What are the security risks of cloud computing? – everyone is looking for the answer to this question. Cloud computing is constantly progressing, and along with it comes the security threats associated. Data safety and cyber protection are some of these risks that companies must consider when using cloud services.
In this blog post, we will go over these issues in detail; examining how organisations can safeguard themselves from other potential dangers such as data breaches or information compromise. We will also take a look at solutions for reducing risk levels, so you can be sure your company’s details remain secure!
Defining Cloud Computing and Cloud Security

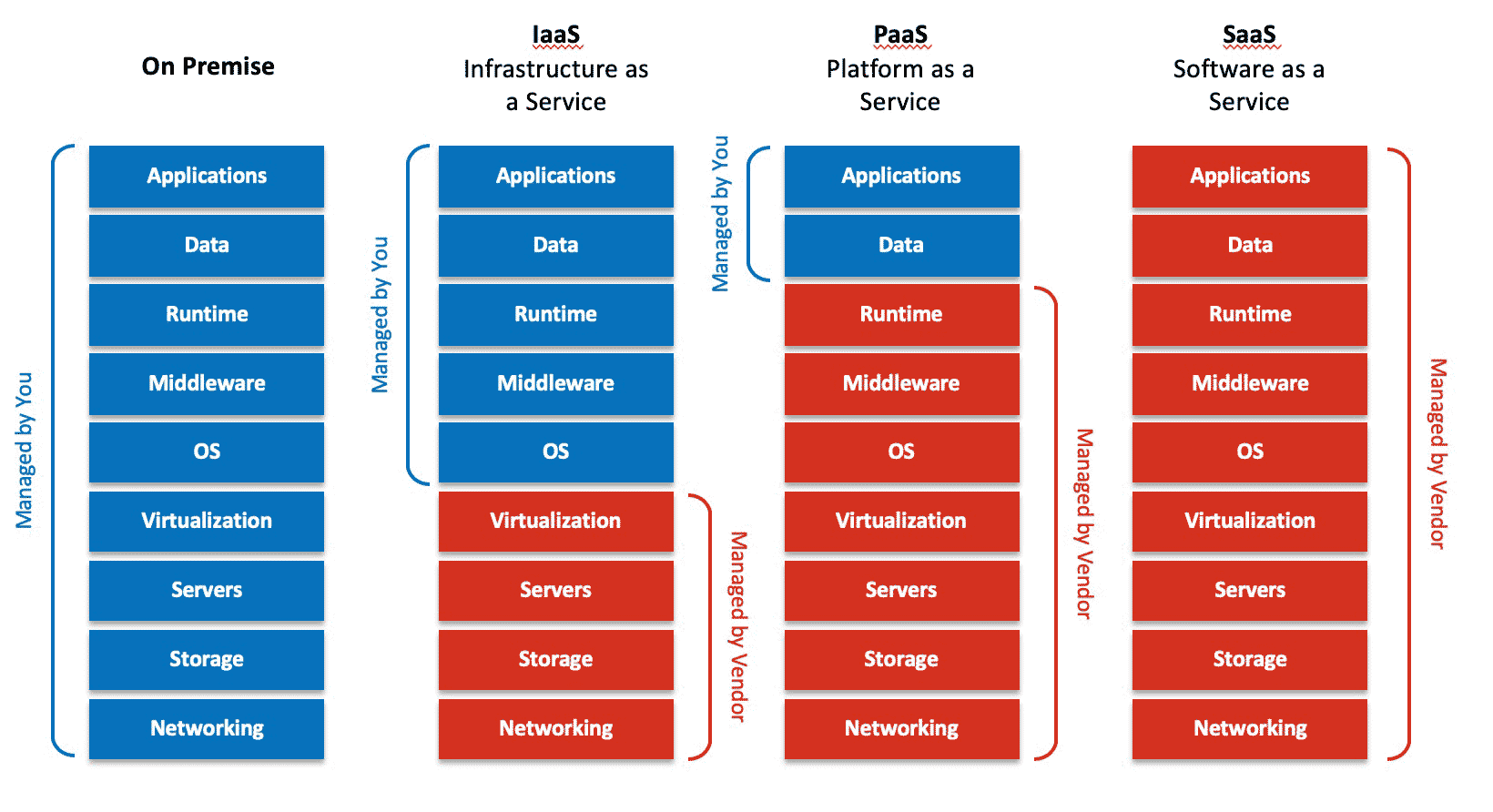
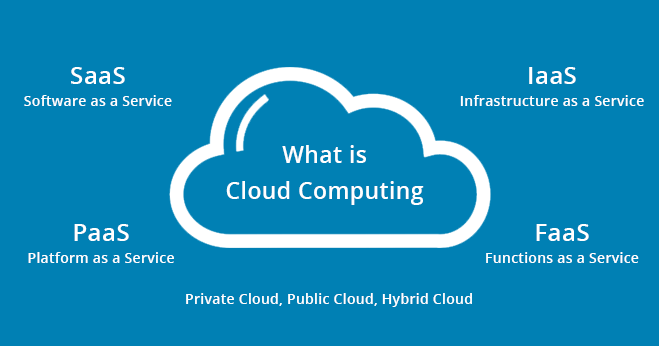
Cloud Computing is a relatively recent phrase that has been escalating in popularity over the past couple of years. It’s essentially described as utilising an array of distant servers hosted on the Internet to manage, store and process data, instead of depending on local servers or personal devices. The use of Cloud Computing technology offers companies plenty of advantages like scalability and cost effectiveness but there are also potential security risks associated with it which organisations need to be conscious of.
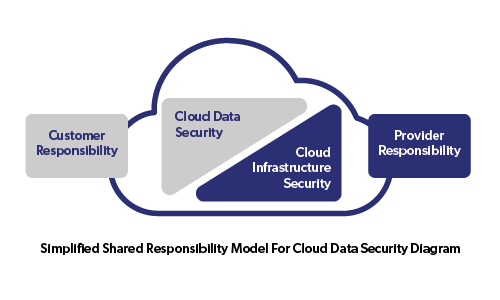
Cloud security concerns safeguarding and protecting your cloud-based services from any kind of malicious activity or unauthorised access. This can be done through encryption strategies, authentication protocols, multi-factor authentication solutions and a variety of other safety measures. It is important to keep an eye on cloud solutions for potential suspicious activity or any attempts made to gain access – originating internally within the organisation as well as externally.
Additionally, businesses must ensure that their data is being regularly backed up in case there’s ever an attack, so they can restore it swiftly afterwards without much effort wasted. How reliable is your business’s current cybersecurity system? Are you confident enough about it?
The most common threats faced by cloud users involve data theft, hacking attempts, account hijacking and distributed denial-of-service (DDoS) attacks. Any application stored on a network connected to the internet could be at risk of attack or exploitation if it doesn’t have appropriate protection in place. To keep these risks from being effective, fundamentally, all customers use strong passwords and two-factor authentication; firewalls also need considered along with intrusion prevention systems (IPS).
All around, using the cloud has dramatically transformed how businesses work – but this carries its dangers unless reliable security procedures are employed properly. To reduce such problems having robust regulations is essential as they specify who can access your information and what rights those people possess; furthermore, frequent inspections should take place to make sure everything stays secure all of the time. Knowing precisely what’s involved with keeping safe when utilising the cloud will aid organisations in protecting their infrastructure against any potential issues while still enjoying every advantage delivered by doing so.
