What skills are needed for Cyber Security – if you want to know the answer in detail, keep reading the blog till the end. As technology becomes more and more integrated into our day-to-day lives, it is essential to make sure that data privacy and network protection are up to scratch. Cybersecurity is an area of expertise that entails a certain level of knowledge and skill in order for one to be successful.
This blog post will delve deeper into what skills are needed for Cyber Security world as well as take a look at some educational pathways available for those wishing to gain further cyber aptitude. We will discuss everything from understanding potential risks associated with various tech tools all the way through protecting digital assets – to dishing out pertinent information on how best to become proficient in this ever-evolving field! What do you need to know about thriving in cybersecurity?
Understanding the Buzz: Defining CyberSecurity

Sometimes trying to understand cyber security can feel just like a foreign language, what with all the acronyms and technical jargon. It is no wonder it can be hard to know where to start! But getting your head around the basics of cyber security is essential in order to protect yourself from online threats – that being said, this article should help you get clued up by explaining some of the most commonly used terms when discussing matters related to digital safety.
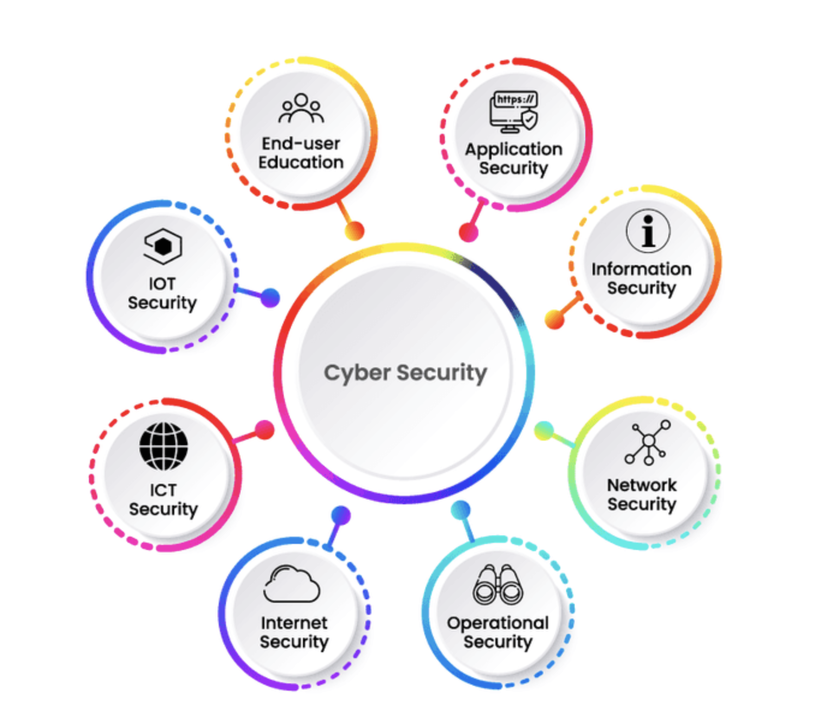
Cyber security is an expansive term that deals with activities intended to protect data, networks, and systems from malicious attack or misuse. It encompasses everything from firewalls and encryption technologies, all the way up to secure coding practices and system monitoring tools – in basic terms cyber security measures are created for actively warding off any digital danger that could potentially be caused by hackers, viruses or other malicious software.
Network security forms a major part of an effective overall cyber defense plan. Network Security concentrates on shielding a company’s IT infrastructure from illegal access points or disruption – fundamentally safeguarding it against interference!
When it comes to cyber security, there are a plethora of measures that must be in place. Network switches and routers need to be securely configured as well as firewalls which determine what data can pass through the system and who has access rights. Additionally, with regards to keeping information secure both while stored (at rest) and whilst traveling between networks (in transit), measures such as data encryption have an essential part to play; encrypting sensitive info so that it cannot be read until decrypted by way of its corresponding key.
