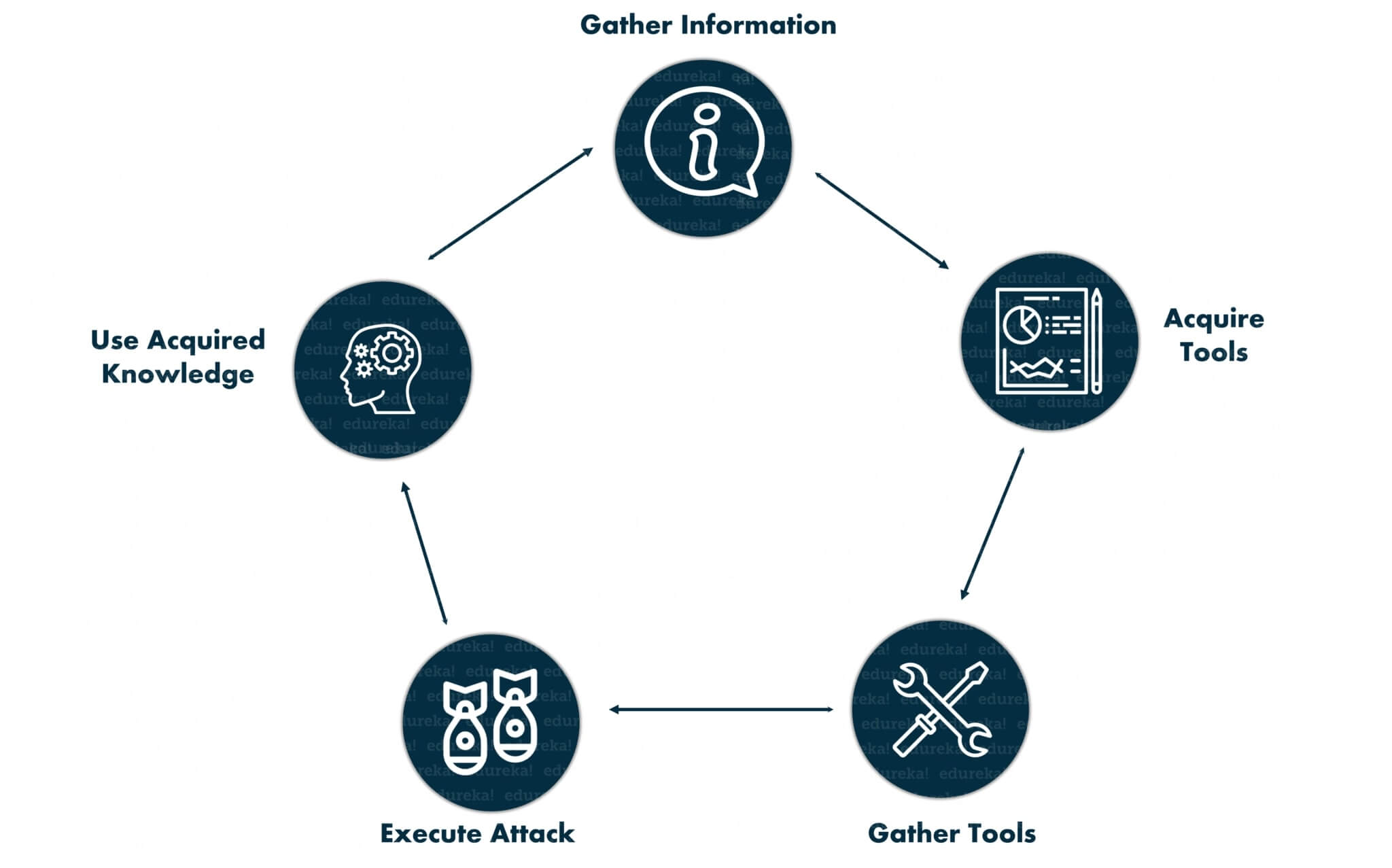
Are you intrigued by what is ethical hacking and want to find out more? Ethical Hacking is a form of cyber security that assists organizations in identifying vulnerabilities and defending their networks from data theft, malicious codes, as well as other kinds of cybercrime. To battle such dangers, moral hackers use different defense strategies, which involve probing systems and networks for potential safety threats.
