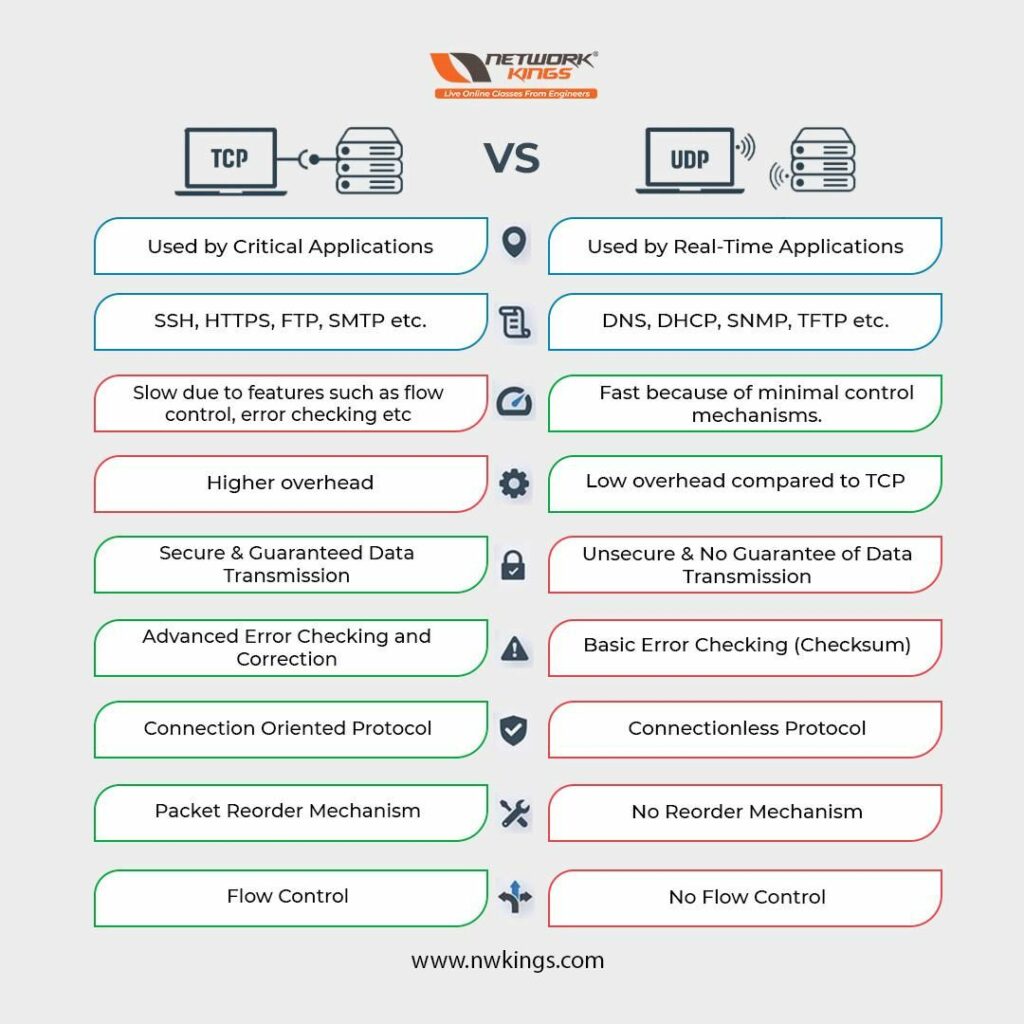
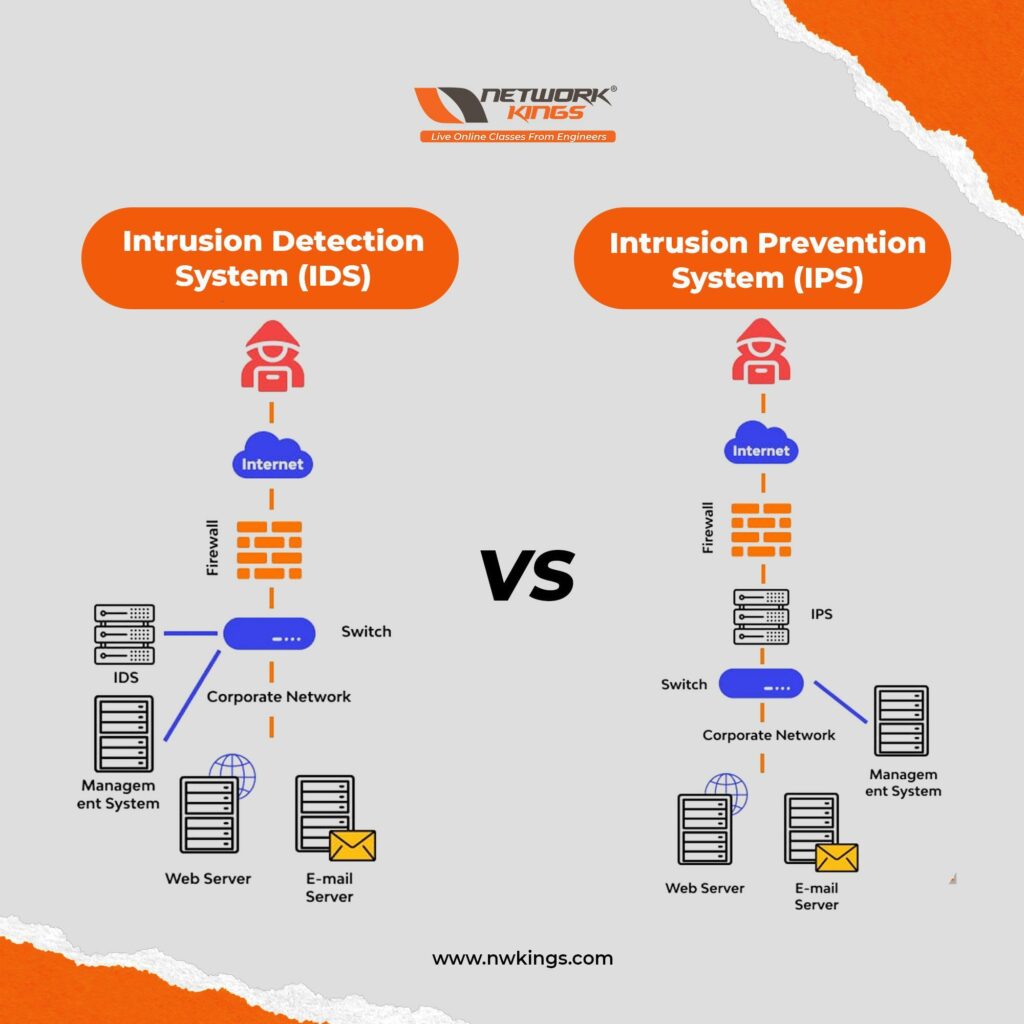
We can not imagine our lives without Networking. Networking is the near future, we all know. To enhance networking, we need new networking technologies. We all know the importance of networking technology in modern society as the tech era is increasing. We need high networking technology to handle advancement in networking technology. Hence, the future of Networking Technology is far beyond our imagination.
This blog will help you learn about The Future of Networking Technology!
What is Network Technology?
Network Technology refers to the technologies that send and receive data between two or more computers with or without the Internet. It contains routers, switches, cables, wireless access points, and hubs.
Network Technology helps in file transferring, media content sharing, email sending, VoIP Telephony, online gaming, communication services, and remote access to applications and systems. There are various types of Network Technologies. Let us explore them.
What are the types of Network Technology?
To transfer Networks, we have various network technologies:
- Wired and Wireless: Wired connections are known for stability, and high-speed capabilities and are considered the backbone of the stationery applications. It is used in corporate offices where mobility is not needed. Wireless connections are known for flexibility and mobility. They are mainly for smartphones, tablets, laptops, etc. It has made our work far more easier than earlier.
- Networking by Transmission method: Transmission of networks can be done by two methods- point to point that generates a direct connection between two endpoints. It helps to generate direct links to nearby places like 2 buildings. The second one is the multi-point network that enhances multiple connections over a single network.
