
Let us discuss what is the first phase of hacking. In the digital age, hacking is something that has become all too familiar. It refers to gaining access without permission to a computer or systems on a network and exploiting any weaknesses present. If you want to protect your information from cybercrime and malicious tools used by hackers, it is essential to know about the fundamentals of hacking first.
This blog will explore stage one in detail concerning phishing scams, exploitation techniques as well and measures for improving security so let us get into it! We will find out what being an ethical hacker entails and how we can put an end to unethical practices attempted against us – after all, prevention is better than cure.
Understanding the Concept of Hacking

So what is hacking all about? Put simply, it is the practice of altering and gaining access to data, programs, or networks without proper permission. It can be done for a variety of reasons – some malicious like stealing information or sabotaging systems; others more benign such as exploring ways in which security could be improved upon or software modified. But whatever its purpose may be, one thing remains constant: hackers typically make changes that don’t conform to the system’s original design specifications.
If you wanna get into hacking, the first thing you gotta do is figure out what type of system it is that you are going after and familiarise yourself with how it works. This means getting to grips with its operating systems – whether it be Windows, Linux, or Mac OS X – plus understanding all about its applications and services like web servers and mail servers, etc.
To make these changes, hackers usually use tools such as network scanners, which allow them to find vulnerable areas within a specific network; vulnerability scanners for scanning for weaknesses in computer systems; code injection utilities so they can push malicious codes into networks without anyone knowing; and exploits for exposing security holes present on certain websites.
After getting the basics right, like researching the environment around the target system (network layout and topology), figuring out if there are any firewalls in place, and understanding how they work, a hacker can start reconnaissance on their targeted systems by utilising network scanning tools such as Nmap or Nessus. These would provide an overview of services running on ports which lets you spot potential vulnerabilities that may be exploited further down the line if necessary. This also helps in locating where sensitive data may be stored within a system or network so it can then be accessed with more refined methods.
Moving onto the next phase, one must identify possible attack vectors by looking at known weaknesses of targeted systems before attempting to exploit them; this includes exploitation and post-exploitation activities – thus entering into the second stage of the hacking mission!
Knowing the Difference between Ethical and Unethical Hacking
Getting to grips with hacking can be a daunting task. It is easy to become overwhelmed by the sheer number of online tutorials and resources available, particularly since ‘hacking’ is such a broad term encompassing different activities. Knowing what separates ethical from unethical hacking is an essential part of understanding how it works in terms of cyber security, so familiarising yourself with the basics should come first and foremost.
Most people are aware that “hacking” or “cracking” has something to do with malicious or unlawful behaviour – but there is far more depth than meets the eye!
Ethical hacking is essentially breaking into a computer system for security testing purposes. In other words, ethical hackers utilise their expertise to recognise possible vulnerabilities to bolster systems against any future threats. Unethical hacking on the other hand consists of using similar methods with illegal or malicious goals in mind – like stealing data, damaging files, or destroying networks. Have you ever encountered such an instance? It is quite alarming when one considers that it can be done without consent and knowledge!
It is worth bearing in mind that regardless of the type of hacker you might become – ethical or otherwise – illegally accessing someone else’s computer without their permission is a crime punishable by law in many countries around the globe. Having said this, companies both big and small consider ethical hacking to be highly valuable when it comes to looking for ways to protect their IT systems from unauthorised access and tampering with data. They often employ ethical hackers who then test out these systems to find any vulnerabilities before they can be taken advantage of by criminals wanting access for potentially malicious purposes.
The first step in any kind of hacking is reconnaissance. This requires gathering information about the target system and can be accomplished by researching public-facing documents such as website source code; studying network architecture, user behavior, communication protocols, etc.; identifying operating systems and applications used by networks; you name it!
As an ethical hacker, understanding how different types of technology interact becomes paramount. That way one knows what attack to put into play – whether that is a brute force assault on passwords or exploiting known software vulnerabilities – so these valuable assets are safe from malicious individuals who would seek to exploit them for their gain.
Delving into Hacking Basics for Beginners

When it comes to hacking, not many know where the journey begins and can be a bit overwhelmed by it all. For those looking for an introduction into this world of tech-savviness, understanding the different types of hackers is key – because believe it or not there are good ones too! Ethical hackers work hard behind the scenes ensuring that cyber security policies are implemented correctly and safely followed by everyone.
A great way to get your foot in the door? Learning more about these ethical defenders could seem like a daunting task at first – but you will soon realise it is worth it as they play a crucial role in keeping us safe online today.
