
If you are after beefing up the security of your AWS cloud landscape, Identity and Access Management (IAM) is an absolute must. In this blog post, we will delve into what is IAM in AWS exactly, how it works and why it is pivotal for good safety as well as user access control. We will cover topics like IAM roles, cloud identity along role administration related to Amazon Web Services Security system – so come on board while we go exploring all things connected to IAM within the context of Amazon Webservices!
Understanding the Basics of IAM AWS: What is IAM in AWS

Grasping the Fundamentals of IAM AWS Getting your head around IAM (Identity and Access Management) is a fundamental part of keeping any system secure, and luckily for us Amazon Web Services has an exclusive service for this. This facility assists you in regulating who can get access to your resources, what they are able to do with them, as well as how they are kept safe; it also permits users from several accounts or services to be managed altogether. In today’s article, we will delve into the basics of this great tool provided by AWS – IAM.
IAM in AWS puts you firmly in the driving seat when it comes to user access. You can create groups, allocate roles and set up policies which determine who is able to gain access to what resources. This works both within your own account – giving you full control over who has what level of accessibility – as well as between different accounts (for example if multiple people are part of an organisation).
Plus, with IAM at your disposal you are also able to dictate exactly how long somebody can be granted temporary access; so if they only need a specific resource or two for a limited period then their usage privileges will expire after that time frame passes. How handy would that come in?
On top of regulating access for users, IAM also has the ability to authenticate secure APIs that run on Amazon Web Services services such as EC2 or S3 buckets. For instance, an app functioning with an EC2 account would likely make use of its related profile’s IAM role in order to call out API within the same service it belongs to or from different accounts respectively. This way each application stays separate and there is no unrestricted access between all services put together.
IAM furthermore provides control over key management – letting you manage SSH keys through their policies rather than having one person take charge of every new user added to your system’s individual keys manually (letting people configure permissions independently). Similar dynamics apply when password rotation is involved: a critical part of security can be done automatically by using IAM policies thus passwords get rotated often without IT staff’s presence nor do admins need any extra input.
The Importance of AWS Security

When it comes to cloud computing, Amazon Web Services (AWS) is renowned for its incredibly dependable services and comprehensive security features. A key element of AWS is Identity and Access Management (IAM). IAM enables you to manage access to resources within the AWS environment based on user roles and policies. It can also be used to define who gets access to which data as well as how much permission they can have – this means that whoever is using a service or application will only ever see what they need in order to do their job properly.
As such, IAM plays an essential part in ensuring secure communication between users and resources; plus it provides consolidated control over any organization’s entire technology infrastructure – allowing them peace of mind that all assets are protected from malicious intent!
The use of IAM is essential for anyone who utilises the AWS platform. It adds that extra layer on top of existing security solutions, which can only be a good thing! The advantages are plentiful – it helps safeguard private information from unauthorised access; users have control and manage their own identity info safely; developers benefit by being able to deploy applications faster with less risk involved; there is an easy way of creating and managing permissions across multiple accounts so compliance is simple…need we say more? All these benefits certainly make using IAM worth considering if you are looking for added protection when using cloud services.
IAM offers significant advantages, reducing the cost of having each user set up separate accounts while providing clear visibility into what everyone can access. This increased governance helps keep cloud resources secure and it is much easier for users to log in without needing to remember passwords or submit personal details like name or address each time they do so. What’s more, IAM creates an environment where authentication is simple yet safe – a real plus point!
It is clear that IAM is a big help when it comes to safeguarding digital assets stored in cloud infrastructure like AWS. There are lots of products out there offering similar features but what sets them apart from other solutions is their enhanced customizability, enabling companies to adjust security settings as per changing business needs without any hassle – making them one of the most effective tools for managing protection on AWS systems these days!
What’s more, with various authorization levels set up by administrators, different read-only permissions can be granted dependent upon access rights across an organizational hierarchy. So ultimately you get a completely tailored solution which makes sure your data remains safe and secure at all times – no wonder so many businesses turn to this technology first whenever they need reliable defence against cyber threats!
