
As organisations become increasingly reliant on cloud-based services, the requirement for effective cybersecurity applications and tools is more essential than ever before. Learn all of the latest news and information regarding the different security technologies available, ranging from data protection to network security.
Furthermore, we debate the challenges associated with cyber risk management to aid organisations in devising successful tactics for protecting their business within a continually fluctuating online environment. Through our comprehensive coverage of cybersecurity topics, you can be certain that you are kept apprised about any advancements related to cloud security as well as other relevant areas.
Understanding the Importance of Cyber Security Applications
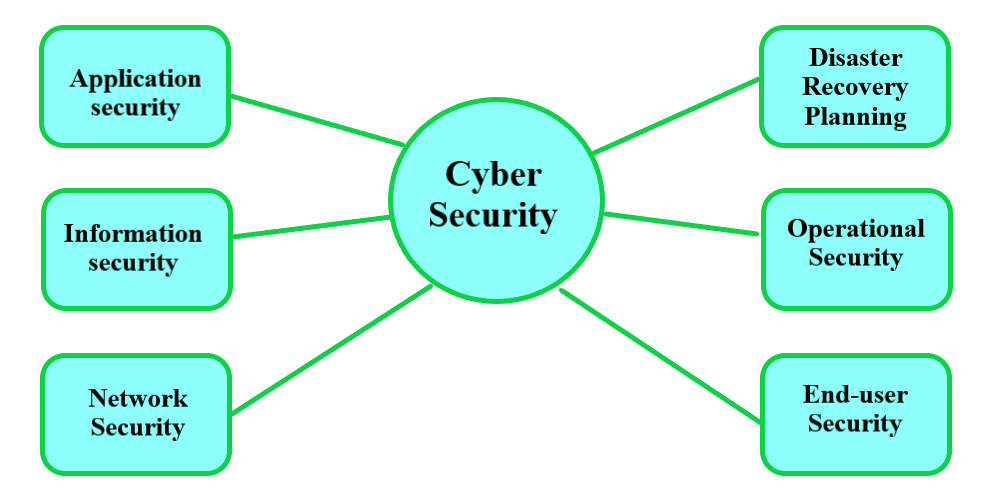
In the current digital world, cybersecurity applications have become increasingly essential. Owing to the proliferation of hackers and malicious entities, organisations must take measures to protect their data and confidential information from being taken or jeopardised. Cybersecurity applications are solutions made to detect, alleviate and prevent security threats which could compromise an organisation’s networks and systems.
These programs can assist in shielding sensitive data against unauthorised access as well as helping shield outside networks from cyberattacks. Furthermore, they supply safety tools for authentication plus encryption of records that are shared between users or preserved in databases.
It is of great importance for organisations to have a comprehensive cybersecurity application to protect themselves from various threats, such as virus attacks, phishing scams, malware infections and data theft. They must remain informed about the latest advancements in this field to take appropriate measures towards ensuring their data remains safe.
By making use of cutting-edge technologies including antivirus programs and malware detection tools businesses can more effectively identify any suspicious activities on their networks or devices thereby enabling them an opportunity to respond accordingly.
Many organisations depend on network firewalls and intrusion prevention systems to obstruct assailants’ attempts at obtaining confidential data or making modifications to the system infrastructure without authorisation. Companies must recognise vulnerabilities in their systems where attackers may utilise particular types of attacks, such as denial-of-service (DoS) assaults or buffer overflows.
In addition, companies should take proactive steps, for example putting into practice strong passwords policies; this ensures that user accounts have secure passwords which cannot be easily deciphered by malevolent actors. Furthermore, businesses ought to systematically run vulnerability scans using automated tools to detect probable vulnerabilities in their linked computer systems prior they are exploited by assailants.
Lastly, yet importantly, companies require investing in training programmes for all employees thus they comprehend the importance of cybersecurity applications and know how to precisely use them when called upon to do so successfully.