On the flip side, those who employ shady practices to get into networks and pilfer confidential data operate with black-hat hacking methods. It is essential that you have a good handle on how digital criminals speak – not just terms related to cyber security but also computer programming dialects like Python or C++ which are utilised by both law-abiding citizens and evildoers alike. After getting up to speed on these languages it will be time for some serious penetration testing!
Penetration testing is all about attacking a system or network to identify any potential weaknesses that could be exploited by bad actors. Tools such as Metasploit and Kali Linux can help you properly carry out tests while simultaneously allowing you to further build your skills in this area. It is not easy for beginners to get into hacking, but with enough effort, it will create an ideal platform for future development; particularly if cybersecurity is something you would like to pursue professionally.
Keeping up-to-date on trends related to the basics of hacking and gaining expertise over topics like malware analysis and securing networks or systems are fundamental ways of making yourself stand out amongst other professionals looking at entering the field of cybersecurity.
Significance of Cyber Attacks in Hacking

Cyber attacks are essential in the initial stages of hacking. Their use allows hackers to discover security flaws within a system, identify targets, and figure out how they can gain access. Cyber attacks are powerful due to their speediness and success rate; it is easier for them to launch such an attack than having someone break into physical networks or manually extract data from systems- which is much more complicated!
For instance, malicious hackers might exploit phishing emails as a way of obtaining sensitive details like passwords, social security numbers as well and credit card information – all with relatively little effort on their part.
Yet cyber assaults aren’t only utilised for malevolent motivations. Ethical hackers may also exploit cyber attacks to test organisations’ defences and alert them of any potential vulnerabilities they uncover. This kind of hacking is called “white hat hacking” or “penetration testing“- it involves conducting tests on the organisation’s security systems without causing any genuine harm or destruction.
The target is to spot deficiencies so that the organisation can take steps to fortify its safety defences. But do white-hat hackings work? Is there any way we could verify if an ethical hacker has done their job properly, preventing most future attack attempts from succeeding?
Furthermore, cyber assaults are likewise instrumental in supporting law enforcement investigations into online wrongdoing and other criminal activities transpiring over the web. Utilizing forensic techniques, law implementation agents can trace back the cause of a cyber attack and decide how exactly it was carried out – this gives significant intelligence that helps them apprehend culprits and bring justice against them satisfactorily.
Discussing What is the First Phase of Hacking
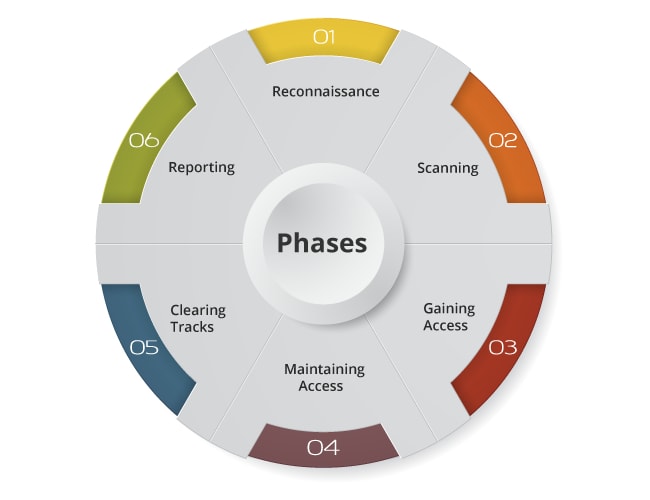
Hacking has been around for years now, and it has started to become a prominent activity as technology advances. Nevertheless, not many people are aware that hacking involves several distinctive stages. To begin with, the initial phase of hacking usually includes acquiring intel on the targeted network or system – this is commonly referred to as ‘footprinting’.
The procedure comprises collecting information such as IP addresses, user names and passwords, and other security-related details. The techniques mostly used during the first step of an attack include port scanning (checking open ports), banner grabbing (grabbing banners from networks), social engineering – manipulating users into revealing sensitive data), and vulnerability scanning(looking out for any susceptibilities).
Port scanning is a process that uses various tools to check for open ports on a host computer or network. It is an integral part of the first phase when undertaking any hacker attack. Banner grabbing involves using particular tools to view the banner information sent from a server in response to requests made by someone accessing it – usually known as ‘the client’. Social engineering plays upon human psychology and manipulation tactics intending to get confidential data, or obtain access to restricted systems; this can be done without exploiting vulnerabilities in technology.
