Are you feeling a bit baffled by the idea of what is NAT Gateway in AWS? Don’t sweat it, we have got you covered! In this blog post, let us take an in-depth look at what exactly is NAT Gateway and how networking traffic functions within AWS Cloud. We will also talk about some of the security features enabled through Amazon VPC that make use of a NAT gateway as well as how to ensure enhanced cloud safety when utilizing these features.
So, if your goal here is to gather info on using NAT Gateways with AWS Network – then stick around because you are definitely in the right place!
Understanding the Basics of AWS and NAT Gateway
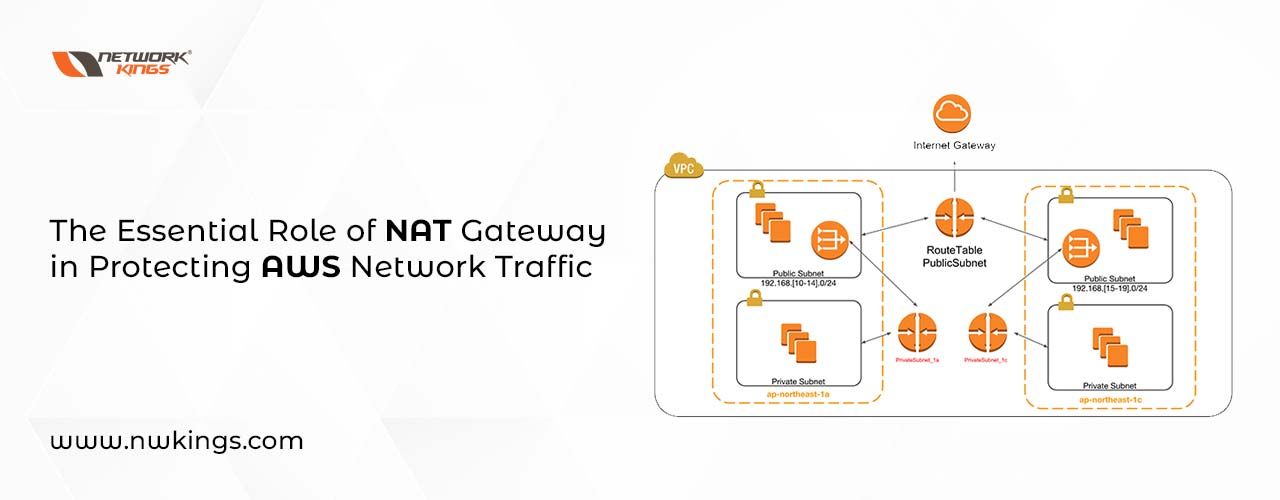
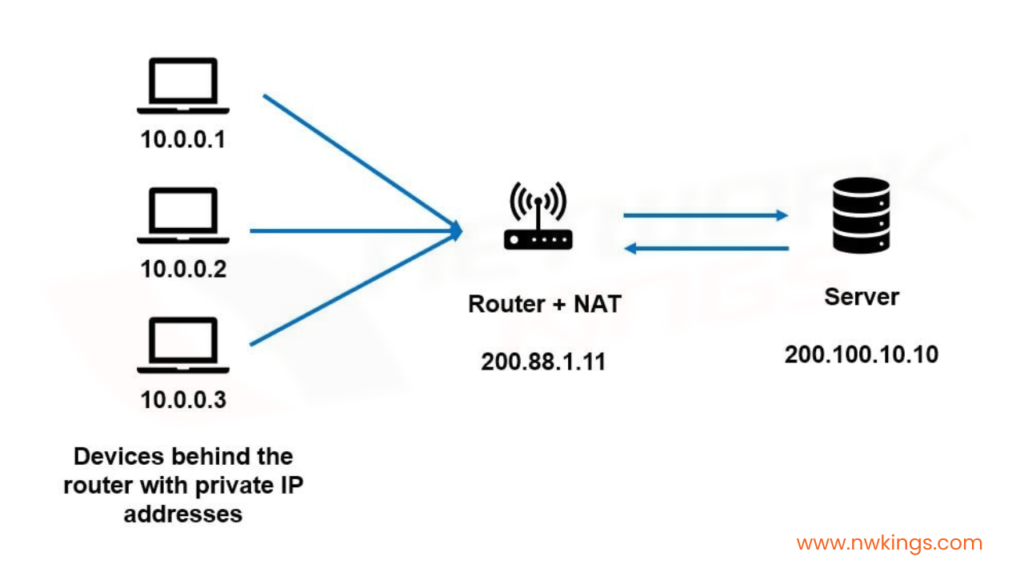
Anyone beginning with AWS knows that understanding the Network Address Translation (NAT) Gateway is fundamental. Grasping how it works will be a great help for getting on your feet in setting up. NAT Gateway, from Amazon Virtual Private Cloud (VPC), allows the directing of web traffic out of an AWS VPC meaning instances inside can go onto the net while any internet-based activity cannot access them.
