
In the present day and age, technology has integrated into every aspect of our lives. From the moment we wake up to the time we go to bed, we are constantly using technology – our smartphone, laptop or TV. The internet has undeniably changed the way we conduct business. It has made it easier for companies to connect with customers and has allowed businesses to reach a larger audience than ever before. While this dependence on technology can be good, it also comes with a few inherent risks. One of the risks we face is that of cybercrime! And, hence we require cybersecurity measures.
Technology is ever-changing, and the field of cybersecurity is no different. While many individuals and businesses are well-protected against the dangers of the internet, new threats always keep approaching! The following paragraphs will provide the latest cybersecurity measures to help you keep your secrets safe from alarming threats. Therefore, keep reading the blog to know in detail.
What sort of Cyberattacks?
Cyberattacks can take many forms, from viruses and malware to phishing scams and ransomware. As the prevalence of cyber attacks continues to grow, it is more important than ever for individuals and businesses to take the latest cybersecurity measures to protect their secrets. While there are many different ways to do this, some of the most effective involve using strong encryption, hiding data in plain sight, and establishing secure backups. Let us discuss each of these in more detail.
What is the use of Cybersecurity in IT?
Cybersecurity keeps your computer systems and confidential information safe from attacks, damages, or unauthorized access. Cyberattacks are a growing concern as the number of ways to commit them increases.
How to safeguard against cyberattacks?
Cybersecurity measures can be as simple as installing anti-virus software on your computer to more complex solutions such as data encryption. Searching and implementing the latest cybersecurity measures can help protect your organization from costly cyberattacks.
Cybersecurity Measures: Secure Your Secrets now!
Let us face it, we all have secrets. Some may be embarrassing, and some may be incriminating, but we all have them. And, in today’s world, those secrets are under constant threat from hackers, cyber-criminals, and other nefarious characters. The good news is that there are things you can do to protect your secrets from these alarming threats.
Here, via this blog, we will uncover some of the best tricks to help businesses protect their data.
Technology is rapidly growing so are the threats to it. Nobody knows when the next cyber attack will happen, but it is a fact that it will. There are many ways to keep your secrets safe from these alarming threats. And some of the latest cybersecurity measures are-
- Multi-factor Authentication (MFA)
- A Password Manager
- Data Encryption
What is Multi-factor Authentication (MFA) in Cybersecurity?
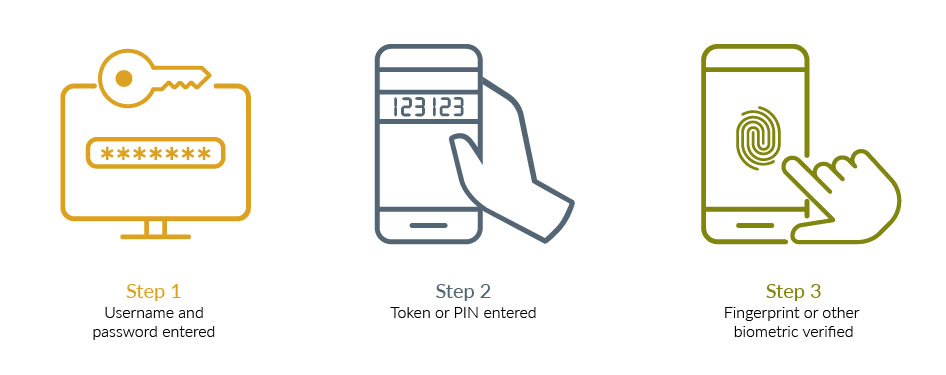
Multi-factor Authentication (MFA), also known as 2FA or two-step verification, is an additional layer of security used to ensure that people trying to gain access to an online account are who they say they are.
It is an important security measure that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction. It is also known as two-factor authentication (2FA) or two-step verification. Two-factor authentication is an effective way to protect against phishing and various kinds of cyberattacks. Phishing is an attack where the attacker tries to trick the user into revealing sensitive information, such as login credentials.
What is the role of a Password Manager in Cybersecurity?
A Password Manager helps the user store and organize passwords. It is software that enables you to generate, store, and retrieve complex passwords, potentially using a master password or other form of biometric authentication.
A good password manager is the first step to online security as it can also help you create stronger passwords making it more difficult for cybercriminals to hack into accounts. Password managers are required if you have multiple online accounts.
What do you understand by Data Encryption?
Data Encryption refers to transforming readable data into an unreadable format as it gets executed using an encryption key, a code which informs the computer how to scramble the data.
Later, the data gets unscrambled using a decryption key, which is the reverse of the encryption key. The encryption and decryption keys are usually different, so even if someone knows the encryption key, they will not be able to decrypt the data without knowing the decryption key.
Are there any real-time examples of cyberattacks?
Alarming threats to cybersecurity are becoming more sophisticated and frequent.
- A recent study by Verizon found that 1 in 131 emails contained malware in 2017, which is a 55% increase over 2016.
- The WannaCry ransomware attack in May of 2017 encrypted the files of more than 200,000 victims in 150 countries and caused billions of dollars in damage.

- NotPetya, another ransomware attack that occurred in June of 2017, caused an estimated $10 billion in damage.

Wrapping Up!
In the 21st century, the world has become a global village and the interconnectedness of economies, societies, and cultures has increased opportunities for businesses and individuals. However, it has also led to increased risks from cyber threats. As they become more reliant on digital technologies, the need for effective cybersecurity measures has never been greater.
No matter how vigilant you are about your cybersecurity, there is always the potential for a data breach. The effects of a data breach can be devastating to both individuals and businesses. A data breach can result in the loss of confidential information, the exposure of trade secrets, and reputation destruction. Cybersecurity measures are constantly evolving, and still be challenging to stay ahead of the latest threats. So, it has become essential for businesses to adopt the latest cybersecurity measures to protect their secrets from alarming threats.