They then proceed to repair the problems before they can be abused by malevolent hackers. In this blog post, we will look at what is involved with ethical hacking, how it is distinct from immoral or ‘malicious’ hacking, and the best tactics available for safeguarding your network against online attacks.
Defining What is Ethical Hacking in Modern Computing

The view of computing and technology has changed dramatically in recent years, so unsurprisingly with it the meaning of ethical hacking too. Nowadays, when we talk about ethical hacking, we mean using computer security techniques to detect potential risks in computer systems or networks. This approach is utilised by firms or individuals to stay one step ahead of cybercriminals trying to harm their IT infrastructures.
Additionally, there is penetration testing, which assesses an organization’s safety position and repairs any weaknesses that get noticed during the audit process if needed. Have you ever heard a hacker say something like ‘I’m doing this for the greater good?’
Being an ethical hacker is about more than just having technical know-how – it is a way of life where protecting customer and company info comes first. Ethical hackers have to be dedicated to preserving data security, they need up-to-date information on the threats that businesses face, as well as knowing all there is to know about system architectures, coding processes, networking protocols database structures, etc., but most importantly they must think like criminals for them to spot any possible hacking attempts directed at their systems before anyone else does. Could you do this?
It is worth highlighting that ethical hacking isn’t just about spotting potential security holes – it can involve helping organizations recover from successful cyber-attacks too. This may include assessing the extent of system damage, obtaining evidence for law enforcement agencies, reversing malicious code, and patching up any security issues identified during investigations. Because of this, more experts now consider ethical hacking to be an integral component when constructing a comprehensive information security strategy across an enterprise.
So, what is ethical hacking today? Well, it encompasses far more than simply uncovering vulnerabilities in networks or software; there are numerous activities included that promote secure networks and protect customer data privacy alike – such as penetration testing techniques paired with preventive measures like threat intelligence tracking and incident response planning. When businesses hone these strategies into their operations, they are taking steps to ensure that their IT infrastructure remains safe from outside hazards while also maintaining customer trustworthiness at the same time.
Evolution and Importance of Ethical Hacking

When it comes to ethical hacking, we need to understand that this method of security has developed over time. It is now routinely employed by organizations all around the world as a way of protecting their networks and computer systems from malicious threats. To put it simply, ethical hacking can be described as an authorized attempt at accessing computers to search for potential weaknesses or vulnerabilities within them which could lead to sensitive information being accessed without permission.
In other words, these hackers are used by companies to find any risk – known or unknown – on their network so they can take measures against it before it’s too late!
Even though ethical hacking can assist organizations in diminishing security breach risks, it is important to understand that this practice can be abused. Therefore, if companies want to benefit from its advantages they need to strictly adhere to guidelines for appropriate behaviour. For instance, a business network would not fall into the category of ethical practices unless those affected were informed and gave their consent priorly – otherwise, such action may constitute unethical activity.
Furthermore, malicious activities carried out under the cover of ethical hacking should promptly be discouraged and reported as required by law. It is plain then that utilizing these techniques has become essential when it comes to modern-day cyber safety measures; given digital threats have grown increasingly intricate while at the same time becoming much more widespread than ever before!
Companies must therefore make sure they stay up-to-date with how precisely one carries out the proper application of ethical hack protocols to take due diligence when protecting sensitive data against any malevolent intentions or attacks on their networks. By understanding all elements included within prudently used ethics approaches firms will feel secure knowing everything was done possible to safeguard themselves accordingly.
Differences Between Ethical Hacking and Cyber Crime
Many people mix up the term ‘ethical hacking’ with cybercrime, yet, in reality, there are quite a few distinctions between them. Indeed, while certain parts of the processes may match to some degree, ethical hacking is just a controlled simulation of malicious digital behaviour that has been done to identify any possible security flaws and issues within an organisation’s systems; whereas cybercrime involves doing illegal things such as stealing from others or attacking other computers without permission.
In short: ethical hackers help protect networks by exposing weak points – criminals exploit those same weaknesses for their gain!
Ethical hackers adopt the same tools and techniques as traditional hackers to identify gaps in an organization’s IT infrastructure, however, they do this responsibly without causing harm to the system or its data. They are permitted by the business that hired them to conduct these activities unlike criminals who break into systems unlawfully – a criminal offence. Furthermore, ethical hackers help organisations by reporting back their discoveries and proposing ways of boosting security controls; whereas criminals misuse those very vulnerabilities for personal gain resulting in chaos and mayhem.