Lastly, vulnerability scanning pinpoints potential weaknesses lying within networks and systems which could later become targets for malicious hackers if not addressed properly. It is worth remembering though that hacking success isn’t always guaranteed; so many factors come into play – ranging from having thorough knowledge about your target system and network, right up to correctly identifying exploitable weak points beforehand! To get ahead though you need to understand how each stage works separately before attempting more complex methods – such as learning exactly what port scans involve!
Exploring the Role of Phishing Scams in Hacking

Hacking is often seen as a dark and complex realm that only tech-savvy individuals can navigate. But what makes hacking so mysterious? Well, it is segmented into different stages – the first one being phishing scams.
Phishing scams are methods used to pilfer confidential information such as logins, usernames, or credit card numbers by using messages that appear to come from legitimate sources but lead unsuspecting users astray with malicious links or downloads. The damages caused by these types of attacks amount to approximately $1.5 billion every year!
This means businesses must teach their personnel how they can recognize and dodge these schemes so they do not be taken advantage of. Companies should also put adequate security systems in place that will protect corporate networks against invaders who want access to sensitive data stored on computers and servers; something like password management tools might help companies achieve this too, since they incorporate two-factor authentication when logging into accounts plus encrypting confidential info kept on devices would ensure overall safety.
By taking precautions we save ourselves loads of problems down the line while significantly reducing any risks related to hackers attempting an intrusion!
Analysing Exploitation Tools Used in Hacking
When it comes to hacking, the first step is all about analyzing and grasping exactly how a certain system operates as well as its potential weak points that can be abused. For this reason, hackers employ numerous tools to discover vulnerabilities and exploit them for their means. Some of these resources encompass port scanners, network monitors, vulnerability scanners, and platforms such as Metasploit and Core Impact.
Port scanners are employed by hackers to examine systems searching for open ports which may then be used to acquire much more detailed knowledge concerning the particular target system – ultimately potentially leading towards further exploitation opportunities or even unauthorised access.
Network analysers let hackers record network activity and analyse it for any dubious behaviour or weak points in communication protocols which may give a hacker the upper hand. Vulnerability scanners can automate checking your system to look out for known weaknesses and show outcomes clearly so that they take urgent action on them.
Finally, frameworks such as Metasploit and Core Impact provide an environment where custom exploits are written – this permits cybercriminals to craft attacks with code particularly tailored toward vulnerable systems. All these tools collectively provide attackers understanding of how systems function which consequently supplies data on the most proficient method of launching an attack against them.
Without having the correct resources at their disposal, it would undoubtedly take much longer for criminals to locate fault lines in targeted machines before mounting a successful offence – if feasible at all! It is almost like having X-ray vision without one of those tools.
The Importance of Network Security in Preventing Hacking
It is imperative to grasp the significance of network security when it comes to keeping out hackers. Network safety is an integral part of preserving your data and avoiding hacking attempts. Network security consists of a compilation of protocols, policies, processes, and practices that are deployed to reduce unauthorized access to specific computer networks’ components along with the data that they keep.
Such protections can incorporate software updates, user authentication procedures together with firewalling implementation; anti-virus protection for detecting as well as preventing malware; encryption technology etcetera – all these measures help protect your information from cyber criminals who might be looking for any possible weaknesses you have at hand within said systems.
It is essential to keep your data safe from any malicious activities, and there are a few measures you can take. Particularly when it comes to hacking, one of the most important steps is defending yourself against malware – this kind of harmful code can be used by hackers trying to gain access to sensitive info or systems. To stop that happening you need an effective network security strategy in place; think firewalls, antivirus software, and encryption for starters! How do these layers of protection work together? Can they truly make sure my personal information stays private?
One of the most effective ways for organisations to safeguard themselves from hackers is by making sure their software and systems are regularly updated with new patches. By doing this, they can guarantee any vulnerabilities that may be present in the system are dealt with before an attacker has a chance to make use of them.
The journey into hacking often starts by accessing vulnerable networks via different techniques such as port scanning or IP spoofing. It’s essential companies stay up-to-date on all sorts of methods used by cybercriminals so that they have sufficient protection against these threats – but how do you know which ones pose real danger?
Once a hacker has gained access to a network, they will be on the hunt for any weaknesses to pinch confidential data or trigger viruses and malware attacks that could do some serious damage. For this reason, it’s essential businesses have robust security protocols set up – these can help detect and prevent malicious activity before things get out of hand.
In short, strong safety measures are paramount when it comes to keeping hackers at bay; not just so intruders are kept away from your system but legitimate traffic gets in without any disruption or delay either. Without such protection though you are leaving yourself open to having sensitive information stolen as well as costly destruction caused by cyber-attacks – something which ought never be disregarded no matter how many internet-connected devices you may own or networks used!
