
We have learned about many different network protocols that help us communicate with other network devices. We are able to share data among different network devices. Secure Shell or SSH is a protocol used to connect devices and configure them via the CLI.
One of the options is to connect a device and configure it through a console port. However, SSH allows you to connect to a device remotely without being directly connected to its console port.
Therefore, SSH is a network protocol that lets you configure network devices using remote access. Before we study SSH, you must know that the industry was using Telnet which is quite similar to SSH, however, it is less secure.
In this blog, you will learn what is SSH and what it is used for. You will also learn about the architecture of SSH as well as how it works. Let’s get started without any further ado!
Note: If you haven’t read the previous blog of our CCNA 200-301 series, I highly recommend you do so.
What is Meant By SSH?
SSH which is also known as Secure Shell or Secure Socket Shell is a network communication protocol. Here are the key feature of the Secure Shell:
- The Secure Shell or SSH protocol was created in 1995 to replace a less secure protocol called Telnet.
- The term “shell” in SSH refers to a computer program that provides an operating system’s services to a user. So, if you are accessing a CLI of a device, it is basically a shell. Earlier, this term referred to a program that processes Unix commands.
- SSH allows encrypted communication between two network devices, therefore, it is very secure.
- Therefore, with SSH, you can remotely access a computer over an insecure network such as the Internet.
- SSH is mainly used by Network Administrators to manage systems and applications remotely. This allows them to log in to another computer and implement commands as well as move files over a network.
- SSHv2 which is a major revision of SSHv1 was released in 2006.
- Version 2 of SSH is much more secure than the first version, therefore, it can be used whenever possible.
- If a device supports both version 1 and version 2, it is said to run version ‘1.99’. Please note that it is not a version of SSH, it simply means version 1 and version 2.
- SSHv1 is not in use anymore because of its rudimentary/old designs.
- In a nutshell, SSH provides security features such as encryption and authentication.
- Telnet uses TCP Port 23. SSH uses TCP Port 22.
What is SSH Used For?
We have already covered the key features of SSH to know what it is used for. Let me highlight what an SSH is really used for in this section.
SSH is used by Network Administrators to manage apps and systems completely on a remote basis. More than 50% of the world’s servers, be they on-premise or cloud are managed by SSH!
It is used to secure, manage, configure, maintain and operate network servers, firewalls, routers, switches, and applications.
Therefore, there are three parameters included in SSH security:
- Encryption
- Authentication
- Data integrity
You must remember that SSH is critically used to connect to a remote host in a terminal session.
How Does SSH Work?
The SSH protocol follows a client-server model. We have learned about it before as well. Just to refresh, the client-server model is a request-response model case where a server responds to the request of a host.
It connects a secure shell client application with the SSH server where the actual end session is executed.
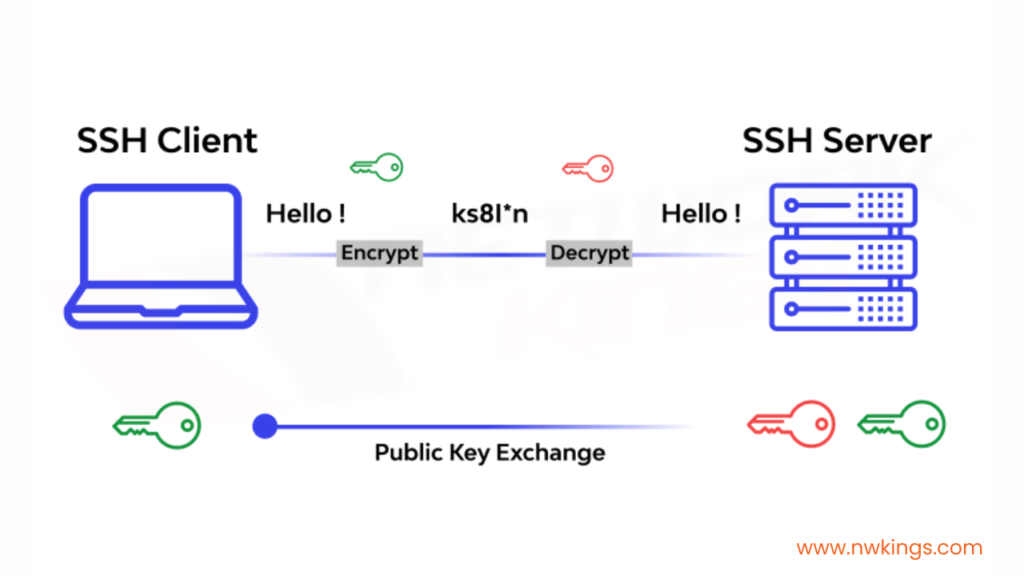
SSH performs the following functions:
- The client initiates the network connection by contacting the server.
- It then sends the server a public key.
- This public key is exchanged with the SSH server.
- The SSH client and the SSH server then negotiate the parameters and open a secure channel.
- A user login occurs to the server host operating system.
The SSH connects to the remote system by using the following demand:
ssh UserName@SSHserver.test.com
What is the Architecture of SSH Protocol?
SSH protocol consists of three layers that are well-separated from each other. The different layers of SSH are as follows:
- Transport layer
- User-authentication layer
- Connection layer
Let’s go over all these layers one by one:
1. Transport Layer:
- The transport layer is the highest layer of the TCP/IP protocol.
- This layer handles initial key exchange, server authentication, encryption, compression, and data integrity.
- It sends and receives plain text packets of up to 768 bytes.
2. User-Authentication Layer:
- This layer is responsible for handling client authentication.
- It also provides different authentication methods.
- The different methods of authentication include:
- Password authentication
- Public key-based authentication
- Keyboard-interactive authentication/ OTP-based authentication
- Authentication by external methods (GSSAPI).
3. Connection Layer:
- SSH service can be provided through various channels which are decided by the connection layer.
- One SSH connection can host various channels at the same time.
- Data could be sent in two directions by the connection layer at the same time.
- There are different types of standard channels in the connection layer:
- Shell: It is used for terminal shells.
- Direct-tcpip: All the client-to-server connections use direct-tcpip.
- Forwarded-tcpip: all the server-to-client connections use forwarded-tcpip.
Through all these different layers, SSH can transfer different types of data such as:
- Text
- Data
- Commands
- Files
Bottom Line:
This marks the end of the SSH blog. In this blog, we have learned about the very important concepts of the Secure Shell protocol. This protocol is the better version of old protocols such as Telnet, etc.
We have learned the key features of SSH. Moving on, we understood the uses of SSH. Then we covered the working of the SSH protocol followed by the architecture of the protocol.
You can check out our previous blogs of CCNA course series to learn about different protocols used in networking.
Stay tuned for more blogs in our CCNA series.
Keep Learning!


