Multi-Access Year Deal
Get 55+ courses now at the best price ever! Use Code: MULTIYEAR
Network Specialist Master Program
About Course
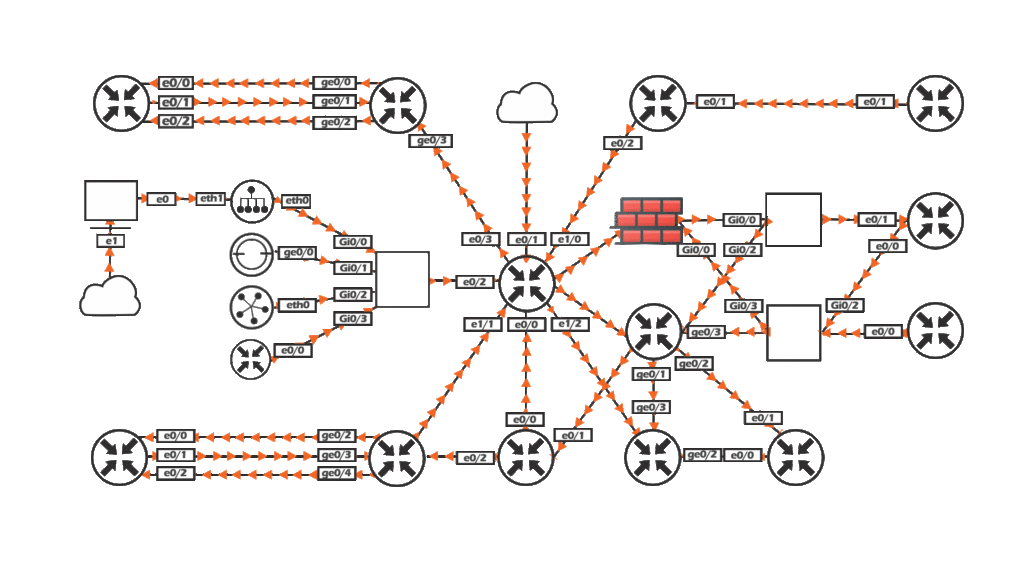
The Network Specialist Master Program is designed to cater for students with CCNP ENCOR and CCNP ENARSI knowledge with advanced skills in SD-WAN and Palo Alto firewalls, empowering you to excel in modern network architecture and security.
The course duration is 6-8 months with 100+ hours of live class and 24/7 lab access.
This Combo Includes



Join Now to win Additional Courses worth $1500 as a Scholarship! ↘
CCNA
CompTIA A+
TAC Engineer
Cisco ASA Firewall
Juniper JNCIA
CompTIA N+
CCNP Service Provider
CompTIA N+
Eligibility
 Basic understanding of networking concept
Basic understanding of networking concept Experience working with network devices such as routers, switches, and firewall
Experience working with network devices such as routers, switches, and firewall

