Understanding what is cloud computing has become a crucial task in the current digital era. The growing field of technology is leading to an increase in the demand for cloud computing services and models. It has greatly impacted the world with the 5x growth in the job vacancies of cloud computing experts. Therefore, read the blog till the end to understand the cloud and its details in deep.
What is Cloud Computing?
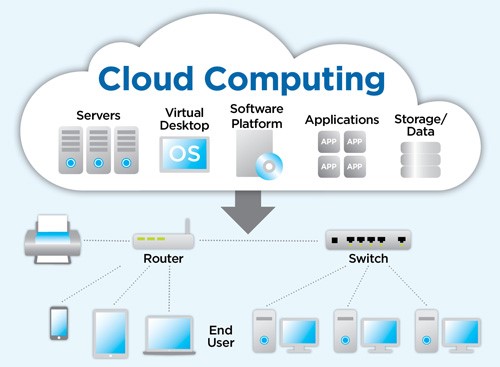
Cloud computing means the delivery of computing services, including servers, storage, databases, networking, software, and more, over the internet. Users can access these services on-demand and pay for only the resources they use, rather than owning and managing physical hardware.
What is the importance of Cloud Computing in IT?
The importance of cloud computing in IT can be discussed as follows-
- Scalability: With cloud computing, businesses can easily adjust the amount of resources they use based on their needs. This is super helpful for managing workload changes efficiently.
- Cost-effectiveness: By using cloud services, companies can save money on buying and maintaining physical hardware. Instead, they can pay for exactly what they need when they need it.
- Accessibility: Cloud computing lets people access their data and applications from anywhere with an internet connection. This makes remote work and collaboration much easier, boosting overall productivity.
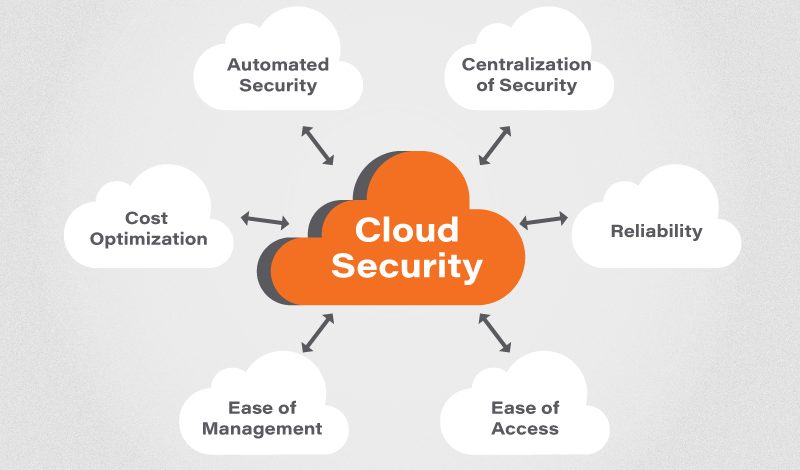
- Reliability: Cloud service providers offer really strong infrastructure with backups in place, so services are almost always available when you need them.
- Security: Cloud providers take security super seriously, using things like encryption and access controls to keep data safe from hackers. Lots of businesses feel their data is even safer in the cloud than it would be on their own servers.
- Innovation: Cloud platforms provide all sorts of tools and services that help businesses come up with new ideas and products quickly, without having to worry about the technical stuff.
- Disaster Recovery: Cloud computing makes it easy to recover data and applications if something goes wrong, like a power outage or a cyber-attack. This means less downtime for businesses.
- Global Reach: Cloud services are available all over the world, so businesses can connect with customers and users everywhere without having to set up their own infrastructure in different locations.
- Resource Efficiency: With cloud computing, lots of users can share the same physical infrastructure, which means resources are used more efficiently.
- Competitive Advantage: Using cloud computing can give businesses a leg up on the competition by helping them get new products to market faster, being more flexible, and adapting to changes in the market quicker.
What are the core concepts of cloud computing?
- Virtualization
- Server Virtualization: Divides a physical server into multiple virtual servers, each capable of running its own operating system and applications.
- Storage Virtualization: Combines multiple storage devices into a single virtual storage pool, simplifying management and scalability.
- Network Virtualization: Separates network resources from the underlying physical network infrastructure, creating virtual networks for improved flexibility and management.
