
Undoubtedly, technology is evolving day by day, and, hence, the risk of malicious attacks is increasing simultaneously. Since the number of hackers and attacks is rapidly growing, IT is looking for plenty of employees in the Cyber Security domain.
Consequently, the market for Cyber Security experts is expanding and providing secure usage to diverse networks. They ensure complete security of the networks and servers at their end. But, technology comes with both pros and cons. Thus, securing our networks and servers is not solely their responsibility. We are equally responsible for keeping our data and information secure.
Sadly, no one can predict or guarantee if the device, network, or server is secure for life! Technology is prone to hacking – Yes, it is true! Innumerable Cyberattacks occur to hack, steal, and violate confidential data and information that further get sold for money or sometimes used for blackmailing purposes. Therefore, Cyber Security is mandatory in IT.
But, various Cybersecurity myths and facts confuse people regarding Cyber Security leading to misconceptions regarding the domain. Here, in the blog, we will solve your confusion by differentiating between the myths and facts about Cyber Security. So, keep reading to learn more.
What is Cyber Security?
Cyber Security refers to guarding a system, network, and program from hostile invasions. These attacks target confidential data, extort money, and interrupt enterprise operations.
Since everyone counts on infrastructures like banks, clinics, academies, and other private or state offices, there is consistently a risk of data theft. Therefore, such infrastructures require a Cyber Security expert to ensure critical and confidential information is safe.
We notice people have differentiated Cybersecurity myths and facts according to their preferences. We will now discuss actual and genuine facts and myths regarding Cyber Security.
MOST COMMON CYBERSECURITY MYTHS
1. | Antivirus software is sufficient to guard the enterprise. |
2. | Passwords will preserve everything. |
3. | We will learn immediately if the systems are compromised. |
4. | Small Scale Businesses do not require to bother about Cyber Security. |
5. | Too much security reduces efficiency. |
Now, We Will Discuss the Cybersecurity Myths in Detail!
1. Cyber Security is just regarding technology. Is it?
CYBER SECURITY = TECHNOLOGY + PEOPLE |
Since technology is a crucial element of Cyber Security, it holds to individuals and systems; technology can’t safeguard an organization from malicious online hazards alone. Hence, it is MYTH.
2. Small Scale Businesses do not require to bother about Cyber Security. Do they?

- The image depicts the rate of cyber raids made on small-scale businesses in different countries.
Small Scale Businesses are at more elevated risk of Cyberattacks than Large Scale Businesses as they lack resources and expert direction to defend their networks against malicious hazards. Hence, it is MYTH.
3. Cyber Security is too costly. Is it?
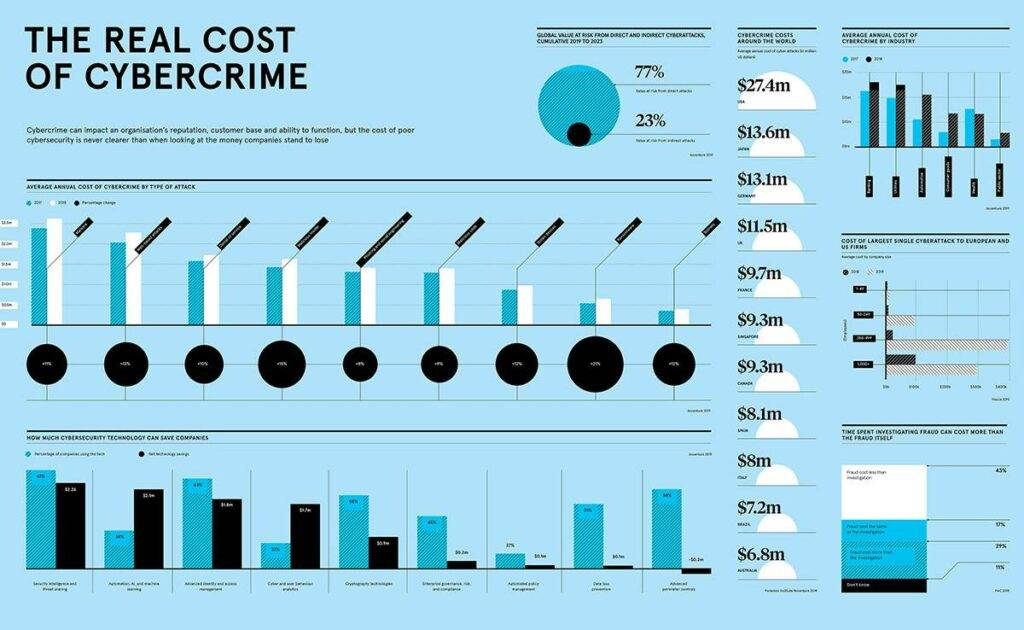
- The image depicts the actual cost of cybercrime and the cost required to fix the damage and install the CyberSecurity services.
CyberSecurity is expensive – Yes, that’s correct! But the expense of not enforcing any security extents is higher. And in addition to the monetary outlay, it comprises other expenditures for data violations, mislaid revenue, reputation deterioration, and legal expenses. Hence, it is MYTH.
4. Only the IT department is accountable for Cyber Security. Is it?
CYBERSECURITY = IT DEPARTMENT + PEOPLE |
IT department is indulged and acts as an accountable force for Cybersecurity; it’s not utterly a ward of IT in any way possible. All other divisions are equally liable for the takeaways and must act as IT to safeguard themselves against online dangers. Hence, it is MYTH.
5. CyberSecurity is too complicated. Is it?