Prevention Strategies Against Phishing Scams

Hacking is no joke – it is serious. The first step involves learning as much about it as we can, and one of the subjects to focus on should be phishing scams. These are ways for hackers to try and get their hands on sensitive data like usernames, passwords, or even credit card numbers by disguising themselves in electronic communication; this could be through emails, social media messages, malicious websites, or phone calls! It is a kind of deception that often works if people aren’t clued up enough – so why do these attackers bother with such attempts?
It is so important for us to get clued up on how these scams work and what we can do to stop them. One of the most effective preventative measures against phishing is being conscious about what kinds of messages you are getting in your emails, texts, or on social media. Take an email that may look as though it comes from a bank asking for confidential data such as passwords – got any alarms ringing? That’s probably because it is some kind of scam! The same goes for notifications popping up when you browse online and phone calls too; if something doesn’t feel quite right then trust your gut feeling and hang up or delete straight away!
It is vital to confirm who is sending these messages before offering any private information.
Another brilliant stopping strategy against phishing tricks is to keep all software up-to-date; make sure your safety programming (including antivirus) has the most modern definitions so it can detect any uncertain action on your system or gadgets. In addition, ensure that your working frameworks and web programs have been updated with the latest patches and security fixes; this will help keep hackers out of your framework just as secure you from some cruel documents or malicious code sent through emails or sites.
At long last, consistently utilize solid passwords with a blend of upper case letters, lower case letters, images, and numbers; never use straightforward words like “password” or “qwerty” which are simple for criminals attempting to achieve entrance into accounts.”
Boosting Network Security to Thwart Hacking Activities

Network security is something that should be taken seriously in this day and age. As more and more activity takes place online, the risk of malicious hackers taking advantage of weak systems to get into our sensitive information or data keeps increasing. To fight against hacking attempts we must bolster network security beginning with an extensive appraisal of all existing protocols and procedures.
So, when it comes to launching a successful attack on somebody’s system the first essential step for a hacker is acquiring knowledge about how precisely their setup works – without understanding one’s exact set-up even if you have some insightful ideas they won’t come to good use!
This could involve looking into the software being utilised, finding out potential points of entry, establishing user privileges or even carrying out vulnerability scans on the system. Any weak links can be taken advantage of by a hacker so it is important to spot any issues before they escalate.
For example, if different users have access to sections where they shouldn’t then this may well provide hackers with an easy way into your systems – not something you want happening!
Staying on top of software updates and plugging any security issues the moment they come up is also key here, as attackers will always be scouring out-of-date systems that are easier to compromise. After spotting potential weaknesses through the initial evaluation and dealing with them accordingly, you should also have plans for how you’ll handle any unusual activity that may occur. What would you do if something suspicious appeared? How quickly could your team react in such a situation? Knowing these answers now can save lots of time when it is needed most!
Having clear policies in place around who should be informed about any potential threats can help to keep damage to a minimum if, unfortunately, you are the victim of an attack. All employees throughout your organisation need to be aware and understand their roles when it comes to network security so they would know best what steps they’d have to take if attacked.
What’s more, for complete protection online organisations will require multiple layers of defence – this could include antivirus software as well as two-factor authentication methods used while logging into accounts – but before making such decisions always seek advice from expert personnel who can advise on which solutions that suit particular businesses depending upon the level of risks posed or security desired internally.
Wrapping Up!
To conclude, hacking the first phase is no easy feat. It involves learning about cyber-attacks, phishing scams, network security, and exploitation tools – a lot to take in! But with enough prepping and planning it can be done. Once you are there though, your knowledge is vast when it comes to spotting potential threats which makes responding fast so much easier; plus you know your system’s safe from attack.
Are you after a career boost in cyber security? Do you want to acquire the skills, knowledge, and qualifications required to become an expert? If so, enroll in our CyberSecurity Master Program today and get stuck into making a real difference. Our advanced training course is tailored for people of all abilities who aim to hone their expertise within this ever-developing field – giving them the tools needed to stay one step ahead of rivals.
With guidance from industry-leading professionals, we keep up with whatever’s happening in the world of cyber security by providing courses that are bang up-to-date. Additionally, there are practical learning opportunities such as lab periods or online simulations available; that way students can gain hands-on experience around potential threats too!
Above all else though, when it comes time for graduates looking for job openings we are here ready and waiting at Network Kings – connecting seekers with recruiters through our network link-ups. So if it is time to take your career forward then don’t look any further than joining us at the Cybersecurity Masters Programme! Enroll now and be part of something sensational!
Happy Learning!


