
Intrusion prevention and Detection Systems (IPS/IDS) are security technologies designed to protect computer networks from malicious activity. IDS vs IPS get often used together to provide comprehensive protection.
IPS is a system that monitors network traffic, identifies suspicious activity, and then prevents it from happening. It is typically put to use to block malicious traffic from entering a network or from leaving a network.
IDS is a system that monitors network traffic and identifies any suspicious activity. However, it typically does not block the operation. Instead, it will alert a user or system administrator of a potential threat, who can then take action to protect the network.
What is IDS?
IDS stands for Intrusion Detection System. It is a system or software application that monitors a network or systems for malicious activity or policy violations. It can use different techniques to detect malicious activities, such as network traffic analysis, file integrity checking, and log monitoring. The goal of an IDS is to spot, alert, and respond to policy violations.
What is IPS?
IPS stands for Intrusion Prevention System. It is a network security technology that monitors and detects malicious activity on a network. It analyzes network traffic, identifies suspicious activity, and blocks doubtful traffic from penetrating the network.
IDS VS IPS
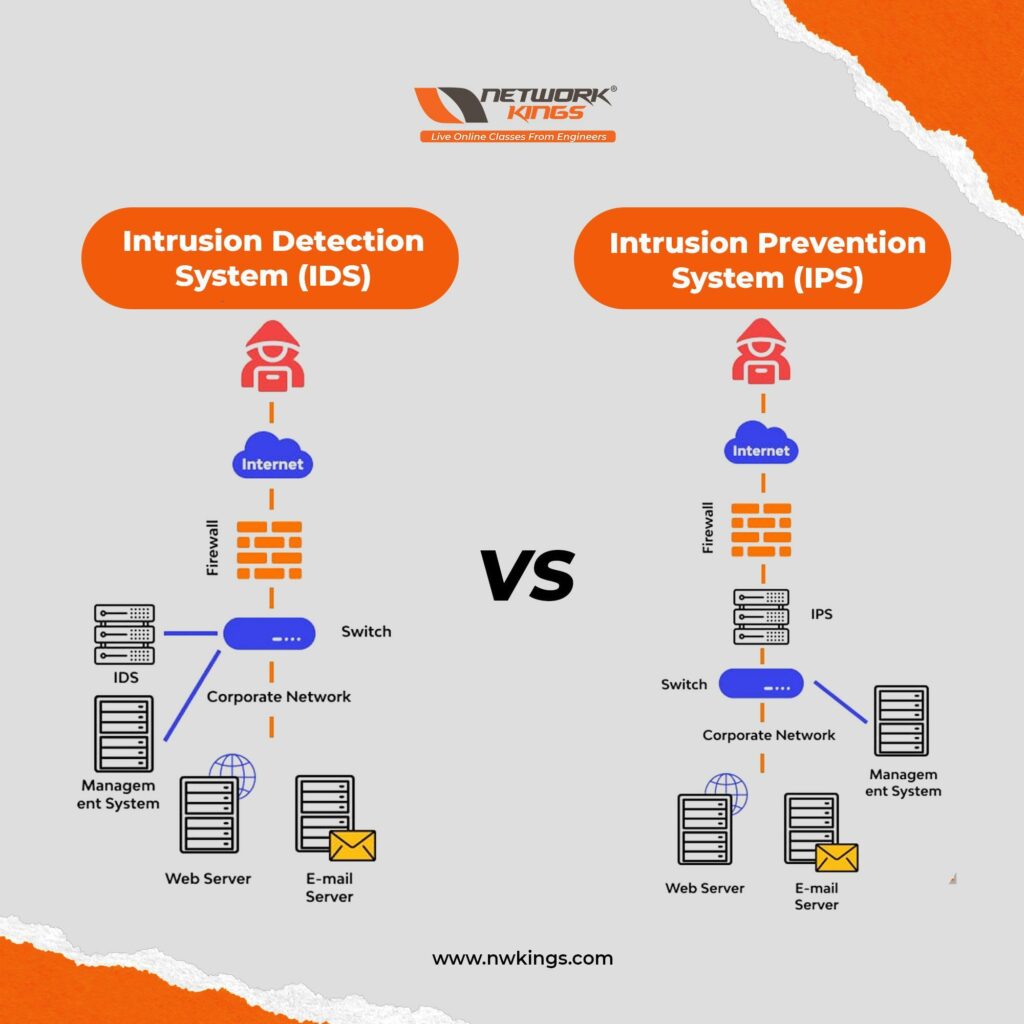
Both IDS and IPS are essential components of a network security strategy. They provide very different types of protection, and both get used to providing the most comprehensive protection.