Multiple Languages
Choose from Hindi and English

24X7 Assistance
To answer your queries

Updated Syllabus
Latest resources to learn from

Hands on Experience
Practice with virtual labs

Get Certified
Earn a completion certificate
Network Specialist Master Program
Live Online Classes
- 200+ Hours of Expert Training
- Career Guidance
- 24*7 Lab Access
- Flexible Training
Network Specialist Master Program
Weekday Batch
Coming Soon
Duration: 6 - 7 Months
Network Specialist Master Program
Weekend Batch
Coming Soon
Duration: 6 - 7 Months
Corporate Training
- If you wish to undergo the corporate training, feel free to contact us via email at Info@networkkings.org
Learn Top programs from experts!
Live CCNP ENCOR+ ENARSI:
The Cisco CCNP course consists of the core technologies with Enterprise Specialization as it is an upgrade of the pre-existing Networking experience provided through Cisco CCNA certification for CCNP training. CCNP Enterprise training involves advanced Routing, Switching, Troubleshooting, Security, SDN, etc.
Live SD-WAN:
The Cisco SD-WAN training Certification also teaches the SD-WAN installation and migration, placement of controllers, deploying and replacing edge devices, and the ways to configure Direct Internet Access (DIA).
Live Palo Alto Firewall
Palo Alto Firewall course is one of the most widely adopted firewalls worldwide to safeguard and secure Cloud Infrastructures. Palo Alto training is an advanced-level course dealing with Network traffic. It features installing, accessing, managing, troubleshooting, understanding, and differentiating core components of Network Security Operators. Palo Alto course also includes in-detail critical Security concepts of Network and Security Program elements.
Self-Paced CCNA Course:
CCNA is short for Cisco Certified Network Associate. The CCNA is a beginner-level Cisco Certification training for candidates wishing to enter the networking domain. The CCNA Certification will introduce you to networking, routing, switching, and networking security.
CompTIA N+
The CompTIA Network+ course is a stand-alone course that covers all the necessary skills needed to support networks on any platform. It is perfect for candidates who want to gain essential knowledge and skills in networking to build a solid career in IT infrastructure.
TAC Engineer
A TAC Engineer is responsible for configuration & troubleshooting for Juniper Products. This role includes knowledge of switching, routing & firewall technologies.
Cisco ASA Firewall
The Cisco ASA firewall certification provides expertise in the core operating system focusing on offering the methodology of operating, managing, and configuring apex-level web-based threat protection firewalls.
Juniper JNCIA
The Cisco ASA firewall certification provides expertise in the core operating system focusing on offering the methodology of operating, managing, and configuring apex-level web-based threat protection firewalls.
Juniper JNCIA
The Cisco ASA firewall certification provides expertise in the core operating system focusing on offering the methodology of operating, managing, and configuring apex-level web-based threat protection firewalls.
CompTIA Security+
CompTIA Security+ is a certification program designed to validate the skills and knowledge of IT professionals in the field of cybersecurity. The certification covers a wide range of topics related to network security, including encryption, access control, and network infrastructure.
CCNP Service Provider
The CCNP Service Provider is a professional-level certification offered by Cisco to deliver in-depth understanding, functioning and maintenance of the study of service-providing solutions and networking to the enrolled candidates.
Easy Financing Options
We have partnered with top companies to provide
you with the best training that is pocket-friendly.


for EMI- Starting at just
₹ 3,636/ month
Other Payments
Options
options to ease your learning.