IAM AWS: Defining Cloud Identity

The AWS Identity and Access Management (IAM) service offers a powerful range of features to make the cloud experience more secure. Specifically designed with customers in mind, IAM makes it easy for them to manage access to their AWS resources in a safe manner. To put it plainly, IAM is the tool used by customers when they need to define who can enter their cloud environment and what actions are allowed. How cool is that? Giving users control over how others interact with their online systems has never been simpler!
When it comes to setting up security and identity management policies in the cloud, IAM is essential for ensuring users have secure access to just what they need – nothing more, nothing less. Using roles and policies an administrator can be sure who exactly has permission to see which resources within the AWS environment as well as being able to perform certain tasks on them. Policies are applicable at both user level and organisation level allowing administrators even tighter control over who sees what with a couple of clicks! But how do you know if your setup provides enough protection?
AWS also presents its users with some sophisticated features like MFA, log activity tracing, cross-account access delegation and group support so that administrators can promptly delegate permissions without providing individual credentials. These cutting-edge characteristics give organisations, even more, suppleness when controlling user identities and groups over multiple accounts or regions.
Moreover, IAM directly integrates with other services such as Amazon Cognito for authentication requirements and S3 for storage needs; making it easier than ever before to rapidly provide secure applications and services while still managing control of user IDs. Additionally, IAM allows integration between federated identity providers such as LDAP/ADFS/Okta, which gives companies the additional reassurance their apps are fully safeguarded against unauthorized entry attempts. What is always worth asking here: How does this help you deliver a safer cloud experience?
To sum up then – IAM offers an extensive resolution for those seeking out a productive manner in defending their info on the cloud minus compromising comfortability of use or authority over individual identifiers along with authorizations. With its wide variety of traits designed specifically towards the cloud environment, Iam makes it simpler than previously thought possible to securely supervise important resources & guarantee that only approved users have entree to them.
Benefits of Using IAM in AWS
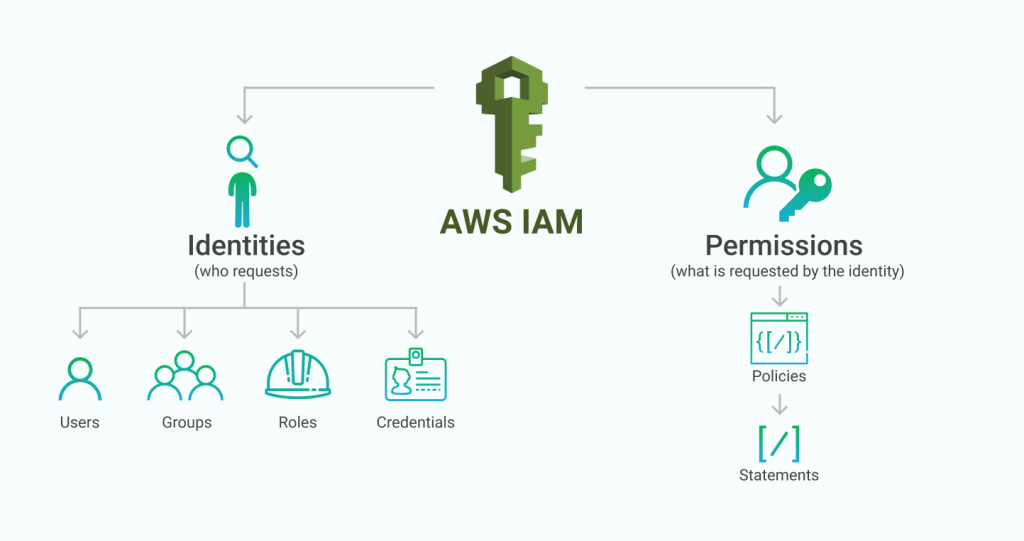
When it comes to cloud security, the Identity and Access Management (IAM) service in AWS is one of the most important. It enables users to control access levels for Amazon Web Services resources which helps make sure only authenticated and authorized people can gain entry – helping keep your account secure from any unwanted activities. This also ensures you are adhering to numerous data protection regulations like PCI DSS or HIPAA.
Through IAM, you are able to create individuals as well as groups and then assign them roles whose permissions set out how they may interact with different AWS services – all contributing towards a more robust safety net around your virtual environment. What’s more, this might stop unfortunate breaches that could lead to fines.
