Secure The Network Devices
In this lesson, we will learn how to secure the network devices. There are various approaches that we can use to secure the network.
- By securing the CLI
- By using Firewall
- By using IPS
We will discuss these 3 one by one.
First method to secure the device is to secure CLI passwords, so that only legitimate users can access the CLI. Many times, engineers team requires remote access (by using telnet or SSH) of device to configure or troubleshoots the device.
When we configure the password by using enable password (run in global configuration mode) command, it visible in the configuration file as clear text. This is not a good way to set the password from security perspective.
Here, I am putting a screen shot of show running-configuration command. In this device I configured password by using enable password command. You can see in below picture, password is clearly visible in plain text.

To avoid this clear-text password, always set password by using service password-encryption ( run in global configuration mode). This command encrypts the password and it will not appear as a plain text in configuration file.
Securing IOS Passwords: The one way to secure passwords is don’t store password in device itself. But, this is not possible, this is quite common to store some passwords in router and switches. So, now the point is how to secure these passwords.
Encrypting older IOS passwords with service password encryption:
After configure service password-encryption command, password will appear in encrypted form, here I am presenting a screen shot, you can see, now password cisco will not appear in plain text.

Also, this command doesn’t encrypted password very well, these passwords can be decrypt easily.
To decrypt the password again, you can use no service password-encryption command.
enable secret <password> command: This command doesn’t remember the exact the password, it stores the encrypted form. And when a user enters the password, it perform some calculation(algorithm) to recover exact password and thus checks whether the user entered the correct password or not.

After entering in enable mode we can overwrite this password by configure enable secret <password> command again.
You can also delete this password by configure no enable secret <password> command, but can’t see the plain form of original password.
Encoding the passwords for local users:
Username <user> password <password> command has clear text and poor encryption problem.
To solve this, Cisco introduced a new command username<user>secret<password> global command which encode the password using the MD5 hash and SHA-256 hash.
Use username secret command instead of username password command. It will provide strong encryption. However, note that some IOS features require that the router knows a clear-text password via the username command (for instance, when performing some common authentication methods for serial links called PAP and CHAP). In those cases, you still need to use the username password command.
Controlling password attacks with ACL:
In general, when an external user connects to a router or switch using Telnet/SSH, IOS uses a vty line to represent that user connection. So, by applying an ACL to the vty lines, you can filter the addresses that can telnet/SSH into the router or switch.
For example, imagine that all the network engineering staff’s devices connect into subnet 10.1.1.0/24. The security policy states that only the network engineering staff should be allowed to telnet or SSH into any of the Cisco routers in a network.
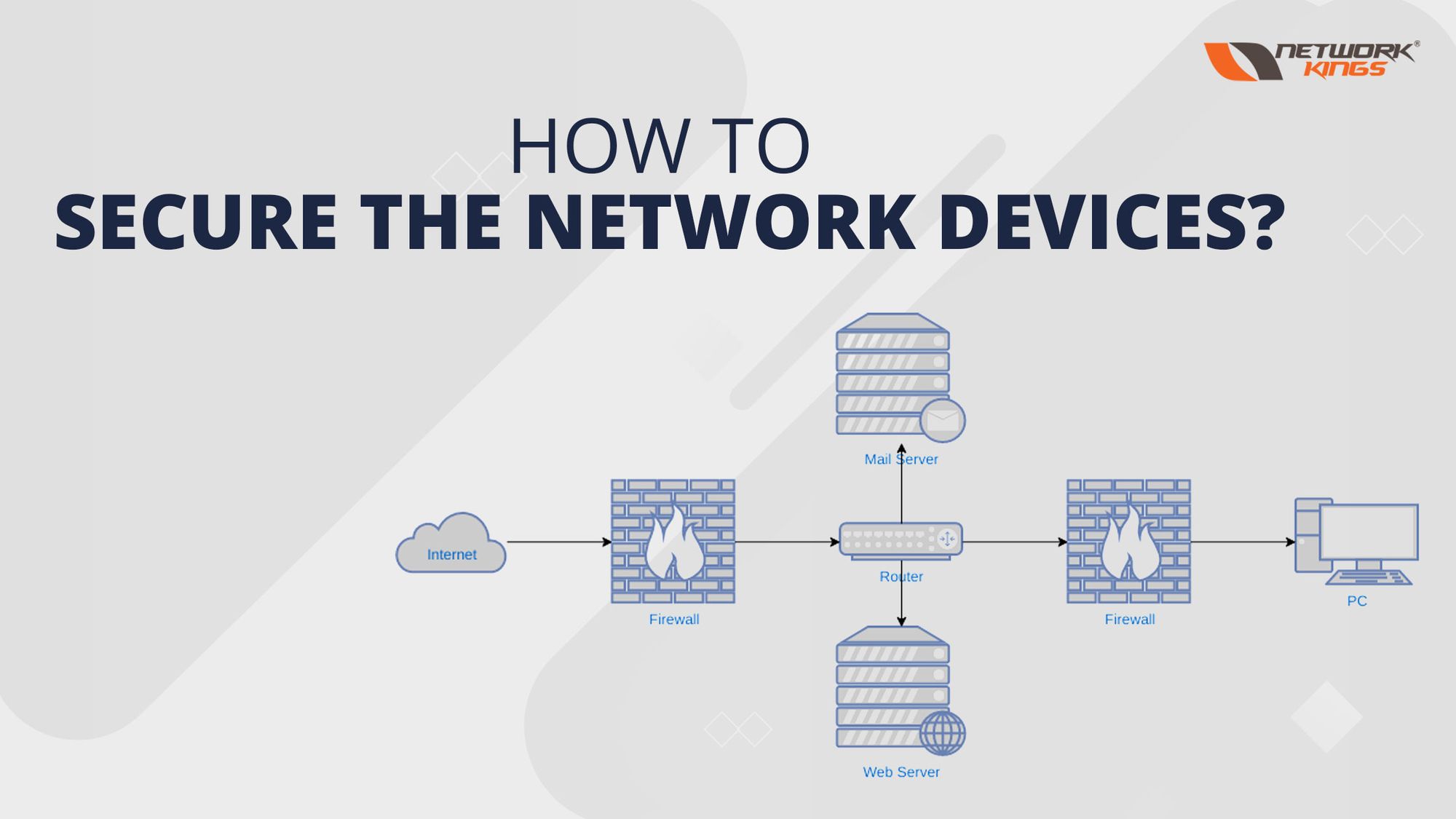
Firewall
Firewall is used to protect our LAN network from outer network attacks.
Firewall may be a virtual device or physical device. Mainly firewall sits between switch and gateway. In general, ACL+router = Firewall, it means firewall and IP ACLs both perform packet filtering task, but the firewalls also perform security task along with packet filtering task.
One more difference, firewall is a flow based device, so before forwarding a packet, it saves the information to connection table and use this information for future use. While ACL+router, doesn’t save any information, it checks the ACL statements and then simply forward the packet.
Here is a list of checks that a firewall does to select the packet (allow or deny)-
- It matches the source and destination IP addresses.
- Identify applications by looking at static well-known TCP and UDP ports.
- It checks the web address of an HTTP request to decide whether to allow or deny the download of the web page identified by URL(web address).
- It saves the information about each packet and uses this data for future filtering decisions. This process is called as stateful inspection.
Firewall sits between switch and gateway, so it checks all the packets before forwarding to default gateway or LAN hosts.
What are security Zones?
Firewalls not only filter packets, they also pay close attention to which host initiates communications.
To secure the company LAN network from outer attacks, we creates security zone inside our network.
Let’s understand this with an example-