- Service Models
- Infrastructure as a Service (IaaS): IaaS provides virtualized computing resources over the internet, including virtual machines, storage, and networking components. Users have control over operating systems and applications, while the cloud provider manages the underlying infrastructure. IaaS offers flexibility and scalability, allowing users to quickly provision and scale resources based on demand without the need for physical hardware management.
- Platform as a Service (PaaS): PaaS offers a platform for developing, deploying, and managing applications over the Internet. It includes development tools, middleware, databases, and runtime environments, abstracting the underlying infrastructure for developers. PaaS accelerates application development and deployment by providing a ready-to-use platform, reducing the need for managing infrastructure and allowing developers to focus on building and deploying applications.
- Software as a Service (SaaS): SaaS delivers software applications over the internet on a subscription basis. Users access applications through web browsers or APIs, and the software is hosted and maintained by the cloud provider. SaaS eliminates the need for software installation and maintenance, offering convenient access to applications from anywhere with an internet connection and reducing IT management overhead.
- Deployment Models
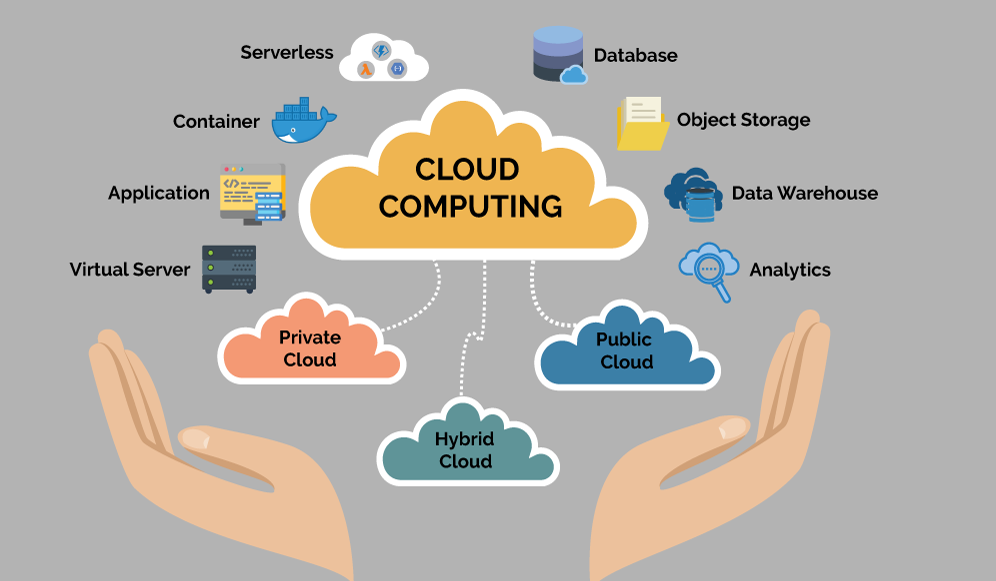
- Public Cloud: Public clouds are operated by third-party cloud service providers, offering computing resources over the Internet to multiple users or organizations. Public clouds are scalable, cost-effective, and accessible, making them suitable for a wide range of applications and workloads, especially for startups and small businesses.
- Private Cloud: Private clouds are dedicated cloud environments operated solely for a single organization, offering greater control, security, and customization compared to public clouds. Private clouds are preferred by organizations with stringent security and compliance requirements, offering more control over resources and infrastructure.
- Hybrid Cloud: Hybrid clouds combine public and private cloud environments, allowing data and applications to be shared between them. Hybrid clouds offer flexibility, enabling organizations to optimize resources, meet compliance requirements, and scale applications as needed, making them suitable for businesses with fluctuating workloads or specific regulatory constraints.
- Community Cloud: Community clouds are shared cloud environments built for specific communities of users with common concerns, such as regulatory compliance or industry standards. Community clouds allow organizations within a specific industry or community to share resources and services while addressing common concerns, promoting collaboration and efficiency and maintaining data privacy and segregation.
What are the benefits of cloud computing?
The benefits of cloud computing are as follows-
- Scalability: It ensures that businesses adjust their resource usage to accommodate changes in workload to save costs.
- Elasticity: It ensures that resources adjust to the current demand without human intervention.