You can also set up multifactor authentication to ensure that no one who isn’t authorised gains access to your AWS resources. What’s more, IAM gives you the chance to register other devices like mobiles and tablets so you can easily manage permissions from locations across the world. IAM even provides logging capabilities which make it possible for users to keep track of their usage within an org over time – this is great for organisations looking out for any suspicious activity or misuse or abuse of privileges by those given access to the system.
Having an efficient user management and authentication system in place on AWS allows companies to protect their sensitive data more securely while at the same time reducing the effort put into managing users’ accounts and passwords manually. IAM provides granular control over which operations each role can carry out, making granting access rights much easier for all roles as well as ensuring that no one has more authority than is necessary for completing their tasks.
With this amount of control over user accessibility businesses are able to reduce any security risks they may be exposed to but still manage a streamlined workflow across teams operating cloud infrastructure on AWS – plus having a detailed audit trail enables organisations to abide by multiple industry regulations such as GDPR with ease.
How IAM AWS Enhances User Access?
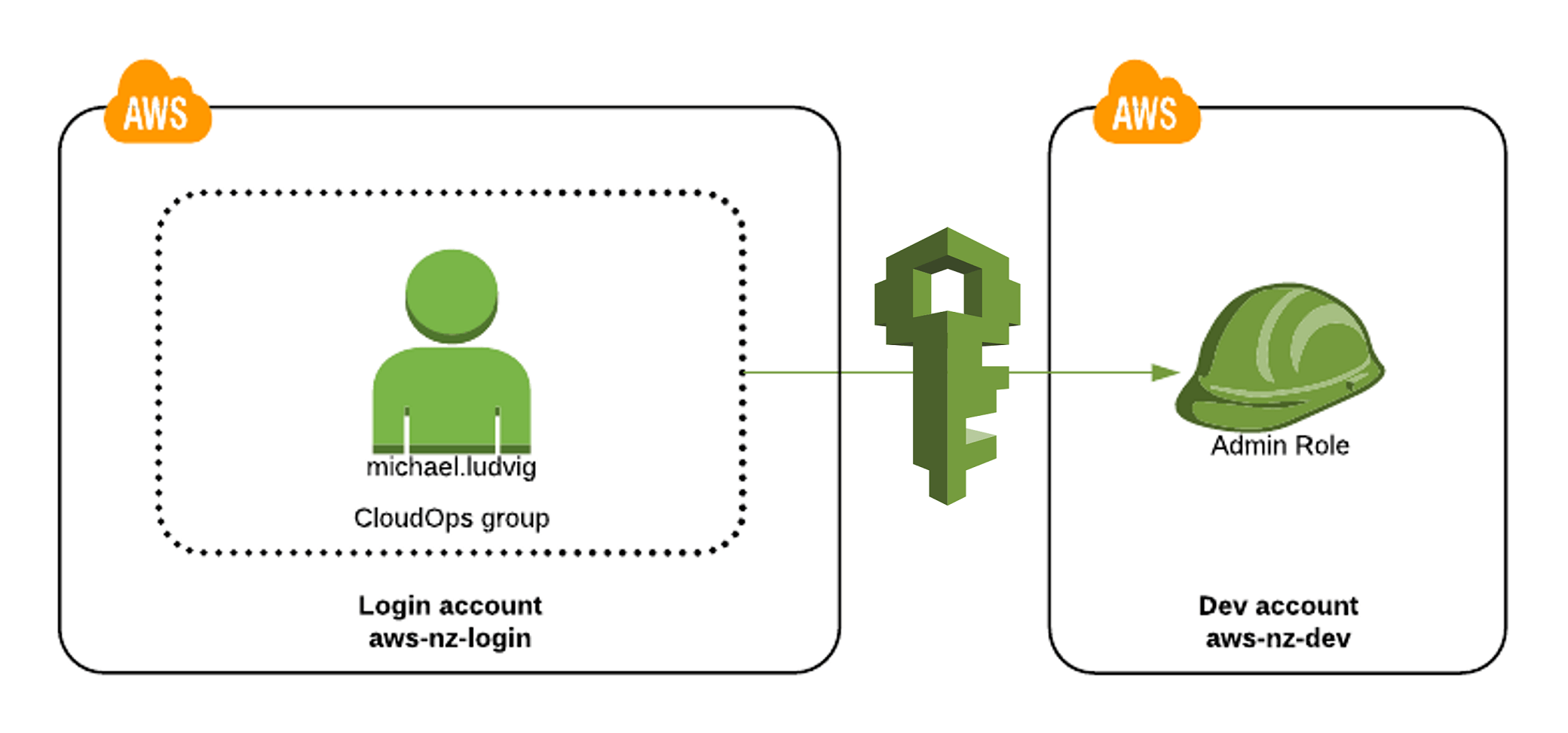
When it comes to security and user management on Amazon Web Services cloud, IAM (Identity and Access Management) is a great way of going about it. This service serves as the ideal solution for those seeking centralised control over access across various environments while at the same time enabling them to limit access to certain resources within AWS realms.