Authentication protocols are essential when it comes to cyber security; they require users to provide proof of identity before accessing certain areas. Penetration testing is also a key element in any cyber security plan as its purpose is to uncover weaknesses within an IT system by simulating real-world attack scenarios so that organizations can take steps and put preventive measures in place that will be more resistant to future breaches.
Lastly, authentication processes such as username and password combinations or biometric methods like thumbprints or facial recognition scans are used by both large and small organizations alike for verifying user identities remotely – thus safeguarding their systems from unauthorized access attempts while ensuring no sensitive information gets leaked out of the network. But what other ways do companies use today to ensure secure online operations?
An Overview of Key Cyber Skills: What Skills are Needed for Cyber Security

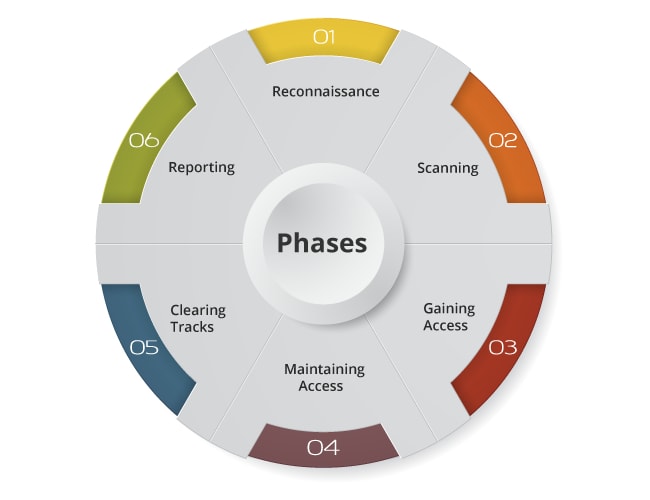
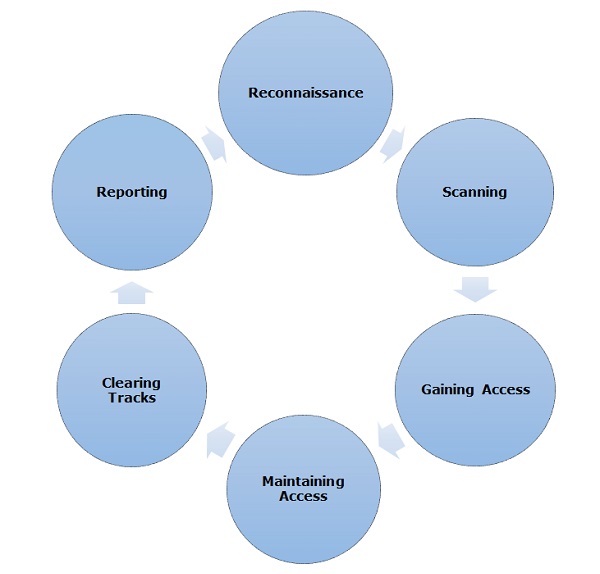
Coming to Cybersecurity, there is no one-size-fits-all approach that can help protect from all possible threats. Rather, a number of cyber skills have to be developed in order for the network environment to stay secure and impenetrable. An Overview of Key Cyber Skills takes into account the most essential knowledge and abilities that should be acquired through training or hands-on experience; thus this blog post aims to explore these key cyber skills so that you decide which ones suit your requirements best. To start with, it’s imperative that each cybersecurity professional has a sound understanding of cryptography – without it, their job would just not make sense!
Cryptography is the use of mathematics and technology to keep data away from people who aren’t supposed to have access to or change it. It is used so that even if unauthorized persons get their hands on the information, they won’t be able to read or alter it. To become good at cryptography a cyber expert must know how encryption works in great detail, possess a solid knowledge of cryptographic algorithms, and understand what happens when you start using encryption on various platforms or networks.
Another important part of being an ace cyberspace security professional involves scrutinizing potential malicious software (malware) and taking steps to reduce its harm whenever possible. Malware is essentially computer code created with one aim – sneaking into computers and networks without setting off any alarms!