- Resource Pooling: This allows for efficient utilization of resources by consolidating them into a shared pool allocated to different users or applications based on demand.
- On-demand Self-Service: It empowers users to rapidly deploy and scale resources as needed.
- Broad Network Access: It enables users to access cloud services from anywhere with an internet connection and mobility.
- Cost-effectiveness: It reduces expenditures on hardware and infrastructure, offering flexible pricing models.
- Flexibility and Agility: These enable businesses to innovate and respond to market demands faster.
- Reliability and Redundancy: They minimize the risk of downtime and service disruptions.
- Security and Compliance: They enhance data protection, privacy, regulatory compliance and integrity of their data.
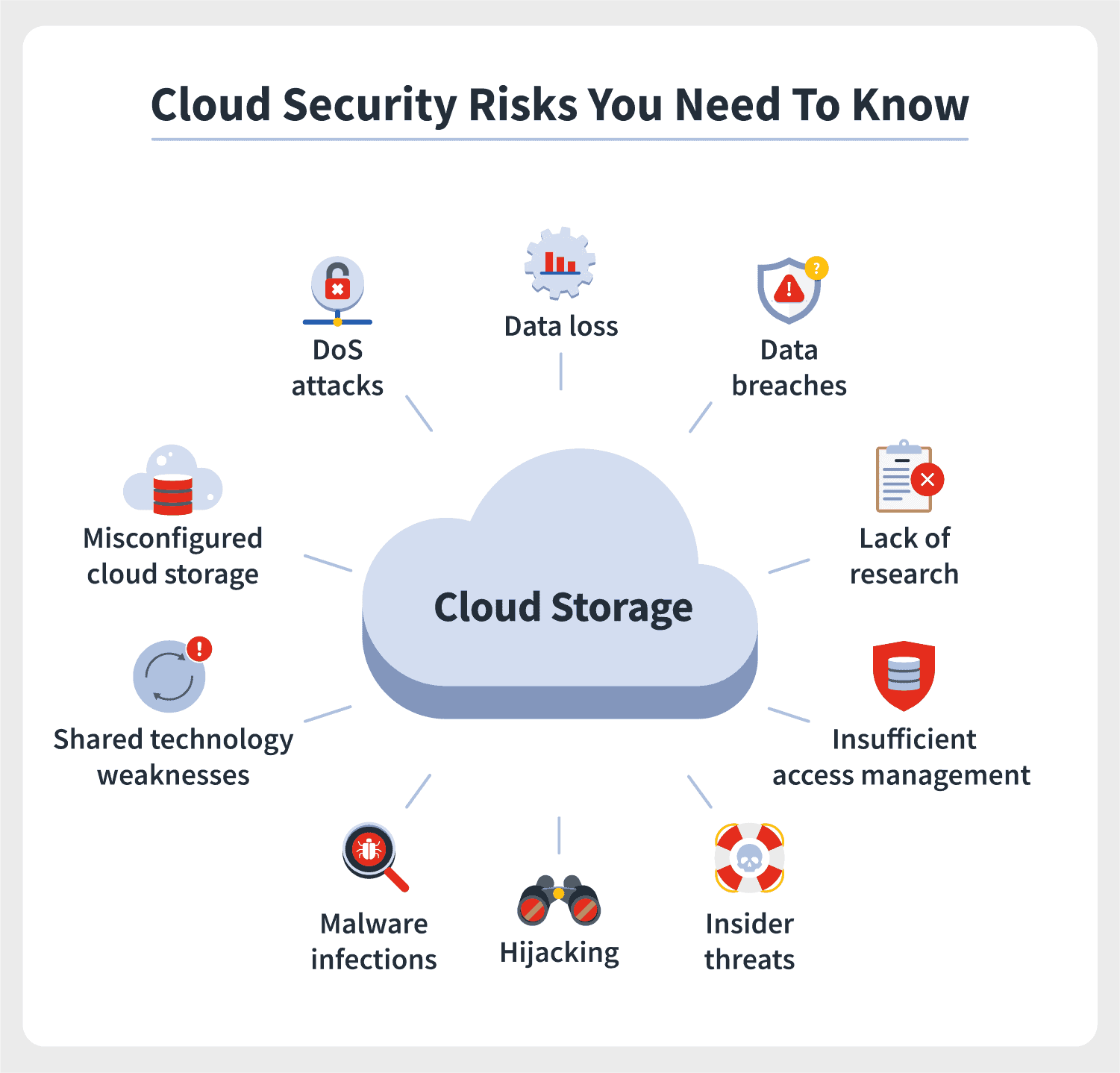
What are the challenges of cloud computing?
