In this blog, we will discuss DHCP snooping in detail. Sometimes, users can acquire illegal IP addresses. This is where the DHCP snooping can come into play which prevents a user from acquiring a fake IP address coming from an untrustworthy DHCP server.
In other words, we can say that the DHCP server is a security feature available on Cisco switches that helps to protect against attacks that take advantage of DHCP. This is a part of CCNA course syllabus ‘configure layer 2 security features’.
We will cover what is DHCP snooping, how it works, the common attacks prevented by DHCP snooping, and DHCP snooping configuration. Let us begin covering all these topics one by one in detail.
In the previous blog of our CCNA 200-301 series , we talked about the Port Security in networking. I recommend you go through it before you jump to this blog.
Stick till the end to grasp all these important concepts!
What is DHCP Snooping?
Let’s now go over the basics of DHCP snooping.
DHCP snooping is a security feature of switches that are used to filter DHCP messages received on untrusted ports. You must note that the DHCP snooping only filters DHCP messages. Any other non-DHCP message is not affected.
The following are the key features of DHCP snooping:
- All ports are untrusted by default. It is up to you to configure which ports will be trusted.
- By default, uplink ports are configured as trusted ports whereas downlink ports are untrusted ports. The latter remains untrusted as any malicious user can initiate a DHCP-based attack from one of their devices in a network connected via a DHCP server.
For example, if there is an end host in a network that wants an IP address, it will use a DHCP server or relay agent to receive an IP address. Since the downlink ports on the switches (pointing toward the end hosts) are untrusted, a network administrator must configure the uplink ports (trusted ports).
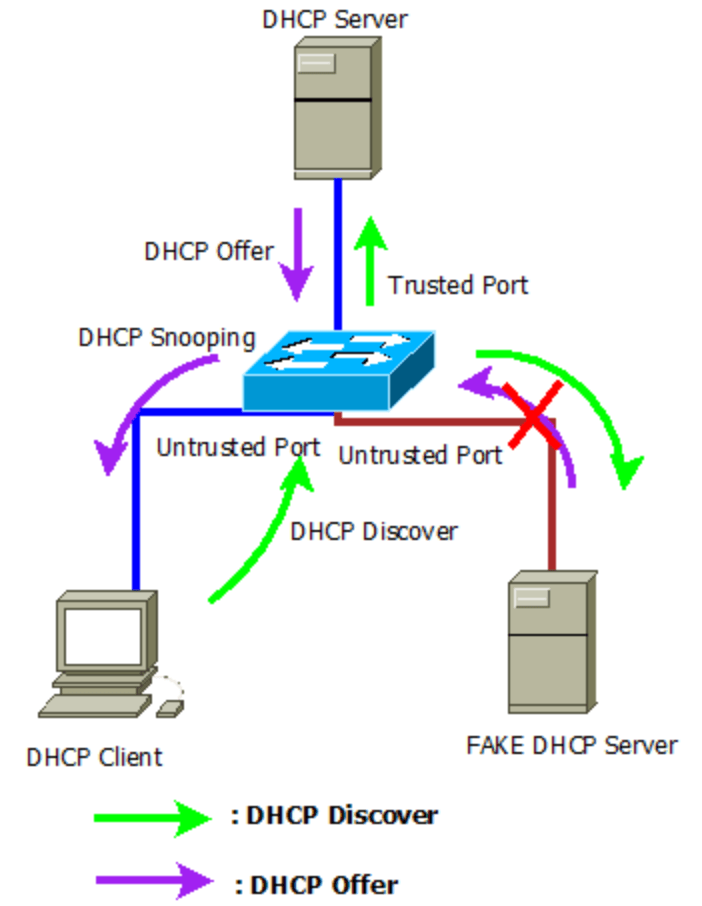
- DHCP snooping won’t inspect any messages on trusted ports. The switch will forward them as normal. The ports that point away from the end hosts toward the network infrastructure are uplink hosts.
- The DHCP server then replies to the DHCP message sent by the user and sends it back to the user through uplink ports.
How Does DHCP Snooping Work?
In order to understand how DHCP snooping works, it is very important for you to understand how a DHCP server works in the first place.