- The image depicts the complexity of a Cybersecurity employee.
Cybersecurity is complicated as it requires precise strategies. Multiple resources are available to assist associations in understanding and executing crucial safety benchmarks. Hence, it is MYTH.
6. Password will preserve everything. Will it?
PASSWORD ≠ COMPLETE SECURITY |
Associations usually believe standard passwords are adequately strong to keep the business secure. However, such practices are just the beginning. An efficient security system comes with multi-layered protection. They should enforce two-factor authentication and data access monitoring.
Employees often assume a password keeps the Wi-Fi network secure at an organization. Passwords only limit access to a network; users in the network can access confidential data to be transmitted. Thus, employees must use Virtual Private Networks (VPNs) to safeguard connections. Hence, it is MYTH.
7. Antivirus software is sufficient to guard the enterprise. Is it?

The security toolkit comprises Endpoint, Firewall, Networks, Email, backup, and disaster retrieval tools that are mandatory to alleviate possible incidents. The software is compulsory to keep the network and systems secure. But technology alone can not protect the entire IT infrastructure from cyber risks.
It only provides one entry point into the system; hackers evade antivirus softwares and penetrate networks. Thus, having such software, hackers can still make an attack. Therefore, antivirus software can only guard you from a set of cyber threats, not from all sorts of cyber threats. Hence, it is MYTH.
8. We only ought to shield against hackers. Do we?
CYBER THREAT = HACKERS = OUTSIDERS + INSIDERS |
While hackers pose an immense threat to businesses, one can not neglect the possibility of vicious insiders. Equally, an intruder or employee having access to confidential data could voluntarily rob or transmit it. Shutting down credentials to core systems assuring fewer employees access them, can help protect against these attacks. Hence, it is MYTH.


- The images depict the following news: One of the most highly publicized accidental breaches was a Heathrow Airport staff member losing a USB stick carrying sensitive data. Fortunately, the person who found it handed it in rather than using it maliciously. However, the company was still fined 120,000 pounds (around $156,000) for failing data protection.
9. Remaining updated with industry constraints is sufficient to preserve us. Is it?
Remaining updated with industry constraints is sufficient for accomplishing business, establishing trust, and bypassing legal matters. But being compliant does not necessarily imply you are safe. Associations must evaluate if the constraints are substantial enough and scope obscures all the vital data. Hence, it is MYTH.
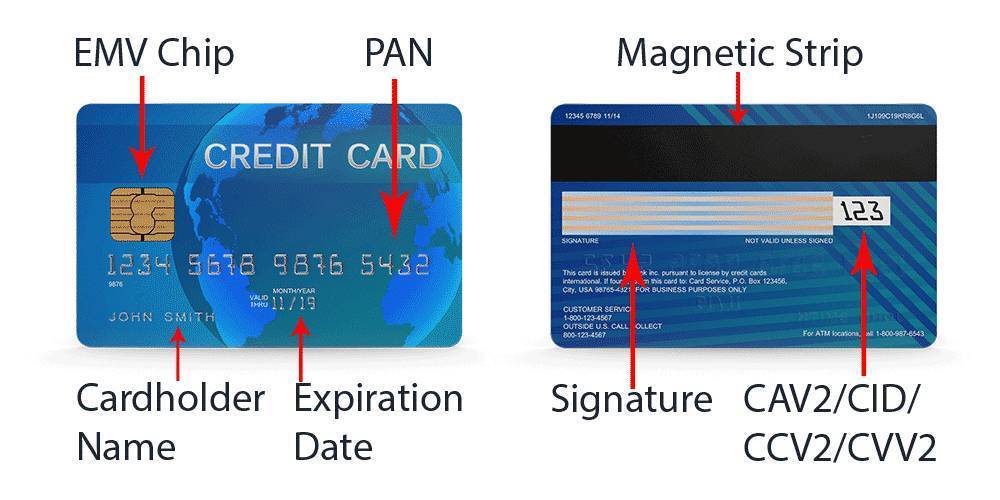
- The image depicts the following news: PCI compliance focuses on securing credit card data, often excluding the other valuable information handled by the organization.
10. A third-party security provider will safeguard everything. Will it?

