
Why cybersecurity is important and what are the types of cyber threats – is a must-know for all cyber enthusiasts. Cyberattacks are on the rise, and the numbers are staggering. We will explore recent statistics that highlight the scale and frequency of these attacks, underscoring the need for robust cybersecurity measures.
This blog aims to explore the pivotal role of cybersecurity in our modern world. We will delve into the growing threat landscape, the consequences of neglecting cybersecurity, and the critical importance of protecting data and assets. We will also discuss cybersecurity best practices, the challenges posed by the Internet of Things (IoT), emerging trends in the field, and government and international initiatives to combat cyber threats. By the end, you will understand why cybersecurity is not just an option but a necessity.
What Cybersecurity is important in the digital age?

As our lives become more intertwined with technology, the importance of cybersecurity cannot be overstated. Every aspect of our personal, professional, and even national security depends on the strength of our digital defences. The ramifications of a cybersecurity breach are far-reaching, affecting individuals, businesses, and governments.
In an increasingly interconnected and digitized world, cybersecurity refers to the practice of protecting electronic systems, networks, and data from theft, damage, or unauthorized access. It encompasses a wide range of measures, technologies, and strategies designed to safeguard information and maintain the integrity and confidentiality of digital assets.
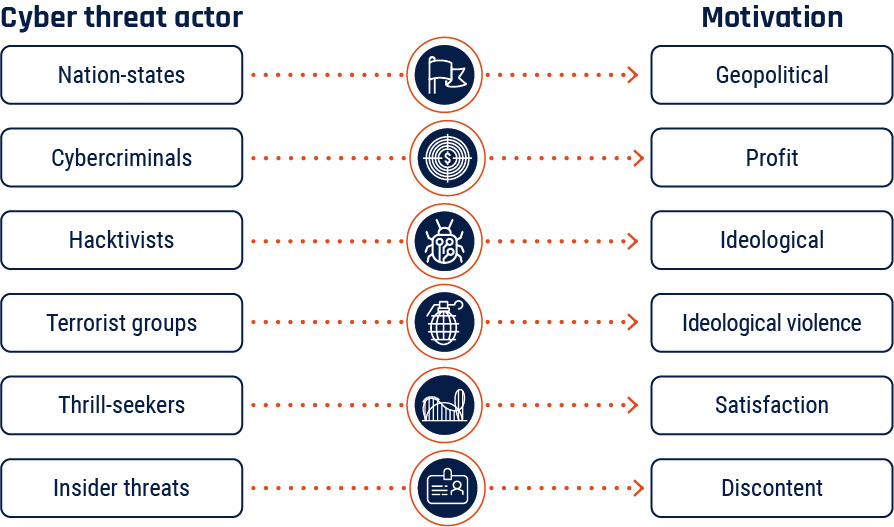
What are the types of cyber threats?

Diverse and evolving, cyber threats come in many forms. From malware and ransomware to phishing and social engineering, we will examine the various methods employed by cybercriminals to exploit vulnerabilities.
The top reported cyber threats are as follows-
Malware
Malicious software, such as viruses, worms, Trojans, ransomware, and spyware, that infects a computer or network to cause harm or steal information.
Phishing
Deceptive emails, websites, or messages that impersonate trusted entities to trick individuals into revealing sensitive information like passwords or credit card numbers.
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
Attackers overwhelm a network, system, or website with traffic, rendering it unavailable for legitimate users.
Ransomware
Malware that encrypts a victim’s data and demands a ransom for the decryption key, often leading to data loss or financial extortion.
Insider Threats
Malicious activities or data breaches are initiated by employees, contractors, or other trusted individuals within an organization.
Man-in-the-Middle (MitM) Attacks
Hackers intercept communication between two parties, eavesdropping or altering messages without their knowledge.
Zero-Day Exploits
Attacks that target software vulnerabilities that are not yet known to the software vendor, making them difficult to defend against.
SQL Injection
Attackers manipulate input fields to execute malicious SQL queries in a database, potentially gaining unauthorized access to or control over the database.
Social Engineering
Psychological manipulation of individuals to divulge confidential information, like passwords, through techniques like pretexting, baiting, or tailgating.
IoT (Internet of Things) Vulnerabilities
Security weaknesses in connected devices can be exploited to gain unauthorized access, control, or even disrupt critical infrastructure.
What are the consequences of neglecting Cybersecurity?