To this end, administrators are given an option of creating distinct identities for each person with any type of relationship or connection to their AWS account before assigning different levels of permission in accordance with that individual’s role and responsibility – pretty nifty, right?
With IAM, you can securely get hold of the resources you need without giving any extra details or passwords away to anyone else. For instance, if you want a whole team of developers to have full access rights for the code repository but only give read-only permission to another group – it is easy peasy! You also don’t have to worry about who has been given what permissions and whether they are overstepping their boundaries; as an administrator, tracking users’ granted privileges is pretty straightforward and auditing these authority levels in case something doesn’t seem right is simple too.
To make sure that only authorised personnel can gain entrance into important procedures and confidential information, setting up multi-factor authentication (MFA) adds yet another protective layer – requiring several pieces of evidence before granting entry makes things much more secure than ever before.
In conclusion then: with IAM one has better control when it comes to managing user accounts by assigning individualised authorization levels – so how do we know our sensitive system won’t be breached by someone unauthorised? With all these measures put in place this risk is reduced significantly making us feel protected from both intentional malicious intent AND accidental slip-ups alike – adding peace of mind whilst still retaining organisational efficiency at the same time!
Role Management in IAM AWS

Talking about role management in AWS Identity and Access Management (IAM), it is a great tool for managing users, groups, roles and permissions. It provides administrators with the power to decide who can access the AWS resources as well as what activities they are entitled to perform using those resources. Additionally, IAM makes crafting complex policies that stop unauthorised entry into your environment easier than ever before. In terms of role management in particular you are granted the ability to design rules which then get used for assigning specified privileges either to individual users or even entire groups once they have signed up – simple yet effective!
Policies are a great way of making sure that the right people get access to the right things at all times. They are written in JSON format, so they can be as simple or complex as you need them to be – which makes them really powerful and flexible when it comes to granting or denying permission depending on who is asking (like their identity, IP address… even what time of day). But there is also another useful tool for managing roles with IAM: Role-Based Access Control (RBAC). It offers an extra layer of security if you need it – plus additional control options too.
This type of policy permits you to assign jobs depending on their job role or capabilities level. This allows you to simply manage who has admission to which resources without having the need to give out permissions every time a new user is included in your system. RBAC policies also make it simpler for audit access as all authorizations are connected straight back with a certain role. What’s more, you can oversee roles in AWS IAM by putting into effect Service Control Policies (SCP).
When it comes to managing roles within AWS IAM, there are a few different approaches administrators can take. You could set up custom policies that allow you to restrict access across multiple accounts so users only have the right permission for their job tasks – this gives an extra layer of security since it limits the number of services they can interact with even if the proper role has been assigned.
That way, users will only be able to do actions directly related to their duties rather than having unrestricted control throughout your infrastructure. Rhetorical question: Who doesn’t want maximum protection? By combining all these tools such as custom policies, RBAC and SCPs admins receive fine-grained control over who is granted access at any given time while keeping safety concerns in mind – making sure the organisation’s cloud setup remains secure at all times!