Cloud Computing Adoption Statistics
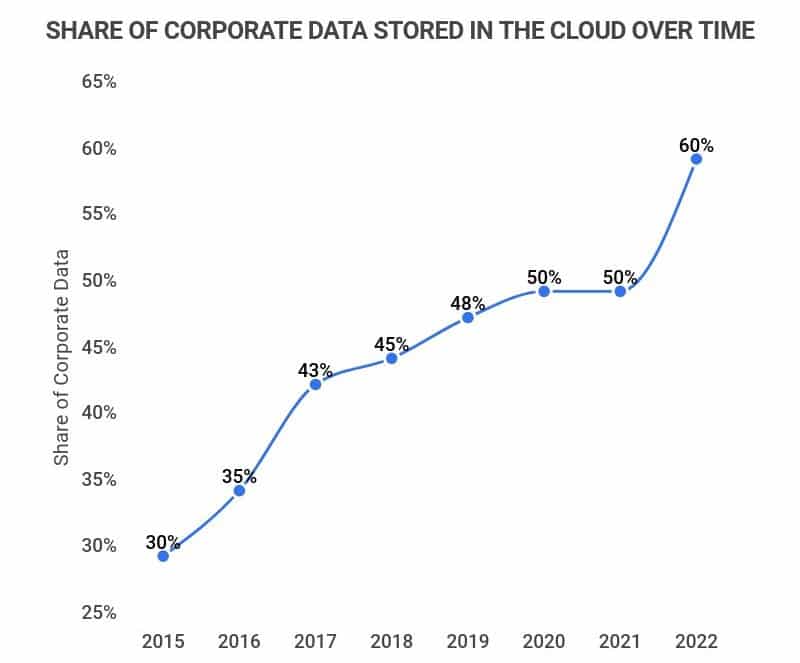
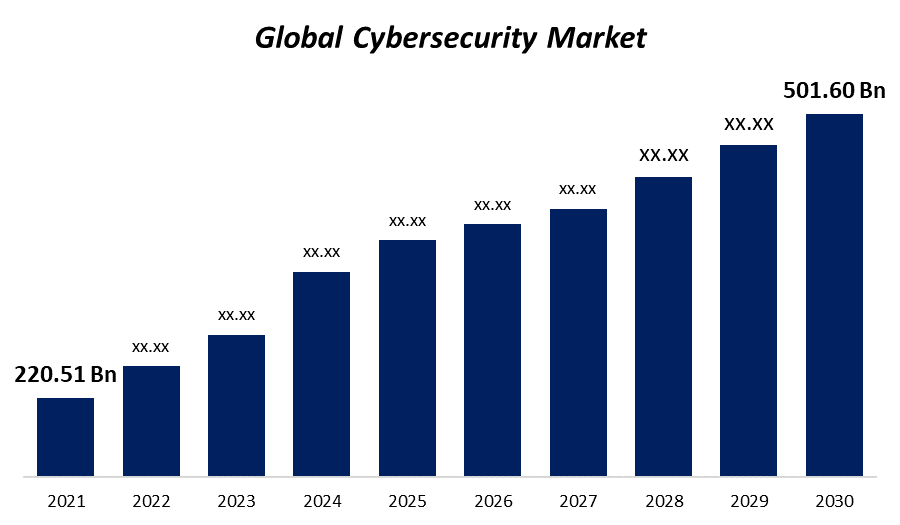
The introduction of cloud computing has revolutionised the way businesses can access computing power to store, process and manage data. Cloud computing adoption has become increasingly popular in the past decade; figures show that more than 50% of companies have adopted it. Though there are innumerable advantages brought by cloud computing, there are also security risks for companies to consider before taking on board this tech. A recent report from Gartner showed that public cloud services worldwide will be worth a whopping £214 billion come 2020 – so just how safe is our information?
It looks like cloud computing is here to stay. 2020 saw an impressive 18% increase in businesses using the technology compared to 2019 – and it’s easy to see why; speed, scalability and cost savings are just some of the advantages over traditional methods. But there are also potential problems that need addressing: security issues such as malware injection or denial-of-service attacks can be particularly damaging if left unchecked, while organisations must ensure compliance with relevant laws around data privacy too.