The consequences of neglecting cybersecurity in IT are as follows-
Financial Implications
Neglecting cybersecurity can lead to significant financial losses, both for individuals and organizations. We’ll explore the direct and indirect costs of cyberattacks, including the expenses of breach recovery and the loss of revenue.
Reputational Damage
The damage to a brand’s reputation following a cyber incident can be long-lasting. We’ll look at examples of companies that have struggled to recover from security breaches and the impact on customer trust.
Legal and Regulatory Consequences
In an increasingly regulated digital landscape, we’ll discuss the legal implications of cybersecurity negligence, including potential fines and penalties imposed on companies that fail to protect sensitive data.
Personal Privacy Concerns
For individuals, cyberattacks can lead to personal privacy violations, identity theft, and emotional distress. We’ll examine the emotional toll of having one’s personal information compromised.
How to protect your data and assets?
The ways to protect your data and assets are as follows-
Personal Data Protection
- Strong Passwords: Use complex, unique passwords for online accounts. Employ a password manager to keep track of them.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security to your accounts.
- Encryption: Encrypt sensitive data on your devices, such as laptops and smartphones.
- Regular Backups: Back up your important data regularly to an external device or cloud storage.
- Email Security: Be cautious with email attachments and links, and avoid sharing sensitive information via email.
Financial Assets
- Online Banking Security: Use strong, unique passwords for your online banking accounts and monitor transactions regularly.
- Credit Monitoring: Sign up for credit monitoring services to detect unusual activity and potential identity theft.
- Secure Wi-Fi: Protect your home network with a strong password and use WPA3 encryption for Wi-Fi security.
- Be Cautious Online: Avoid sharing financial information on suspicious websites, and double-check URLs for legitimacy.
Protecting Intellectual Property
- Patents and Copyrights: Register your intellectual property to establish legal protections.
- Non-disclosure Agreements (NDAs): Use NDAs when sharing your intellectual property with others.
- Secure Storage: Keep digital intellectual property in secure, encrypted storage and physical copies in a safe place.
Home Security
- Home Security Systems: Install security systems, cameras, and smart locks to protect your home.
- Safes: Use safes to secure valuable assets and important documents.
- Neighbourhood Watch: Join or initiate a neighbourhood watch program to enhance community security.
Personal Security:
- Awareness: Be vigilant and aware of your surroundings, especially in unfamiliar or high-crime areas.
- Self-Defence Training: Consider self-defence training to protect yourself in emergencies.
- Emergency Contacts: Keep a list of emergency contacts and have a safety plan in place.
Protecting Business Data and Assets:
- Firewall and Intrusion Detection: Implement firewalls and intrusion detection systems to protect your network.
- Access Controls: Limit access to sensitive data and systems to authorized personnel.
- Employee Training: Train employees on security best practices and conduct security awareness programs.
- Business Continuity Plan: Develop a business continuity plan to ensure operations can continue in the event of a disaster.
Protecting Government and Critical Infrastructure:
- National Cybersecurity Strategy: Develop and implement a comprehensive national cybersecurity strategy.
- Critical Infrastructure Protection: Strengthen the security of essential infrastructure, such as power grids and water supply.
- International Collaboration: Cooperate with other governments to share threat intelligence and respond to global cyber threats.
What is the role of cybersecurity in IT?

The role of cybersecurity in IT are as follows-
- Cybersecurity Analyst: Responsible for monitoring, detecting, and responding to security threats and incidents.
- Network Security Engineer: Focuses on securing network infrastructure, including firewalls, routers, and switches.
- Information Security Manager: Oversees an organization’s overall security program, including policy development and compliance.
- Incident Responder: Investigates security incidents, identifies the root cause, and initiates incident response procedures.
- Security Consultant: Provides expert advice and recommendations for enhancing an organization’s security posture.
- Security Architect: Designs and implements secure systems and applications, ensuring they meet industry standards and best practices.
- Penetration Tester (Ethical Hacker): Conducts authorized attempts to exploit vulnerabilities in systems, helping organizations identify weaknesses.
- Security Operations Center (SOC) Analyst: Monitors security alerts and incidents, responding to and mitigating threats in real time.
- Security Software Developer: Creates security software, tools, and applications to protect systems and data.
- Security Compliance Officer: Ensures that an organization complies with relevant security regulations and standards, such as GDPR or HIPAA.
- Security Awareness Trainer: Educates employees and users on security best practices and promotes a security-conscious culture.
- Vulnerability Assessment Analyst: Identifies and assesses potential security vulnerabilities in an organization’s systems and applications.
- Cloud Security Engineer: Specializes in securing cloud-based services and infrastructure, such as AWS or Azure.
- Data Protection Officer: Ensures the protection of sensitive data and compliance with data protection regulations like GDPR.
- Mobile Security Specialist: Focuses on securing mobile devices and applications, given the increasing use of mobile technology.
- Forensic Analyst: Investigates cybercrimes, collecting and analyzing digital evidence for legal purposes.
- Security Compliance Auditor: Evaluates an organization’s security controls and practices to assess compliance with established standards.
- Security Operations Manager: Manages the day-to-day operations of a Security Operations Center, overseeing SOC analysts and incident response teams.
- Endpoint Security Administrator: Ensures the security of individual devices, such as laptops and smartphones, by deploying endpoint security solutions.
- Disaster Recovery Specialist: Develops and maintains plans to recover data and systems in case of a security breach or catastrophic event.
What are the best cybersecurity practices?

The best cybersecurity practices in IT are as follows-
Password Hygiene
Elaborate on creating strong, unique passwords and the importance of changing them regularly.
Regular Software Updates
Emphasize the significance of keeping operating systems and software up to date to patch vulnerabilities.
Security Awareness Training
Discuss the benefits of educating employees and individuals about cybersecurity best practices.
Least Privilege Principle
Explain the concept of granting the minimum level of access or permissions necessary to perform a job or function.
What are the emerging Cybersecurity trends in IT?

The emerging cybersecurity trends in IT are as follows-
- Artificial Intelligence (AI) and Machine Learning in Cybersecurity: Describe how AI is being used to detect and respond to threats.
- Zero Trust Security: Explain the shift towards a model where trust is never assumed, and verification is a constant requirement.
- Quantum Computing Threats: Discuss the potential threat posed by quantum computers to current encryption methods.
- Threat Intelligence Sharing: Explore the trend of organizations and nations sharing threat intelligence to strengthen collective defences.
Wrapping Up!
Cybersecurity is a vital necessity in the digital age. As threats evolve, neglecting them leads to serious consequences. Understanding various threats is crucial for individuals and organizations. Best practices and emerging trends like AI, zero trust, and threat sharing are key. Cybersecurity pros are indispensable in our interconnected world. It’s a shared, ever-adapting responsibility.
Happy Learning!


