
Hacking is a very commonly used term nowadays, every here and there we get to hear this term. Be it a tech-friendly person or an amateur, the world is used very frequently. What is Hacking actually? In this blog, we shall read and know more about hacking, its types etc. Our prime focus shall be ethical hacking, here.
The Ultimate Ethical Hacking Roadmap
This article is a roadmap that will help you navigate through the world of Ethical hacking. we shall start with some basic information on what is Ethical Hacking and what it entails. The last part will be about how you can become certified as an Ethical Hacker so that employers can have the confidence in your skillset before hiring you for their company’s most vital projects and clients
Hacking:
Hacking can be defined as the act of compromising digital devices and networks through unauthorised access to an account, system etc. Hacking in simple terms means gaining unauthorised access to data of any kind that is present in a computer or a system etc. Hacking If categorised broadly is of basic two kinds, Ethical Hacking and Unethical Hacking. Although there are many types of hacking like the following:
- White Hat Hackers
- Black Hat Hackers
- Gray Hat Hackers
- Script Kiddies
- Green Hat Hackers
- Blue Hat Hackers
- Red Hat Hackers
- State/ Nation Sponsored Hackers.
In this blog, we shall read about Ethical hacking only, considering all the different aspects of it.
Ethical Hacking
Ethical hacking can be defined as an authorised attempt made in order to gain unauthorised access to a computer system, applications, data etc.
Types of Ethical Hacking :

The fact that anytime, any system, process or website, device etc can be hacked. Nothing actually is Full proof. In order to be able to comprehend how and when a hack could occur, it’s important to understand the psyche behind every malicious attack. To be able to beat them (hackers) it’s important to think like one and march ahead accordingly. Let’s have a look at these types of hacking:
1. Web Application Hacking.
2. System Hacking
3. Web server Hacking
4. Social Engineering
5. Hacking Wireless Networks.
Phases of Ethical Hacking:
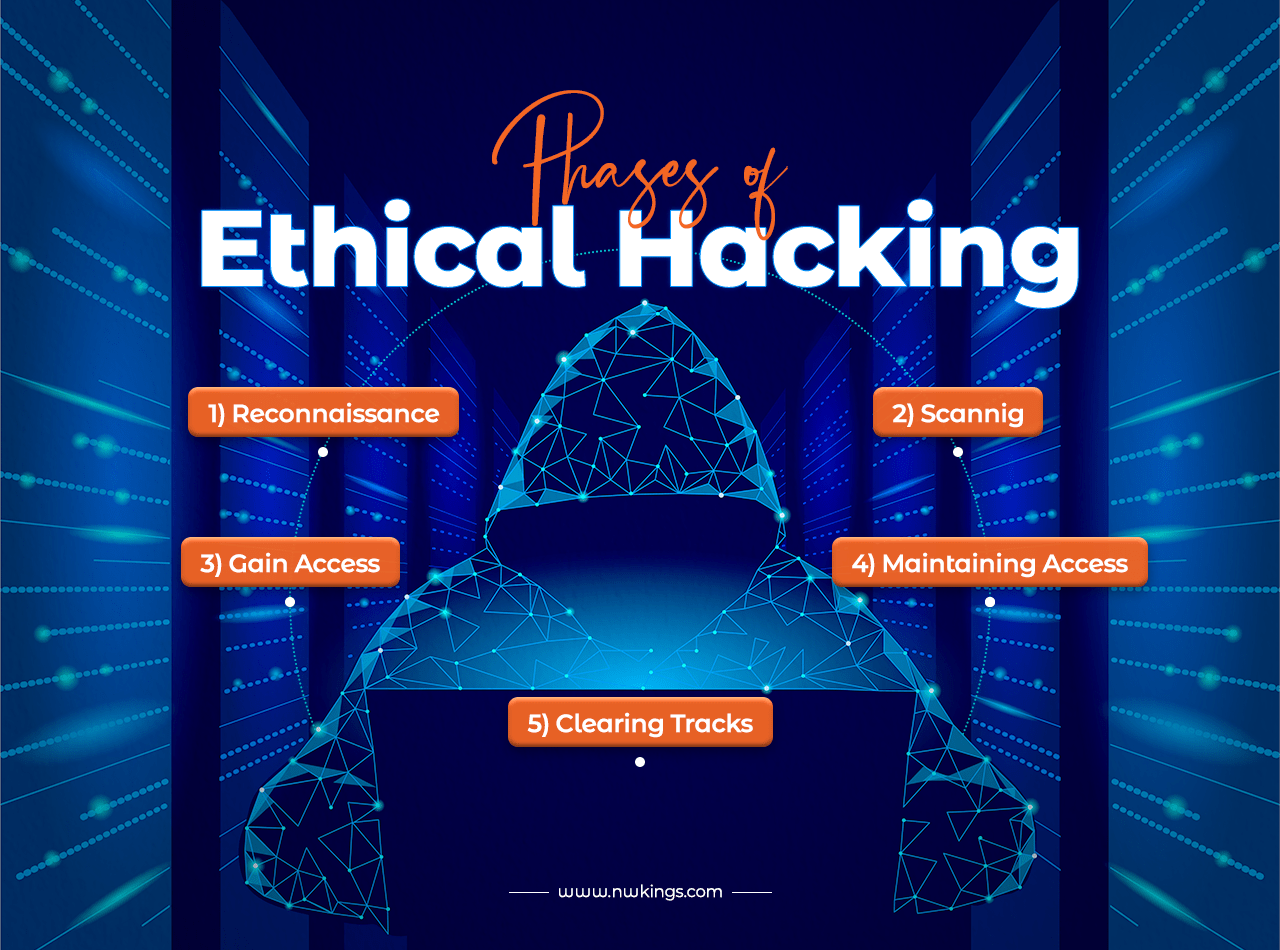
There are phases that occur when trying to hack into a system. The perspectives may vary in intent but the phases are similar. So similar phases are used differently as, the unethical hackers use these for getting into a system to cause damage, of their choice. Whereas ethical hackers use these to protect the system. The phases are as below:
1. Reconnaissance:
This phase is also referred to as the preparatory phase. In this phase, the hacker gathers information about their target system, device, organisation, website etc. This phase has certain stages or phases as well. One of the first ones is Dumpster living.
