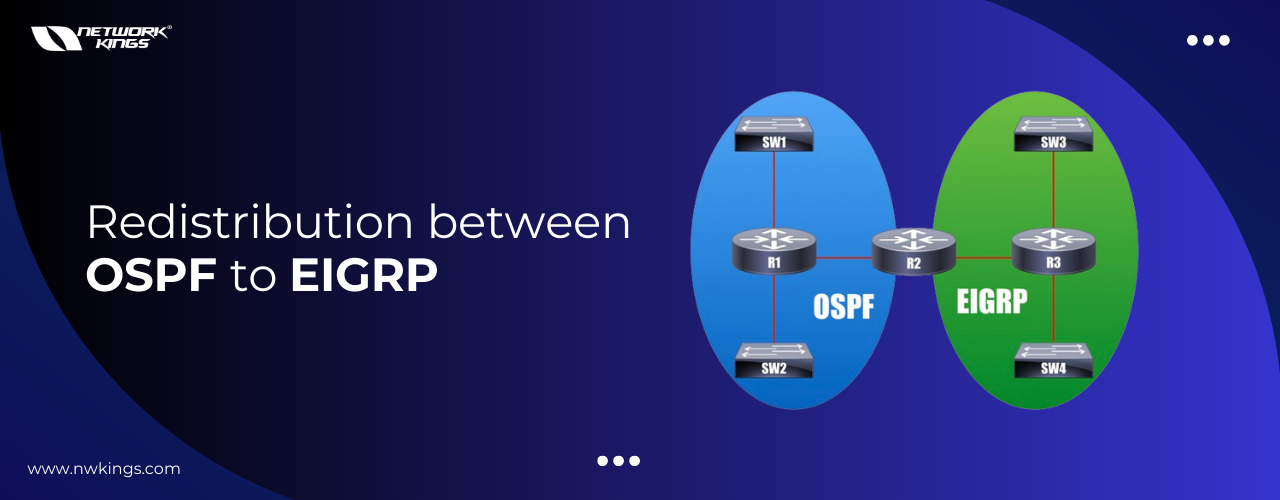
Redistribution between OSPF and EIGRP
In a network, there is a possibility that it is running on both OSPF and EIGRP and the route of OSPF cannot be advertised to EIGRP by itself. Similarly, routes of EIGRP cannot be advertised to OSPF by itself. We can make use of Redistribution to advertise routes between each other. Route Redistribution is a … Read more