Key Features of IAM AWS
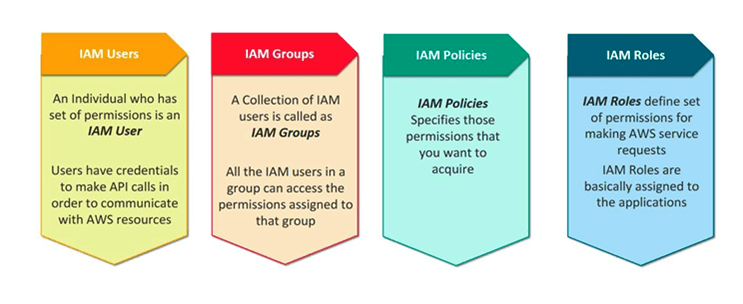
Identity and Access Management (IAM) is an integral part of Amazon Web Services (AWS). It allows users to control who can access their AWS resources such as EC2 instances, S3 buckets or services like Lambda and ECS. IAM enables you to create users and groups with different levels of permissions – deciding who has access to which resources when, what actions they are allowed to take on them etc. For extra security, it even permits setting up multi-factor authentication methods for each group or user individually. With IAM managing access becomes much easier; giving peace of mind that all your important information is secure from malicious hands!
One of the major advantages IAM provides in AWS is that you can assign very precise permissions, so only people with specific tasks have access. You can also craft policies which determine exactly what a user or group are authorised to do with your AWS resources. These regulations utilise the JSON language and may be applied across multiple accounts when required. This allows for a single primary place from where all your accounts can be managed without having to manually approve each individual’s request individually. Isn’t it brilliant?
Another vital element of IAM in AWS is its capability to meet hefty scalability needs. As your cloud setting advances and your usage intensifies as time passes, you need a system that can easily cope with intensified demand while still preserving everything secure. With IAM you don’t have to bother about manually raising permissions as use rises – instead, it takes care of this by itself so that there are always adequate permission levels accessible when needed.
Lastly, IAM in AWS offers finely-tuned logging capacities which let administrators evaluate user activity over their complete environment without difficulty. By constructing custom rules one can observe user actions at an exceedingly minute level and be alarmed whenever something not ordinary occurs – this helps guarantee compliance with any connected industry standards or inside regulations to promptly identify peculiar events if they occur suddenly..
Enhancing AWS Security with IAM
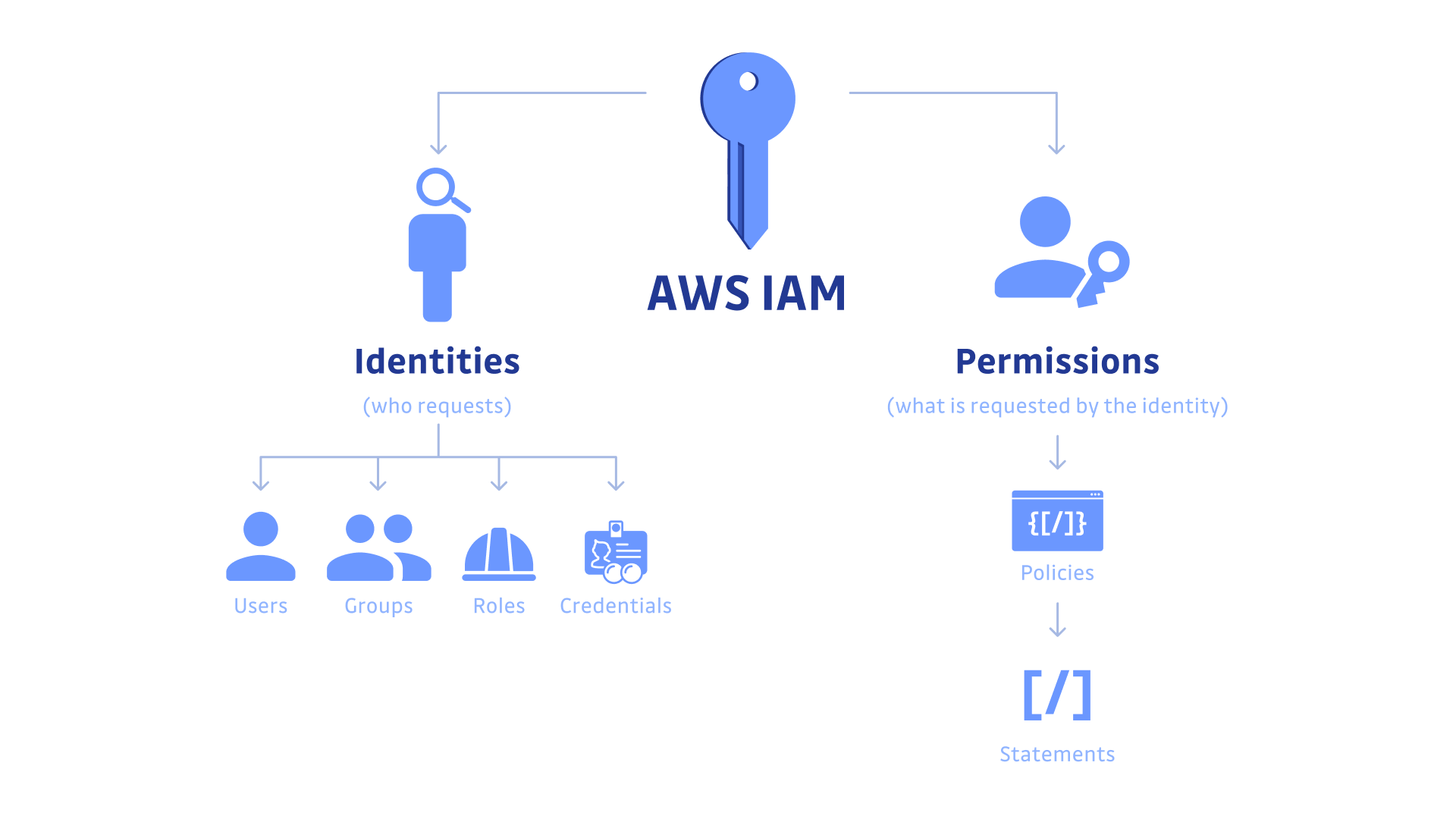
When it comes to securing cloud-based infrastructure, Identity and Access Management (IAM) is a key element. AWS IAM has been developed with the purpose of allowing users to manage their access rights within the environment in an efficient way. With its help, businesses can establish certain regulations for their accounts that will make sure every individual user stays inside those boundaries. In this blog post, we’ll investigate how IAM may be used as a tool to step up security on AWS plus what kind of policies should be implemented in order to get the most out of it – why not take advantage?