To protect their applications and info stored on a cloud platform, firms should think about working with third-party experts who specialise in cybersecurity measures for maximum protection against future threats. To further this cause they could provide staff training so everyone knows how best to use services securely – plus thoroughly analyse any risk factors associated with transitioning operations into cyberspace beforehand (to make sure it is worth doing!).
Delineating Security Risks of Cloud Computing
No doubt, cloud computing has transformed the way companies handle data but there are a few associated risks as well. Acknowledging and controlling these potential dangers has become an obligation for many businesses now. To protect yourself from any kind of unauthorised access or malicious attack, it is essential to understand what security hazards come with cloud technology. One major risk here is that organisations have less control over their information when stored in the cloud which puts them at greater threat of cyberattacks or maybe even human mistakes.
The dangers of trusting cloud computing are very real and can lead to major data loss or theft. This could be incredibly costly for a business’s reputation, as well as financially damaging. What’s more, having multiple users accessing the same resources via the cloud raises an increased risk of privilege escalation – if one user can exploit another user’s privileges then they can access sensitive info without permission; plus companies must ensure their services have correct support over time otherwise applications may fail leaving organisations open to further risks such outages and compliance issues.
But it doesn’t all have to be doom-and-gloom – with careful configurations on user permissions and investing in updated app versions businesses should successfully reduce any potential threats while protecting their data at the same time!
Exploring Cloud Security Risks
Investigating the safety challenges of cloud computing can be a daunting mission, with its continually changing and somewhat convoluted nature. Particularly, companies who utilize cloud computing services must take additional measures to guarantee that their information is secure. The most striking hazard regarding cloud security is the absence of command when an organization has finished its condition. At whatever point organizations decide on cloud stockpiling or applications, they depend on the third-party supplier to give a protected virtual domain.
However, by shifting to cloud solutions it can leave companies exposed to certain threats – like privilege elevation attacks for instance – that may not be so likely in an internal system. Plus, there is the possibility of malicious insiders getting access to data from within the cloud itself; either via unauthorised employees or even through dodgy software which might slip past admins unnoticed.
A tricky problem when looking at a secure-cloud situation is keeping tabs on user behaviour and making sure only authorised users have entry into specific systems or apps etc., If criminals gain access with compromised credentials then they could easily get hold of company resources without anyone realising or any security measures being alerted.
To battle this risk organisations should ensure passwords are kept safe as well as look into more sophisticated methods such as biometrics authentication and 2FA (two-factor authorisation) for extra precautions against criminal activity! Strict policies including monitoring/auditing accounts regularly will also help reduce potential risks arising from stolen logins being abused.
Delving into Cloud Risk Scenarios

As the popularity of cloud computing increases, organisations of all sizes are being drawn to its promises of increased agility and cost savings. However, companies must consider potential risks in comparison with these rewards before jumping headfirst into cloud risk scenarios. To ensure that businesses can be confident their data is secure, there are a few key points to take into account.
The initial stage in addressing cloud risk is recognising the most prominent threats.
Organizations need to be mindful when it comes to data security in the cloud. There are a range of cyber threats lurking out there, ranging from state-sponsored malicious actors looking for any opportunities they can get their hands on intellectual property, to criminal users trying to pinch personal or financial information with unlawful intent. If an organisation wants its systems and data kept secure in the cloud then knowing where your stuff is stored and who has access becomes critically important – not just because of potential breaches but also due to various laws and regulations which must be adhered to.
By having all these facts at hand you’ll have useful insights about what services best fit your safety requirements. As well as being aware, organisations should take proactive steps towards protecting their assets within cloud environments!
Having a good security posture requires both technical and administrative measures. On the technical side, firewalls, IDS/IPS systems, two-factor authentication mechanisms and encryption technologies are just some of the options to consider implementing throughout your network. In addition to that, there should be comprehensive policies in place for managing user identities as well as access controls and incident response processes.