Now look at the above diagram, here is 1 payroll server and 1 user in LAN network. Now, for security purpose, we want our company users are able to access the web server (exists outside the network). But outside users shouldn’t access the payroll server.
Firewalls use the concept of security zones when defining which hosts can initiate new connections. The firewall has rules, and those rules define which host can initiate connections from one zone to another zone.
So, here we will create a security zone and put LAN network into security zone and configure a rule in firewall that allow security zone hosts to access web server(allow to initiate a TCP request) and doesn’t allow outside hosts to access the payroll server(doesn’t allow to initiate a TCP request).
What is demilitarized zone?
In above example, there are only 2 zones- inside security zones and outside security zones. But, in company networks, most of time, we also need a demilitarized zone. In a company network, there are few servers that need to be available for users in the public Internet. To secure our company network from outer access, a special zone is created for these type of servers that is called Demilitarized zone.
To explain this, I am taking an example. There is a company named XYZ, divide its network into 2 zones, in one zone put the network devices that outside users can access, this zone is called as demilitarized zone. And in another zone, put the devices that you want to keep safe and don’t want outside user should access, this zone is called as security zone.
By separating those web servers into the DMZ, away from the rest of the company network, the enterprise can prevent Internet users from attempting to connect to the internal devices in the inside zone, preventing many type of attacks.

What is Exploit Signature?
Exploit signature is a set of information that is used to identify an attacker’s attempt to exploit a known operating system or application vulnerability.
What are Intrusion Prevention Techniques?
Same as firewall, IPS also sits in the forwarding path of packets, but IPS makes decision by using different logics. The IPS first downloads a database of exploit signatures. Then to examine compare the packet with signatures and when found a packet as a part of known exploit, discard the packet or even redirect the packet to other security applications for further examination. Signature database is mostly supplied by vendors.
Signatures look for below attacks:
- DoS
- DDoS
- Malware (Worms, Viruses)
Summarization: In this article we discuss various methods to secure the network or network devices. Security is very crucial for every network doesn’t matter it is a small home network or big enterprise network.
Many time engineer teams remotely access the device for troubleshooting or monitoring purpose. So, there is need to secure the CLI by using well encrypted password commands. So, only legitimate user can access the device.
Also, we can secure the CLI, by configuring ACL to vty lines.
Apart from these, we discuss 2 security devices- Firewall and IPS(Intrusion Prevention technique) that protects the network from outer attacks by filtering the traffic based on stored information.