Exploring Various Cyber Security Tools for Safety
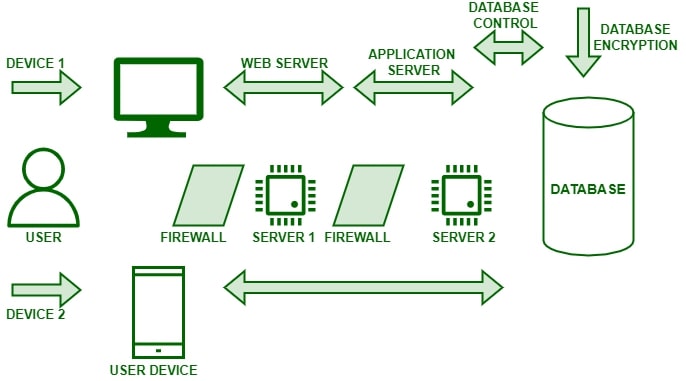
Cybersecurity is a significant worry for any organisation. There are numerous tools available that supply organisations with the capability to protect their systems from malicious assaults. Investigating different cybersecurity tools for safety can be an effective way of helping to guarantee data is secure and safe. It is of paramount importance to comprehend the various types of tools accessible, how they work, and how they can most beneficially be utilised to safeguard the organisation’s data and systems.
One of the most prevalent categories of cybersecurity instruments are malware scanners and vulnerability scanners. Malware scanners detect malicious code on computers or networks ahead of it being able to cause harm to the system, while vulnerability scanners recognise weaknesses in a system or network that might result in an attack.
Furthermore, firewalls and intrusion detection systems are also present which can prevent potential attacks as well as spot any activity that should be deemed suspicious. All these tools ought to be employed alongside each other so that they may yield their maximum benefit and guarantee all areas of the system have been guarded against danger.
Access Control Management is a further significant aspect of Cybersecurity which involves determining who has access to different aspects of a system or network, as well as the magnitude of such access levels. This encompasses both physical security components such as locks and passwords, along with digital security measures including encryption algorithms and multi-factor authentication protocols.
It is indispensable in forestalling undesired entry by cybercriminals that only those approved are given admittance to specific information and systems.
Moreover, having an incident response plan prepared ahead of time is vital for any organisation if confronted with an attack on its systems or a breach in security measures; this enables teams to act rapidly yet effectively should anything occur thus diminishing possible harms resulting from the invasion. A contingency approach like this allows for instantaneous solutions e.g., encapsulating infected machines so they cannot spread out more widely than necessary or closing down particular services until remedial action can be accomplished suitably..
Benefits of Adopting Network Security in Organisations
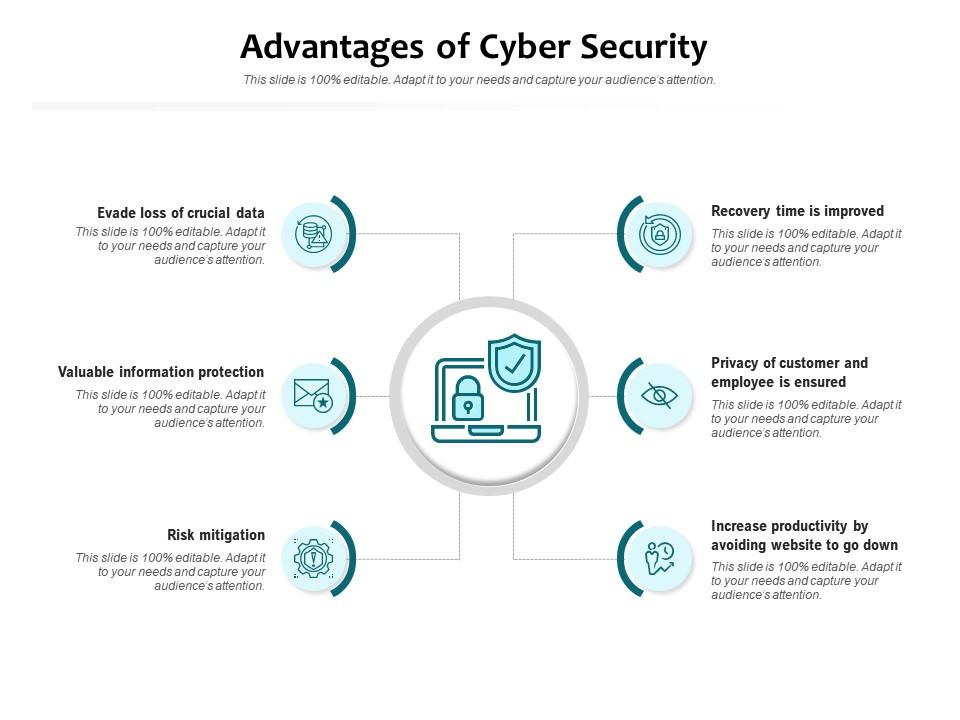
Organisations of all sizes and across virtually every industry need network security. This is the most effective approach to shielding their data, possessions and interests from damage inflicted by malicious actors. Moreover, thorough network security measures are capable of averting external threats from interfering with operations or damaging reputations.