The challenges of cloud computing are as follows-
- Security Concerns
- Data Privacy
- Data Transfer Bottlenecks
- Downtime and Availability
- Vendor Lock-in
- Compliance and Legal Issues
- Performance and Latency
- Cost Management
- Data Governance
- Integration Complexity
What are the future trends of cloud computing?
The future trends of cloud computing are as follows-
- Edge Computing: As more and more devices connect to the internet, there is a need to process data closer to where it is generated. This trend, called edge computing, is likely to become even more common.
- Serverless Computing: Developers love serverless computing because it lets them focus on writing code without worrying about managing servers. This trend is probably going to stick around because it is efficient and scalable.
- Hybrid and Multi-Cloud Environments: Companies are starting to use a mix of different cloud services to get the best of each one. This trend is expected to grow as businesses try to balance performance, cost, and reliability.
- AI and Machine Learning Integration: Cloud providers are offering more tools for AI and machine learning, making it easier for developers to use these technologies in their apps. We will likely see even more of this in the future.
- Containerization and Kubernetes: Containers are a popular way to package and run applications, and Kubernetes helps manage them. This is becoming the standard way to handle applications in the cloud.
- Quantum Computing: Quantum computing is still in its early stages, but it could change the game for cloud computing and many other industries. Cloud providers are already looking into it, and we will probably see more developments in the future.
- Data Sovereignty and Compliance: With stricter rules about data privacy, companies need to make sure they are following the rules no matter where their data is stored. Cloud providers will need to offer solutions that help with this.
- Zero Trust Security: Old-school security models aren’t cutting it anymore in today’s connected world. Zero Trust security, which assumes threats could come from anywhere, is getting more attention and will probably be a big focus in the future.
- Serverless Databases: Just like with serverless computing, serverless databases take the hassle out of managing infrastructure. Developers can focus on building their apps without worrying about database stuff.
- Green Cloud Computing: People are becoming more aware of the environmental impact of technology. We will likely see more demand for cloud services that use renewable energy and are designed to be more energy-efficient.
Where can I learn cloud computing?
You can get the best cloud computing training at Network Kings, where you can learn directly from experts. The student-oriented training helps to understand cloud computing better by providing 24*7 access to the world’s biggest virtual labs with zero downtime.
At Network Kings, you will get to enjoy the following perks-
- Learn directly from expert engineers
- 24*7 lab access
- Pre-recorded sessions
- Live doubt-clearance sessions
- Completion certificate
- Flexible learning hours
- And much more.
AWS Cloud Security Master Program
If you are looking forward to specialising in AWS cloud security, utilizing both cloud and security techniques, opt for our AWS Cloud Security Master Program comprising-
- AWS Solutions Architect Associate
It covers designing and deploying, cost-effective security measures, and cloud solutions using Amazon Web Services (AWS) technologies.
The exam details of the AWS Solutions Architect Associate are as follows-
Exam Name: AWS Certified Solutions Architect – Associate
Exam Code: SAA-C02
Exam Cost: 150 USD
Exam Format: Multiple-choice and multiple-response questions
Total Questions: Approximately 65
Passing Score: 720 out of 1000
Exam Duration: 130 minutes
Languages: English, Japanese, Korean, and Simplified Chinese
Testing Centers: Pearson VUE testing centers
- AWS Security
It covers the knowledge of securing Amazon Web Services (AWS) infrastructure, services, and data against potential threats and vulnerabilities.
The exam details of the AWS Solutions Architect Associate are as follows-
Exam Name: AWS Certified Security – Specialty
Exam Code: SCS-C01
Exam Cost: 300 USD
Exam Format: Multiple-choice and multiple-response questions
Total Questions: Approximately 65
Passing Score: 750 out of 1000
Exam Duration: 170 minutes
Languages: English, Japanese, Korean, and Simplified Chinese
Testing Centers: Pearson VUE testing centers
- AWS Certified Advanced Networking – Speciality
It covers advanced networking concepts and practices within the AWS cloud environment.