On a fundamental level, IAM enables businesses to generate users with an allocated authority amount. This implies that you can allocate different authorisation levels relying on who needs it and where they need for example, a developer could only have the right of entry to certain files in an S3 bucket while an administrator would have wider access liberties such as being able to delete items or customise rights on existing stuffs.
This balanced control permits companies to set up safe conditions and sustain division amongst teams’ work operations. But how do we ensure our data is secure? How much freedom should developers have when dealing with customer information? These are all valid questions that must be addressed before implementing Access Management systems like IAM.
As well as user management, IAM also has certain functions created for security purposes. Take multi-factor authentication (MFA) for example – it requires users to show two pieces of proof when they log in: normally a code sent through text or email plus something that only the user knows like a password or PIN code. It is an extra layer of protection to make sure your account remains secure and private; who would want their details compromised?
With Multi-Factor Authentication (MFA) enabled, it is virtually impossible for unauthorised people to gain access – even if they have your login details. This is because the MFA challenge requires a device or other credentials that would have had to be accessed previously in another way; such as stealing your phone or accessing emails online. IAM also has great tools like Amazon GuardDuty which detects any suspicious activity related to user accounts and CloudTrail events can alert you when someone attempts API calls from an unrecognised IP address.
It is worth noting that while using IAM certainly adds additional levels of security and enforces policy restrictions, there are still risks associated with cloud services like AWS – just look at the infamous Capital One data breach despite their multi-factor authentication! Therefore businesses should always consider additional measures alongside IAM such as encryption of all stored data or regularly patching systems whenever new vulnerabilities appear on the horizon.
Cloud Identity and User Access in AWS
The heart of AWS Identity and Access Management (IAM) is user control. IAM lets organisations keep track of who’s using their Amazon Web Services cloud-based infrastructure, what they can do with it and how to make sure it remains secure. IAM users are identities within an AWS account that have access to the resources in the account. Administrators can create, delete or adjust these user identities as necessary.
