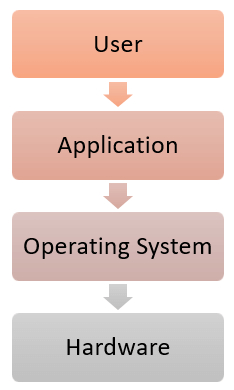
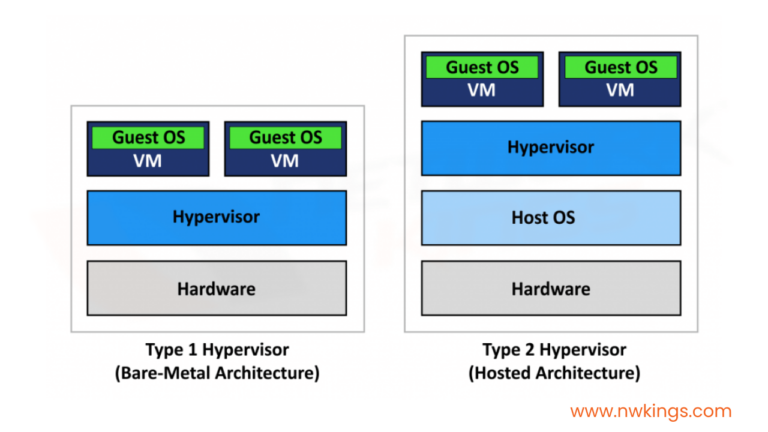
Cisco is the world’s number one provider of IT services, systems and products in the domain of computer networking. Right from its establishment in 1984, Cisco has been the pioneer of core networking technologies.
Today, most business organizations and companies use Cisco equipment, especially the big tech companies. That is why a lot of companies are looking for Network Engineers proficient with Cisco technologies. Being a Network Engineer at Cisco is indeed a dream job for many.
Cisco offers the broadest range of hardware products that function to form information networks or give people access to those networks. The best part about Cisco is that it does not follow a hard and fast rule to use only one technology. Cisco always listens to its customers and monitors all technological options. It also provides a wide range of options to choose from to its clients.
Therefore, it is evident that Cisco develops its products and services on the basis of accepted industry standards.
Cisco Interview Rounds:
If you are looking into getting a job at Cisco, you need to clear three interview rounds. These rounds are:
- Online Assessment Test:
The online assessment test consists of two tests: the aptitude test and the technical test. The aptitude test consists of questions such as probability, algebra, simple and compound interest, number series, profit and loss, etc.
The technical test consists of questions based on computer networking, C, algorithms, DSA and Microprocessor, etc.
- Technical Interview Rounds:
The technical interview rounds consist of asking questions based on computer fundamentals such as networking, Operating Systems, algorithms, Database Management, Data structures, etc. You need to have an in-depth knowledge of concepts to pass this round.
Pro tip: along with your resume, it is best to have your projects showcased. It will help you stand out from the crowd.
Now, we are going to discuss Cisco technical questions. These questions will be both for the freshers as well as experienced candidates. Let’s begin with it without any further ado!
Cisco Interview Questions: For Freshers and Experienced Candidates
Questions for Freshers:
1. What is a link?
A link is a logical or physical component of a network that interconnects devices or nodes. It is a communication channel used for data transmission. For example, when you join two ends of a chain together with a lock, it makes a link.
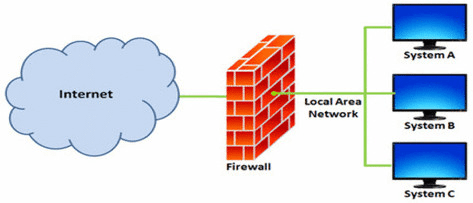
2. What is a firewall?
A firewall is a filtering unit of a device. It filters the incoming and outgoing traffic based on an organization’s previously built security policies. In other words, the firewall is a network security device that monitors and filters the traffic.
A firewall is a barrier that is present between a private internal network and the public Internet.
3. What is a node?
A node is a computer network defined as the connection point among network devices like routers, switches, printers, etc. that can receive and send data through a network.
4. What are the types of network nodes?
The following are the different types of network nodes on the basis of their application and function in a distributed network:
- Internet Network Nodes:
- The physical network nodes are the host computers in Internet networks.
- These nodes are represented by their unique IP addresses.
- WAN access points do not have an IP address.
- Data Communication Nodes:
- Data communication devices include physical nodes or communication devices such as switches, routers, bridges, hubs, modems and many more.
- These nodes are present between data communication circuits and Data Terminal NodeS (DTE).
- The most important role of such devices is to carry out the signal conversion, coding and line clocks.
- DTE includes devices such as host computers, digital telephones, printers and servers.
- Telecommunications:
- The use of telephone nodes in a computer provides intelligent network services.
- They help in exchanging information.