The adoption of comprehensive network security policies and technologies brings numerous advantages which include enhanced safety, greater efficiency, better compliance outcomes on audits accompanied by cost savings as well as other benefits.
Ensuring that assets are protected from external threats brings forth the advantages of increased reliability, continuity and resilience for organisations when it comes to undertaking key business functions. Network security solutions can help to prevent hackers or malicious individuals from gaining access to confidential information which is held within an organisation’s digital system.
This is highly beneficial in protecting pertinent details about customers’ identities as well as corporate strategies, all of which may be employed illegally if stolen. Such precautions will lower the probability of a cyber attack occurring or data being lost through inadvertence on behalf of internal employees.
Enhanced safety provides organisational heads with the assurance that any confidential data is kept secure, making it simpler to observe laws and regulations involving online dealings or communications between members of an organisation. This lessens the risk of corporations being sanctioned for not adhering to regional or international principles, which could cause considerable financial damage.
Network security permits only certified staff authorised access when required legitimately – avoiding unauthorised use of resources which might otherwise be wasted if left unchecked. In addition, during audits organisations are likely going to fare better if they have undertaken dependable cybersecurity procedures taking into account both internal and external perils equitably.
Insights into the Role of Data Protection in Cyber Security

Cybersecurity is an indispensable part of any modern business operation. To ensure the safeguarding of data from adverse agents, it is pivotal to comprehend the role that Data Protection assumes. In simple words, Data Protection measures provide supplementary security for delicate information. These rules may come in the form of encryption or authentication which facilitate obscuring and protecting data against potential hazards.
Nevertheless, it is also significant to contemplate on implications deriving from breaches and unauthorised access when implementing these regulations. Instating stringent protocols regarding protection can aid commerce in decreasing risks related to cyberattacks and securely preserving customer details as well as other sensitive records. To guarantee adequate safety, businesses ought to apply appropriate user authentication procedures to control access towards vulnerable systems plus employ encryption technology wherever applicable.
Furthermore, they should observe their systems frequently searching for vulnerabilities which could be manipulated by malicious characters Utilising impenetrable protective programmes coupled with actively inspecting possible weak spots are essential components required when striving for optimal Cybersecurity within today’s digital arena by any organisation.
Cloud Security: A Game-Changer in Cyber Security Applications
Cloud security has come to the vanguard of cybersecurity applications in recent times and it can be argued that it is the most significant game-changer when considering defence against cyber threats. Cloud security is a form of data protection which utilises cloud computing to offer secure services to users, companies and organisations.
Its flexibility and scalability are unequalled and deployment within an environment can swiftly take place with minimal effort or cost involved. Additionally, cloud security proves highly effective at countering some of the more intricate attacks.
Cloud security has become an integral part of a reliable cybersecurity strategy, providing the means to significantly reduce any potential risks posed by malicious attackers. It offers numerous features which are designed to protect data from being accessed or modified without authorisation, such as advanced authentication mechanisms and encryption tools in addition to monitoring utilities.
Furthermore, cloud-based solutions can be harnessed both preventatively and reactively due to their capability for near real-time threat detection; along with automated patching processes, resource management functions and malware identification capabilities that would not be attainable if relying on traditional onsite methods alone.
As a consequence, organisations gain access to outstanding protection without needing to heavily invest in dedicated hardware or personnel resources. The effectiveness of cloud security resides in its capacity for continuous monitoring and safeguarding across an entire network regardless of its size or complexity. By taking advantage of multiple layers of defence comprising firewalls, segmentation within the network and intrusion prevention systems (IPS), entities can guarantee that all their assets remain secure even if one layer has been infiltrated by an external malevolent agent.
In addition, solutions based on the cloud offer versatile analytic abilities which enable rapid recognition and reaction towards potential threats before they cause any lasting harm. Overall, cloud security represents a vital component for any enterprise wishing to protect themselves from malicious actors hoping to exploit their networks or steal confidential information.