It is also important that regular reviews take place – internally or externally – so you can verify if any changes have occurred compared with current threats (the dreaded ‘what’s new?’). Lastly don’t forget to have an incident response plan ready in case something goes wrong; this includes knowing where critical data is stored so it can be recovered quickly if needed!
Understanding Data Protection in Cloud Computing
When it comes to cloud computing, data protection is one of the biggest security concerns. There’s an enormous amount of data stored in the cloud and that needs to be kept secure; no one wants it hijacked or taken by unauthorised people! Understanding possible risks associated with this technology is a must for anyone planning on using it professionally – otherwise, you could find yourself at risk from malicious hacking. That’s pretty scary stuff right there!
Hackers have become ever more intelligent in their efforts to get access to worthy info held in the cloud, so organisations are having to take solid precautions against these risks. This involves putting effective security protocols such as multi-factor authentication and encryption algorithms into place alongside doing periodic scans of the system for possible weaknesses and responding quickly if they show up. Data hacks can happen due to either insider human errors or malicious activities from outside attackers, which makes it essential that companies set out suitable plans and approaches for protecting their network setup.
It’s crucial to keep a close eye on user access and make sure only permitted personnel can get their hands on sensitive data. Companies should also track who has accessed what data, when or from where by using different logging methods such as event logs or audit logs. A great way of defending against external threats that could lead to losing information is implementing strong encryption technologies like the AES 256-bit key – the kind of encryption so complex it renders any stolen material unreadable without authorised credentials.
On top of this, organisations may want to consider having more advanced security solutions in place like Intrusion Prevention Systems (IPS) which are capable of detecting anything fishy before there’s any real damage done. In conclusion, if you plan on utilising cloud computing services then bear all looming security risks in mind and become thoroughly familiar with best practices for protecting confidential info; otherwise, your business might suffer not just financially but legally too if an incident takes place due to negligence regarding safety precautions taken.
Highlighting Recent Security Breach Incidents

We all know that cloud computing is an incredibly convenient way of storing and accessing data, but it doesn’t come without some risk. It’s a well-known fact that companies are frequently subjected to cyber criminals who persistently look for loopholes in security protocols to get whatever they want – whether it be customer information or money.
Consequently, keeping track of recent instances where there has been a security breach comes in handy if you want to ensure your safety standards stay on point. Analyzing these situations offers valuable insights into how we can prevent similar occurrences from taking place again; which could save us immense amounts of stress (and potentially finances) down the line!
Come October 2019, Yahoo was hit by a data breach that affected nearly 500 million user accounts. The hackers gained access to personal information like passwords, telephone numbers and birth dates – all of which could be used for identity theft crimes. It wasn’t until 2016 when the company noticed something fishy going on with their network that they realised what had happened. Chilling stuff! What would you have done if it had been your account?
This case drives home the need for frequent scans to pick up any suspicious activity and keep customer data safe. What’s more, taking preventative measures like this could help you stay on top of potential attacks and avoid regulatory or consumer issues in future. Just take a look at what happened with Twitter last July – it was hit by an enormous security breach which allowed hackers to get into some high-profile accounts owned by people such as Bill Gates and Elon Musk. Regular scanning is key if you’re serious about keeping your customers’ information secure!
This recent security incident has highlighted the importance of companies being extra vigilant when protecting their confidential data. It seems that attackers were able to gain access by using social engineering techniques, such as manipulating certain employees into giving away login credentials for internal systems. Given this instance, it is paramount organizations ensure they have proper controls in place and that staff are cautious about any requests which require divulging sensitive information online – these can often lead to greater problems down the line if not monitored carefully.
Moreover, we have seen how scammers exploited famous accounts on Twitter to defraud people out of money via fake tweets stating rewards would come from depositing funds into cryptocurrency wallets – which never came true unfortunately! This emphasises why checking again before handing over crucial details is important; after all, nobody wants a nasty surprise further down the road, do they?