It is in this phase that the hacker finds useful information like old passwords and the names of employees that are pivotal in any organisation. The hacker then performs an active reconnaissance so as to know how the organisation works. As the next step, the hackers complete the next step, called Footprinting to collect data on the security posture, reducing the focus area such as finding out specific Ip addresses, vulnerabilities es etc. It is beyond this that the hackers draw a map so as to know how they should how the network infrastructure works and be able to break into it.
2. Scanning:
This phase is the time when a hacker tends to identify the easiest and the quickest method to gain access to the network and look for information. There are 3 methods of scanning;
- Pre-attack:
This is the phase where the hacker scans the network for any specific kind of information that is based on all the information that is gathered during the reconnaissance period.
- Port scanning/ sniffing:
In this phase, the main aim is to scan information with the help of a dialler to port scanners vulnerabilities and also other multiple data-gathering equipment.
- Information Extraction:
In this phase, the attackers work to collect information about ports, live machines and also other details for launching the attack.
3. Gain Access:
The hacker gains access to the system, application and network and also they utilise it to organise and exercise their privileges to control the systems that are connected tend to it.
4. Maintaining Access:
In this phase, the hacker tends to secure access to the organisation’s Rootkits and Trojans and further utilise that access to launch additional attacks on the network.
5. Clearing Tracks:
Once the hacker gains access they try and absolutely cover their tracks so as to escape the security personnel. This they facilitate by clearing the cache and cookies, tampering with the log files and also by closing all the ports that are open. This step is utterly crucial because it clears the entire system information, which further makes the hacking a way harder deal to be tracked.
We saw that ethical hacking is a rigorous process and the ones facilitating this are called Ethical Hackers. Let’s read more about them.
Ethical Hacker or White Hat:
Ethical hackers also known as White Hats, are individuals who specialise in security and perform security assessments. The work done by them is helpful for improving any organisation’s, enterprise’s security posture. The work done by white hats is absolutely opposite to that done by malicious hackers. They tend to begin their work always with prior consent from the organisation, or the responsible body.
There are multiple other types of hackers as we saw above. But we shall have a deeper look at the types of ethical hackers.
Benefits of Ethical Hacking:
- There is the most crucial and primary benefit of Ethical Hacking is that it prevents all kinds of data from being misused by all kinds of malicious attackers.
- This is very helpful in discovering vulnerabilities from an attacker’s point of view so all the weak points can be fixed and worked upon and any future damage can be handled efficiently.
- This comes in handy for planning and implementing a secure network that can protect a system against any kind of security breach.
- Yet another very important benefit of having ethical hacking is also assisting in the matters of national security, as this helps in defending national security by protecting data from any resource that can be harmful, for instance, terrorists etc.
- It is also beneficial in helping companies, organisations etc, gain the trust of clients etc by ensuring the protection of their work, data etc.
- It also comes as a savior while protecting the networks with real-world assessments.
Limitations of Ethical Hacking:
As every prospect has two aspects, Ethical Hacking is no different. There also are certain limitations or so to say the disadvantages of Ethical Hacking:
- This procedure may corrupt the files or data of importance in any organisation.
- Often ethical hackers can be seen as an additional expenditure of the company.
- There always can be a rift while trusting them as they could misuse the access to information etc.
- The process of ethical hacking can often hamper the system operation or can elevate the risk of system operation being affected.
The Scope of Ethical Hacking:
There is still a lot of debate around the term Hacking and when we talk about Ethical Hacking a lot of people are still foreign to this concept. They view Hacking only in one light; the process where a person breaks into any other person’s system, device etc to damage them, their reputation or for that matter for ransom. But people who know, know that this field of network security is progressively advancing and growing manifold at once. Data is unarguably the currency, so its protection is of prime concern.
Hence, Ethical Hacking will continue to grow, in the near future as we. With Artificial Intelligence also growing at a fast pace, the need for Ethical hacking will also witness a surge. The number of jobs being opened up in this field is also massive. The scope, on the whole, is huge and the best part is it shall not be fading away anytime soon in the foreseeable future.
How can you become an Ethical Hacker?
We discussed how there is a vast scope, what’s the point if this information can not be utilised? It’s time you make big in the field that most definitely won’t see dawn for a long time. To utilise the benefits and become the need of all organisations, enterprises etc, becoming an Ethical Hacker seems like the smartest way. Let’s now read into how one can become an ethical hacker. There are many Ethical Hacking certifications one should take:
- CEH: Certified Ethical Hacker
- CEH (Practical)
- Certified Ethical Hacker (Master)
CEH: Certified Ethical Hacker
The Certified Ethical Hacker certification stands, as proof of an individual’s in-depth understanding of ethical hacking phases, and their types, to have a detailed knowledge of preventive measures, one must know how to combat damage.
CEH (Practical)
Certified Ethical Hacker, is a rigorous exam that lasts for about 6 hours. It needs for an individual to demonstrate the application of ethical hacking techniques, he/she has learnt. For instance, the aspirant needs to demonstrate the application of threat vector identification.
Certified Ethical Hacker (Master)
This is the most advanced level of CEH, as the two former certifications prepare a person, acquaint them with everything, make them practice, and prove their learning respectively. This is a final earning in their learning.