- Networking by Scale: Networking by scale includes LAN [Local Area Network, MAN [Metropolitian Area Network], PAN [Personal Area Network], VPN [Virtual Private Network], and SDN [Software-defined Network].
What is the Evolution of Networking Technology?
Do you know the concept of Packet-switching wide area networks was
imagined before local area networks, and in 1965 national packet-switched network was proposed by Donald Davies in the UK for Britain. In 1966 Bob Taylor secured funding for ARPANET, the first network to use TCP/IP, set by Robert Kahn and Vint Cerf.
As of now, we have transformed into a modern Network technology with the help of SDN [Software-defined Network].
The transition from traditional networking to modern networking technologies like SDN has occurred as it allows management of the network from a central location, it can manage network configuration easily, is capable of using a northbound interface that communicates with APIs helps developers in network programming, etc.
SDN has helped to move from traditional to modern networking.
What are the Current Trends in Networking Technology?
Here are the current trends in the Networking Technology:
- Software-Defined Networking (SDN): SDN is a network architecture that utilizes software to control networks, which allows IT administrators to configure networks using a software application. SDN operates a centralized controller to handle switches and routers, isolating network control from data processing. This improves network flexibility and efficiency, optimizing infrastructure device configuration for enhanced versions.
- Network Function Virtualization (NFV): By positioning virtualized network functions at the network edge, closer to end-users, delays in data transmission are reduced. This trend not only improves the general user experience but also unlocks doors for creative applications such as AR, autonomous vehicles, and real-time analytics.