Getting a grip on how malware functions and having the capacity to recognize it is vital for any cybersecurity master who needs to secure their frameworks from attack or bargain. Experienced pros additionally need to comprehend what kind of effect malware has on systems and networks, just as the best way possible they can alleviate its effects when it occurs.
Network security is under essential part of making compelling Cybersecurity methods too. It is critical that specialists have enough knowledge about these strategies so they are better ready during inevitable attacks while keeping their data safe constantly. While every individual framework may vary regarding security prerequisites; underneath everything lies an equivalent common goal i-e helping organizations protect against targeted cyber threats with efficient policies and estimate procedures at all times!
Network security is all about making systems secure from external threats such as hacking attempts and also having internal policies for network users. It involves monitoring logs, and traffic patterns to detect any suspicious activity and then responding accordingly if an intruder attempt has been found. Also understanding the topologies and protocols helps in configuring firewalls which adds extra protection against malicious actors trying to access networks unethically.
Moreover, being able to identify strange behaviour within a system can stop intrusions that would have caused damage otherwise counting changes or downloads outside regular work hours might alert cybersecurity departments before someone unauthorized gets into their environment.
Deeper into Cyber Protection: Network Protection Skills

When it comes to cybersecurity, network protection skills are absolutely essential. Cyber attackers have access to resources and techniques that make cyber security a priority these days. In this blog post, we will be looking into what kind of network protection abilities you need in order to keep your data and systems safe from malicious hackers.
It is key for protecting yourself from cyberattacks that you understand the fundamentals behind networking. This includes knowledge about IP addresses, protocols, ports, network architectures, VPNs as well other basic aspects linked with networking safety – all topics that must not be overlooked!
Having familiarity with the fundamental aspects of firewalls and encryption means you will be able to set them upright, as well as make sure any connections are properly protected. You should also have a good understanding of different kinds of attacks and how they operate so that you can identify and oppose them effectively. What’s more, having an informed grasp on authentication systems such as two-factor authentication will make certain only individuals who are authorised are permitted access to files or systems. Utilizing secure protocols stops malicious forces like hackers or viruses from accessing stuff without permission – which is why strong authentication methods play an important role in creating safe networks.
It is absolutely critical to use strong passwords featuring uppercase characters, numbers, and special symbols when it comes to cybersecurity. Not only does this help reduce the possibility of a brute force attack but also adds an extra layer of security. Besides that, implementing appropriate monitoring protocols is important for being able to spot suspicious activity on your network right away – before any potential damage could be done.
This way you can take any necessary measures quickly enough in order to minimize risks associated with such intrusions or other malicious activities. Furthermore, regular checks should be conducted if applications or operating systems have any exploitable vulnerabilities as these might leave your system wide open; so best make sure they’re addressed without delay!
Having the right logging tools is essential for keeping tabs on all activities taking place on your network, allowing you to pick up any odd behaviors or unauthorized access attempts quickly. It is especially important within businesses due to likely sensitive customer data and valuable intellectual property being present – therefore security procedures should be taken very seriously here. To make sure social engineering doesn’t work its way into your company, employee education is necessary; show them how to recognize phishing emails as well as common indications of malware infiltration in their device so that potential break-ins can be prevented from occurring at all costs.
In conclusion, strong networks are built by having both technical knowledge (understanding networking principles) alongside good security practices (monitoring activity and routinely applying updates). This will give organizations the best chance of protecting themselves against cyberattacks.
The Role of Data Privacy in Cyber Security
When it comes to cyber security, data privacy is something every organization needs to bear in mind. With hackers becoming increasingly sophisticated and data breaches more common occurrence, organizations must make sure that their data is safe and protected. Technological measures like encryption or multi-factor authentication can be applied for the prevention of a breach but they cannot guarantee complete safety. To ensure secure handling of personal information within the organization there should also be policies and procedures put into place.