Essentially, NAT Gateway acts as a middleman between public networks like the Internet and private ones. It is actually rather different to just Network Address Translation because it also accepts incoming traffic from outside – so even though instances in your VPC have their own special private IP address, they can still receive data from external sources. That way you don’t need to expose your sensitive information but remain connected externally; sounds great right?
What’s more, you can use Amazon NAT Gateway in an AWS free tier account or even on your AWS EC2 instances without paying any extra money. The Amazon VPC wizard offers some settings that will help you to personalize the gateway set-up for distinct objectives such as logging and security needs; so it is worth taking time to examine these choices closely and make a decision regarding which suits your requirements best.
Additionally, if multiple gateways are needed by different services or apps inside of one VPC, then creating numerous ones should be possible – however, there is an upper limit concerning how many gateways per VPC may exist, so double-check this prior to making too many just in case those limits are exceeded!
Exploring the Significance: What is NAT Gateway in AWS Network
NAT Gateway in the AWS network is definitely something to take into consideration when seeking methods of protecting your software resources. It is complex, that much can be sure – even for experienced tech professionals, it could present a challenge!
Yet, if you wish to keep all the applications running smoothly on the Amazon Web Services platform then this highly complicated technology becomes essential. So what exactly does NAT Gateway do? In very simple terms: one of its most crucial roles is allowing secure connections between different networks without having the necessity of configuring each resource separately. Pretty useful right?
A public IP address can be allocated to the NAT Gateway, meaning that all requests from outside sources will go through this particular IP Address. You will also have control over access coming in from external sources – you are able to permit specific types of traffic whilst refusing any others. What’s more, utilizing a NAT gateway can make your links much quicker by routing them far more effectively when compared with standard networking solutions. It begs the question: why would you not use a NAT gateway?
An extra benefit is that with a NAT gateway in your AWS network, you don’t have to worry about investing in a separate firewall or other safety measures as all of the traffic going into and out of the system via this gateway will be monitored and managed by its integrated features for protection assurance.
Additionally, using a NAT Gateway allows you to switch IPs without difficulty so that rules related specifically to one type of communication can be changed or added easily while having no effect on any other ongoing transmissions within the same local area network. All in all, if making sure your application running on an Amazon Web Services platform works optimally is something which matters greatly then setting up a reliable NAT Gateway should definitely feature highly on your list of priorities; security and efficiency are maximized while IT administrators save plenty due not needing to oversee multiple components separately given it is built-in into their services package plus kept updated constantly thanks Cloud Experts at AWS!