- The image depicts what threats third-party security providers put into an enterprise.
A Cybersecurity enterprise obligates enforcing and examining security procedures to keep it secure; it is essential to comprehend the cyber risks to an organization and how they get handled. A third-party security provider records the safety roles, commitments, capacities, and violations for maintaining company security. But they can not protect it alone, as there remains a possibility of some cyberattack. Hence, it is MYTH.
11. Cyber threats only arrive from external factors. Do they?
CYBER THREATS = INSIDER ATTACKS + OUTSIDER ATTACKS |
Undoubtedly, foreign threats are a concern of every enterprise and must deal with comprehension. Therefore, native threats are equally destructive. Employee carelessness, insensibility, and hostile conduct frequently create inside dangers and a high-security menace than foreign threats. Hence, it is MYTH.
12. We only require to secure internet-facing applications. Do we?
Associations must secure internet-facing applications as the entire IT system might get compromised if an employee uses an infected flash drive or opens unknown links and emails. Thus, associations should have sufficient authority to avert and handle native menaces. Hence, it is MYTH.
13. We conduct penetration trials regularly. Do they help?
CYBERSECURITY ≠ ONLY PENETRATION TESTS |
Numerous businesses believe they can diminish the risk by conducting penetration trials regularly. But a penetration test is futile as it only benefits for a short time. The organization should address and fix the vulnerabilities and loopholes in the security stances encountered during the trial. Hence, it is MYTH.
14. We have infused refined security mechanisms; we are safe. Are we?
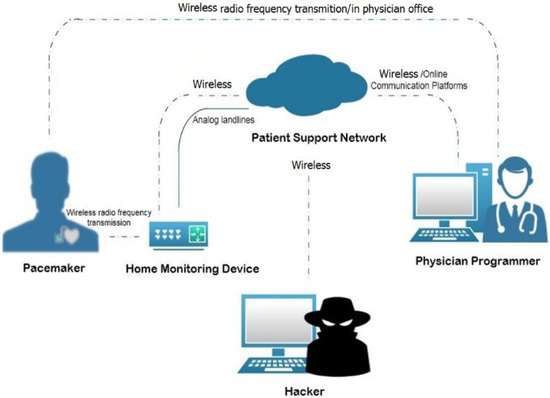
- The image depicts how a hacker can attack even the refined versions of Cybersecurity Networks.
Associations generally misinterpret financing in high-end security tools and keys, helping them to build an indestructible shield between networks and cyber-criminals. Cultured Cybersecurity solutions are essential to keep businesses secure, but they do not cover everything.
They are effective only if configured, observed, sustained, and merged with prevailing safety procedures but partially. Hence, it is MYTH.
15. We have acquired complete CyberSecurity. Have we?

- The image depicts nothing like complete Cybersecurity exists as new methods come into force every day.
Cybersecurity is an endless revolution rather than an effect. Fresh, creative, and refined cyberattacks ripen with time, putting the alliance at constant risk. Thus, continuous monitoring of crucial assets, conducting inner audits and reviewing safety guidelines is mandatory. The enterprise must implant Cybersecurity techniques into business procedures and sponsor ongoing updates. Still, the risk is there. Hence, it is MYTH.
16. We will learn immediately if the systems are compromised. Will we?

Cyberattacks are better hidden. It could be months or years until one finds out the computer is infected and breached. Malware and other safety menaces are even more challenging to detect. As cybercriminals evolve, the guarding shields must evolve to keep an eye on anything suspicious. Inconspicuous compromises could be creeping. Hence, it is MYTH.