When it comes to data privacy, one must take extra caution. This means having policies in place that limit who has access to the data, as well as ensuring all employees are aware of proper storage practices and regularly auditing control systems; without these measures, any breach could jeopardize a company’s system. But not only does this protect an organization from attack – protecting customer information is equally crucial too since hackers often target organizations with large amounts of customer info available: how secure can we be sure our customers’ details really are? Taking steps now towards better security will ensure peace of mind for both your business and its clients alike.
Figuring out what information your customers need for their business operations and allowing only authorized people access to it is one of the most important steps you should take. Moreover, making sure that laws like GDPR are being adhered to in order to protect users’ private info shouldn’t be overlooked either.
Organizations have got to understand that if they don’t pay enough attention when it comes to keeping customer data secure, not only will they put themselves at risk but also those same customers – who could find themselves victims of identity theft or other malicious acts from hackers who get into accounts or networks illegally. So really, the question is; how much effort are organisations willing to make towards protecting this vital information?
When it comes to cyber security, data retention is also key. If an organization doesn’t store certain types of confidential user information then they’re less likely to become the target for hackers or other malicious actors looking for this sort of thing. But there’s more than just a security issue here; if companies aren’t careful about how long they retain personal details from their users, then that could be seen as violating someone’s right to privacy, leading them into trouble with the law in the future – and nobody wants that! What measures should businesses take to protect users while still adhering to legislation?
It is essential for organizations to make sure they get their heads around both the risks attached to storing specific types of user data and any local regulations regarding what kind of customer or employee details need saving. The bottom line is, that knowing and implementing decent processes on issues such as this can help guarantee companies have a sound cyber security plan in place and are doing everything possible to defend their digital resources – not only from external dangers but also from inside misuse or misuse of delicate individual info too!
Are you allocating enough time or money to your company’s cybersecurity strategies? Have you made changes recently due to new laws in different regions that may affect how user information is handled within your organization?
Expertise Required: Important Technical Education for Cyber Security
The demand for cyber security is growing exponentially, which just goes to show how important it has become. Surprisingly though, there are certain technical abilities you must have in order to make a successful career out of being a cybersecurity pro.
Knowing programming languages such as HTML, JavaScript, CSS, Python, and Ruby – the ability to write patches and fix flaws in web applications depends on this – is essential. You also need good database knowledge; working with systems like MySQL or PostgreSQL will help develop secure applications that stand up against any threats.
Having an understanding of networking technologies such as routers and switches can be really helpful when it comes to designing secure networks or even spotting any intrusions on existing ones. And if you know the insides of operating systems, then you will be able to harden them up against those script kiddies exploits that rely upon vulnerabilities in these systems. Additionally, being familiar with cryptography and encryption methods gives us a great advantage while decrypting passwords quickly or dealing with data that has been purpose-obfuscated somehow.
Lastly, possessing basic knowledge about hardware components is definitely beneficial too – particularly if we are planning for device forensics purposes! At first sight, all this may feel overwhelming but luckily enough they can all be easily mastered by simply reading quality materials coupled with some dedication during our practice sessions.
The more effort we put into sharpening our technical skills now, the greater rewards it should bring in the future – so let’s take time today to invest ourselves in learning security techniques essential for success!
Cyber Skills: A Closer Look Towards Mastery

When it comes to cyber security and the skills needed for a pro in this field, there is much more than technical knowledge involved. Cybersecurity is something vast and complex that requires lots of understanding as well as experience to master properly. It isn’t only about having the capacity to set up antivirus software or delete viruses from computers either – there’s far more involved.
In this piece, we will explore those essential cybersecurity abilities necessary for mastering them all! Problem solving stands out among other key skills when it comes down to cybersecurity; yet what does that really mean? How can someone develop problem-solving aptitude or talent? These are questions worth asking if you want to enjoy success within such a competitive industry… Good problem-solving abilities are essential in cyber security.