Delving into the Operational Mechanism of NAT Gateway
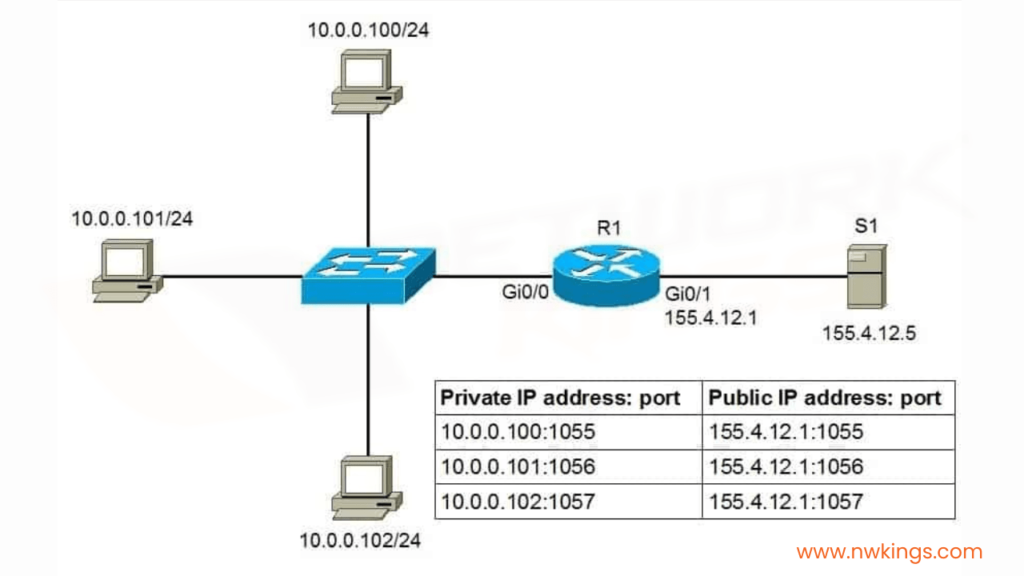
The NAT Gateway is a major tool in AWS that gives users an internet connection to computers operating on private subnets by giving them their own public IP addresses. It acts as a router, allowing outbound traffic from the private subnet and also enabling incoming ones like web requests. To be able to take full advantage of its functionality, it is essential we understand how it functions – what are its two main elements? The gateway subnet and network address translation (NAT). Have you ever used this powerful tool before?
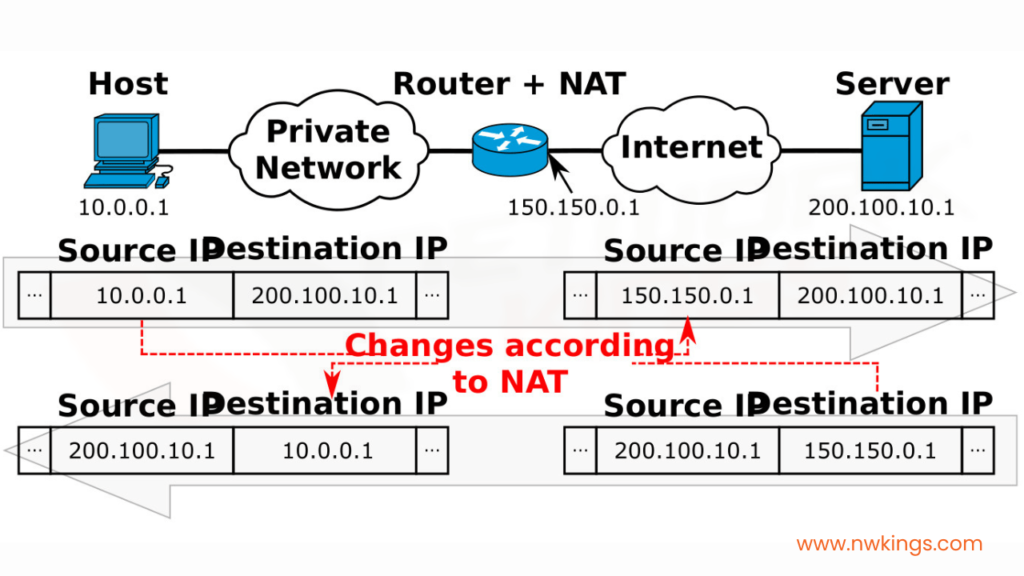
The gateway subnet has an Elastic IP Address (EIP) associated with it, which is used as the source of all outbound traffic. This EIP will receive any incoming traffic meant for private subnets such as web requests or SSH connections. The second part of this setup is Network Address Translation (NAT), which translates private IPs into public ones when leaving the network and back to their original form upon return. So essentially, NAT works like a one-way door; allowing you to enter from public space but only exit through the known way – via your own local premises!
Ask yourself why you would need such a system. Well, there are many reasons behind setting up these security measures: privacy protection by restricting access solely based on authentication methods and service availability even if outside networks get disrupted somehow still functioning inside its secured zones without impact since they use different protocols compared to unreliable external resources..
The Nature of NAT Gateways really aids us in keeping security and privacy within our networks since no one from an external network can figure out which instances are running on inside our VPCs, as it assigns individual public IP addresses to each instance instead of using one for all.
Consequently, every single instance appears like a standalone system when seen from outside even if they belong to the same private subnet – how cool is that?