Relationship between Risk Management and Cyber Security
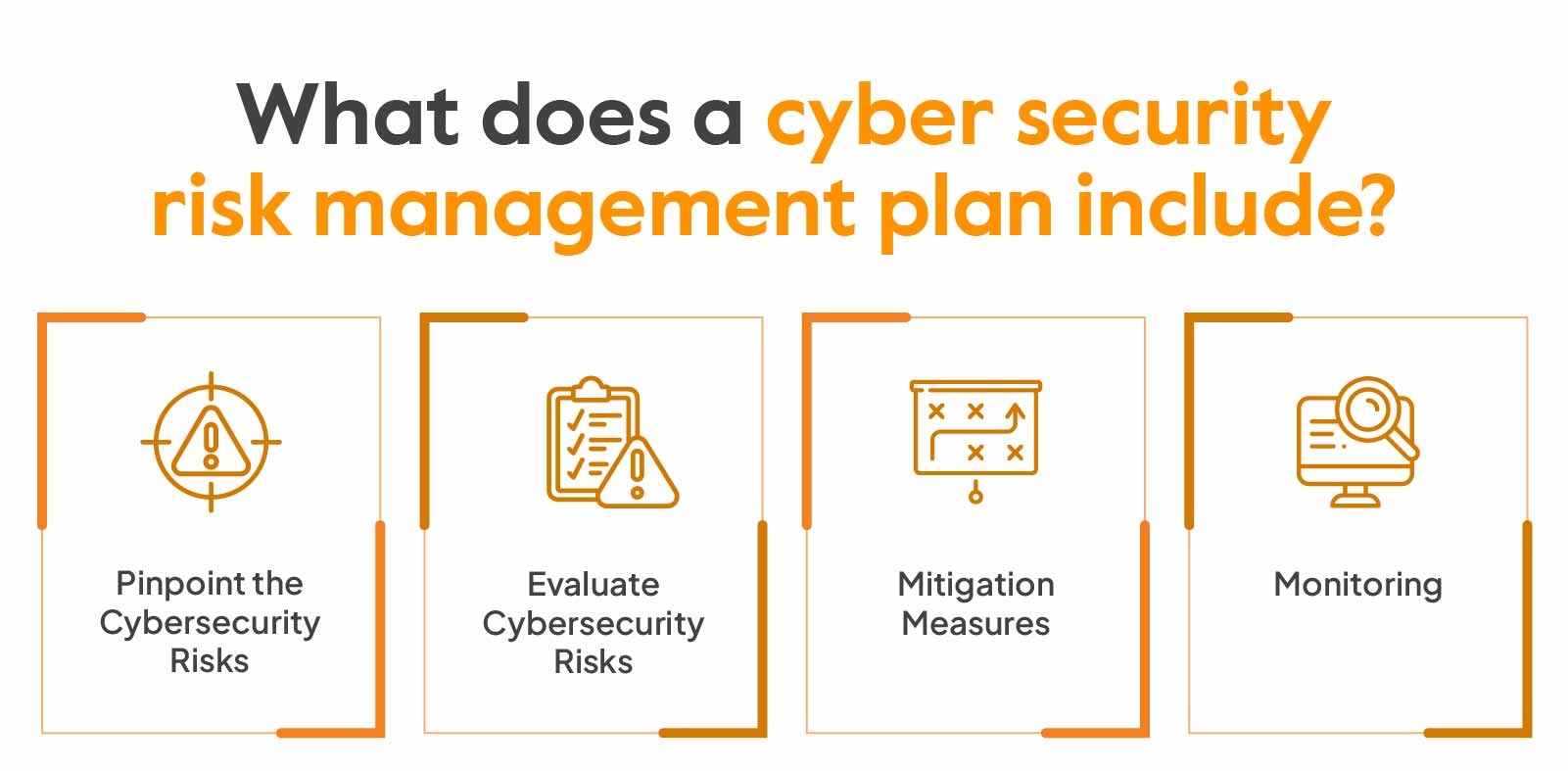
Organisations in the present day are ceaselessly confronted with difficulties maintaining their cyber security while adhering to cost-effective requirements, advancing technologies and ever-shifting regulations. A key element in comprehending how best to competently handle these exposures is understanding the relationship between risk management and cyber security. Risk management is a series of processes that afford an organisation the ability to identify, evaluate, address and monitor risks arising from utilising technology.