The exam details of the AWS Solutions Architect Associate are as follows-
Exam Name: AWS Certified Advanced Networking – Specialty
Exam Code: ANS-C00
Exam Cost: 300 USD
Exam Format: Multiple-choice and multiple-response questions
Total Questions: Approximately 65
Passing Score: 750 out of 1000
Exam Duration: 170 minutes
Languages: English, Japanese, Korean, and Simplified Chinese
Testing Centers: Pearson VUE testing centers
Azure Cloud Security Master Program
If you are looking forward to specialising in AWS cloud security, utilizing both cloud and security techniques, opt for our Azure Cloud Security Master Program comprising-
It covers the fundamentals of Azure cloud services and provides the skills required to deploy, monitor, and manage Azure resources.
Exam Code: AZ-104
Exam Cost: 165 USD
Exam Format: Multiple-choice questions, scenarios-based questions, and interactive items.
Total Questions: 40 to 60 questions.
Passing Score: Approximately 700 out of 1000.
Exam Duration: 180 minutes (3 hours).
Languages: English, Japanese, Simplified Chinese, Korean, and Spanish.
Testing Centers: Available at designated testing centers worldwide.
It covers security technologies and features used to secure Azure resources and fulfil compliance requirements.
Exam Code: AZ-500
Exam Cost: 165 USD
Exam Format: Multiple-choice questions, scenarios-based questions, and interactive items.
Total Questions: 40 to 60 questions.
Passing Score: Approximately 700 out of 1000.
Exam Duration: 180 minutes (3 hours).
Languages: English, Japanese, Simplified Chinese, Korean, and Spanish.
Testing Centers: Available at authorized testing centers worldwide.
It covers the skills and knowledge required to manage Azure resources, implement and monitor security, and optimize cloud infrastructure.
Exam Code: AZ-700
Exam Cost: 165 USD
Exam Format: Multiple-choice questions, case studies, and interactive items.
Total Questions: 40 to 60 questions.
Passing Score: Approximately 700 out of 1000.
Exam Duration: 180 minutes (3 hours).
Languages: English, Japanese, Simplified Chinese, Korean, and Spanish.
Testing Centers: Available at authorized testing centers globally.
What are the job opportunities after the cloud computing course?
The top available job opportunities after the cloud computing course are as follows-
- Cloud System Engineer
- Cloud Administrator
- Cloud Developer
- Frontend Developer
- SQL Database Developer
- Cloud Security Analyst
- Cloud Network Engineer
- Cloud Automation Engineer
- Cloud Consultant
- Cloud Engineer
- Cloud Software
- Cloud Architect
- Data Engineer
- Cloud Database Administrator
- Backend Developer
- Java Cloud Developer
- Development Operations Engineer
- Data Scientist
- Platform Engineer
- Full Stack Developer
What are the salary aspects for a Cloud Security Engineer?
The salary aspects of a cloud security engineer in different countries are as follows-
- United States: USD 90,000 – USD 150,000 per year
- Canada: CAD 80,000 – CAD 130,000 per year
- United Kingdom: GBP 50,000 – GBP 90,000 per year
- Germany: EUR 60,000 – EUR 100,000 per year
- Australia: AUD 90,000 – AUD 140,000 per year
- India: INR 6,00,000 – INR 15,00,000 per year
- Singapore: SGD 80,000 – SGD 120,000 per year
- Brazil: BRL 80,000 – BRL 150,000 per year
- Japan: JPY 7,000,000 – JPY 12,000,000 per year
- South Africa: ZAR 400,000 – ZAR 800,000 per year
- UAE: AED 180,000 – AED 300,000 per year
- Saudi Arabia: SAR 180,000 – SAR 300,000 per year
- China: CNY 200,000 – CNY 400,000 per year
- South Korea: KRW 60,000,000 – KRW 120,000,000 per year
- Mexico: MXN 500,000 – MXN 900,000 per year
Wrapping Up!
Grab this chance to upgrade and become a top-notch Cloud Security Engineer today. If you are looking to learn what is cloud computing, consider enrolling in our AWS Cloud Security Engineer Master Program and Azure Cloud Security Engineer Master Program today. Should you have any questions or require assistance, please do not hesitate to reach out to us through the comment section. Your queries are welcome, and we are here to help!
Happy Learning!