What’s more, we have the power to control which ports are accessible from outside by configuring safety groupings in our VPCs, so it just allows access to certain protocols, such as HTTP, HTTPS or SSH connections for particular instances or even entire subnets. However, there are a few restrictions when setting up your NAT Gateways that you should be aware of – like not permitting specific kinds of communication between instances situated in various AZs; and needing multiple gateways if you desire redundancy across different AZs due to a single gateway’ limitations.
Additionally, according to how much traffic is going through it, there may arise extra charges, hence, ensure that you constantly keep an eye on your usage levels!
Unpacking NAT Gateway's Role in Enhancing Cloud Security
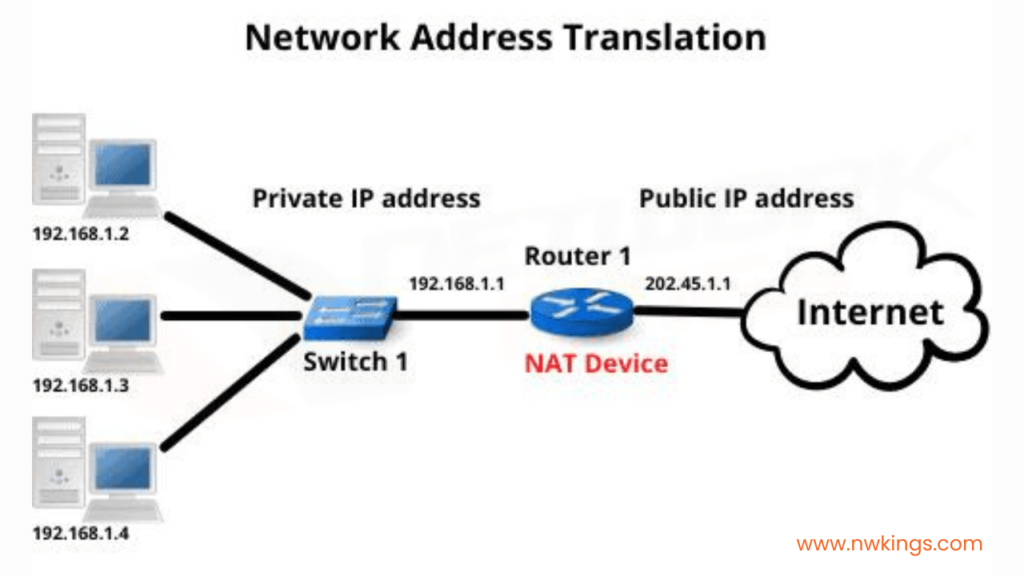
NAT Gateway is a cloud-based managed service from Amazon Web Services, designed to help secure and protect those using the network. Network Address Translation (or NAT) Gateways allow private networks to connect with external ones by using just one IP address; taking each request that originates on the private side of things and translating it into a public IP in order for it to be sent out across the internet – essentially keeping everything safe while still enabling communication. Have you ever thought about how this works?
Having confidential data on private networks is essential for security and NAT Gateway ensures it stays safe from anyone outside of the network. Not only does NAT Gateway make managing multiple devices easier, but also more secure: with this system you have one public IP that can be seen by outsiders. This setup has been used extensively in AWS environments where cloud security must take precedence – no wonder! After all, who wants their valuable information to get into the wrong hands?
To get a grip on how this service contributes to increasing security, take into account an arrangement where many resources are functioning within an AWS environment – EC2 instances, RDS databases, Lambda functions and so on. All these assets need access to the web yet don’t really require direct public accessibility. In such circumstances, configuring NAT Gateways can help eliminate unnecessary exposure of internal resources and enable restricted entry just when necessary. But what does this mean in practice?
It means that instead of allowing unrestricted internet connection from your private network to any external host, you establish a gateway which acts like a proxy between the outside world and your own servers or applications – thus keeping them safe from potential threats while still making it possible for them reach out bad hosts if required for some task(s).
As well as stopping any malicious traffic from infiltrating your system, NAT Gateways can also increase performance by caching requests which significantly cuts down internet usage for websites or services that are used frequently. These gateways don’t just give security and optimization of AWS environments with their storage abilities; they route data internally too between VPCs both within an AWS account or even across multiple accounts securely without the need to install extra infrastructure like a VPN or encryption keys or certificates.