Counteracting Cloud Risks with Cyber Security
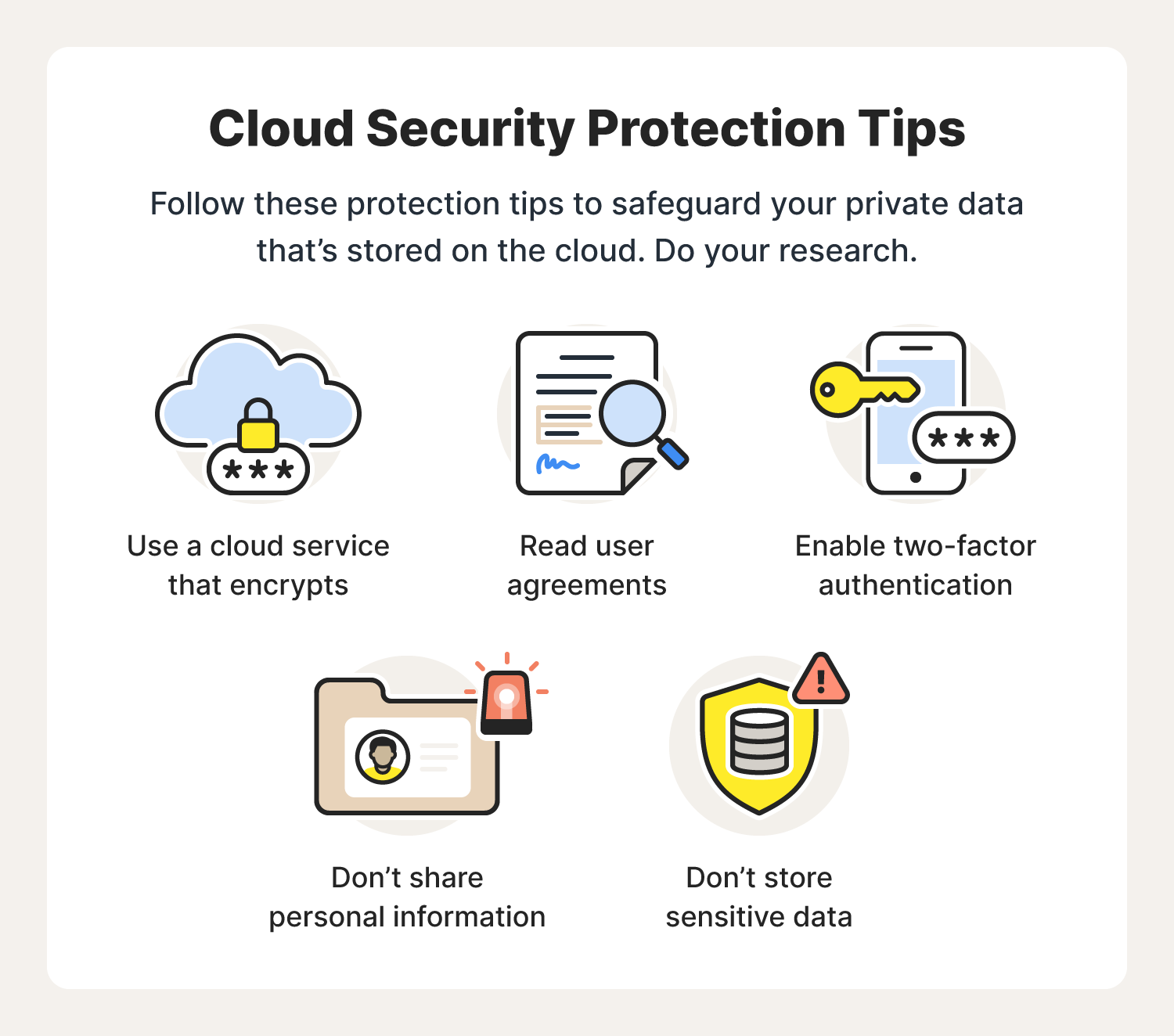
The use of cloud computing has been rising in prominence over time. It is a terrific way to free up the internal storage on your devices, share documents and information promptly and effortlessly, and always stay connected with co-workers across the world. Though cloud technology is truly handy, it can equally be open to cyber security risks which could damage your data or risk compromising the systems you employ.
