The Rapid Spanning Tree Protocol (RSTP) is a network protocol that allows for the rapid recovery of failed links in a network. It is an open standard, originally developed by IEEE in the early 2000s. RSTP is based on the Spanning Tree Protocol (STP), but it significantly reduces the time it takes to recover from link failures.
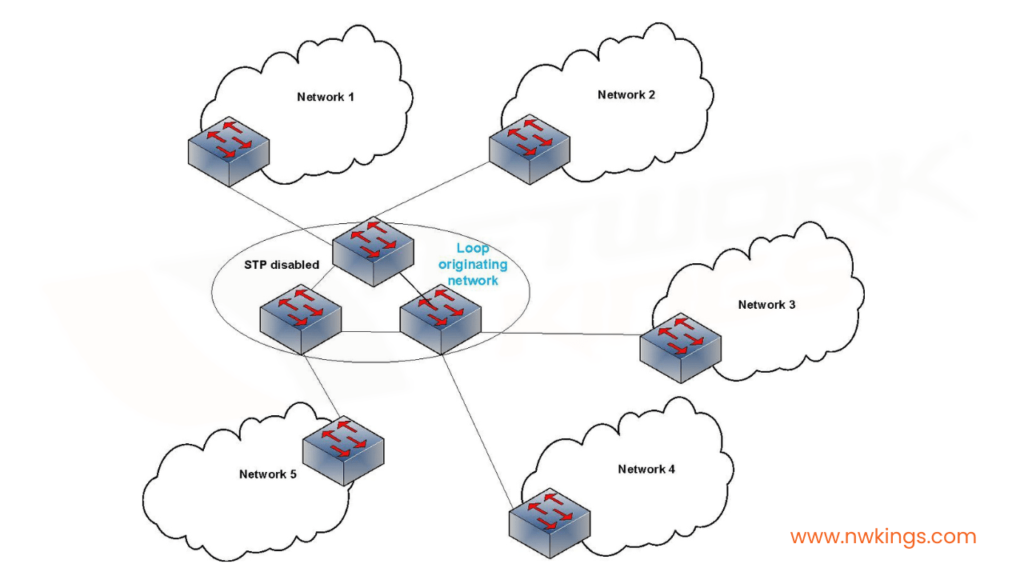
The Spanning Tree Protocol (STP) is referred to a network protocol that builds a loop-free logical topology for Ethernet networks. The STP was invented by Dr. Radia Perlman while working for Digital Equipment Corporation in 1985. STP is commonly used in bridged Ethernet local area networks (LANs).
The RSTP was designed to be an improvement over the STP. The RSTP was defined in the IEEE 802.1w standard in 2001. RSTP is similar to STP in that it prevents loops in the network and allows for redundant paths. However, RSTP converges much faster than STP.
In a traditional STP network, if a link fails, it can take up to 50 seconds for the STP algorithm to converge and re-route traffic. With RSTP, this time is reduced to less than 10 seconds. RSTP accomplishes this by using a more efficient algorithm, and by defining new port states that allow for faster recovery.
In this blog, we will take a closer look at the RSTP. We will explain what the RSTP is, how it works, and how it compares to the STP.
In the previous blog of our CCNA 200-301 series , we talked about the Security Program Elements in CCNA. I recommend you go through it before you jump to this blog.
What is the RSTP Protocol?
The Rapid Spanning Tree Protocol (RSTP) is an open, IEEE-standard network protocol that is based on the Spanning Tree Protocol (STP). It is designed to provide rapid recovery from failures in network links by allowing the network to quickly converge and route traffic around the failure.
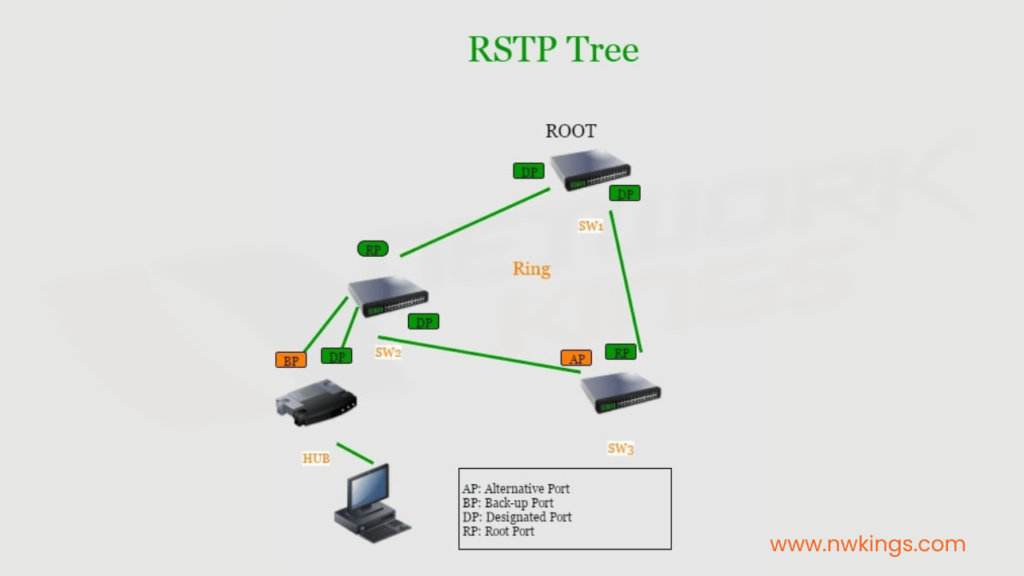
RSTP works by detecting the loss of a link and then rapidly electing which new link should be used to re-route traffic.