This is great news if you are trying to cut costs on expensive maintenance overhead! With all these features rolled into one gateway solution, it gives peace of mind knowing your cloud environment will be secure but still hugely responsive to user applications whenever needed.
Detailed Look at How NAT Gateway Aids in Network Traffic Management
You have no doubt heard of NAT Gateway if you have recently been playing around with Amazon Web Services. This is a useful tool for network traffic management and it can make your life much more straightforward. But before we get into the nitty-gritty of how NAT Gateway functions, let us first understand what exactly it is.
NAT Gateway is an AWS-managed service which assists users in securely managing their network traffic. The gateway provides customers secure, private access to their resources on AWS – thus providing peace of mind!
Using Amazon Virtual Private Cloud (VPC) service, users can have a secure connection between their virtual private clouds and external networks such as the Internet.
This makes it easy for them to keep a check on incoming and outgoing network traffic without having to deal with two different networks or complicated configurations. Moreover, customers additionally benefit from extra security features offered by VPC like firewall protection, encryption services, intrusion detection systems etc., which help protect against malicious attacks aimed at targeting subnets in particular.
The most vital characteristic of a NAT Gateway is that it offers an effective way to direct information from one network interface to another without having any immediate access on either side. This implies all requests are channeled through the gateway which confirms just authorized demands get approval for admittance into AWS-maintained infrastructure, whilst turning away unauthorized ones.
Additionally, it works as a liaison between internal networks and outer sources where every traffic goes by means of particular ports which can be modified corresponding to the customer’s desires. This guarantees only necessary data passes through from interior VPCs while keeping other unrelated info blocked at all times.
Generally speaking, NAT Gateways present tremendous elasticity when it comes to controlling network traffic in an AWS environment due to its routing abilities, firewall protection features along with its skillfulness in managing port allocations depending on requirements set forth by customers or administrators alike; giving users higher power over who has admission their resources while defending against malicious activities simultaneously – how great does that sound?
Amazon VPC- Its Relationship with NAT Gateway
A NAT Gateway is an indispensable element of the Amazon Virtual Private Cloud (VPC). It serves as a passageway between public and private networks, facilitating secure outbound internet traffic from instances inside your VPC. Though it can be employed for incoming traffic too, NAT Gateways are normally used primarily for outgoing requests.
When setting up a NAT Gateway, you must furnish an Elastic IP address so that all external calls have one stable public IP address. How does this ensure security? By masking internal resources such as EC2 servers in the AWS cloud to users on the outside!
Having an Elastic IP makes it simpler for other services online, such as websites or API endpoints, to distinguish your requests and answer accordingly. Furthermore, having an Elastic IP guarantees that if you ever need access from outside the VPC – for maintenance or troubleshooting purposes – then you will still be able to get in even if the IP alters due to instance restarting or replacing. What’s more NAT Gateways utilize Network Address Translation (NAT) protocol so they can turn private IP addresses into public ones and vice versa. This is very helpful indeed!
This enables outbound traffic from instances within your VPC to access external services, for example, web servers or APIs, without exposing their internal IP addresses. The requests are guarded by both the firewalls inside the VPC and by NAT Gateway, which reduces the chances of any unauthorized access. Moreover, NAT Gateway adds an extra security layer as it ensures that only particular ports can be accessed from outside of the network; this stops unauthorized people from gaining entry through open ports on your instance(s). Why risk a potential breach when you have an additional defense mechanism?
Furthermore, by dividing outbound requests into various subnets with distinct routing tables, you can raise safety even more considerably by limiting specific sorts of traffic (such as SSH) from being sent through particular ports. All in all, NAT gateways are an absolute necessity for safeguarding secure connections between two networks while still allowing users to make use of the plentiful advantages provided by cloud computing frameworks like AWS.
By taking advantage of NAT gateways together with other security measures such as firewalls and routing tables, you are able to guarantee that each communication between your inner network and the web is safeguarded at all times – how else could one achieve this level of precaution?
