to complete their relevant duties.
In conclusion, identity and access management has an essential role within cloud safety protocols because its capability is so diverse – ranging from controlling privileges to supporting completeness across business operations combinedly.
Key Strategies for Optimising Cloud IAM Functions

It is no shocker that cloud computing is the bedrock of modern businesses. Identity and Access Management (IAM) solutions are essential to guarantee secure and effective performances in the cloud. Optimising IAM operations can be a tricky process sometimes, but it needs to be managed correctly if you want your organisation’s Cloud infrastructure to function at its best – here are some key tactics which will help keep your cloud IAM functions optimized:
To kick off optimising those vital IAM features, begin with grasping all the fundamentals of identity and access management.
It is essential to get your head around what IAM does, so you can set up the right ID and access policies for your organisation. Likewise, knowing various assets open in a cloud setting will guarantee data security of work applications and resources. Therefore, once you have got that all straight it is time to kick-start safety measures across your company’s Cloud arrangement. Do these steps have enough coverage? What else could be done to improve protection within the system?
When it comes to Cloud Infrastructure, there are several measures you can take to optimise the IAM functions. These range from multi-factor authentication and role-based access control, through encryption and logging capabilities up to user education initiatives – each of these help identify potential vulnerabilities before they become a problem.
Automated identity provisioning solutions also offer organisations an efficient way of providing secure access management without users having to manually input their information every time they log into something. This not only saves on tedious manual processes but ensures that only authorised people have access to confidential data or applications within your organisation’s cloud environment. It can even make organizations compliant with regulations such as GDPR or HIPAA more effectively than manual processing would allow for!
Having said this, however, robust governance systems coupled with audit tools should still be used regularly for internal parties (or third-party vendors) managing Cloud infrastructure internally to check who has privileged rights over sensitive material stored on those systems – after all, if unauthorised individuals were able to gain unfettered access then no amount of security protocols would protect against any malicious behaviour occurring thereafter!
Future Trends in IAM for Cloud Computing

Recent statistics show that the cloud computing market is estimated to soar beyond USD 400 billion by 2026 – a boost partially owed to organisations always seeking cost-effective solutions which will give them more agility. This means it is important for businesses to comprehend changes within IAM so they can keep on creating their infrastructure efficiently and securely.
As businesses transfer their IT systems and applications to the cloud, the demand for a secure Identity and Access Management (IAM) system is becoming increasingly essential. Moving on from old-fashioned user authentication and authorization practices won’t cut it anymore – reliance on locally stored passwords and usernames is insecure. To stay one step ahead of digital threats organisations need advanced enterprise access control solutions such as Multi-Factor Authentication (MFA), Role Based Access Control (RBAC) or Single Sign On (SSO). These will ensure that they remain in full control over who can access what in their networks while keeping all precious data safe.
What’s more, identity federation has come to the fore as a key component of an efficient IAM strategy. This allows users from diverse networks to sign in to one setting without needing to enter their login info every time they link up. Not only does this streamline operations but also boosts security by guaranteeing that each user is accurately identified before given permission rights – which provides several layers of protection against malicious actors such as hackers or internal threats.
We can’t forget about ongoing trends too like the spread of mobile devices and automated tools that make it simpler for admins.
Take automated password reset systems, for example – this means you will need fewer admins to manage passwords and identities across domains. Not only does this reduce operational costs, but also significantly increases security at the same time! AI and machine learning algorithms are being used too; they detect unusual behaviour so administrators can be alerted when suspicious activity is spotted – adding another layer of protection against data leaks or insider threats, which raises the level of security even further.
Ultimately, organisations must not just take advantage of these upcoming trends, but should also pay close attention when searching for a vendor who can provide them with solutions that best fit their individual needs.
Wrapping Up!
In conclusion, Cloud Identity and Access Management (IAM) is an absolute must-have if you are looking to strengthen security in your cloud architectures. With IAM solutions, organisations can set up secure policies that control access to their services and resources – protecting user credentials and data from malicious actors as well as meeting regulatory standards.
It enables them to create robust authentication processes; run single sign-on operations; implement effective authorization systems; and provision users appropriately with suitable levels of access control… the list goes on! Plus, it is a great way of preventing identity theft or unauthorised snooping into sensitive data across all areas of the business.
So whether you are starting with cloud computing or have been using it for some time, investing in trusted Cloud IAM Security and Identity Access tools really should be at the top of your agenda when evaluating overall enterprise security measures.
Are you hunting for a novel approach to turn into a cloud architect? Look no more! Our Cloud Architect Master Program is devised to furnish aspirant architects with the state-of-the-art skills and expertise they need to thrive in the industry. With our exhaustive syllabus, you’ll master priceless tactics such as designing, engineering and enacting cloud-based applications. Plus, our seasoned teachers will be available every step of your journey throughout this program. Thus, don’t linger – enrol on our Cloud Architect Master Program now! Your upcoming career as a cloud architect awaits ahead of you!
Do you have a passion for cloud computing? If the answer is yes, why not take your career to the next level by enrolling in our Cloud Architect Master Program? This program will equip you with all of the latest tips and techniques when it comes to creating, developing, administering and maintaining cloud-based solutions. It is an amazing opportunity that gives you a chance to stay ahead within this continuously evolving field.
You will attain a practical understanding of how cloud architecture works while also honing your communication skills; both these things are extremely invaluable whenever someone is working inside a business sector like this one. Moreover, having experienced professionals guiding us through each step means there is no better place than our Cloud Architect Master Programme wherein we can get started! So what exactly are you waiting for? Sign up straight away and become part of us as we explore fresh horizons full of prospects!
Happy Learning!









































)