As such, when planning out any cloud-based approach it is essential to take into account means for lightening these potential issues through counteracting them using measures related to cyber safety.
One of the biggest risks to data stored in the cloud is a breach by malicious hackers or some other third party accessing your info without permission. This hacker could get hold of sensitive material like financial information or personal contacts and use them for their nefarious ends, even blackmailing at times.
To safeguard yourself from this happening it is advisable that you set up two-factor authentication wherever possible and only ever grant access to those who require it. In addition, always putting strong passwords on things which are changed regularly will also help avoid any unauthorised entry taking place!
Another hazard connected with cloud computing is the possibility of accidental deletion of data due to human blunders or other technical challenges like system failures. To avoid this, there are several steps you can take such as routinely backing up your information onto an external hard drive or any other sort of external storage – ideally offsite so that in case something does occur, then you would have a duplicate copy of all vital records and files which could be restored from if necessary.
But what happens when it’s too late? How do we prepare ourselves for these situations before they even happen? What’s more, we should take regular backups and it would be wise to check them regularly too! That way you can make sure your data is up-to-date and working properly in case of an emergency. A further point when looking at minimising cloud risks arises over software updates – how do we best manage the bugs or security vulnerabilities that might be present?
The best practice to protect from hackers is to stay up-to-date with updates. The updates must be tested beforehand, however – both manually and automatically. This way you ensure everything runs smoothly once they’re applied, so no errors occur for users afterwards either! Manual testing allows us to check thoroughly but it takes longer than automated which can speed things along granted it may miss issues not considered before. Therefore, if anything unexpected happens we need a plan in case further investigation is needed down the line.
Best Practices for Cloud Security
Cloud security has become one of the biggest worries for anyone looking to transfer their businesses and operations online. Although cloud computing offers a bunch of advantages, incorporating scalability, straightforward access and cost savings, there are some built-in risks connected with it as well. Consequently, it is essential to implement best practices that will shield your data from cyber dangers. So, what are some of the top techniques for keeping your cloud secure?
Most significantly you should ensure you have an effective authentication system in place. But how would having strong credentials help minimise any potential threats? Well, verifying user identities before allowing them access into networks or systems can reduce fraud attempts caused by malicious attackers who may be seeking unauthorised entrance or information theft within organisations’ databases.
When it comes to protecting data stored on the cloud, encryption is something you absolutely must have. This means taking advantage of multifactor authentication – a login process which requires more than just a username and password. Two-factor authentication (which involves using something that you know like your password, as well as having possession of something like your phone) is widely accepted to be one of the most secure options available.
Without these extra steps in place, anyone with malicious intent could gain access to sensitive information or even take control over your entire system if they get hold of any single user’s account credentials – scary!
Protecting your data by encrypting it before sending it to the cloud adds an extra layer of security, making interception and viewing confidential information much harder. Backup encryption is also essential; if something goes wrong or you experience a crisis, sensitive info can still be accessed. Thirdly – and this one’s particularly important for anyone keeping customer or financial records in their cloud – regular monitoring must take place.
This way any suspicious activity involving unauthorised users will quickly become apparent. Furthermore, why not set up alerts that notify when unusual access attempts occur? That could provide some extra peace of mind around protecting valuable information stored on the system!
What’s more, all employees must be briefed on the basics of cyber security: how to detect phishing attempts and not pass around passwords. This way they can be aware of any potential security concerns and know what to do if something happens. Plus, make sure your hardware devices have up-to-date safety patches in place as this safeguards them against hackers or other people trying to access confidential data stored online.