They also get to assign distinct levels of authorisation for every single user identity so activities are restricted – empowering administrators to offer just the correct amount of accessibility for a given customer. How much power should one be granted? Organisations utilising IAM can introduce regulations or policies which restrict what services certain users are allowed to access, such as only permitting particular users to access precise S3 buckets or EC2 instances. These rules may also be implemented in order to guarantee compliance with organisational policy and industry regulation by granting permission for specified resources and services based on conditions defined by the rule.
As an example, allowing just specific authorised images from where EC2 instances can be launched will make sure that all new assets abide by a distinct security standard. IAM also offers you control over how individuals authenticate prior to being granted admission into any service or resource; multi-factor authentication (MFA) is activated for each user needing extra verification when logging into the account – making it more secure!
Best Practices for Role Management in IAM AWS
It is essential to create roles which are tightly scoped in order to manage role management correctly with AWS Identity and Access Management (IAM) via Role-based access control (RBAC). By doing this, you ensure that each specified role has only the permissions it needs for its own designated task. But how can we best practice role management when using IAM?
No one likes clutter, and that should apply to your environment too. If a user only needs access to certain S3 buckets then they shouldn’t be given permission on those other than what’s necessary – read and write permissions. That keeps the potential attack surface low, meaning it is safer for everyone involved. Not giving users extra privileges also prevents them from making any blunders or causing data breaches with perms they don’t have business having in the first place. Next up is ensuring you have all relevant policies specified by each role correctly attached at every level of an individual account setup!
It is really important to have well-defined policies with clear instructions about who can gain access to or modify resources and when. And don’t forget, you could also combine several policies if one doesn’t quite serve your needs! On top of that, it is a good idea to monitor all the changes made in roles as well as any alterations applied to existing policies so there are no security flaws created by something that changed long ago but is now being forgotten.
Conducting regular audits is a good way to identify potential issues early on, which could become critical problems later. Moreover, it is also important to implement the least privileges access control – only provide the minimum amount of privileges needed for users so they can fulfil their duties and not compromise security standards in any process. This makes auditing and monitoring user activity simpler too as there are fewer credentials at hand that need controlling or tracking.
Last but by no means least, don’t forget about keeping up with updates! Technology continues advancing all the time presenting fresh security threats each day necessitating timely updates of roles and policies along with new capabilities created to protect your system from malicious attacks. Have you got everything securely updated already?
Wrapping Up!
To finish off, it is clear that IAM in AWS plays a key part when it comes to cloud security. It offers user access control, role management and identity defence so businesses can be sure their valuable assets will remain secure while users have the capacity to safely gain access to whatever services they need.
Furthermore, its ability to manage multiple accounts simultaneously makes IAM an efficient and economical way for companies to ensure their data’s safety on the cloud. So all things considered – why risk your important information? Investing time into setting up your own properly guarded system with IAM will pay dividends down the line!
Welcome to our AWS Cloud Security Master Program! Fancy becoming an expert at protecting your cloud infrastructure from cyber threats and getting certified? Then this program is for you. Our comprehensive course provides foundational and advanced-level training on how to identify, mitigate against, and respond effectively to suspected security breaches across your cloud environment.
With the know-how that comes with completing this program, achieving certification as an AWS Security Expert will be a piece of cake – plus we have plenty of helpful instructors there along the way who will give you all the advice about what’s best practice when it comes to securing things in line with Amazon Web Services standards. So don’t hesitate any longer – sign up today down begin unlocking your destiny as a certified AWS Cloud Security Master!
Are you ready to become an expert in cloud security? Our AWS Cloud Security Master Program is the perfect way for you to acquire all of the skills and knowledge needed to keep your data safe in a virtual environment. We boast world-class instructors who are dedicated to equipping our students with everything they need – from fundamental concepts through advanced technologies – so that they can achieve their goals, whether it is becoming an AWS Cloud Security Master or just gaining more experience and understanding of this field.
Understanding that everyone has different learning styles, we offer three ways for people to absorb what we teach: online courses; classroom teaching sessions; as well as private virtual classrooms. So don’t wait any longer – by joining us today, you will be one step closer towards taking your security career even further!
Happy Learning!



I just could not depart your web site prior to suggesting that I really loved the usual info an individual supply in your visitors? Is gonna be back regularly to check up on new posts.