A further major contrast between ethical hacking and cybercrime is that while ethical hacking necessitates certain qualifications like Certified Ethical Hacker (CEH) certification; cyber thieves have no such requirements—they usually look for weaknesses within a framework using trial-and-error methods driven by their expertise. Additionally, if something goes wrong during an ethical hacker’s work then he or she takes on legal responsibility, but it does not come down hard on felons due to inadequate evidence against them – showing how useful proactive steps can be when protecting businesses from malicious actors’ actions!
Essential Skills for Ethical Hacking

It is a fact that ethical hacking is an extremely complicated process, entailing both technical and non-technical skills. It has nothing to do with learning how someone else’s network or system can be infiltrated; it also requires understanding the legal issues associated with your actions as well as using any knowledge obtained for the good of society at large.
Being able to comprehend essential topics such as basic computer networks, operating systems, programming languages, and coding standards are all necessary characteristics when participating in ethical hacking activities. But what other qualities does one need? How can we use our expertise ethically without infringing upon laws in each country that regulate online behavior?
Knowing how to use penetration testing tools, such as Nmap, Metasploit, and Kali Linux can help you uncover a system or network’s security vulnerabilities. This then allows you to develop solutions that will guard against data breaches – an invaluable skill in today’s digital world.
Furthermore, being able to analyze large sets of data and draw meaningful insights from them is imperative; it helps detect any potential attempts at unauthorized access on systems or networks too. Lastly, those keen on ethical hacking must have some understanding of computer forensics which involves gathering evidence for cybercrimes while adhering to a code of ethics set out by experts within the industry.
If you are interested in getting involved with this kind of work then be sure not only to acquire all the relevant skills but also remember that mastering this craft takes time!
How Ethical Hacking Contributes to CyberSecurity?
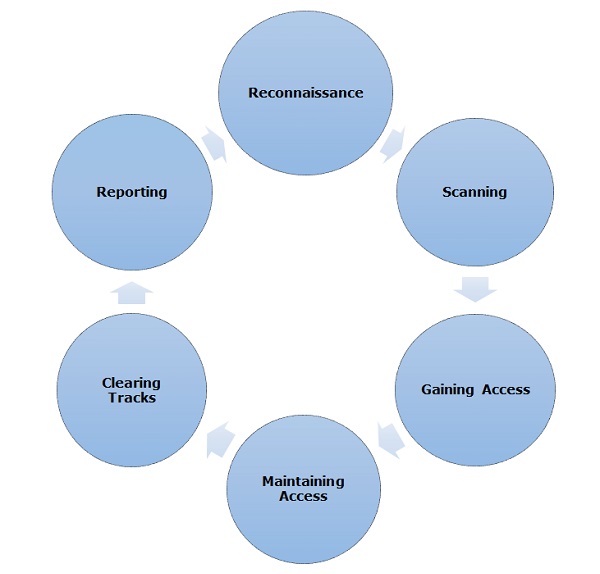
Ethical hacking is an awesome tech that has been used to bolster the cyber security of systems and networks. Ethical hackers – also known as penetration testers – are experts at locating weak spots in computer systems, they can be hired by firms to scrutinise their safety aspects. They apply the same techniques as malicious hackers but legally with permission. This way, any errors or vulnerabilities a hacker could use can be identified helping organizations improve their defense measures. Have you ever wondered how exactly ethical hacking works?
Ethical hacking aims to offer organizations an insight into how protected their network is against malicious attacks. Take, for instance, a situation where an ethical hacker attempts to access a server using numerous methods such as attempting passwords or exploiting individual weaknesses in hardware or software.
Once any gaps are discovered the organisation will be notified about them and suggestions on ways in which they can be improved upon will also be provided. It is like having somebody else conduct security checks on your system – so you know exactly what needs changing before another person finds out! Have you ever encountered cyber-security issues? How did it affect property safety?
Organizations are using defensive testing not only to prevent cyber crimes but also to follow the rules, such as with PCI-DSS (Payment Card Industry Data Security Standard). This standard places specific demands on all organizations that process credit card payments to protect customers from fraud or identity theft; ethical hacking allows them to see if they comply with these regulations. By employing ethics hackers when trying their defenses, companies can make sure they aren’t going out of their way and/or risking their clients by leaving any kind of space uncovered within security systems.
