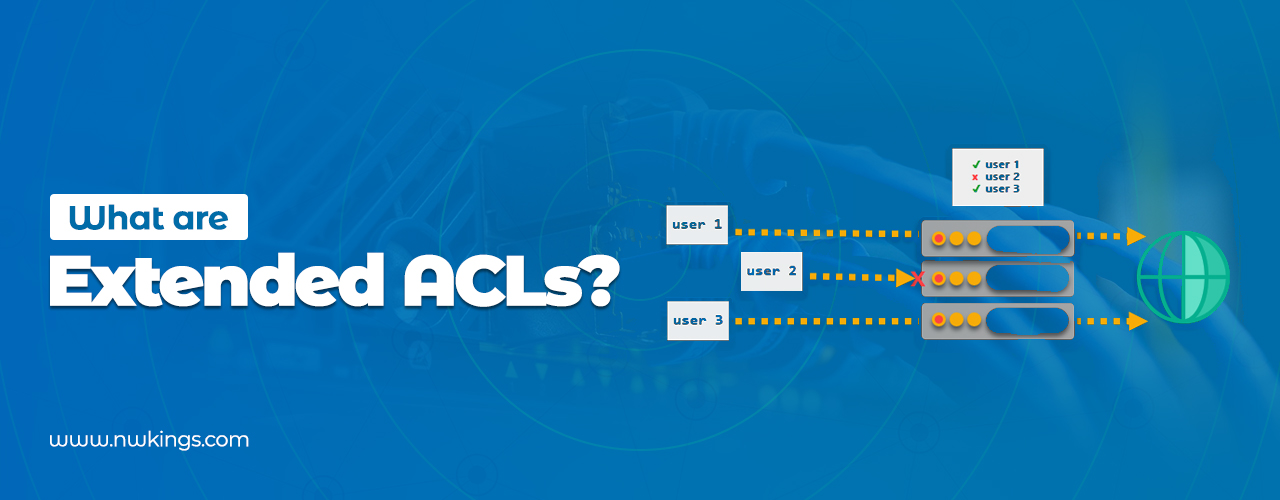
An extended access control list (ACL) is a type of ACL that can be used to filter traffic based on source and destination IP addresses, as well as port numbers and protocols. Extended ACLs can be used to allow or deny traffic from specific devices or groups of devices, as well as to specific ports and services.
Extended ACLs provide more granular control over traffic than standard ACLs, which can only be used to filter traffic based on source IP address. In addition, extended ACLs can be applied inbound or outbound, while standard ACLs can only be applied inbound.
In this blog, we will take a closer look at extended ACLs and how they can be used to protect your network. We will also compare extended ACLs to standard ACLs and discuss the benefits and drawbacks of each type of ACL.
In the previous blog of our CCNA 200-301 series , we talked about the Standard ACLs. I recommend you go through it before you jump to this blog.
What is an extended ACL?
An extended ACL is a type of access control list that provides detailed control over traffic flows on a network. An extended ACL can be used to filter traffic by source IP address, destination IP address, port number, and protocol.
Moreover, extended ACLs can be applied inbound or outbound, to or from specific devices or groups of devices, as well as to specific ports and services.
Extended ACLs are more flexible than standard ACLs because they can be used to filter traffic in more detail. For example, an extended ACL can be used to block requests to a web server from a particular IP address or range of IP addresses, while a standard ACL can only be used to filter traffic based on the source IP address.
Why do you need an extended ACL?
Extended ACLs are essential for ensuring that only the desired traffic is allowed on a network. If a network does not have an extended ACL configured, malicious attackers can exploit the network by sending malicious traffic that bypasses security measures.
Furthermore, without an extended ACL, certain applications may not function correctly because the traffic associated with the application is being blocked or rate limited.
Extended ACLs also allow network administrators to troubleshoot network issues quickly and efficiently. For example, if a user is unable to reach a web server, the network administrator can use an extended ACL to check which ports and protocols the server is accepting connections on. This can help the administrator determine the cause of the issue more quickly.
How do you configure an extended ACL?
Configuring an extended ACL can be a complex process and depends on the network architecture and the desired security objectives.
Generally, the process involves defining the traffic flow that needs to be controlled (i.e., which traffic is being allowed or denied), specifying the source and destination IP addresses, port numbers and protocols, and then applying the extended ACL to the network device (e.g., a router or firewall).
You can follow the following mentioned steps to configure an extended ACL:
- To configure an extended ACL, first, use the “access-list” command to create a named extended ACL.
- Next, use the “permit” or “deny” commands to define the traffic that the ACL should allow or block. For example, to block incoming ICMP traffic from a particular IP address, use the following commands:
access-list permit icmp any access-list deny icmp any
- Finally, apply the extended ACL to the desired interface using the “ip access-group” command. For example, to apply the extended ACL to the serial 0/0 interface, use the following command:
ip access-group in serial 0/0
What is the Difference Between Extended ACLs and Standard ACLs?
Extended ACLs | Standard ACLs |
Filtering is based on the source IP address, destination IP address, protocol type, source port number, and destination port number. | Filtering is based on source and IP address. |
They are used to block particular services. | They are used to block a specific host or subnetwork. |
They are implemented closer to the source. | They are implemented closer to the destination. |
The extended ACLs numbers lie in the range between 100 to 199. | These can either be named or numbered with numbers in the range between 1-99 and 1300-1399. |
One-way communication will be blocked in extended ACLs. | Two-way communication is blocked in standard ACLs. |
A specific service is blocked. | All services are blocked. |
What are the benefits of extended ACLs?
Here are some of the most significant benefits of extended ACLs:
- An extended ACL provides greater granularity and control over traffic flows than a standard ACL, allowing administrators to specify which traffic should be allowed or blocked.
- This allows administrators to secure the network from malicious attackers, as well as prevent certain applications from being misused.
- In addition, extended ACLs can be applied inbound or outbound, allowing administrators to filter traffic on the ingress or egress of the network.
- This provides more flexibility in how traffic is filtered, allowing administrators to secure the network in more detail.
Are there any drawbacks to extended ACLs?
The primary drawback to extended ACLs is that they can be difficult to configure and maintain. Configuring an extended ACL requires detailed knowledge of network architecture, as well as various networking protocols, such as TCP and UDP.
In addition, extended ACLs must be regularly reviewed and updated to ensure they remain in compliance with security best practices and current standards.
To sum it up
In conclusion, extended ACLs are a powerful tool for controlling traffic on a network. They provide more granular control than standard ACLs, allowing administrators to filter traffic based on source and destination IP addresses, as well as port numbers and protocols.
However, designing and configuring extended ACLs can be complex and time-consuming, so it is important to have a good understanding of network architecture and protocols before undertaking this task.
I hope this was helpful.
Stay tuned for more blogs for the CCNA 200-301 series!
Happy studying!