Multi-Access Year Deal
Get 55+ courses now at the best price ever! Use Code: MULTIYEAR
Cloud Architect Master Program
Gain Practical Insights and Expertise in Cloud Domain through Direct Training from Industry-Leading Professionals.
About Course
The Cloud Architect Master’s Program is for individuals who want to specialize in cloud computing. This master’s program covers the fundamentals of the cloud, where you will learn basic to advanced-level cloud computing skills and technologies.
Enroll today to stand out and earn huge in the tech industry.
This Combo Includes



Eligibility
 Basic understanding of cloud computing.
Basic understanding of cloud computing. Familiarity with Databases
Familiarity with Databases Familiarity with Operating Systems
Familiarity with Operating Systems

Multiple Languages
Choose from Hindi and English

24X7 Assistance
To answer your queries

Updated Syllabus
Latest resources to learn from

Hands on Experience
Practice with virtual labs

Get Certified
Earn a completion certificate
Cloud Architect Master Program Fees
Live Online Classes
- 120+ Hours of Expert Training
- 1:1 Doubt-clearance Sessions
- Career Guidance
- Flexible Training
Cloud Architect Master Program Weekday Batch
Mon-Fri
Oct 23rd, 8 PM IST
Duration: 4 - 5 Months
Cloud Architect Master Program Weekday Batch
Mon-Fri
Nov 20th, 8 PM IST
Duration: 4 - 5 Months
EMI Plans Starting from ₹2667 Per Month
Corporate Training
- If you wish to undergo the corporate training, feel free to contact us via email at Info@networkkings.org
Learn top programs from experts!
Live Azure 104 Program
The Azure 104 course covers the fundamentals of Azure cloud services and provides the skills required to deploy, monitor, and manage Azure resources.
Live GCP Cloud Program
GCP, short for Google Cloud Platform, provides fundamental to advanced-level skills required in designing, implementing and managing Google Cloud products. It is a certification designed by Google.
Live AWS Solutions Architect Program
The AWS Solutions Architect course provides comprehensive training on designing and deploying scalable, cost-effective, and secure cloud solutions using Amazon Web Services (AWS) technologies.
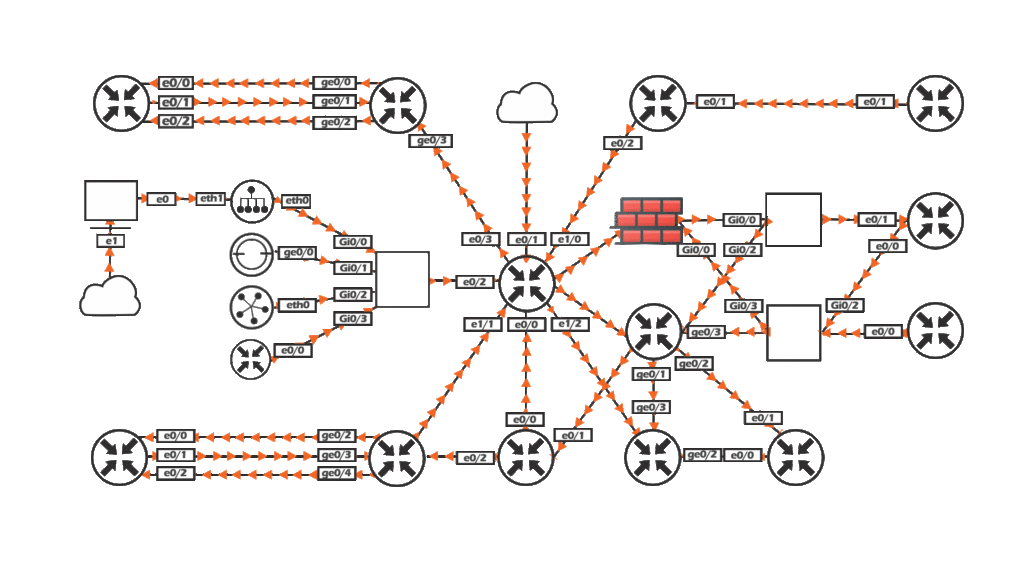
We offer world's biggest virtual labs
![]() Experience real-world simulations to become job ready.
Experience real-world simulations to become job ready.
![]() Get 24×7 access to labs to learn at your convenience.
Get 24×7 access to labs to learn at your convenience.
![]() Access virtually from any part of the world.
Access virtually from any part of the world.
![]() Zero downtime.
Zero downtime.
![]() Industry-oriented training.
Industry-oriented training.
Meet your Mentor

Atul Sharma
Having 12+ years of experience in the IT industry, your favourite mentor, Atul Sharma, is a Network Engineer and the founder of Network Kings who began his IT journey merely through a YouTube channel in 2013 and focussed on his vision to produce Engineers worldwide. He has worked with Aricent, TCS, Apple, and Juniper.

Amit Bhatt
After clearing the top certification exams - RHCE, and RHCSA, Amit Bhatt has become an asset to IT. He has approximately 11 years of industry experience. He has worked with firms like TechStratus Solutions Pvt. Ltd. CDAC, IBM, and Integrated Solutions.

Sukesh
Your mentor, Sukesh, has gained 12 years of industry experience by clearing CCIE Security, NSE1, NSE2, and VCP-DCV certification exams. He has worked with HCL, CompuCom, RSTFORUM, Capita IT Enterprise Services, Sungard Availability Services, and Cyber Software.

Adhirath
One of your favourite mentors, Adirath, has around 4+ years of industry experience. He has worked with Ideogram Technology Solutions Pvt. Ltd. and has acquired CEH, CompTIA PenTest+, VMware, MCSA, CCNA, and CCNP certifications.
Regular LIVE Webinars
Upskill your knowledge with Live Webinars held by Industry Experts catering learners from different domains. These webinars offer the opportunity to gain insights and learn about the latest trends and developments in their respective fields from renowned experts.
Word of Mouth
Our Student Got Jobs At
Frequently Asked Questions
The Cloud Architect Master Program is ideal for professionals who want to specialize in Azure security, such as Azure Security Engineers, Cloud Security Architects, IT Security Analysts, and Network Security Engineers.

©2024. Network Kings. All Rights Reserved.






