- Nodes in cellular networks have base station controllers.
- These controllers function to control multiple base stations.
- LANs and WANs:
- LANs and WANs include physical nodes or devices.
- They include a unique MAC address for Network Interface Card (NIC).
- These network devices are computers, wireless LAN access points, modems, etc.
- Distributed Nodes:
- These are the nodes involved in a distributed environment.
- There are two types of distributed nodes: physical nodes and virtual nodes.
- They are used to maintain transparency within the network.
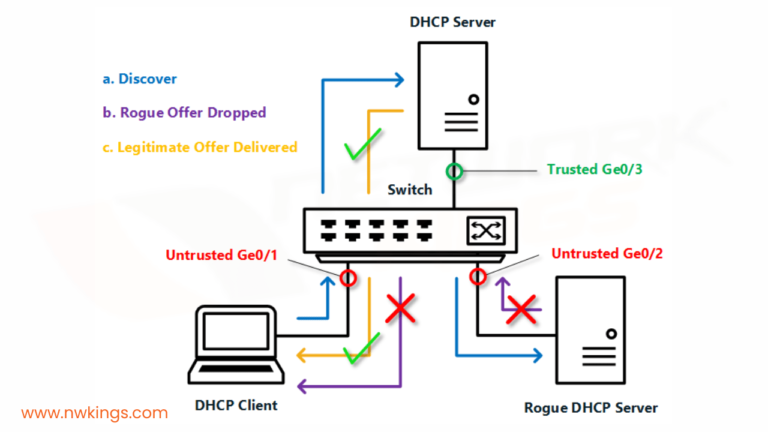
5. What is the default TCP session timeout for Cisco?
The default TCP session timeout for Cisco is one minute. The connection slots are closed for an average of one minute once the sequence of normal connection close gets completed. However, it can be configured into other settings according to the needs.
6. What is a gateway?
A gateway is a node of a network. In other words, it is a computer that sits between different networks or applications. It can be used as an entrance into some other network. It is a piece of hardware. It is important to remember that it is not the same as a default gateway.
The gateway converts information, data, or other communications from one protocol or format to another.
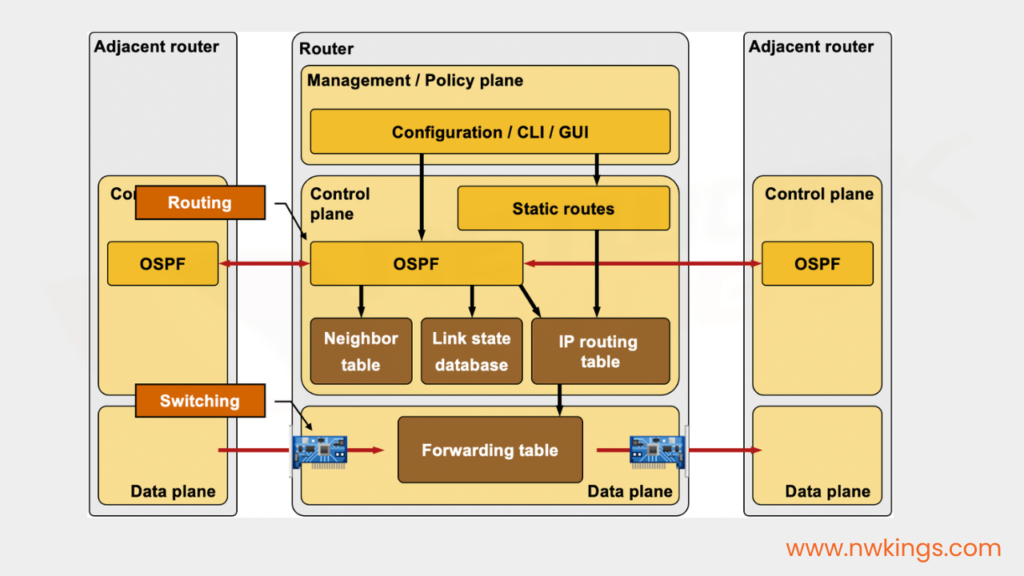
7. What is routing?
- Routing is the process of building routes that data packets carry to a particular location.
- Router performs routing. The router is a device that is used to select a path for traffic in a network, or between or across multiple networks.
- The network topology depends on a setup of hardware, to effectively transmit data.
8. What are the various types of memories in a Cisco router?
The different types of memories in a Cisco router are as follows:
- NVRAM for storing the startup configuration file.
- DRAM for storing the executed configuration file.
- Flash memory for storing Cisco iOS.
Questions for Experienced:
9. How is a TCP connection established?
A TCP connection is established by following the steps given below:
Step no. 1:
The host or the receiver sends a packet with an SYN flag to the sender (server). The server then responds with an SYN flag and ACK (ACKnowledge) flag in order to accept the connection.