Cybersecurity, on the other hand, is defined as the protection of electronic systems, networks and data from unauthorised access or damage utilising methods such as authentication, encryption and monitoring. Organisations need to grasp the relationship between these two concepts since a functioning cybersecurity strategy must be derived from effective risk management.
Risk management can aid organisations in assessing their current state of vulnerability while also providing direction regarding which risks ought to take priority when it comes to being addressed initially or necessitating greater consideration. This information can then further serve towards implementing more successful strategies geared toward mitigating cybersecurity incidents; thus constructing a sturdy foundation for efficient cybersecurity applications.
Moreover, by having an accurate understanding of organisational risks at hand one may plan accordingly so that appropriate defences are prepared should any potential future threat present itself regarding cybersecurity issues.
Evolving World of Cyber Security and the Future of Cloud Security
The development of technology has been responsible for prompting changes in the area of cybersecurity. The increased prevalence of cloud computing and mobile technology has necessitated a transformation within the sphere of online security. As enterprise networks have transferred to hybrid cloud, organisations must possess the capacity to oversee security across multiple layers and gadgets.
It is precisely here that Cloud Security convenes – an array consisting of processes and utilities designed to safeguard data, applications, and services together with infrastructure within a particular cloud surrounding. Cloud Security encompasses aspects such as authentication, access controls, and encryption along with ongoing compliance according to legal stipulations.
Going beyond the scope of traditional solutions that are focused on perimeter-based security, Cloud Security provides comprehensive protection for systems ranging from those located in a physical environment to public clouds. Moreover, utilising analytics and intelligence capabilities allows organisations to gain visibility into user activity at various levels; this is often referred to as ‘Security Analytics’ or ‘Cloud Intelligence’.
Through leveraging these more advanced tools, organisations can detect anomalous behaviour quickly and react promptly when potential threats or incidents arise. Although providing an upgraded level of online safety measures, Cloud Security brings with it additional concerns surrounding privacy which must be taken seriously by any organisation engaging with such services. As companies shift their data and applications away from onsite storage, they are introducing fresh vulnerabilities which could be exploited by malicious actors.
Of particular anxiety is the danger posed by unreliable sources such as third-party service providers or outsourced developers who may not uphold established security protocols or best practices in the industry when managing confidential information. Furthermore, compliance issues with cloud deployments can arise – particularly for businesses functioning within heavily regulated industries like healthcare or finance.
If organisations wish to reap all of the benefits offered through Cloud Security without exposing themselves to any avoidable risks then these predicaments will need to be tackled head-on going forward.
Strategies for Enhancing Data Protection in Cyber Security
The protection of data is an essential aspect of any cybersecurity strategy. This guarantees that private information and corporate data remain safeguarded from malicious actors, identity theft, and other forms of cyber attacks. For the most effective protection for a company’s data, organisations need to take into account the strategies listed below as they build up their cybersecurity plans: The initial step towards any successful policy on protecting data is correctly classifying and sorting all sets of data. This entails comprehending the degree of sensitivity associated with every dataset and applying access controls to restrict those who are authorised adequate access only.
Furthermore, organisations ought to put in place encryption protocols across all their systems so that even if malicious actors were able to procure the data, it would be incomprehensible without the relevant key or password. Moreover, organizations should make use of token-based authentication systems rather than relying on conventional username/password combinations as these present a more substantial challenge for malefactors looking to gain entry. Additionally, organisations must routinely appraise their security infrastructure to uncover any vulnerabilities which may have been taken advantage of by assailants before they can do so.
A thorough vulnerability assessment will incorporate searching for open ports or services, malware scanning, recognising feeble passwords or user access control mechanisms and examining network protocols such as SSL/TLS to identify weaknesses. Moreover, organisations should have a breach response plan in the event of any attack which consists of an incident team who are at all times prepared and pre-ordained steps to answer suitably while securely eradicating compromised data from devices.
Furthermore, there must be policies and procedures put into effect that ensure end users comprehend how confidential information is handled within the organisation. End-user awareness sessions can assist in reducing potential risks whilst instructing personnel on basic cybersecurity principles like robust password practices and phishing scams; this will further enhance an organisation’s ability to protect their sensitive data against malicious entities with minimal interruption to operations running smoothly.