In recent years, it has become more and more important due to our lives moving further online – from bank details up to personal data kept safe at cloud servers. It is indispensable that businesses take some proactive actions toward ensuring networks against possible threats coming down from digital criminals. Hiring ethical hackers works like a charm here: it provides access to top professionals who understand how offenders function plus which steps should be taken best regarding protection – something most enterprises don’t have inside the company itself.
Role of Ethical Hacking in Secure Networking
When it comes to securing networks, ethical hacking is a vital part of making the system safer. Ethical hackers are especially qualified professionals who imitate harmful assaults to spot and patch any potential security vulnerabilities before they become misused by malicious attackers. What’s more, ethical hacking assists businesses to meet regulatory principles like SOX, PCI DSS etc which protect user data thus guaranteeing that their customers’ privacy isn’t endangered.
Generally speaking, ethical hacking involves utilizing several tools and techniques for infiltration testing to uncover any weak points or flaws in the network – anything from unauthorized access control weaknesses and database vulnerabilities right through to web server malware exploits might be identified and patched up this way!
Ethical hacking involves searching for security breaches and unauthorized access in systems, analyzing log files, and uncovering any data left by hackers. Once a weakness is found it must be sorted out straight away to stop further abuse. As well as this, ethical hackers will use techniques like phishing or malware distribution to evaluate an organization’s resistance against cyber-attacks.
If someone wants to do these tasks effectively they need a comprehensive understanding of various computer operating systems, pieces of hardware, and software programs.
A successful ethical hacker needs to have strong communication skills so that they can easily express themselves, both verbally and in writing for reporting purposes. Equally as important is an unwavering moral code; it’s essential that a professional understands the importance of conducting tests ethically by not causing any damage or destruction during the process. What would be the consequences if this type of testing was done carelessly? How could businesses and individuals benefit from regular security checks?
Ethical hacking offers numerous benefits – it helps companies spot potential risks early on, ensuring their network remains safe from intrusions or malicious activities that could lead to data theft or loss of confidential information. Furthermore, peace of mind comes with knowing your system has been regularly tested against these threats.
Ethical Hacking as a Defense Strategy Against Data Breach

As the world advances towards becoming more dependent on data and technology to store confidential information, it is sadly being exposed to potential threats. To negate such dangers businesses are beginning to implement ethical hacking as a form of defensive protection from any possible breaches in their system’s security. Ethical hacking or penetration testing entails assessing an organization’s IT infrastructure for weaknesses by running simulated attacks just like malicious hackers do – this way they can recognize, stop, and act against all kinds of digital challenges that may arise.
The goal of ethical hacking is not just about detecting existing vulnerabilities, but also to explore potential ways in which they can be exploited to prevent any harm from occurring should somebody attempt to take advantage of them. The main plus point of employing such tactics lies in its capacity to identify security flaws before anyone with malicious intent exploits it. By doing this one could drastically lower the odds that their system will be subject to a breach since most organizations aren’t even aware that these latent weak spots exist until circumstances force them into action.
Moreover, ethical hacking can offer organizations a glimpse into how their systems might be exposed and what would need to be safeguarded in the event of an attack – allowing them to take appropriate preventive measures. With this kind of understanding under your belt, you would have much more protection against cyber-attacks. In addition to spotting weaknesses within your system, ethical hacking can also evaluate different aspects such as internal rules and regulations, personnel training, and physical access control facilities. How well are these areas equipped? What extra precautions could one implement for better safety?
Having a comprehensive security strategy in place is key to protecting your vital information from getting into the wrong hands. Ethical hackers use specialized tools and techniques that can spot weak spots you might not even know about, giving them an invaluable edge when it comes to defending against cyber threats.
What ethical hacking gets down to is understanding how attackers operate and planning for any unexpected scenarios – ensuring that if a data breach does happen, your business won’t be caught out of its depth. If you haven’t already invested in this type of proactive defence tactic then now’s probably the time before it’s too late! Taking steps sooner rather than later could ultimately save both money and headaches further down the line.
Latest Tools and Techniques in Ethical Hacking
Ethical hacking is using computer and network security procedures to spot weaknesses. This method of testing looks for system vulnerabilities that could let malicious hackers attack or breach data. The approach involves mimicking an attack on a computer or network to find any safety gaps that a hacker might be able to use. The newest techniques and tools associated with ethical hacking are consistently changing as threats become more advanced. Cyber security pros utilize these measures to evaluate their systems, as well as those of their customers – helping them stay one step ahead of the game!