In a traditional STP network, the election of this new link could take up to 50 seconds, but with RSTP, the time is reduced to less than 10 seconds. To achieve this rapid recovery, RSTP uses new port states and functions that allow for faster link failure detection and recovery. In addition, the RSTP algorithm is more efficient than the STP algorithm, and it also simplifies the topology of a network by using fewer protocol packets.
How is the RSTP Similar to the STP?
Here are some of the main similarities between the RSTP and STP:
- RSTP serves the same purpose as STP, blocking specific ports to restrict Layer 2 loops.
- RSTP elects a root bridge with the same rules as STP.
- RSTP elects root ports with the same rules as STP.
- RSTP elects designated ports with the same rules as STP(Spanning Tree Protocol).
How Does the RSTP Protocol Work?
The RSTP protocol is based on a link-state algorithm. This means that is it constantly listening and monitoring the network to detect any changes in the topology or link status.
When a link failure is detected, the RSTP algorithm quickly reconfigures the network to route around the failed link. The RSTP protocol uses a set of defined port states and functions to enable it to rapidly detect link failures and reconfigure the network.
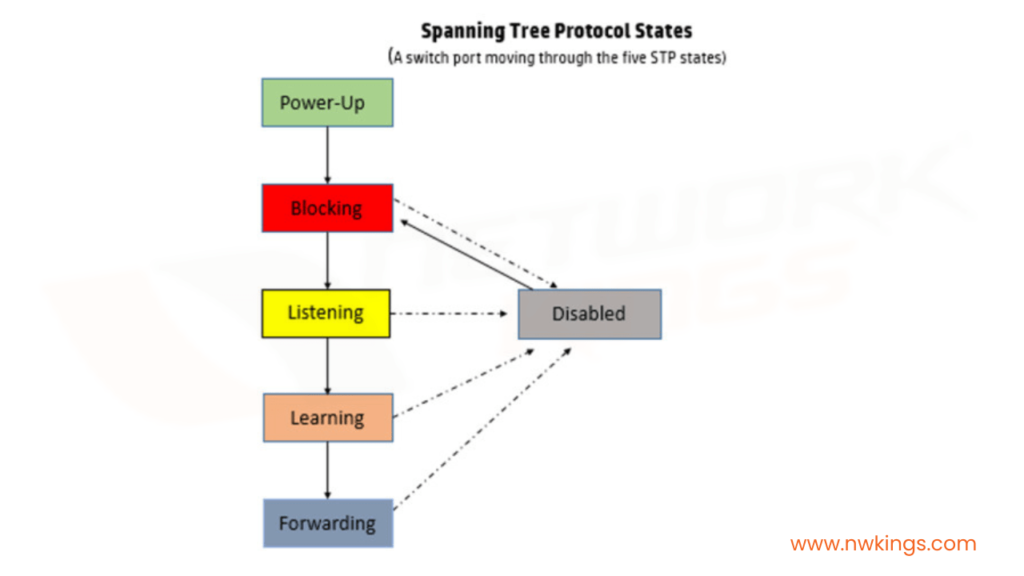
The five defined port states are mentioned below:
- Blocking
- Listening
- Learning
- Forwarding
- Discarding
Each port state serves a specific purpose in the RSTP recovery process. For example, when a link fails the RSTP protocol assigns the failed port to the blocking state, which prevents it from participating in the forwarding of traffic for that period of time.
Then, the RSTP protocol quickly elects which port should become the new root port and assigns it to the forwarding state, allowing it to take over the forwarding of traffic.
The Rapid Spanning Tree Port States
The various RSTP port states are given below in the table:
STP Port State | Send/Receive BPDUs | Frame Forwarding (Regular traffic) | MAC Address Learning | Stable/Transitional |
Discarding | NO/YES | NO | NO | Stable |
Learning | YES/YES | NO | YES | Transitional |
Forwarding | YES/YES | YES | YES | Stable |
- If a port is administratively disabled (shutdown command), that is equal to discarding state.
- If a port is enabled but blocking traffic to prevent Layer 2 loops, it means it is in the discarding state.
RSTP Link Types
RSTP distinguishes between three different ‘link types’.
- Edge:
It is a port that is connected to an end host. It moves directly to forwarding without negotiating.
- Point-to-Point:
It establishes a direct connection between two switches.
- Shared:
It is an established connection to a hub. It should be operated in half-duplex mode.
The Benefits of Using the RSTP Protocol
The biggest benefit of using the RSTP protocol is its ability to quickly recover from link failures. With a traditional STP network, the time it takes to re-route traffic around a failure can be up to 50 seconds. With RSTP, this time is reduced to less than 10 seconds. This drastically reduces network disruptions and improves the overall performance of the network.
In addition, since RSTP is an open, IEEE standard, it is supported by most network switches and routers. This makes it easy to implement and maintain in any network.
Some Final Thoughts
The Rapid Spanning Tree Protocol (RSTP) is a powerful, open standard that provides improved link-failure recovery time compared to the traditional Spanning Tree Protocol.
It is a fully supported protocol and is easy to implement and maintain in a network. RSTP is especially beneficial in network environments that require near-instantaneous recovery from link failures.
I recommend you read about STP first in order to understand RSTP in a better way.
Stay tuned for more blogs for the CCNA 200-301 series!
Happy Learning!