They enable you to identify an issue, trace it back to its source, and develop solutions that will address the problem at hand – whether this be troubleshooting computer systems, identifying malicious software, or finding any vulnerabilities in networks that could potentially be taken advantage of by criminals. Problem solvers also need very good analytical skills as well as being able to think outside the box if presented with tricky problems without clear-cut answers.
Communication is just as crucial for mastering cyber security too though; expressing your thought process clearly and concisely can make all the difference when it comes to successfully handling a difficult situation – so why not hone these skills today?
Being able to effectively communicate issues and potential threats is essential in order for organizations to be ready for anything that comes their way. Cybersecurity professionals need the ability to work with different teams within an organization so as to create firm security measures and processes by which they can handle any type of threat encountered.
The key here lies in learning how best one can explain technical concepts and procedures using language that both IT personnel, as well as those without a technical background, will understand. Asking yourself questions such as “What other ways could I put this across?” or “How do I make sure everyone understands what needs doing?”, may help you reach your goal!
Finally, staying on top of your learning is absolutely crucial for mastering cyber security. New technologies are being developed all the time, vulnerabilities are getting patched and criminals come up with new techniques regularly – making it very hard even for experienced professionals to keep track without dedicating some serious study time!
Cybersecurity experts should always aim to stay abreast in their field, including languages like Python or Java which often get used when coding tasks connected to cybersecurity operations as well as other important disciplines closely related such as cryptography and malware analysis; skills they can only gain effectively through proper focus beyond what’s taught in college courses.
Importance of Continuous Learning in CyberSecurity

Cybersecurity is no longer a nice to have, but an essential piece of any IT professional‘s armoury. As companies get more digitalised the demand for knowledgeable cybersecurity experts has never been greater. But as technology develops so do the risks against it, which means that anyone in cyber security must be willing to learn continuously if they want to beat out hackers. Constant learning is paramount for staying up to speed with the constantly changing world of cyber safety and warding off attacks on firms. Have you got what it takes? Or does this sound too daunting?
It is absolutely essential to keep up with the most recent cybersecurity trends. For instance, IT professionals must be aware of any new viruses that attack susceptible systems, they should understand fresh technologies like AI and machine learning which can help identify oddities in networks and also stay on top of alterations in data protection laws so firms conform to applicable regulations.
Do we have all the necessary equipment for proper system monitoring? Have you thought about implementing a dedicated network intrusion prevention system (NIPS)? What is your opinion regarding deploying artificial intelligence algorithms when it comes to detecting potential intrusions?
It is essential that IT professionals in the cyber security field stay up-to-date with developments and do their research regularly. This means they must always make sure to keep learning – it is a nonstop process! Gaining cybersecurity certifications is also incredibly useful, as it not only shows off their expertise but attests to the fact they have attained an industry-recognized qualification or badge. Plus, who doesn’t want some extra virtual bling?!
Gaining certifications can be a great way for cyber security professionals to deepen their understanding of topics such as ethical hacking, secure coding practices, and advanced threat detection techniques – allowing them to hone their skills further and better defend organizations from attack.
Attending conferences or events related to this industry also offers the chance to network with other like-minded individuals in your field, hear talks by experienced experts who may share ideas that could both inspire you but also challenge any pre-existing knowledge base; enabling you to uncover new perspectives on key issues affecting areas right now.
Plus attending these sorts of conferences keeps one abreast of cutting-edge tech trends that might have an effect on the world of cybersecurity this includes breakthroughs such as quantum computing – highlighting yet again why staying upskilled is so important if we’re going see success today and tomorrow!