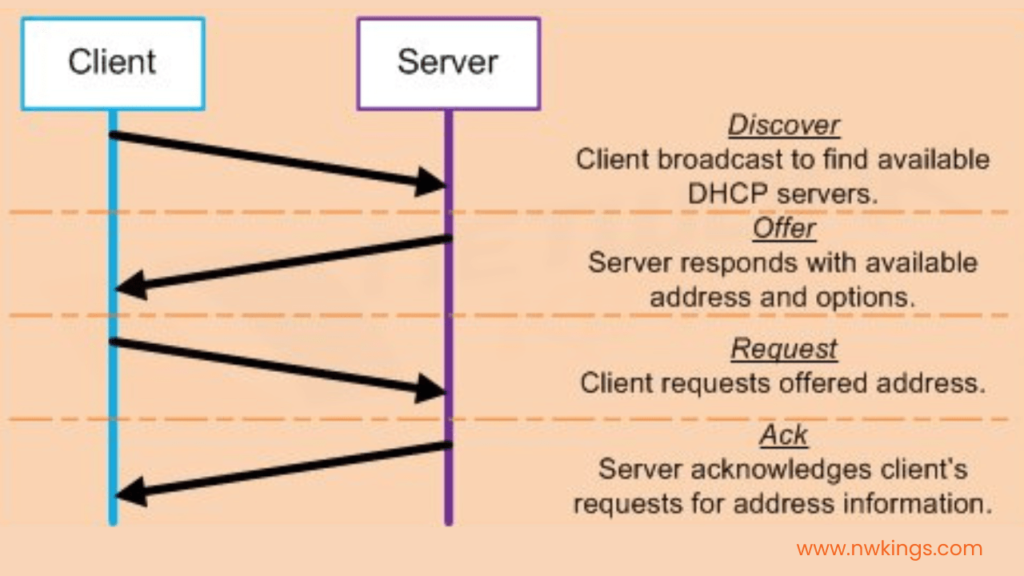
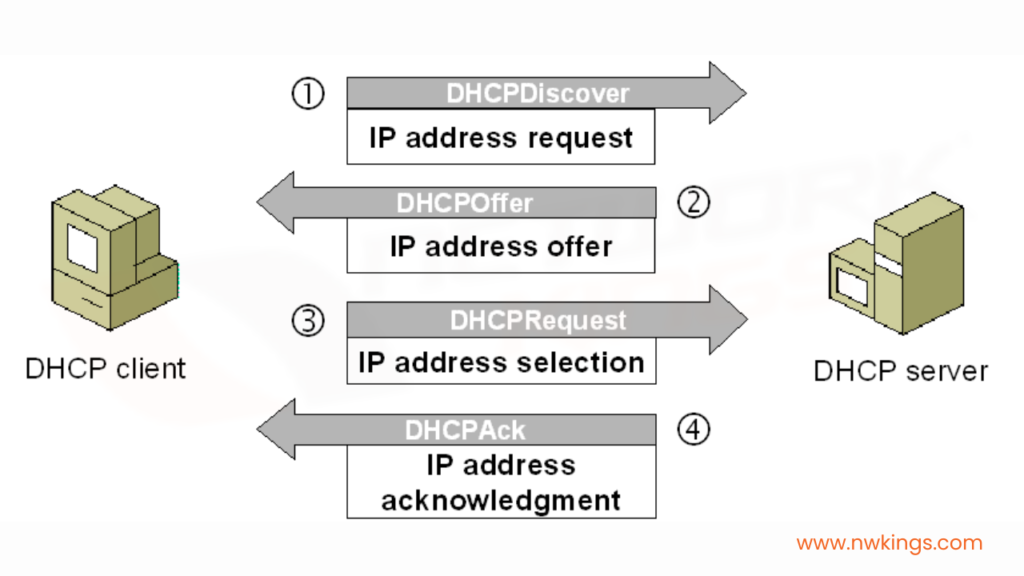
When the DHCP is enabled, a network device without any IP address assigned will approach the DHCP server in four stages:
- Discovery stage
- Offer stage
- Request stage
- Acknowledgment stage
We have already discussed these stages in our DHCP blog. Make sure to read it before you learn DHCP snooping.
