Do you have curiosity to know How AWS Cloud Practitioner Certification Boosts Your Resume? The prospect of getting started in the field of IT is an interesting one. The opportunities in this field are also humongous. And are also progressing each day. Especially in the domain of the Cloud. The job roles in the Cloud domain continue to rise at a rapid pace. The cloud generates enough employment for all, accounting for an increase of 24% in the previous year.
The growth in IT is definite by venturing into a field like a cloud.
Like the title suggests, now we are going to have a look at the best Amazon Web Service for people who wish to scale higher dreams and realize even bigger visions. But first what is AWS?
What is AWS?
Amazon Web Service, is referred to as an on-demand service provider for cloud computing platforms and APIs to the individuals, companies and governments on a metered pay-as-you-go basis.
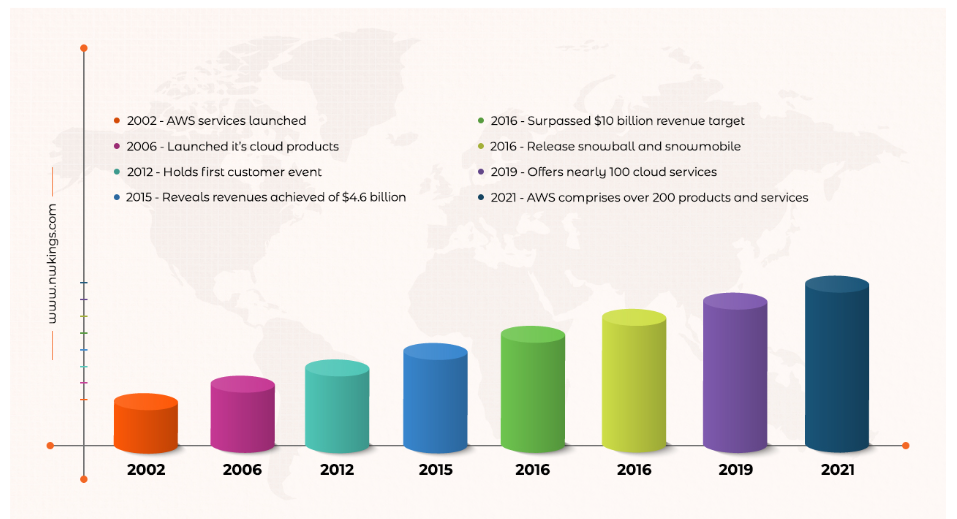
Amazon Web Services (AWS) happens to be the leader in facilitating all cloud-based services. The might of AWS is well identified, as the learner may be experienced or fresher, and the opportunities that open up are massive.
In the blog, we shall learn more about AWS certifications, and how they are beneficial for an individual’s career growth. We shall also try and find the AWS certification for those, newer to the scene of IT.
The varied levels of the certification:
Amazon offers three different levels of certifications based on the aspirant’s current experience in the cloud. Namely, foundational, Associate level and Professional level.
- The Foundational level is focused on the newer professionals or the ones who are seeking to make a career change, along with six months of fundamental AWS and cloud industry knowledge.
- The Associate level is aimed at one year of experience in working with and troubleshooting solutions in the AWS cloud.
- The professional level keeps the focus, on the experience, of about two or more years of comprehensive experience in designing, implementing and further operating AWS solutions.
With all varying areas, the categories of the certifications also vary. For each different area, the certification also varies. The areas can be as diverse as, Data Analytics, Machine Learning and security.
Importance of AWS certifications:
AWS- Amazon Web Service has emerged and its practice is unarguably growing. Passing the exam and getting certified is most certainly a worthy credential. There are multiple benefits, let’s have a look at the following:
- Getting prepared for the future:
As we read earlier, the initial benefits of AWS relate to the increasing popularity of cloud technology. The shift of major enterprises to the cloud is going to be beneficial for the candidates who have earned the AWS certifications, as AWS as discussed earlier is the leader among all cloud service providers.
- The emergence of newer avenues for widening the horizon:
The earning of AWS certifications ensures that you have entered the game for developing expertise of any kind. The horizons are wide and continue to stay the same as a candidate isn’t bound, they can learn AWS DevOps Certification after qualifying for the AWS Developer associate certification as well.
- Acts as authentication of learning:
Another very vital mention in AWS is related to the fact that these certifications bring a lot of recognition to all. All AWS-certified professionals are recipients of digital badges. These badges are further representative of the individual’s certification achievement. The badges are a way to prove that an individual is worthy of exclusive access to select AWS Summit events etc.
- A better remuneration:
Another benefit of AWS certification is the salary of an individual. As per certain surveys, the AWS certification is credible enough to improve the salary of an individual who has gained the certification, by 25% approx. The average salary for AWS-certified individuals is estimated to be 100,000 USD approx.
Best-suited options for new IT professionals: AWS Cloud Practitioner Certification.
There are many recommendations as we have seen but as discussed previously all recommendations are not suitable for one role. As per the level of learning and expertise, certifications keep on varying. For an aspirant, to whom the concept of developing, implementing and problem-solving is comparatively newer or foreign then it is recommended that they should go in for the AWS Cloud Practitioner, which is a course at a foundational level.
The AWS Cloud Practitioner Certification recommends a period of 6 months, for developing familiarity with AWS and basic understanding of IT services that are being provided by a cloud platform.
Not having any experience at all shouldn’t deter you from learning new things, at least not here, as the AWS Cloud Practitioner is intended for people who are new to the scene of cloud ecosystem. The certification covers all the basics of the cloud ecosystem and also provides a baseline for the foundational knowledge.
Job roles after AWS Cloud Practitioner Certification:
There are numerous job roles that open up after the AWS cloud practitioner certification, like the following:
- Program Manager
- Cloud Engineer
- AWS engineer
- Cloud Consultant
- Security Analyst
- Solutions Architect
Getting ready for the AWS Cloud Practitioner Certification Course:
The process of getting certified is seemingly long, but once this is assured the journey is definitely worth the wait. The efforts are definitely worth it, especially for the upscaling in the professional front. There are multiple ways of beginning to learn and amp up for the journey of getting certified. It is a highly subjective matter.
One of the ways is taking a proper guided course, with mentoring from people who have already taken the certification. As the journey of attainment helps an individual to get not only the academic help but a pragmatic insight into the working of an AWS certified professional.
It is up to an individual but if this mode of learning suits an individual here is a course by Network Kings, that seems befitting, tap here to know more.
Concluding thoughts:
The AWS cloud practitioner certification is absolutely worthy for beginners. It is a good certification to begin with when looking to get started in the cloud domain. Also the job availability in this field is just as huge due to the huge game in the supply demand gap in this field. The number of jobs is huge when compared to the people who are certified in this field. That latter number is really scarce.