Strengthening Network Protection: Skills and Techniques
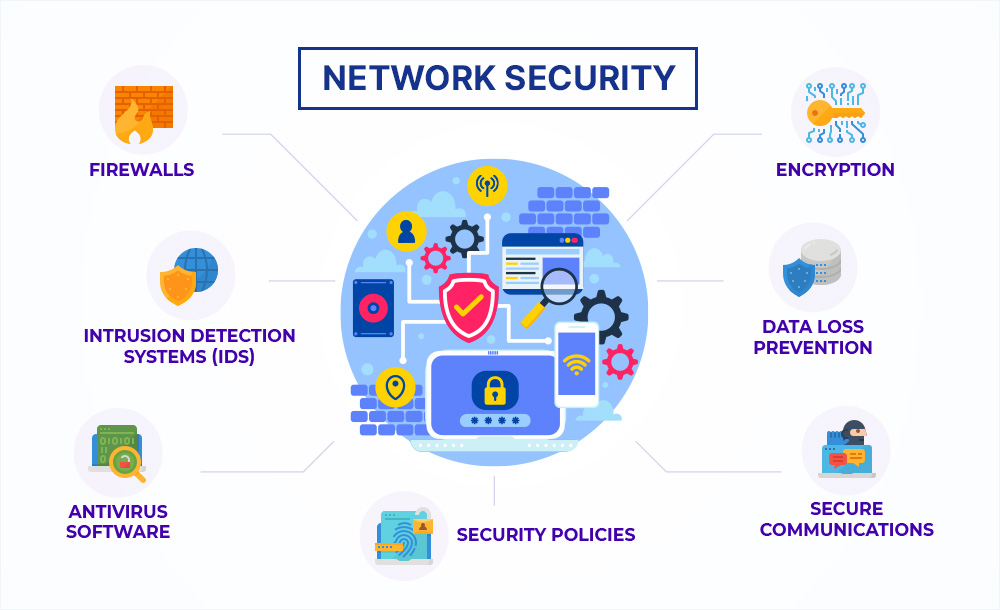
When it comes to staying safe online, there is no getting away from the fact that you need a range of key skills and techniques for network protection. Cybersecurity is becoming increasingly important as cyber-attacks are on the rise every single year – so having an understanding of basic security principles is essential if you want to keep your data secure.
One particularly crucial element when it comes to network protection relates specifically to firewalls: make sure all devices connected to the same network have firewall protection enabled, which should then be regularly updated with any new patches or updates issued by developers! This can provide peace of mind knowing that your technology has been given some extra support in terms of its safety measures – but do bear in mind how vital regular reviews may be; spending time ensuring these are up-to-date could end up saving lots more trouble further down the line…
Firewalls are an extra layer of protection to stop any unauthorized access or dodgy activities on a network, so keeping them up-to-date is really important for getting the best security. It is also massively vital that users have robust password rules in place when it comes to accounts shared around networks – passwords should be one-offs and often changed over time just to make sure no one can get into someone else’s account without authorization. Experts would suggest making all your passwords 8 characters long with lowercase letters, uppercase letters, numbers, and symbols thrown in too for good measure!
As well as enabling two-factor authentication to add an extra layer of security when accessing online accounts, it is important to make sure that only trusted applications are running on a system for maximum network security. This means installing anti-malware software or antivirus programs onto every computer and device connected to the same network. These types of programs will scan incoming traffic for threats such as malware or viruses which can be blocked from entering if detected.
This provides an extra layer of security; nonetheless, even after installation is complete, vigilance needs to remain in order to keep up with newly evolving threats. Furthermore, being mindful of phishing scams is absolutely essential for safeguarding networks from unwanted intrusions; these emails are often disguised as genuine messages sent from trustworthy sources but the links they contain lead directly to malicious software downloads and other detrimental activities within a user’s computer system once clicked on.
Therefore, teaching users about how this kind of scam works equips them with the knowledge needed so that they can spot potential danger quickly – ensuring no suspicious communication or attachments get opened – thus making sure hackers have far fewer chances at accessing their systems without authorization.
Data Privacy Policies: A Must-have Skill for Cyber Security

The cyber-world is an ever-expanding, always-changing environment that demands a great deal of expert knowledge. One crucial talent that can be easily forgotten in the digital realm is comprehending data privacy policies. Being conversant with these regulations could help to reduce security hazards and ensure compliance with privacy matters.