As we have read in the above-mentioned example the DHCP offer message can only be sent through the trusted port when the DHCP snooping is initiated. Or else, it will be cancelled and dropped.
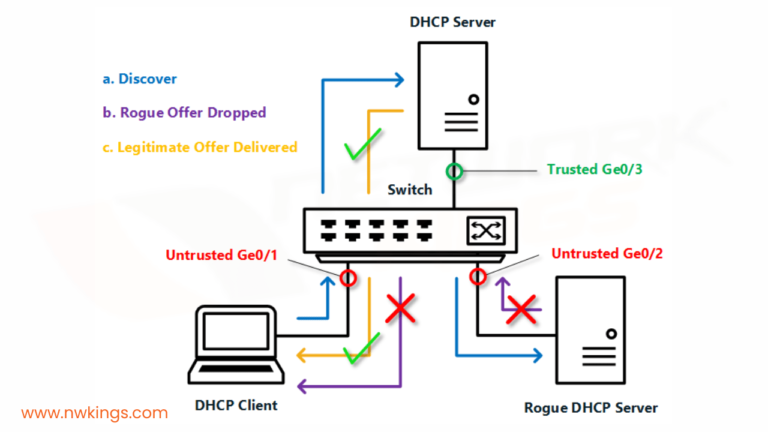
After the offer stage, a DHCP binding table is created on the basis of the DHCP ACK message in the acknowledgment stage. The following metrics are noted in the DHCP binding table:
- MAC address of the host
- The leased IP address from the DHCP server
- The binding type
- The VLAN number
- Interface information related to the host
If the upcoming DHCP packet received from an untrusted host fails to match the provided information, it will be disapproved.
What are the Common Attacks Prevented by DHCP?
Let us now discuss a bunch of examples of DHCP-based attacks that DHCP snooping can prevent against!
DHCP Starvation:
- It is also called a DHCP exhaustion attack.
- In such an attack, the attacker uses a spoofed MAC address to flood the DHCP Discover messages, i.e., the messages that are sent to request the IP address.
- Then the target server’s DHCP pool becomes full. This results in a Denial-of-Service (DoS) to other devices.
- They won’t be able to get an IP address from the server.
- The attacker sends countless DHCP discover messages with false source MAC addresses.
DHCP Poisoning/Spoofing Attack (Man-in-the-Middle):
- DHCP poisoning can be used to perform a Man-in-the-Middle attack.
- A fake DHCP server replies to a client’s DHCP discover messages and assigns them an IP address, but makes the client use the fake/rogue server’s IP as the default gateway.
- The client usually accepts the first offer message they receive.
- This will cause the client to send traffic to the attacker instead of the real default gateway.
- The attacker can then modify or examine the traffic before forwarding it to the real default gateway.
How is DHCP Snooping Configured?
Let us now go over some basic DHCP snooping configurations.
In order to enable DHCP snooping on the switch (switch no. 2), the following command is run:
SW2(config)#ip dhcp snooping
But this is not enough. The DHCP snooping needs to be enabled globally with IP DHCP snooping by directing the switch to enable it on the VLAN as such:
SW2(config)#ip dhcp snooping vlan1
Then the no ip dhcp snooping information option is enabled as such. This step is not necessary but depends on the network design.
SW2(config)#no ip dhcp snooping information option
Finally, one of the uplink port or interface on the switch (G0/0 interface) is configured as such:
SW2(config)#interface g0/0
SW2(config)#ip dhcp snooping trust
As we have discussed before that all the ports are untrusted by default and it needs to be mentioned which ports can be trusted.
A similar configuration is performed for another switch such as switch no. 1 in a network consisting of the DHCP server.
After that, the DHCP binding table is checked by using the following command:
SW1#show ip dhcp snooping binding
This is how DHCP snooping is configured!
Conclusion
This wraps up everything you need to know about DHCP snooping. It is very important to learn the mechanism of DHCP snooping and how a DHCP server behaves in such a situation. Before jumping on to DHCP snooping, it is necessary to learn how DHCP works and assigns IP addresses to the hosts.
Happy learning!
Stay tuned for more blogs for the CCNA 200-301 series!