What are the types of IDS?
The IDS lies upon the two types of detections–
- Signature-based Detection
Signature-based IDS solutions warn administrators established on pre-existing signatures referring to attack or malicious behaviour that permits accurate and automated alerts since the system points to an existing signature database.
This sort of system often seeks indicators of concession like scanning file hashes, traffic heading to known malicious domains, malicious byte series, and even email subject lines, known as phishing attacks.
- Anomaly-based Detection
Anomaly-based IDS works by monitoring network activity for deviations from normal behaviour as it hunts for patterns in user behaviour, network traffic and system configurations that are not typical, indicating that something may be wrong.
The advantage of this type of IDS is that it can detect new threats having no solution. However, its results are unreliable and can generate false positives since it yearns for deviations from normal behaviour.
The kinds of IDS are as follows-
- Network-Based Intrusion Detection System (NIDS)
NIDS monitors traffic on a network and uses signatures to detect malicious activity. It can also detect anomalies in network traffic that can indicate malicious activities.
- Host-Based Intrusion Detection System (HIDS)
HIDS monitors activity on a single host and is more effective at detecting malicious activity specific to a single host.
- Protocol-based Intrusion Detection Systems (PIDS)
PIDS is positioned at the front of a server and observes the flowing traffic to and from devices. It secures users browsing data on the internet.
- Application protocol-based Intrusion Detection Systems (APIDS)
APIDS is equivalent to a protocol-based system in innumerable ways, but the only difference is that it examines traffic across a group of servers. It depends upon explicit application protocols to monitor activities and help network administrators better differentiate and organize the network inspection activities.
- Hybrid Intrusion Detection Systems
Hybrid IDS delivers a medley of the above kinds of intrusion detection. Some vendors offer a variety of IDS to shield numerous systems in a single interface.
What are the types of IPS?
- Network Intrusion Prevention System (NIPS)
This type of Intrusion Prevention System (IPS) got designed to observe and detect malicious activity on a network. It monitors all traffic entering and leaving the network and looks for suspicious activity or patterns that indicate an attack.
It can then take appropriate action, such as blocking the connection or alerting the network administrator.
- Wireless Intrusion Prevention System (WIPS)
This type of IPS got designed to catch malicious activities on wireless networks. It can detect unauthorized access points, rogue devices, and other malicious activities.
WIPS is identical to NIPS. The only difference is that WIPS limits wireless networks for detection and reaction against it.
- Host-Based Intrusion Prevention System (HIPS)
HIPS are frequently deployed on principal devices and hosts that an organization yearns to protect. The system monitors the flowing traffic (through and from the host) to witness malicious behaviour of a network.
- Network Behavioral Analysis (NBA)
NBA is the complete opposite of NIPS. NBA tries to search for abnormal behaviour of a system. This abnormality is found in patterns, making it prominent for detecting incidents like DDoS attacks, behaviours against the policy, and other types of malware in a network.
What are the similarities between IDS and IPS?
- Monitoring systems and networks
- Alerting on detecting a threat
- Learning new methods of threat detection
- Logging the activity
What are the distinctions between IDS and IPS?
- Response
- Protection
- Impact
Wrapping Up!
IDS and IPS are both essential components of cybersecurity since they detect and prevent threats or malicious attacks on a network. Therefore, it is necessary to segregate IDS and IPS to safeguard the systems and networks simultaneously!
Leave your queries in the comment section since we are available for help.
Good Luck!


