Introduction to Cyber Security Interview Questions and Answers
In today’s digital age, cyber security has become a critical concern for individuals, businesses, and governments alike. With the increasing number of cyber threats and attacks, it is essential to have a strong defense system in place to protect sensitive information and prevent unauthorized access. This is where cyber security professionals come into play. They are responsible for safeguarding networks, systems, and data from potential threats.
Cyber security interviews are an important part of the hiring process for organizations looking to hire skilled professionals in this field. These interviews help employers assess the knowledge, skills, and experience of candidates to determine if they are a good fit for the role. It is crucial for candidates to be well-prepared for these interviews to showcase their expertise and stand out from the competition.
Being prepared for cyber security interviews is of utmost importance. It not only demonstrates your commitment and dedication to the field but also increases your chances of securing a job in this highly competitive industry. By thoroughly researching common interview questions and practicing your answers, you can confidently showcase your skills and knowledge during the interview process.
As technology continues to advance, the need for cyber security professionals is becoming increasingly important. If you are preparing for a cyber security interview in 2023, it is important to be knowledgeable about the latest trends and best practices in the field. Here are the top 50 cyber security interview questions and answers for 2023:
Top Cyber Security Interview Questions
- What is your understanding of cyber security?
- What motivated you to pursue a career in cyber security?
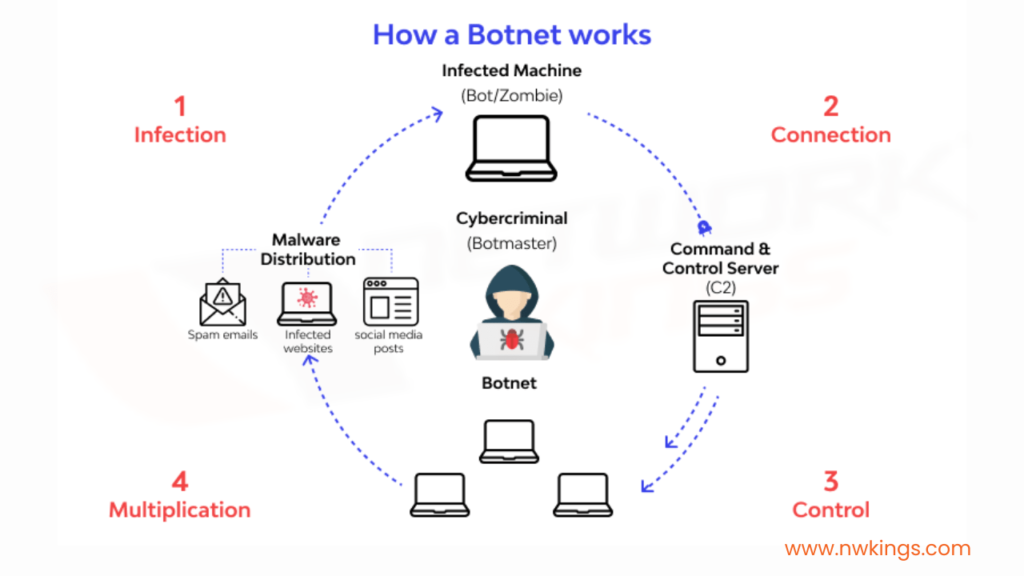
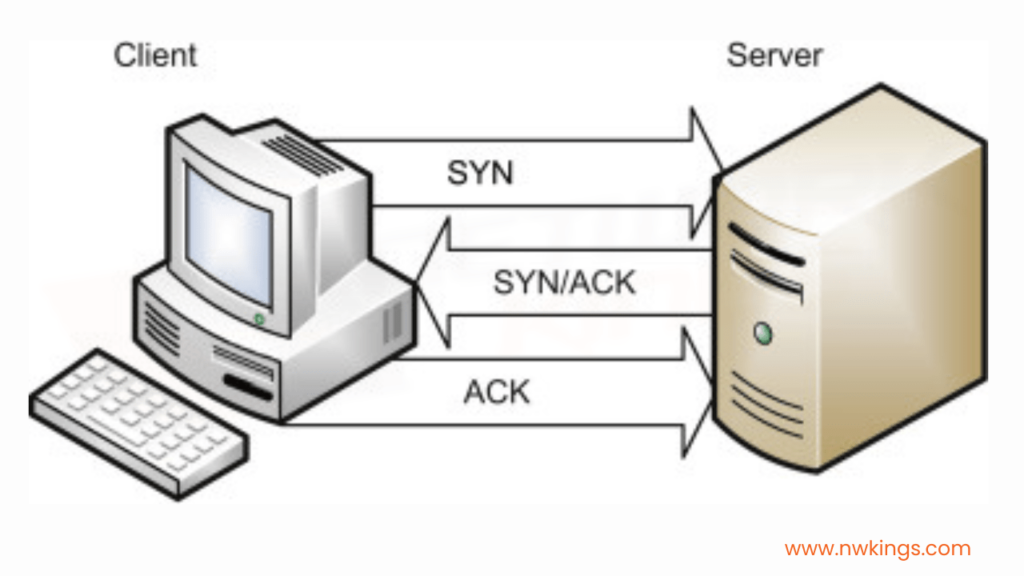
- What are some of the most common cyber security threats that organizations face today?