Case Study Example of NAT Gateway Usages in AWS Network
NAT Gateway, a service in Amazon Web Services (AWS) network is an excellent route for administrators to manage internet traffic amongst their virtual private cloud subnets and the online world. By means of NAT Gateway, one sole IP address can securely channel traffic from one individual subnet to another without having to sort out public addresses inside each subnet. So let us take into consideration this example – imagine you possess a website that applies AWS services such as Amazon EC2 instances and S3 buckets. How would we be able to use the NAT gateway?
Do you need to stop outsiders from accessing your resources and data? Setting up an AWS VPC with two public subnets – Subnet A and Subnet B can help. But how do they communicate securely without making any of the internal issues visible on the internet? NAT Gateway could be a real savior here! It allows communication between these two subnets in such a way that no one outside knows what is going on inside them. Cool, right?!
Having NAT gateway enabled, all the traffic that is traveling from Subnet A to Subnet B will be routed through an isolated virtual private cloud instance running on AWS Network infrastructure. This implies that your entire data transfer is encrypted and safe as nobody else can access it. What’s more – considering both of these subnets are part of the same VPC (Virtual Private Cloud), they will have no problem communicating with each other without doing any additional setting up or customizing! Pretty neat, huh?
When implementing a NAT gateway into your AWS network architecture, not only will you be increasing the security of your infrastructure but also helping to reduce costs by no longer needing individual public IP addresses for every instance in each subnet. This is useful too for those who want granular control over their Internet traffic routing patterns; they can choose which ports should remain blocked and specify which routes are permitted through the single IP address associated with that particular NAT gateway instance.
Ultimately, utilizing a NAT Gateway within an AWS VPC ensures reliable communication between all different services while simultaneously bolstering security measures as well as reducing costs – it is really quite beneficial!
Comparing NAT Gateway and Other AWS Network Components
NAT Gateway is a network component from Amazon Web Services (AWS) that helps you keep in check the outbound traffic of your VPC. In contrast to the traditional NAT device, it doesn’t need to have all your traffic routed via one single apparatus; instead, numerous IP addresses on various public subnets can be assigned. You will also get more control over which outgoing ports are available and what sort of data transmission is allowed – the question arises, how important this might be for security?
When looking at the different network components available in AWS, it is clear that compared to Virtual Private Cloud (VPC), Elastic Load Balancer (ELB) and Internet Protocol Security (IPSEC) VPNs, NAT Gateway provides a much more straightforward and cost-effective way of managing outbound internet access. VPC is an incredibly powerful resource; it enables customers to secure their cloud resources, such as EC2 instances and RDS databases, by forming connections between them across single or multiple Availability Zones.
Customers can also control what kind of services are accessible externally using security groups within each subnet they set up with the VPC service – this includes being able to establish IPSec tunnels for additional protection if desired.
Doing away with the old ways, ELB (Elastic Load Balancing) enables users to spread their incoming application or network traffic across multiple EC2 instances for improved availability and scalability. IPSec VPN defines an encrypted tunnel between your data center or cloud environment and the AWS platform – authentication is mutual, meaning secure transit of data from one system over unknown networks like the Internet can be ensured.
NAT Gateway sorts out any issues related to obtaining online access by applications running on a VPC without being obliged to channel all traffic through just one device as was required in traditional NAT device set-ups. Why would you bother going back when there are so many better options available?
It is easier to configure than setting up a VPN, and much lower cost than running multiple ELBs in each public subnet of your VPC. You can control outbound traffic by determining which ports are open on the gateway, as well as specify source or destination IPs or ranges from where particular types of traffic will be allowed.
For example, you could make port 80 available for web access but block ICMP echo requests using CIDR notation for source IPs or ranges so that only certain public addresses may reach those services operating inside your AWS environment while refusing all others direct access over the Internet. What does this mean? It means you can ensure no unauthorized individuals gain entry into these parts of your system without permission!
Advantages of Implementing NAT Gateway in the AWS Environment
NAT Gateway is a managed service from AWS that enables users to securely route traffic coming in from the internet, right up to their private subnets. This tool has become increasingly important for setting up secure and efficient channels of communication between resources within as well as outside of AWS. Introducing NAT Gateway into your cloud environment could be quite advantageous: it can bring an increase in security, improvements with performance plus cost savings!
Basically, what NAT gateway does is give you a safe channel for communications between Address Spaces when used alongside Security Groups – all adding extra peace of mind knowing there are more layers protecting your info!