Total Admission Fees
₹ 75,000
(Incl. Taxes)
Everything you need to know about Network Specialist Master Program
What is the Network Specialist Master Program?
Network Specialist Master Program comprises of three LIVE courses:
- CCNP: The Network Specialist Master Program covers both CCNP ENARSI+ ENCOR. It helps to have a basic knowledge of CCNP Enterprise training involves advanced Routing, Switching, Troubleshooting, Security, SDN, etc.
- Cisco SD-WAN: The Software-Defined Wide Area Network or SD-WAN course builds expertise in designing, installing, arranging, and managing SD-WAN solutions in wide networks in a short time. The Cisco SD-WAN training Certification also teaches the SD-WAN installation and migration, placement of controllers, deploying and replacing edge devices, and the ways to configure Direct Internet Access (DIA).
- Palo Alto Firewall: Palo Alto training is an advanced-level course dealing with Network traffic. It features installing, accessing, managing, troubleshooting, understanding, and differentiating core components of Network Security Operators. Palo Alto course also includes in-detail critical Security concepts of Network and Security Program elements.
Why choose the Network Specialist Master Program?
Choosing the Network Specialist Master Program will benefit you in mastering Network Specialist skills. You will get three live courses plus self-paced courses worth $1500.
The Network Specialist Master program is specially designed to help students gain all the essential knowledge required to become a Network Specialist.
If you want to become a Network Specialist, then this program is for you.
What is the scope of the Network Specialist Master Program?
Network Specialist Master Program has a high scope. Here is a list of reasons why you should choose Network Specialist as a career opportunity:
- Expansive learning opportunities
- High Advancement knowledge
- Multiple work tasks due to continuous development
- Industrial stability due to high demand in tech-era
- Significance in the industry
- Flexibility
- The future of Network Security is promising.
Why is the Network Specialist Master Program required to sustain IT?
Network Specialist Master program is required to sustain in IT due to the following reasons:
- Specialized Expertise
- Network Infrastructure Management
- Security Management and Implementation
- Network Performance Optimization
- Troubleshooting and Problem Resolution
- Collaboration and Communication
- Compliance and Regulatory Requirements
- Continuous Learning and Professional Development
What Skills will you learn in the online Network Specialist Master Program?
Here are the skills you will learn in the online Network Specialist Master Program:
- CCNP ENCOR/ENARSI
- PCNSE- Core concepts
- PCNSE- Deploy & configure Core concepts
- PCNSE- Deploy and Configure features and subscriptions
- PCNSE- Deploy and Configure Firewalls using Panorama
- PCNSE- Manage and Operate
- PCNSE- Troubleshooting
- PCNSA- Device management and service
- PCNSA- Managing objects
- PCNSA- Policy evaluation and management
- PCNSA- Securing Traffic
- Architecture
- Controller Deployment
- Router Deployment
- Policies
- Security and Quality of Service
- Management and Operations
What are the necessities before applying for the online Network Specialist certification course?
Here are the eligibility criteria for the Network Specialist Certification Course:
- Basic understanding of the networking concept
- Experience working with network devices such as routers, switches, and firewall
Where to enroll for the best Network Specialist course training?
You must enroll for the best Network Specialist Course training from Network Kings. We believe in creating engineers from our specialized training.
Once you complete the Network Specialist Master Program training, you will see the results and advantages Network Kings provides. We equip our students with the best training for upliftment and enhancement in Networking
Why choose Network Kings for the online Network Specialist training?
You won’t regret choosing Network Kings for the online Network Specialist Training. Here are the reasons why you should choose the online Network Specialist Training from Network Kings:
- We deliver courses in Hindi and English to assist students in comprehending the idea better.
- We supply 24/7 Lab access with zero downtime.
- We begin our batches in the evening by giving you enough time to make yourself free with all the work.
- The timing also does not become a hurdle if you are a working professional.
- We have trainers who are industry experts and are instilled with all the knowledge and know the industry requirements since they teach accordingly.
What jobs are available after completing the online Network Specialist certification training in IT?
Here are the job opportunities after the online Network Specialist Certification Training:
- Network Specialist
- Access Network Engineer Specialist
- Network Management Specialist
- Datacenter Network Specialist
- Specialist- IP Network
- L2 Network Specialist
- Network Tech Specialist
- Cloud Network Specialist
- 3rd Line Network Specialist
- Network Checkpoint Specialist
- Network L1 Specialist
- Sr. Network Specialist
- Azure Cloud Networking Specialist
- OCI Network Specialist
- Network Engineer- F5 Load Balancer
- IT & Network Specialist
- Network Operation Lead
- Network Support Engineer
- Technical Network Specialist
- Network Specialist- SD-WAN and R &S
What are the salary prospects after completing the online Network Specialist training course?
Here are the salary prospects after completing the online Network Specialist Training course:
- United States: $89,000 per year
- Canada: CAD 89,000 per year
- United Kingdom: £47,000 per year
- Germany: €76,500 per year
- France: €69,000 per year
- Switzerland: CHF 110,000 per year
- Australia: AUD 100,000 per year
- New Zealand: NZD 80,000 per year
- Japan: ¥300,000 per year
- Singapore: SGD 6000 per year
- India: INR 400,000 per year
- China: CNY 3,00,000 per year
- Brazil: BRL 90,000 per year
- South Africa: ZAR 500,000 per year
- United Arab Emirates: AED 79,000 per year
We offer world's biggest virtual labs
![]() Experience real-world simulations to become job ready.
Experience real-world simulations to become job ready.
![]() Get 24×7 access to labs to learn at your convenience.
Get 24×7 access to labs to learn at your convenience.
![]() Access virtually from any part of the world.
Access virtually from any part of the world.
![]() Zero downtime.
Zero downtime.
![]() Industry-oriented training.
Industry-oriented training.
Meet your Mentor

Atul Sharma
Having 12+ years of experience in the IT industry, your favourite mentor, Atul Sharma, is a Network Engineer and the founder of Network Kings who began his IT journey merely through a YouTube channel in 2013 and focussed on his vision to produce Engineers worldwide. He has worked with Aricent, TCS, Apple, and Juniper.