- The image depicts the following news: Take Marriott Hotels. They were victims of a cyberattack in 2014 that stole customer names, contact information, and passport details. It took four years for them to notice they had been compromised and cost them £18.4m in fines.
17. Cybersecurity experts believe in Bring Your Own Device (BYOD) policy is secure. Is it?

Bring Your Own Device policy has multiple benefits as employees feel effective and capable while operating it. Allowing BYOD unplugs business up to a possible threat each time an employee links a device. Hence, it is MYTH.
18. Too much security reduces efficiency. Does it?

Increased security makes it challenging for employees to access what they need, not just for hackers. Rigid approaches like routine surveillance and access management delay productivity at work. Hence, it is MYTH.
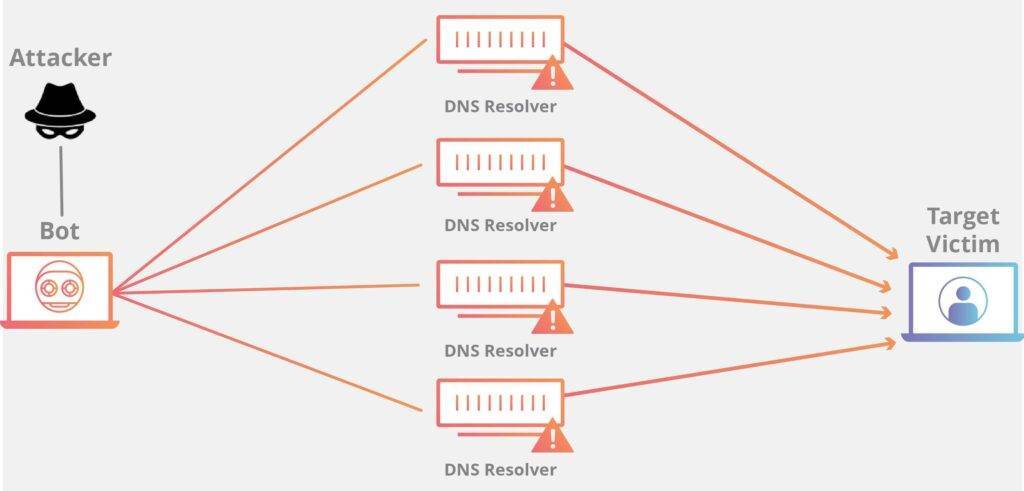
- The image depicts the following news: A successful attack like DDoS attack ransomware can bring your business to a standstill. Employees might not access important files, networks, and information after an attack.
MOST COMMON FACTS REGARDING CYBERSECURITY
1. | A business is always prone to hacking and hostile invasions. |
2. | All public Wi-Fi can be hacked, even with a password. |
3. | Every employee is obliged to keep the organization safe. |
4. | Strong passwords can not ensure complete security. |
5. | Months or years can pass learning the system is compromised. |
Now, We Will Discuss The Facts Regarding Cybersecurity In Detail!
1. Enhanced CyberSecurity can expand output. Can it?

Cybersecurity method employs security devices having a built-in safety element integrated into a system. It also influences progressive tech brilliance and analytics for real-time detection and alleviation of menaces allowing developers to focus on enhancing productivity. Hence, it is a FACT.
2. Cyberattacks can come from somebody you know. Can they?
- This image depicts that cyber attacks can come from anyone, i.e., an insider or an intruder.
Employ a mixture of behavioural analytics and permit the administration to minimize insider hazards. Also, execute security awareness training sessions to enlighten employees regarding the risks of insider threats and methods to detect them. Hence, it is a FACT.
3. A business is always prone to hacking and hostile invasions. Is it?