Penetration testing has become one of the most sought-after ways to uncover weaknesses in networks and applications. Using automated tools involves scanning through a target system for any vulnerabilities that could put it at risk – while also exploiting these flaws with malicious intent for potential abuse by hackers.
But there are other techniques employed too: cyber security pros may turn to social engineering tactics such as phishing or sending out spam emails which can be used to gain access to internal systems or get their hands on sensitive information. What’s more unsettling is that you never know what sort of data miscreants are after; personal details? Corporate secrets? It has vigilance like this why staying secure is becoming ever-more paramount in our digital world today.
Forensic tools are seeing a surge in use by ethical hackers to investigate any suspected attacks or recover data from damaged systems. These allow them to inspect log files, system configurations, and other material so they can figure out what happened beforehand, during the attack, and when it was all done. For instance, if there has been an invasion on a website or network then forensics might be used to discover who did it and how were they able to access the said area.
Awareness of cybercrime is becoming more commonplace among people these days; companies need sufficient measures that shield themselves across every aspect – physical equipment/devices along with networks, applications at their core, and data centers as well as cloud infrastructures. Implementing strong cybersecurity policies alongside routine checks may help spot potential threats quickly thus averting major harm – something which makes ethical hacking increasingly necessary for businesses than ever before.
Ethical Hacking as a Profession
Ethical hacking – or white-hat hacking, as it is sometimes termed – is a vitally important part of life in the digital era. Ethical hackers are experts who use their knowledge to identify and address any potential security issues with systems and networks. Companies hire them to hunt out possible vulnerabilities that could be leveraged against them; they then work with businesses or organizations to set about patching up those weak points before anyone else can take advantage.
In certain instances, corporations may even employ an ethical hacker on a retainer basis just so they have someone regularly checking for weaknesses in their system architecture. It begs the question: would your business feel safe if its network was not subject to regular audits by professional ethical hackers?
Put simply, ethical hacking is when hackers use their talents for good rather than evil. Instead of breaking into systems to steal data or cause mayhem, these professionals work on behalf of companies to uncover security vulnerabilities that could be taken advantage of by bad actors. In other words, they help organizations protect themselves from harm before it happens – and given the amount of cybercrime we are seeing today that’s never been more important.
Hackers are becoming increasingly clever in terms of what they can accomplish with malicious intent – like stealing documents and planting malware – so having an ethical hacker working proactively as part of your team has become a must-have for many businesses operating online right now. But what sets ‘ethical’ apart from regular old hacking?
To kick things off, ethical hackers are obliged by ethics and legislation not to cause any harm while performing their job roles. They don’t exploit any flaws or loopholes they come across; instead, they report them back to the company so that immediate measures can be taken to fix said issues. Plus, ethical hackers usually create in-depth reports listing all of the deficiencies detected with suggested solutions which would help avert prospective problems.
All in all, ethical hacking is an incredibly useful occupation that helps keep our digital lives secure from cyber criminals. When done bearing others’ privacy rights and security needs in mind this form of ‘hacking’ has demonstrated numerous times its worthiness when it comes down to defending us online – how impactful could such a role be?
Future Trends in Ethical Hacking and Cyber Security

Ethical hacking” is a term that has become increasingly popular in the world of cyber security. It involves testing computer systems and networks for vulnerabilities, to prevent or mitigate harm from any malicious attacks they may be exposed to. To stay ahead of these potential threats, ethical hackers must continually monitor emerging trends within their field – something which is proving particularly important as technology evolves at such a rapid rate!
One such trend gaining traction at present is ‘bug bounties’ – programs where organizations invite experienced (and often amateur) ethical hackers to offer up solutions when it comes to identifying bugs and flaws in existing systems or networks; this then allows them to develop better strategies for protecting against future attacks. What’s more, bug bounties can also provide financial rewards if an issue can successfully be resolved by exploiting its weaknesses!
Another key development being seen right now relates specifically to mobile devices: given our increased reliance on smartphones and tablets today, there needs to be a greater focus placed on hardening access control measures so as not only to protect sensitive information stored on those devices but also guard against attackers potentially taking advantage via remote exploits like Wi-Fi or Bluetooth connections, etc., thus leaving people open vulnerable data theft or worse still virus infections?