Configuring Security Groups to only allow specific ports and protocols is a great way of ensuring your network remains safe from malicious attacks or unauthorized access. What’s more, all the traffic passes through our NAT Gateway before it reaches its destination, which helps in preventing host-level attacks such as DDoS (distributed denial of service) on servers inside the network – an extra layer of protection that drastically increases security posture.
As well as ensuring the security of your system, introducing a NAT Gateway into your Virtual Private Cloud can have a positive effect on its performance too. By putting all traffic through this gateway before it reaches its destination, some processing load is taken away from the web servers in the VPC – reducing latency and improving website speed for end-users outside your premises. Plus, there are also cost benefits to be had!
Going for traditional solutions such as VPNs or leased lines from ISPs typically involve high initial costs related to hardware acquisition, setup and long-term contracts with consequent monthly payments. However, using NAT Gateways in AWS has the advantage of only paying according to usage without any kind of upfront charges or lengthy commitments – making them more cost-effective and scalable than other options.
All things considered, introducing NAT Gateways into your AWS environment proposes great advantages, including augmented security levels, improved performance and impressive savings – turning them into essential components for applications needing secure communication within and beyond the limits of AWS networks.
Possible Challenges and Solutions When Using NAT Gateway in AWS
As you ponder cloud-based virtual private networks, it is key to get your head around the function of a NAT Gateway. A NAT Gateway is a gateway in Amazon Web Services (AWS) which allows for the setting up of an encrypted connection between two disparate networks. This service provides you with the capacity to route traffic from one network to another without having to tinker with every single server or device on each end. But there are certain issues and possible traps that come along with using a NAT Gateway – what kind of troubles could arise?
Let us look at a couple of scenarios that could arise in a network environment. For example, if you have too many users trying to access the same resources all at once, your entire system could be brought down by an overload. Additionally, problems can occur if subnets on your network aren’t set up correctly and dynamic routing is disabled – this means communication between them would become impossible without making some changes.
Fortunately, there are several ways to solve these potential issues: proper configuration and quality monitoring tools like Amazon Web Services CloudWatch go hand-in-hand with ensuring smooth performance from servers and services on networks; they are also incredibly useful for anticipating bottlenecks or other difficulties before customers even experience any disruption!
AWS also provides an ELB Classic Load Balancer service so that performance can stay consistent even during peak usage times. This allows you to distribute requests across multiple servers automatically giving you more control over how traffic is routed between networks. AWS VPC Peering offers extra features such as custom routing tables and IP address translation support if further control is needed for your setup.
When it comes to security, AWS Security Groups can be used behind a NAT gateway in order to restrict access from various sources and IP ranges whilst still allowing necessary inbound or outbound traffic flow from applications running within the network – making sure there is no compromise on customer experience or security when using this set-up!
Wrapping Up!
To sum up, NAT Gateway is a fundamental part of the AWS Network. It provides an additional layer to your cloud security and enables hassle-free connectivity between Amazon Virtual Private Clouds (VPCs). As well as this, it helps maintain secure communications for applications while providing increased availability, scalability and low latency. Ultimately with its various features, using NAT Gateway makes sure that you can uphold both safety in your cloud environment but also experience smooth network access – how great is that?
Are you keen to top up your skills and get the know-how in Amazon Web Services (AWS) cloud security? Then our AWS Cloud Security Master Program is absolutely ideal for you! Through a comprehensive syllabus, you will learn all of the best methods of configuring and managing safe AWS cloud infrastructure. Our AWS course offers an easily followed plan with attainable objectives so that you can keep pace with your understanding progressions whilst honing your technical abilities in this field. So what are waiting around for – sign up today and begin mastering cloud safety! Have any questions about it? We will be more than happy to answer them all.
Fancy mastering the basics of cloud security? Keen to join our AWS Cloud Security Master Program and up your skills in this area? If so, don’t dilly-dally! Get signed up for our Master Programme right away for direct experience via hands-on labs under certified trainers from leading cloud provider Amazon Web Services (AWS). It doesn’t matter if you are a seasoned IT pro, an ardent cybersecurity fan or just starting out – this course is designed to accommodate all levels.
Join us now and be part of a select few working at the forefront of digital tech. Don’t miss this unique chance – enroll on our AWS Cloud Security Master Programme today!
Happy Learning!