Hackers don’t distinguish their targets. Therefore, do not let the size of the business decide how vital or secure data and assets are! Hence, it is a FACT.
4. Antivirus softwares can only shield from a set of identified cyber attacks, not from all the emerging cyber hazards. Can they?
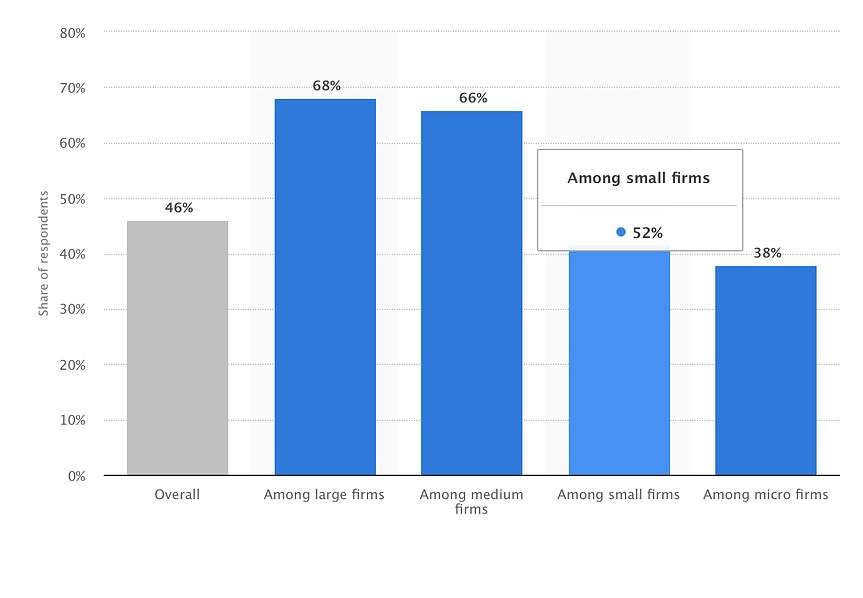
- The image depicts the rate of cyber raids made on different businesses even after they had installed Antivirus.
Deploying an all-encompassing safety resolution – Web Application Firewall – antivirus software scans dangers and provides end-to-end protection 24*7. Hence, it is a FACT.
5. The expenditure of a sound Cybersecurity solution is zero compared to the price of a triumphant attack. Is it?

There are numerous preventive measures with zero additional cost to secure business, such as strong passwords, two-factor authentication, entry administration, and employee training. They might seem expensive, but the cost to repair the damage caused by malicious attacks is beyond imagination. Hence, it is a FACT.
6. You can become the next target. Can you?

Generate a sound security technique that enables the team to identify weaknesses and reduce invasion attempts before causing any notable damage. Cyber menaces and hacking mechanisms are constantly evolving to become sophisticated and undetectable daily. And any confidential information is a possible prey for the attack. Hence, it is a FACT.
7. There is nothing like absolute or excellent Cybersecurity against attacks. Is there any?

Inspecting security approaches, conducting security audits, scanning crucial assets continually, and financing the forthcoming updates in security criteria can not completely secure a firm from cyberattacks. Hence, it is a FACT.
8. Strong passwords can not ensure complete security. Can they?

No password is 100% secure. No matter how many digits or special characters one uses, there is consistently a chance that they can be cracked or revealed in some way. Thus, it is necessary to use uncommon passwords and two-factor authentication to keep the network and devices secure. Hence, it is a FACT.
9. Insider hazards are equally dangerous and require similar awareness as external threats. Do they?
CYBER THREATS = INNER THREAT + OUTSIDER THREAT |
Most cyber-attacks occur because of insiders, says research. A dissatisfied employee, an ex-employee with resentment, or an immature user on the network can grant admission to the data resulting in data violation. Thus, it is mandatory to train employees by teaching them about cyber threats beforehand. Hence, it is a FACT.
10. Every employee is obliged to keep the organization safe. Is it?