- How do you stay up-to-date with the latest cyber security trends and threats?
- What is your experience with vulnerability assessments and penetration testing?
- How do you ensure that sensitive data is protected from unauthorized access?
- What is your experience with incident response and disaster recovery planning?
- How do you prioritize security risks and vulnerabilities?
- What is your experience with network security and firewalls?
- How do you ensure that employees are trained on cyber security best practices?
- What is your experience with cloud security?
- How do you ensure that third-party vendors are following proper cyber security protocols?
- What is your experience with mobile device security?
- How do you ensure that software and systems are updated with the latest security patches?
- What is your experience with identity and access management?
- How do you ensure that passwords are secure and not easily guessable?
- What is your experience with encryption technologies?
- How do you ensure that data backups are secure and accessible in case of a disaster?
- What is your experience with social engineering attacks?
- How do you ensure that physical access to sensitive areas is restricted?
- What is your experience with compliance regulations such as GDPR or HIPAA?
- How do you ensure that data is properly disposed of when it is no longer needed?
- What is your experience with threat intelligence and monitoring tools?
- How do you ensure that remote workers are following proper cyber security protocols?
- What is your experience with incident management and reporting procedures?
- How do you ensure that all devices on a network are properly secured?
- What is your experience with risk assessments and risk management strategies?
- How do you ensure that data breaches are detected and contained as quickly as possible?
- What is your experience with network segmentation and isolation techniques?
- How do you ensure that all software used by an organization is properly licensed and up-to-date?
- What is your experience with secure coding practices?
- How do you ensure that all employees understand their role in maintaining cyber security?
- What is your experience with threat modeling techniques?
- How do you ensure that all devices on a network are properly configured for maximum security?
- What is your experience with cloud access security brokers (CASBs)?
- How do you ensure that all data transfers are encrypted and secure?
- What is your experience with multi-factor authentication (MFA)?
- How do you ensure that all devices on a network are regularly scanned for vulnerabilities?
- What is your experience with intrusion detection systems (IDS) and intrusion prevention systems (IPS)?
- How do you ensure that all logs and audit trails are properly maintained and reviewed regularly?
- What is your experience with application whitelisting techniques?
- How do you ensure that all employees understand the importance of reporting potential security incidents or breaches as soon as possible?
- What is your experience with secure email gateways (SEGs)?
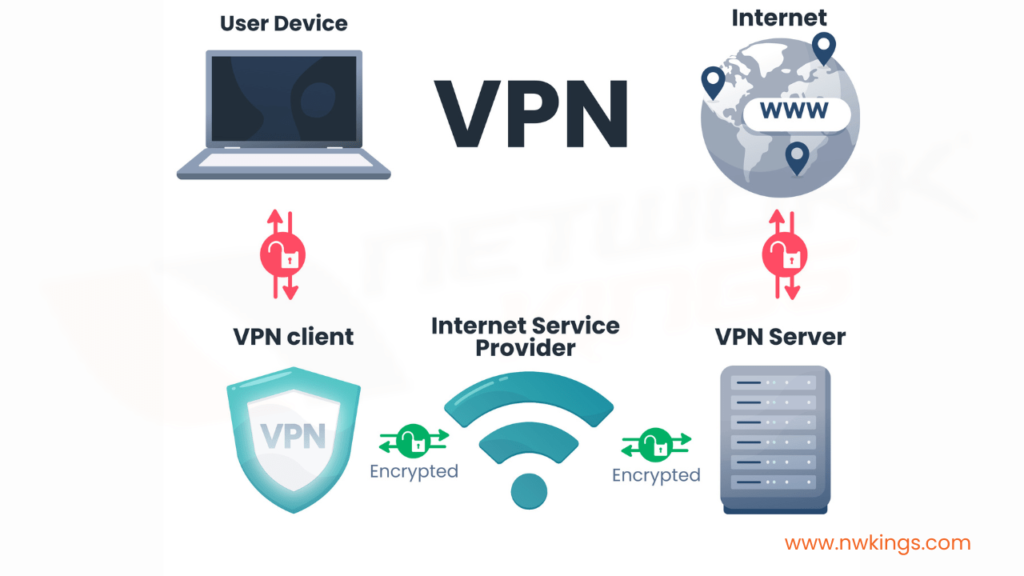
- How do you ensure that all wireless networks are properly secured against unauthorized access or attacks? 45. What is your experience with virtual private networks (VPNs)?