Amit Bhatt
After clearing the top certification exams - RHCE, and RHCSA, Amit Bhatt has become an asset to IT. He has approximately 11 years of industry experience. He has worked with firms like TechStratus Solutions Pvt. Ltd. CDAC, IBM, and Integrated Solutions.

Sukesh
Your mentor, Sukesh, has gained 12 years of industry experience by clearing CCIE Security, NSE1, NSE2, and VCP-DCV certification exams. He has worked with HCL, CompuCom, RSTFORUM, Capita IT Enterprise Services, Sungard Availability Services, and Cyber Software.

Adhirath
One of your favourite mentors, Adirath, has around 4+ years of industry experience. He has worked with Ideogram Technology Solutions Pvt. Ltd. and has acquired CEH, CompTIA PenTest+, VMware, MCSA, CCNA, and CCNP certifications.
Regular LIVE Webinars
Upskill your knowledge with Live Webinars held by Industry Experts catering learners from different domains. These webinars offer the opportunity to gain insights and learn about the latest trends and developments in their respective fields from renowned experts.
Word of Mouth
Our Student Got Jobs At
Frequently Asked Questions

To prepare for a career in networking, consider obtaining relevant certifications, gaining practical experience through internships or projects, staying updated on industry trends, and continuously improving your technical skills.
While CCNA certification demonstrates foundational knowledge in networking, many employers may require additional certifications, experience, or specialized skills for Network Engineer positions.
Yes, a Network Engineer is typically considered an IT job as it involves designing, implementing, and maintaining computer networks to support an organization's communication and data exchange requirements.
Networking is considered a promising career path in IT due to the constant demand for skilled professionals who can design, secure, and troubleshoot complex networks for businesses.
A career as a Networking Engineer can be financially rewarding, especially as you gain experience, expertise, and specialized certifications that are valued in the industry.
Certificates in networking validate an individual's skills and knowledge in various aspects of networking, such as routing, switching, security, and wireless technologies. Examples include CCNA, CompTIA Network+, and CCNP.
The three levels of Network Engineers typically include entry-level positions (such as Network Technician or Junior Network Engineer), mid-level roles (Network Engineer or Network Administrator), and senior positions (Network Architect or Network Manager).
A Network Development Engineer focuses on designing and implementing network infrastructure solutions to meet business requirements, optimize performance, and ensure the scalability and reliability of network systems.
A professional Network Engineer is an individual with specialized training, certifications, and experience in designing, implementing, securing, and managing computer networks for organizations.
The best certification for a Network Engineer may vary depending on your career goals and specialization within networking. Popular certifications include CCNA, CCNP, JNCIA, and CompTIA Network+.
A degree in computer science, information technology, or a related field can provide a strong foundation for a career as a Network Engineer. However, many employers also value industry certifications and practical experience.
To become a Network Engineer, you typically need to complete relevant education (such as a degree or certification program), gain hands-on experience through internships or entry-level positions, and continuously update your skills through training and professional development opportunities.
The best certification for a Network Engineer depends on your career goals, specialization within networking (e.g., Cisco vs. Juniper), and the specific requirements of employers in your region. Popular choices include CCNA, CCNP, JNCIA, and CompTIA Network+.
Courses that lead to industry-recognized certifications like CCNA, CCNP, JNCIA, or CompTIA Network+ are often beneficial for aspiring Network Engineers. Choose courses that align with your career goals and offer hands-on practice with networking technologies.
For beginners looking to start a career in IT networking, courses that cover fundamental concepts like TCP/IP protocols, routing and switching basics, network security principles, and wireless technologies are recommended. Consider certifications like CompTIA Network+ or Cisco CCNA.
CCNA is typically considered more advanced and specialized compared to CompTIA Network+. If you are looking to pursue a career focused on Cisco technologies specifically, CCNA may be the better choice. However, CompTIA Network+ is a solid entry-level certification covering broader networking concepts.

©2024. Network Kings. All Rights Reserved.