The accountability lies on the shoulders of everyone regarding Cybersecurity. Lack of training might lead them to download vicious data via emails or unsafe websites. There must be easy-to-understand training and transparent approaches concerning Cybersecurity. Hence, it is a FACT.
11. All public Wi-Fi can be hacked, even with a password. Really?
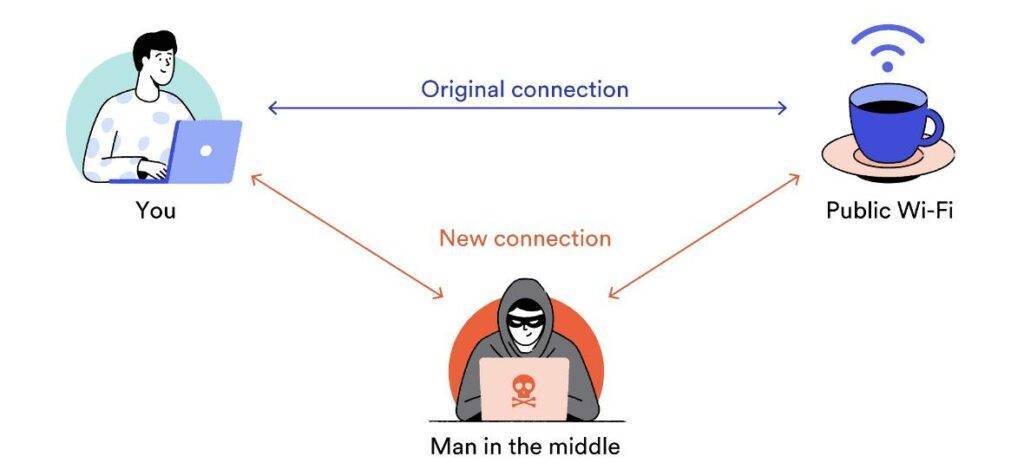
While using public Wi-Fi, you are a possible prey for a man-in-the-middle invasion. It is where a hacker blocks the moving data between two participants. It is more concerning when one sends confidential or economic information. Hence, it is a FACT.
12. Months or years can pass learning the system is compromised. Seriously?

Cyberattacks are occurring more often these days. It could be months or years until one finds out the computer is infected and breached. Malware and other safety menaces are even more challenging to detect. As cybercriminals evolve, the guarding shields must evolve to keep an eye on anything suspicious. Hence, it is a FACT.
13. All personal devices - smartphones, laptops, and wearables - can put the network at risk. Do they?
It only takes a weak link to fetch, disable, and shut the entire network. Thus, one must ensure all users cling to Cybersecurity approaches before using personal devices. Hence, it is a FACT.
14. One must always adopt the latest Cybersecurity techniques as new threats appear. Seriously?

Adopting the latest Cybersecurity constraints is sufficient for accomplishing business, establishing trust, and bypassing legal matters. But being compliant does not necessarily imply you are safe. Associations must evaluate if the constraints are substantial enough and scope obscures all the vital data. Hence, it is a FACT.
15. Safety tools must properly configure, observe, and incorporate comprehensive security prospects. Really?

Associations generally misinterpret financing in high-end security tools and keys, helping them to build an indestructible shield between networks and cyber-criminals. Cultured Cybersecurity solutions are essential to keep businesses secure, but they do not cover everything.
They are effective only if configured, observed, sustained, and merged with prevailing safety procedures but partially. Hence, it is a FACT.
16. Penetration tests operate when the vulnerabilities get rectified on time. Seriously?

Numerous businesses believe they can diminish the risk by conducting penetration trials regularly. But a penetration test is futile as it only benefits for a short time. The organization should address and fix the vulnerabilities and loopholes in the security stances encountered during the trial. Thus, penetration tests operate when the vulnerabilities get rectified on time. Hence, it is a FACT.
17. One has a legal and moral obligation to secure critical acquisitions despite partnering with a security provider. Really?
CYBERSECURITY = SECURITY PROVIDER + INDIVIDUAL LEVEL |
A Cybersecurity enterprise obligates enforcing and examining security procedures to keep it secure; it is essential to comprehend the cyber risks to an organization and how they get handled. A third-party security provider records the safety roles, commitments, capacities, and violations for maintaining company security. But they can not protect it alone, as there remains a possibility of some cyberattack. Thus, despite partnering with a security provider, one has a legal and moral obligation to secure critical acquisitions. Hence, it is a FACT.
18. Fresh and sophisticated cyberattacks ripen daily. Seriously?

One can never be certain regarding Cybersecurity as the technology is progressing with time. The endless expansion of technology means new dangers are appearing each day. Thus, the Cybersecurity system could be entirely extinct in future. One must adapt new Cybersecurity procedures and techniques to evade any casualties as fresh and sophisticated cyberattacks ripen daily. Hence, it is a FACT.
Wrapping Up!
One needs to stop considering the Cybersecurity myths and upgrade the security prospects in the system. One is always at threat of getting attacked in the digital realm. The facts can help in understanding the real threats under Cybersecurity.
Since numerous courses are available under the Cybersecurity domain, one can enroll and enjoy the benefits of IT in deep. Join today!
GOOD LUCK!
NOTE: Since you have read the blog till the end, we have a special offer for you. Now learn the Basics of Firewall worth INR 4,999/- directly from professional Engineers by paying INR Zero.