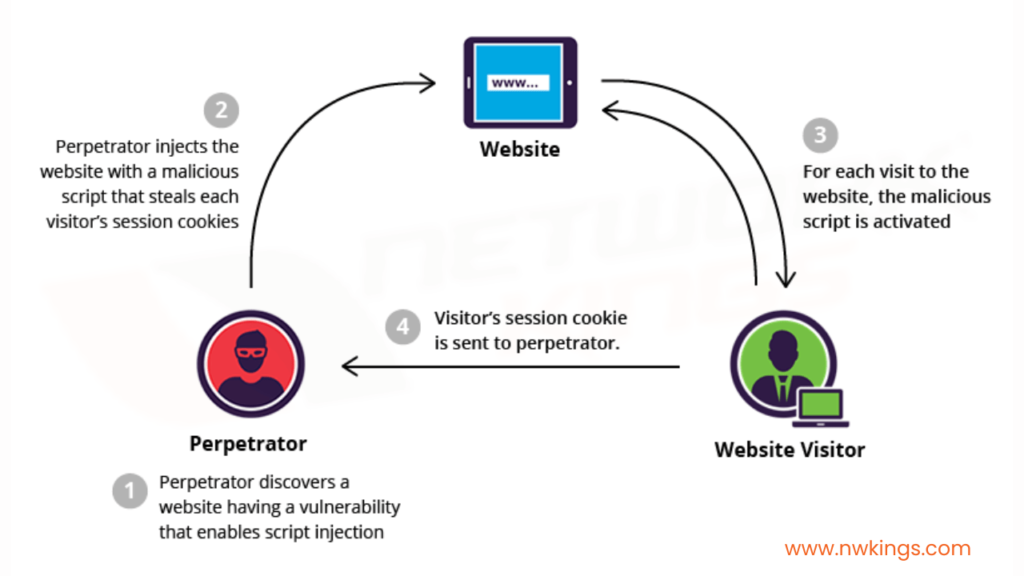
- How do you ensure that all web applications are properly secured against common attacks such as SQL injection or cross-site scripting (XSS)?
- What is your experience with containerization techniques such as Docker or Kubernetes?
- How do you ensure that all devices on a network have up-to-date antivirus software installed and running properly?
- What is your experience with zero-trust networking architectures?
- How do you ensure that all employees understand the importance of maintaining good cyber hygiene practices such as strong passwords and regular software updates?
General Tips for Preparing for a Cyber Security Interview
Preparing for a cyber security interview requires more than just memorizing answers to common questions. It involves thorough research, self-assessment, and practice. Here are some general tips to help you prepare for your cyber security interview:
1. Research the company and the job role: Before your interview, take the time to research the company you are interviewing with. Understand their mission, values, and any recent cyber security incidents they may have faced. Additionally, familiarize yourself with the job role you are applying for and the specific skills and qualifications required.
2. Answer questions confidently and effectively: During your interview, it is important to answer questions confidently and effectively. Take the time to understand the question before responding and provide clear and concise answers. Use real-life examples or experiences to support your answers whenever possible.
3. Practice mock interviews: Practicing mock interviews can help you become more comfortable and confident during the actual interview. Enlist the help of a friend or mentor to conduct mock interviews and provide feedback on your performance. This will help you identify areas for improvement and refine your answers.
Join Network Kings - Cybersecurity Master Program combo of Comptia Sec+, CEH & Pentest+
If you are looking for comprehensive preparation for your cyber security interviews, consider joining Network Kings’ Cybersecurity Master Program. This program is a combination of CompTIA Security+, Certified Ethical Hacker (CEH), and Pentest+ certifications, providing you with a well-rounded education in the field of cyber security.
The Cybersecurity Master Program offered by Network Kings is designed to equip individuals with the knowledge and skills needed to excel in the cyber security industry. The program covers a wide range of topics, including network security, ethical hacking, penetration testing, and more. It includes hands-on labs, real-world scenarios, and practical exercises to ensure that students gain practical experience in addition to theoretical knowledge.
By enrolling in Network Kings‘ Cybersecurity Master Program, you will have access to experienced instructors who are industry professionals with extensive knowledge and experience in the field of cyber security. They will guide you through the program, provide personalized feedback, and help you prepare for your cyber security interviews.
Testimonials from previous students who have successfully landed jobs in the cyber security industry after completing Network Kings’ Cybersecurity Master Program speak to the effectiveness of the program. These individuals credit the program’s comprehensive curriculum, hands-on approach, and expert instructors for their success in securing jobs in this highly competitive field.
Conclusion
In conclusion, cyber security interviews are an important step in the hiring process for organizations looking to hire skilled professionals in this field. Being well-prepared for these interviews is crucial to showcase your expertise and increase your chances of securing a job in the cyber security industry.
By thoroughly researching common interview questions, practicing your answers, and enrolling in a comprehensive program like Network Kings’ Cybersecurity Master Program, you can confidently navigate the interview process and stand out from the competition. Don’t miss out on the opportunity to enhance your skills and knowledge in cyber security and increase your chances of landing a job in this rapidly growing industry.