‘Ethical Hacking’ has recently gained huge popularity amongst cyber security professionals due to its ability to help safeguard digital resources from possible intrusions and malware infiltrations. This proactive technique helps identify system loopholes before criminals can exploit them thus offering a considerable protection layer whereas ever-evolving technologies bring about new challenges requiring vigilant efforts to ensure safety standards remain current and updated accordingly.
As part thereof, one new concept currently making waves is ‘Bug Bounties’ whereby companies request voluntary assistance from highly skilled individuals who find discrepancies related to coding/network issues – should fixable technical defects be discovered, a monetary incentive is tendered too!
Similarly needs to be extra attention regarding smartphone usage; advances made accessible storage capabilities make valuable targets for criminal activity coupled with exposure relationships through Wifi / Blue Tooth connectivity cause additional risk factors necessitating stronger authentication protocols used to offset risks associated with bad actors and safeguarding essential user details!!
Automation is becoming increasingly commonplace in the world of ethical hacking, allowing hackers to use automated tools to discover vulnerabilities within networks and systems more quickly. This can be hugely advantageous for organizations looking to secure their systems as it allows them to identify potential threats before they become a reality and reduce their attack surface area significantly.
On top of this, AI-based attacks are also increasing rapidly which means that cybersecurity professionals must keep up with the latest trends if they’re going to remain at least one step ahead of malicious actors. When it comes down to it, staying on your toes when it comes to artificial intelligence technology could well mean the difference between success and failure – not just for you but potentially for hundreds or even thousands more people too!
The Internet of Things (IoT) is becoming increasingly commonplace in our world today, which means hackers have more opportunities than ever to use vulnerable connected devices for malicious reasons. Cybersecurity professionals need to be aware of how these gadgets work and make sure they are safe from both a physical and digital point of view, to prevent any risks that might come up through the usage of IoT apparatus.
Cloud computing has revolutionized the way organizations keep their data stored; however, it also presents potential vulnerabilities needing attention by ethical hackers if they are looking to protect info against theft or loss. As cloud security involves various skills not required with traditional approaches due to its complicated structure, practitioners must ensure they are well-versed in cloud technologies when defending against threats posed by clouds. In conclusion, as technology progresses forward and cyber criminals become better at attacking computer systems or networks – a movement towards ethical hacking will continue developing accordingly!
Wrapping Up!
To sum up, ethical hacking is a fundamental element of any cyber security system and should be implemented as an integral line of defense against data breaches. It can guarantee organizations are well-equipped with the right tools to ward off malicious online threats effectively. By bringing in professional hackers, businesses have greater peace of mind knowing that they are sufficiently prepared for even the most sophisticated digital assaults. Plus, ethical hacking allows companies to remain one step ahead when it comes to cybersecurity concerns – now more than ever before!
Are you keen to become an expert in the field of cyber security? If so, we have got just what you are looking for! Our Master Program in Cyber Security will provide you with all the insight and skills necessary to protect digital systems from malicious hackers as well as create new strategies and methods for keeping important data safe.
You will be able to learn from experienced professionals who have worked at some of the biggest companies out there, making use of our top-notch facilities and resources. So why wait any longer? Enroll in our program today, and arm yourself with up-to-date knowledge suitable for a prosperous career in cyber security – ready your go make an impact within this fast-changing industry!
Are you ready to boost your cyber security career? Then what are you waiting for – enroll in our Cyber Security Master Programme right away! Our industry-leading course equips students with the latest curriculums, tools, and experts within the field. Upon graduating from us, those who have completed this program become highly coveted professionals amongst their peers.
By taking part in this program, you will gain all of the key skills necessary so that you stay up to date with ever-shifting threats present online today. You can also expect lessons on identifying breaches rapidly; defending against attacks efficiently and reacting quickly during an incident inside a business environment that is constantly changing shape at breakneck speed.
Also included will be practical training featuring malware analysis as well as digital forensics by qualified specialists – providing everything needed for professional success!
So don’t hesitate any longer: take advantage of this amazing opportunity straight away and let us aid your goals through the completion of our Cyber Security Master Programmes where thousands upon thousands of successful graduates already have been – making real differences not only across industries but around the world too!
Happy Learning!