By following these best practices (and also having good password management protocols) businesses will be able to guarantee their valuable information remains secure when using cloud technology even with the possible risks out there on the internet!
Future Trends in Cloud Security and Risks

Cloud computing is becoming more and more popular among businesses, but with the ease of storing information on the cloud comes a few risks that can not be neglected. Plans for securing this type of technology are being made to ensure data remains secure from any malicious activities. To comprehend what these trends will entail, it is pivotal to identify all potential hazards in advance.
What could arguably pose one of the greatest risks when it comes to using cloud services would be unauthorised access or stolen confidential data stored on its platform – an issue we must take seriously!
Storing data remotely on a server means it can be accessed by multiple users, increasing the risk of someone without permission getting into the system and stealing or manipulating data. To protect against this danger encryption technology is often used to scramble information before transmission – making it unreadable if an unauthorized person intercepts it.
Along with encryption, businesses should take further measures like two-factor authentication for secure access; firewalls and intrusion detection systems which help prevent breaches from occurring in the first place. But there’s another potential threat worth bearing in mind when using cloud computing – insider threats.
Insider threats can be a real problem, with employees who could abuse their access privileges or simply cause unintentional damage due to a lack of training on security measures put into place by businesses. To address this risk, companies need to implement user activity monitoring tools that monitor employee activities during work hours and create comprehensive policies outlining what is considered acceptable when it comes to working with sensitive info or talking to customers via different channels.
But exactly how much control should employers have over the actions of their staff? And are there any benefits in allowing for more open communication between customer service representatives and customers online? These questions remain unanswered as we come up against new challenges posed by cyberattacks within our ever-evolving digital landscape.
The outlook for cloud security looks encouraging as more and more solutions are becoming available that make data storage safer than ever. As technology progresses, fresh solutions like blockchain will carry on emerging with its aptitude to supply tamper-proof Audit Trails and heighten the reliability of transactions done over networks – aiding in lessening potential risks related to working in an open network such as the internet.
It is clear that Cloud Security is going to be a lasting priority for organisations which wish to run securely – thus instead of ‘just hoping’ your business stays secure – mull over-investing in some sturdy Cloud Security steps today! What could you do right now so you can feel safe about storing information online?
Wrapping Up!
In conclusion, it is become increasingly evident that cloud computing is a great option for many businesses. However, there are security risks associated with using the cloud; such as unauthorised access to data or theft and cyberattacks which can lead to serious breaches of security.
It is therefore essential that those who use the cloud take all necessary steps to protect their data from these threats – strong authentication measures, encryption of sensitive information stored in the cloud and robust cybersecurity implementations should be put into practice. By taking cautionary action like this we can ensure our virtual environment remains safe and secure without any additional worries!
Are you looking to progress your career in cybersecurity? If so, what are you waiting for – enrol on our Cybersecurity Master Program now! Our pioneering program gives a holistic approach to security and is structured to provide you with the knowledge and proficiency required of an industry-leading expert.
You will get an extensive understanding of current issues and threats, as well as instruction in cutting-edge systems. In addition to this, we will help hone your problem-solving skills – fundamental if you want success within the sector. Upon completing the course, receive your Master Certificate that demonstrates your adeptness in cybersecurity; go ahead and take charge of tomorrow’s career prospects today by signing up for our Cybersecurity Master Program!
Sign up right away for our Cybersecurity Master Program to get ahead of the digital world! We’ve got state-of-the-art courses ready for you that will provide essential security knowledge and technologies needed to fend off malicious attacks. Get a thorough understanding of ethical hacking, computer networks, as well as effective secure coding methods.
Our certified trainers guarantee your skills are sharp enough so you can stay one step in front of cyberattacks which continuously emerge in today’s swiftly changing virtual environment. Read more about how we can lend a helping hand with securely guarding critical information assets and preventing data breaches. Come join us now – enrol on our Cybersecurity Master Programme this instant!
Happy Learning!