By adhering to these strategies, organizations can better defend their delicate information from malevolent actors simultaneously maintaining operations without disruption.
How Risk Management Contributes to Effective Cyber Security
Risk management forms an integral part of any system for cyber security. It serves as a first line of defence against the possibility of cyber threats, allowing identification and analysis to be made about existing systems with potential weaknesses so that a secure environment can be created for the storage and utilisation of data. This process commences with risk assessment which is conducted by pinpointing and studying likely hazards before determining their chances of arising.
Subsequently, once these possible risks have been identified, it’s essential to develop mitigation plans to either lessen or completely eradicate them; this includes implementation of appropriate protective measures such as firewalls, encryption protocols and authentication processes to prevent unauthorised access towards confidential resources.
Additionally, it is also important that a response plan should exist if there were ever a breach enactable thus enabling the organisation’s capacity to act quickly yet effectively when required. Through the application of these methods, enterprises can verify safeguards within their networks from external attacks whilst upholding efficient cybersecurity practices simultaneously.
Best Practices for Implementing Network Security
It is of paramount importance for any organisation to have network security as part of its cybersecurity infrastructure. It is essential to ensure that business operations flow without hindrance and, more importantly, prevent cyberattacks from taking place. Unfortunately, several organisations are unaware of the best practices when it comes to implementing such measures; ranging from selecting an appropriate firewall through to software updates – however, these guidelines can assist them with protecting themselves against malicious threats.
In determining which type of firewall would be most suitable for their particular needs, organisations must consider what sort and degree of protection they require before making their selection.
Firewalls can be obtained as either hardware or software, with each having its advantages and shortcomings. Generally speaking, a hardware firewall will provide an enhanced level of protection against external dangers such as malicious software; whereas a software firewall may prove to be more efficient in defending internal hazards like phishing emails or malware infections.
It is also significant for organisations to guarantee that they are using the most up-to-date version of their chosen firewall which includes all recent security patches and features. Access control constitutes an essential aspect when it comes to implementing network safety measures. Access controls determine who has permission to access the system and what data or resources they have authorization to view or change.”
Access control regulations ought to be founded on user roles in the organisation so that only those with suitable authorisations can access data which they require for carrying out their duties proficiently. Access control systems should additionally comprise two-factor authentication processes when accessing delicate information, thus providing an additional layer of security against unauthorised attempts at gaining access.
Network monitoring is yet another essential component of network security; it grants administrators observation into activity occurring on the network, thereby making it possible for them to recognise peculiar behaviour speedily.
Network monitoring tools monitor traffic on the network in real time, alerting administrators to any behaviour that might suggest malicious intent or attempts at infiltration by hackers and other cybercriminals. Furthermore, these tools grant administrators the capability of proactively detecting weaknesses in their security posture before they can be taken advantage of by attackers.
Additionally, organisations must invest in user training so that all personnel are cognizant of best practices when it comes to utilising organisational networks securely; this includes not clicking on dubious links within emails or joining unknown devices to a company’s WiFi network. Being aware of potential signs of an attack also facilitates staff being able to quickly report if one is taking place and limit its harm as much as possible. Ultimately, by following such steps organizations will reduce their risk of becoming victims themselves along with protecting data which could potentially fall into malicious hands.
Wrapping Up!
In summation, the employment of appropriate cybersecurity tools for a business can provide important benefits in protecting data and networks. By employing Cloud Security, Data Protection, Network Security and Risk Management solutions businesses are offered assurance that their enterprise is secure against any possible cyber threats. Taking action towards constructing robust cybersecurity structures ahead of time will enable businesses to confront any hazard firmly when it arises.
Are you seeking to take your cybersecurity career up a notch? It would be an error not to enrol in our Cybersecurity Master Program. Our cutting-edge syllabus supplies the hands-on experience and comprehensive abilities required to become a triumphant leader within the realm of cybersecurity.
Consequently, what are you awaiting? Register now to gain access to our lectures led by experts, project-based learning openings, and real-world involvement. We provide flexible payment plans as well as discounts for eligible pupils – so there is no reason why one should fail to take their knowledge of cybersecurity further!
Happy Learning!