- Cloud Networking: Cloud networking presents high speed, automatic software integration, unlimited storage, speedy deployment, mobility, cooperation, cost deduction, and data backup/restoration abilities. These characteristics improve productivity, scalability, and flexibility while lessening costs and providing data security.
- Internet of Things (IoT) and Networking: The IoT is a network of physical objects that use detectors, software, and other technologies to swap data with other devices and systems over the Internet. IoT is a review of current trends, with a firm focus on cloud computing and the blending of sensors and actuators with the environment. IoT is used in many industries, including healthcare, security, and AI, and is most typically associated with “smart home” products.
- Edge Computing and Edge Networking: Edge computing concentrates on fetching computation and data storage to the devices at the network edge as close to the data source as practicable. Edge networking is a dispersed computing paradigm that drives data storage and computation nearer to the point of need, away from centralized data centers.
What are the Emerging Technologies Shaping the Future of Networking?
Here are the emerging technologies shaping the future of networking:
- 5G Networks: 5G technology is the most delinquent generation of mobile communication networks, providing faster speeds and enhanced dependability compared to earlier generations. It can revolutionize the way we live, work, and play, by encouraging new and creative applications that were once not possible.
- Artificial Intelligence (AI) and Machine Learning (ML) in Networking: Using AI and ML, network analytics tailors the network baseline for warnings, diminishing noise and wrong positives while allowing IT teams to accurately pinpoint problems, trends, irregularities, and root causes.
- Quantum Networking: Quantum networks hold the possibility for more rapid and secure communication. However true quantum networks are practical and need more engineering and scientific research. Quantum networking links systems and shares data among them using quantum phenomena.
- Blockchain Technology and Networking: Blockchain technology is an evolved database mechanism that permits transparent information transfer within a business network. A blockchain database keeps data in blocks that are connected in a chain.
- Augmented Reality (AR) and Virtual Reality (VR) Networking: Augmented Reality (AR) and Virtual Reality (VR) have appeared as transformative technologies, reshaping how individuals interact with digital content and the physical world. As these immersive technologies gain momentum, their impact on network infrastructure becomes a critical consideration.
Future of Networking Jobs: Trends and Predictions
With the rise of technology, Network Engineers are in high demand. Network engineers play a vital role in creating and supporting the infrastructure that supports the connected world operating smoothly.
This generation needs more than 6 Lacs engineers but at present, we only have 65k. It clearly describes the need and demand for Network Engineers in this epoch.
To manage complicated systems, we need the help of Network Engineers. Also, emerging technologies like 5G, IoT, cloud computing, etc.
Jobs: There are various jobs in the Networking field including
- Support Engineer
- Desktop Support Engineer
- Jr. Network Engineer
- Sr. Network Engineer
- L2 and L3 Network Engineer
- F5 Load Balancer- Network Engineer
- Network Engineer (Routing & Switching) L1 / L2 support
- Lead Network Engineer
- Lab Engineer
- System Administrator
Salary: Here is the list of salary expectations in different countries:
- United States: $84,472 per year
- Canada: CAD 84,439 per year
- United Kingdom: £25,500 per year
- Germany: €57000 per year
- France: €75,700 per year
- Switzerland: CHF 1,20,000 per year
- Australia: AUD 110,000 per year
- New Zealand: NZD 90,000 per year
- Japan: ¥300,000 per year
- Singapore: SGD 49,585 per year
- India: INR 5,00,000 per year
- China: CNY 345,000 per year
- Brazil: BRL 96,000 per year
- South Africa: ZAR 540,000 per year
- United Arab Emirates: AED 343,195 per year
Recognition: Recognition with relevant skills is crucial to set your future in networking technology. This recognition will help you get better opportunities and career enhancement.
What are the top Networking Courses in IT?
Where to pursue IT Networking Courses?
You can pursue an IT Networking course from Network Kings where you will learn from industry experts who possess experience in the IT Networking field of around 15+ years. Here are the benefits of learning from Network Kings:
- Network Kings does not hire local teachers/ trainers to provide you with the best training instead we hire industry experts who possess industry experience of more than 15 years in their field.
- Network Kings delivers online training so that you can access it from anywhere.
- Network Kings has a free Live demo class for your better understanding.
- Top technical courses for beginners at Network Kings are available in Hindi and English.
- The Linux program span is approximately 30+ hours.
- With Network Kings, get credentials to real labs with live doubt-clearance sessions.
- Batches have evening classes. So you don’t have to consume your office time in classes.
Conclusion
Being up to date with tech lets you see and involved in jobs faster than ever.
Remaining current with technology can keep your skills from evolving stale. Maintaining your tech skills fresh and up-to-date can help you succeed in your career.
Scalability is set to be a primary focus of networking in the not-too-distant future. As organizations keep on adopting and making new advancements like cloud computing, they’ll need network architectures that can grow with them as their needs range and develop.