The receiver then sends an ACK flag and confirms the relationship. The OS at both ends is told about the newly established connection.
Step no. 2:
The sender then initiates data transmission and gets acknowledgments from the receiver. A timer starts as the sender begins sending data.
Step 3:
The sender transmits the data again even if it has not received any acknowledgments after the timer limit exceeds.
Step 4:
When the receiver buffer is full in case of windowing, the receiver stops the signal to the sender. This stops the data transmission.
Step 5:
After the completion of data processing, the receiver sends the go signal to the sender. This starts the transmission of data again.
10. What is cut-through LAN switching?
Cut-through LAN switching which is also known as cut-through forwarding is a method for packet switching systems. It is done when the router receives a data frame and then sends it out again immediately. It reads the destination address and forwards it to the following network.
How does it works?
The cut-through switching reduces latency inside the switch. Even if the frame is corrupted, the cut-through switch still forwards the bad frame. The destination then checks the frame’s CRC and dumps it. This then forces the switch to resend the frame.
11. What is the access-list range for extended IP, extended XNS, and extended VINES?
The access-list range for Cisco devices is as follows:
- The extended IP access list range is 100-199 and 2000-2699.
- Extended XNS access-list range is 500-599.
- The extended VINES access-list range is 101-200.
12. What is a transparent firewall?
- A transparent layer acts as a line of layer between two devices. It is also known as a bridge firewall.
- It is a Layer 2 application that is installed easily into an existing network without making any changes to the Internet Protocol (IP) address.
- The transparent firewall acts as a bridge by checking and moving network frames between interfaces.
- Transparent firewalls also let in layer 3 traffic from higher security levels to lower security levels without the need of access lists.
13. What is an IP address?
- All the devices connected to the Internet has a unique number assigned to it. This number assigned to that device is called the IP address.
- You will not be able to communicate with other users, computers and devices on the Internet without the presence of this unique number on your machine (device).
- For example, IP address is like a telephone number. Each number is unique and identifies a way to reach you.
14. What is context switching and how is it activated?
Context switching stores the context or state of a process for reloading and applying it after starting from the same point as before. This feature is used for multi-tasking Operating Systems that allow multiple functions to share a single CPU.
The three major triggers are:
- Multitasking
- Interrupt Handling
- User and Kernel Mode Switching
15. What are the various layers of the OSI Model?
The OSI model has the following seven layers:
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
16. What is recovery testing?
A software testing technique such as recovery testing tells you how well the software can recover from failures such as hardware/software crashes, network failures, etc. It often involves forces loss of software in several ways to verify whether the recovery is performed correctly or not.
17. Which command enables failover in an ASA firewall?
The command that enables failover in an ASA firewall is the ‘Failover’ command.
18. What is the security level in an ASA firewall?
ASA Firewall Security Level can range anywhere between 0 to 100. The highest value od the security level on an ASA firewall is 100. It represents the most-trusted zone.
On the other hands, the lowest security level in an ASA firewall is 0.
19. Which LAN switching method is used in Cisco Catalyst 5000?
The Cisco Catalyst 5000 uses the store-and-forward switching method. The entire frame gets stored into buffers and a CRC check is carried out before deciding whether the data frame should be forwarded or not.
20. How to use a linked list to activate 3 TCP/IP packets?
All the packets should have a source IP, a destination IP, and some data (of at least 20 characters) in order to use a linked list to activate 3 TCP/IP packets.
The following steps need to be followed to activate the 3 TCP/IP packets. These are:
- Step 1:
You need to search the packets one by one for suspicious IP (that starts with 000).
- Step 2:
You will then check the data for the cipher, subtract 1 from ASCII of the first 8 to check if “JOHN JAY” is the data.
- Step 3:
Your program should ideally activate processing six packets in 2 groups of 3.
- Step 4:
Then you have to check all 3 packets (or nodes) and change the IP and data in each one. Then check again. Instead of a linked list, a QUEUE can be used. The QUEUE must contain the same data.
HR round basic Cisco Interview Questions:
The following are the questions that are the most frequent-asked interview questions in the Cisco interviews. These questions are asked in the HR rounds of Cisco interviews:
- Why do you think that you’re fit for this particular role?
- What are your strengths and weaknesses?
- What has been the greatest networking challenge in your career so far?
- Why do you want to join this position at Cisco?
- Why are you quitting your current job?
- Where do you see yourself in the upcoming ten years?
- What is your strategy for prioritizing tasks?
- Why do you want to join this company?
Conclusion:
We understand that getting a job as a Network Engineer at Cisco is not an easy job. That’s why we have handpicked questions for you. It will help you to go over the major concepts quickly.
To help you in the best way, we have collected questions for both freshers and experienced candidates. At last, we have added the most popular asked questions for the HR interview round. We hope this helps you.
Happy interviewing!