A well-rounded familiarity with data protection rules will go a long way towards preventing any sort of data breach, keeping users’ sensitive information from being accessed without their permission as well as giving people mental assurance regarding their safety online. Data privacy standards are critical pieces for preserving safe systems and networks alike.
When it comes to data privacy policies, they spell out the details about what info an organization collects and stores – including who has access to it and how long that will be for. Having a grip on this information is critical so we can get our head around any security risks that might exist, as well as know exactly what needs doing to reduce these risks. When constructing such a policy there are two key areas of focus: legal requirements determined by governing bodies plus industry standards when it comes to protecting personal data or confidential documents (such as best practices).
No matter, if you are developing new systems or auditing existing ones, being aware of data privacy policies, is an essential skill for anyone in cybersecurity. Having this knowledge and understanding of which laws should be implemented as well as the best practices to follow, helps ensure that all data will always be managed correctly and any potential security dangers can easily be identified before they cause serious harm.
Plus, adhering to these standards allows people to take advantage of their rights when utilizing online services or resources with peace of mind knowing that everything’s secure. Crucial measures must also be included within each organization’s policy on data protection; such steps include firewalls, password encryption methods two-factor authentication protocols virus scans along other precautionary features designed specifically so unauthorized parties don’t access nor misuse the sensitive information stored by a system network, etc…
Moreover, processes should exist detailing how organizations respond if ever there is a breach where inappropriate use occurs – regardless of whether intentional or unintentional. What would your response plan consist of?
Tech Education: A Cornerstone in Building Cyber Skills
We all know that technology is really powering the future, and there is a lot of discussion regarding the significance of tech education in the security area. While many may believe that getting an IT degree would be adequate for equipping someone with skills to excel at cybersecurity, there’s actually a large range of other areas that should also be studied. After all, cybersecurity includes protecting systems from malevolent threats and assailants – so having knowledge about programming languages; coding conventions; network safety practices, etc is indispensable for any position within this domain.
Aside from technical know-how, having a good grasp of business processes is also key. Knowing how firms operate can assist specialists in quickly pinpointing vulnerable areas and taking action before adversaries have the chance to exploit them. Possessing great problem-solving and communication aptitudes is necessary for being able to spot hazards as they arise – not forgetting that one must be capable of conveying complex concepts in simple language to colleagues who don’t possess an equivalent level of tech literacy.
Wrapping Up!
To sum up, staying afloat with technological advances plays a major role for any person wanting employment within cybersecurity. As there are brand new tactics developed every week to attack networks; those manning the fort need to constantly evaluate their strategies while understanding what developments and technologies may mean down the line. Keeping abreast of industry news is pivotal if pros wish to find success in this area – only reading textbooks on cyber security theory isn’t going cut it anymore seeing as ideas become obsolete rapidly unless renewed often enough!
To round things off, it is evident that if you want to stay up-to-date with cyber security then there are certain skills and knowledge bases that must be achieved. We are talking about network defence, data privacy as well and tech teaching. It is vital for those in the info safety or planning on entering this arena to know these matters inside out. By giving time and money into growing their ability sets companies can guarantee their information is kept safe from any malicious intentions. What other steps do employers need to take in order to keep digital assets secure?
Are you keen to boost your career in cybersecurity? Then why not join our Cybersecurity Master Program and take advantage of all the impressive expertise we have gathered? We provide a thorough training program with hands-on sessions conducted by professionals working in this field, so you can be sure that what they are teaching is up-to-date and relevant.
Our bespoke course material has been created specifically for each student’s individual needs, giving them the skills required to make it big time within the cybersecurity industry. You will also get access to top-notch resources as well as valuable insights into the present-day and future tendencies when it comes to cyber security. Don’t procrastinate – sign up today and jump on board this information security revolution! Who knows where it could lead if you grab onto every opportunity available..
Happy Learning!